CANCUN–Researchers at Kaspersky Lab have uncovered a cyberespionage group that has been operating for at least 15 years and has worked with and supported the attackers behind Stuxnet, Flame and other highly sophisticated operations.
Tag Archives: Malware
Spat Leads to Partial Leak of Rig Exploit Kit
A reseller of the Rig Exploit Kit has leaked some of the source code behind the pack after parting ways with the kit’s developer. Experts don’t expect a spike in Rig-based attacks.
Yet another ransomware variant!
Recently we caught what seems to be a new ransomware variant in our nets. The mail contained a file called “Transferencia devuelta pago erroneo” (translated: “Transfer back erroneous payment”) with the .cmd extension and is actually just an executable.
When running the file, you’ll get the following notification:
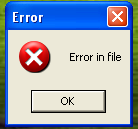
Error in file, nothing to see, move on… Right? Not exactly, in the background a new folder on C: called xwintmp is created and new files are being download and executed:
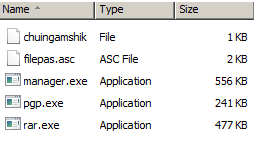 5 new files are created:
5 new files are created:
- chuingamshik -> file which contains the word “chuingamshik”, possibly the project’s name
- filepas.asc -> contains your calculated PGP key and ransom message
- manager.exe ->payload, dropped by Transferencia devuelta pago erroneo.cmd
- pgp.exe -> generates your custom PGP key
- rar.exe -> to encrypt the files
As to not arouse suspicion or to evade sandboxes, the malware then waits for a while using the Windows API “sleep” function and afterwards starts ‘encrypting’ all your files:
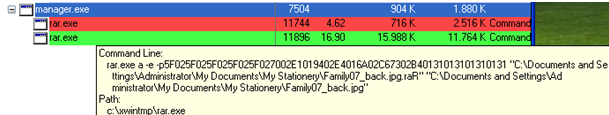
I’ve used single quotation marks here since there’s no real encryption going on, but rather the manager.exe file starts archiving (or “RARring” if you will) your files with some parameters and adds a password, using the command line version of WinRAR. The ransom creates a random key, unique per infection process. The seed for the random key is the Windows API “GetCursorPos”. “GetCursorPos” gets the current X and Y coordinate from mouse cursor, and is launched 16 times, making it impossible to guess or recover the key.
It connects to a TOR server where it sends the random key encrypted with PGP and the public key it contains.
Here’s the good news: when the malware is still encrypting your files, you can easily retrieve the password from memory as is also shown in the screenshot above. Starting with 5F0 and ending with 131 is in fact the password used to encrypt the files. You can use for example Process Explorer to determine the command line arguments and extract the password.
As said earlier, the filepas.asc contains your PGP key + a ransom note, which is as follows:
The files are packed in archives with a password.
Unpacked – 300 eur
To unpack the files send two files to email: [email protected]
1) file you are reading now
2) one packed file (no more than 1 megabyte)
In response comes the original file and the instruction for bitcoin transfer
(The original file is proof that it is possible to return all files to their original)
After the transfer bitcoin, you will receive your password to archives.
Also coming program to automatically unpack files
Reply to your letter will come within 24 hours.
If no response comes for more than 24 hours write to reserved e-mail: [email protected]
Do not pay for ransomware, but restore your files using Volume Shadow Copies or straight from a backup.
In case you’re fast enough, you can get the password and restore your files (kill the manager.exe process after copying the password though, or it will keep encrypting your files).
The post Yet another ransomware variant! appeared first on MediaCenter Panda Security.
Facebook ThreatExchange Platform Latest Hope for Information Sharing
Facebook announced ThreatExchange, an API-based platform for the exchange of attack and threat data.
Security terms explained: What does Zero Day mean?
One of the terms I’m most often asked to explain is what a “zero day” vulnerability or exploit is; let’s look at what that phrase entails.
The post Security terms explained: What does Zero Day mean? appeared first on We Live Security.
New Cyber Threat Center May Face Challenges
In the wake of news-making attacks on Sony Pictures, Home Depot and many others, the federal government is establishing a new information integration center to focus on cyber threats.
PlugX, Go-To Malware for Targeted Attacks, More Prominent Than Ever
The popular remote access tool PlugX enjoyed an ascent in popularity in 2014 and is now a go-to malware for attack groups.
How to spot a Facebook hoax
Hoaxes are all over Facebook so it’s vital that you know what to look out for. Keep in mind these 5 top tips when scrolling through your news feed.
The post How to spot a Facebook hoax appeared first on We Live Security.
Microsoft phishing email targeting corporate networks with ‘neurotic malware’
Security researchers have uncovered a trojan that evades sandboxes specifically targeted at corporate users, hidden in legitimate looking phishing email that apes Microsoft’s Volume License.
The post Microsoft phishing email targeting corporate networks with ‘neurotic malware’ appeared first on We Live Security.
Patch Now – Adobe Vulnerabilities Under Attack
This has not been a great week for Adobe; they have been scrambling to fix a number of critical vulnerabilities in their Flash Player product that are being used in active attacks. But a patch is now available to cover all these vulnerabilities – so patch now!
The post Patch Now – Adobe Vulnerabilities Under Attack appeared first on We Live Security.