If the most wanted cybercriminal in the US used the name of its cat as its password and a Google study revealed that typical security questions such as “What is your favorite food?” were practically useless, what should we expect of the unblocking system that protects our smartphone from being accessed? Very little, of course…
Just like the obvious passwords and answers, the traces that most of us draw on the screen to unblock our smartphone are usually easy to guess. This has been demonstrated by Marta Løge, an investigator from the Norwegian University of Science and Technology, in a study which shows her findings which and that she presented at the PasswordsCon conference in Las Vegas.
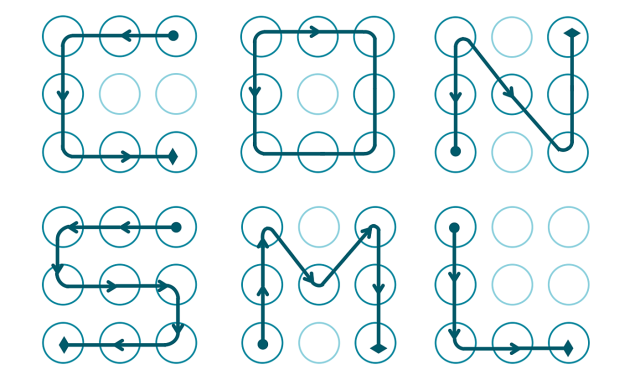
By analyzing nearly 4,000 real user patters, the expert was able to discover a series of inadvisable practices which are repeated all too often. First of all, when choosing a blocking pattern we can draw a trace of up to 9 points (the grid is laid out in 3×3), but the majority of users choose to use less.
The average number of swipes used for the pattern is five, which reduces the number of possible combination to only 9,000. However, it turns out that the majority of users only opt for four swipes (the minimum allowed), which means that the range of patterns that the average user chooses is limited to a little more 1,600, which is clearly not enough.
| Length of pattern | Number of combinations |
| 4 | 1624 |
| 5 | 7152 |
| 6 | 26016 |
| 7 | 72912 |
| 8 | 140704 |
| 9 | 140704 |
This isn’t the only error that we are making as 44% of us start the pattern in the top–left corner of the screen. If that wasn’t worrying enough, 77% of the patterns start in any one of the four corners of the grid. By knowing that the pattern is usually made up of just four points, and that one of them could be in any of the corners, then this considerably reduces the security of the pattern.
Furthermore, it turns out that we are more likely to trace the pattern from left to right and from top to bottom, which makes it even easier to guess.
There are other important factors to keep in mind besides the number of swipes. The complexity of the sequence is also essential when choosing a pattern. If we go with the numbers in order from 1 to 9, we see that it is more difficult to guess the combination of “2, 1, 3, 6” than it is “1, 2, 3, 6”.
Even though both have just four swipes, the stronger choice features a change in direction (from 2 to 1, and from 1 to 3), while the simpler one displays all of the errors we mentioned earlier – starting from the top left of the screen, going from left to right, and from top to bottom. If this is what you are using to protect your cellphone, change it straight away.
It is usually said that the user is the weakest link in the chain when it comes to cybersecurity. As Løge said at PasswordsCon, “the human being is decipherable” and therefore acts in ways that can be guessed easily. In fact, “we are seeing the same elements in the unblocking patterns as in PIN codes or numerical passwords”, states the investigator.
From now on, if we don’t want to be the link that breaks the chain, leaving our device open to threats, we will have to think outside the box when it comes to creating an unblocking pattern. One last bit of advice – don’t stop swiping until it looks like an abstract painting!
The post Why the unblocking system of your Android isn’t secure and how you should change it appeared first on MediaCenter Panda Security.