The online advertising industry has witnessed the emergence of “invisible enemies” that pass themselves off as regular online users – the infamous bots. This network of zombie users has become a serious headache for businesses and this is reflected in recent data. According to a recent study, advertisers worldwide look set to lose $6.3 billion dollars per year (roughly €5.7 million) due to these scammers that try to imitate human behavior.
The investigation also signaled that 23% of all advertising video views and 11% of clicks on advertisements were carried out by botnets. This detail is harmful to the advertisers, as it implies that they are paying in order to artificially inflate page clicks and video views, which results in their campaigns losing credibility.
This worrying situation has forced leading technology companies to come together in the fight against the bots. Google, Facebook and Yahoo have recently joined forces with specialized digital marketing agencies such as Quantcast, Rubicon project and MediaMath. The Trustworthy Accountability Group, a group created by the American Advertising Association and the Interactive Advertising Bureau, has been the main diver behind this initiative to put an end to the fraudsters.
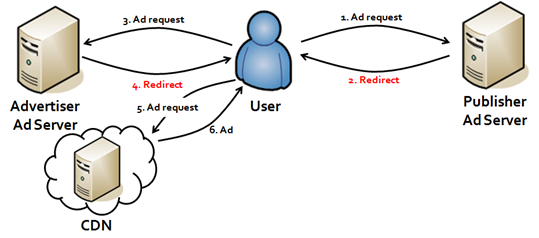
The agreement that they reached can be summed up as follows: there’s strength in numbers. Each of the businesses has its own internal blacklists – databases which contain information relating to suspicious IP addresses. Now, they will combine all of them to create one massive database which will allow them to block the bots.
“The industry is united in this fight and we are going to win the war against fraud”, stated Mike Zaneis, the executive director of the Trustworthy Accountability Group.
The DoubleClick blacklist, a platform for creating and managing the online advertising for Google, filtered 8.9% of web traffic in May. This database will be the most important for this information sharing program that will identify the bots that are designed to evade detection by the IAB/ABC International Spiders & Bots List.

“By pooling our collective efforts and working with industry bodies, we can create strong defenses against those looking to take advantage of our ecosystem. We look forward to working with the TAG Anti-fraud working group to turn this pilot program into an industry-wide tool”, explained Vegard Johnsen, Product Manager Google Ad Traffic Quality, on the company’s online security blog.
A study carried out by Distil Networks estimated that, during 2014, malicious bots appeared in 22.78% of web traffic. This compared to 36.32% of “good” bots while humans only accounted for 40.90%. The harmless bots were able to be identified and this prevented them from carrying out any malicious activities.
Mountain View has detected fraudulent web traffic generated by platforms such as UrlSpirit, which uses Internet Explorer to visit a list of websites that generate up to 500,000 fraudulent requests per month, and HitLeap, a web-sharing service with 1,000 fraudulent advertising requests in the same period.
“By contributing our data-center blacklist to TAG, we hope to help others in the industry protect themselves,” claims Vegard Johnsen of Google. TAG will soon launch a pilot program which will collect a series of general principles, although the actual tool for detecting the online fraudsters isn’t available until the end of the year.
The post Google, Facebook and Yahoo join forces to fight against scammers who inflate the clicks on their ads appeared first on MediaCenter Panda Security.




 We are very excited to announce the debut of a new series of videos called Avast Hack Chat. Every week we invite a security expert to talk us through the hacks on Mr. Robot, USA Network’s summertime hit TV show. We also talk about current news, technology in pop culture, and tips that you can use in your everyday life to keep your devices and data secure. Please subscribe to
We are very excited to announce the debut of a new series of videos called Avast Hack Chat. Every week we invite a security expert to talk us through the hacks on Mr. Robot, USA Network’s summertime hit TV show. We also talk about current news, technology in pop culture, and tips that you can use in your everyday life to keep your devices and data secure. Please subscribe to 



 BYOD, or bring your own device, is a common practice at many businesses around the world. CEO Vince Steckler announced the acquisition of
BYOD, or bring your own device, is a common practice at many businesses around the world. CEO Vince Steckler announced the acquisition of  Students wanting to know how they did on their AP test installed
Students wanting to know how they did on their AP test installed