We all think we know Santa – where he lives (to the nearest Pole!), what he likes to wear (on one day of the year!) – but what do we really know about this mysterious character? What does he do during the rest of the year, what are his hobbies, where does he work on the other 364 days of the year, what is his ‘real’ name, and more importantly – who is on his naughty list?! None of these personal details have ever been revealed, and even in today’s connected world, Santa has managed to keep his identity a closely guarded secret – but how, and what best practices can we learn from our favorite festive character?
He wears the AVG Invisibility glasses
Santa saw AVG’s Invisibility Glasses in February and sent us a letter saying “Dear AVG, those Invisibility Glasses are just what I need to keep me invisible during the year. I have been a good Santa, and I hope you can help me out.”
The glasses make it difficult for cameras or other facial recognition technologies to get a clear view of Santa’s identity, so Facebook can’t automatically tag him in that embarrassing picture under the mistletoe, for example! We, of course, agreed to provide a pair, enabling Santa to travel the world without being tracked, seeing sights that would have been difficult to visit due to the number of people taking pictures to post online. Santa has provided us some pictures from his travels that we can share with you here…XXXX.



While not generally available yet, unless you’re Santa, the concept serves as a reminder to protect your privacy online. There are, of course, many other methods Santa uses to stay private – he has shared a few of them with us in this exclusive interview!
He stays away from social media
“There are hundreds of Santa impersonators on Facebook, but I – the real Santa – am nowhere to be found,” says Santa. Staying away from social media completely might be a challenge for the rest of us, but it’s worth thinking about the information we share via these channels at this time of year. Make sure to check your security and privacy settings to ensure you’re not exposing any information you’d rather not be. “You may want to think twice about posting those pictures of the latest high-tech gadgets you’ve been gifted too – you never know who might be looking!”
He still uses a POLARoid camera
“I never take selfies,” says Santa, “they may get leaked online and that could be awkward.” But with most of us now using our smartphones to take pictures, there are privacy issues you may not have considered. Aside from pictures getting into the wrong hands – the recent VTech hack which may have enabled hackers to steal children’s photos is an example – you might not know that smartphone photos are also often ‘geotagged’, meaning that others can find out exactly where your pictures were taken.
His sleigh is Wi-Fi free and disconnected
“Checking out if you have been good or bad is now even easier with people posting so much of their lives on their online profiles. I avoid being located, tracked or leaving things to chance by using an encrypted Virtual Private Network (VPN) when using the Internet,” says Santa. But It would be impractical for most of us to avoid the Internet completely. There are ways to make sure you’re surfing securely and privately though.
Secure your home Wi-Fi with encryption using a strong password. Also avoid public Wi-Fi hotspots when transferring personal details online during bank transfers for example, or follow Santa’s example and use a VPN. Phishing emails also tend to spike around the festive season as cybercriminals try to tempt us with too good to be true deals. If at any point you think the email is spam and fraudulent then do not open or click on any links, just delete the email!
He pays for everything with toys
Santa told us that his “route and present list is a closely guarded secret. I use very strong passwords and a reindeer for two-factor authentication”. If you’re doing last minute shopping online this year, it’s worth taking to time to remember good password practice – to save time, and a potential headache, later! This means using strong passwords that are different for each account, along with additional security codes or the ‘two-factor authentication’ Santa refers to where available.
So now you know a bit more about Santa and his security secrets – hopefully they’ll also help you to stay safe and secure this Christmas. Happy Holidays!
Image sources:
The British Foreign and Commonwealth Office, Erik (HASH) Hersman, TANAKA Juuyoh (田中十洋), Sreejith K, Brian Burk
![]()
![]()



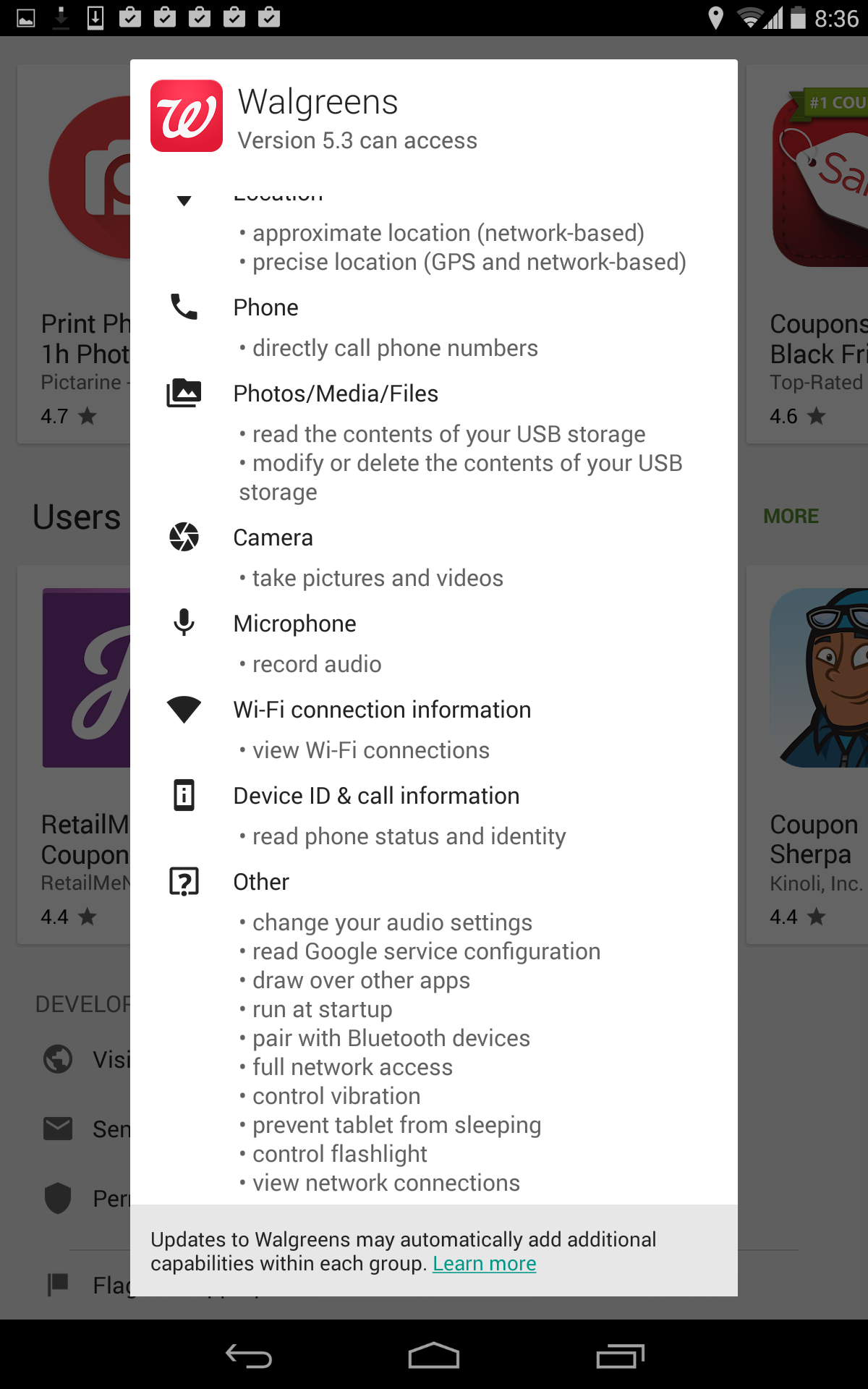
 If you want to choose a shopping app based on the amount of unnecessary permissions it collects then Walgreens is the app for you!
If you want to choose a shopping app based on the amount of unnecessary permissions it collects then Walgreens is the app for you!