WeLiveSecurity sits down with Igor Kabina, the ESET malware researcher who ultimately created the universal ESET TeslaCrypt decryption tool.
The post Expert insight from the author of the ESET TeslaCrypt decryptor appeared first on We Live Security.
![]()
WeLiveSecurity sits down with Igor Kabina, the ESET malware researcher who ultimately created the universal ESET TeslaCrypt decryption tool.
The post Expert insight from the author of the ESET TeslaCrypt decryptor appeared first on We Live Security.
![]()
These days, it is not Vogon poetry that’s the most widespread risk one can encounter in the universe, but rather ransomware, explains ESET’s Ondrej Kubovič.
The post Don’t want ransomware to rock your universe? Add this to your towel appeared first on We Live Security.
![]()
Something odd is happening in the world of ransomware – morality, advanced business strategy, or mom got angry.
The post Ransomware turns over a new leaf … maybe appeared first on Avira Blog.
The Angler Exploit Kit is exploiting the latest Flash zero day and is moving Dridex banking malware. The Magnitude and Neutrino exploit kits have also integrated the 0day.
You have already read some of our tips to help prevent the most feared and common cyber-threat of the moment, ransomware; it can hijack your computer and all the computers in your company. Its main strength is that it is able to block computers and encrypt files, and the only one who is able to decrypt it is the cyber-criminal that created it, which is why so many victims are paying the ransom demanded by these attackers.
When an attack is this sophisticated, the only way to combat it is by taking precautions. Any recommendations you may have can help you, but there is a key measure that is worth mentioning: the backup copies are your best allies to resist the escalation of a cyber-abduction.
In the second part of this guide, we will explain what is essential and how you can handle a ransomware attack.
First of all, ransomware does not block everything. If your devices have been infected, the first thing you should check is that the information is really encrypted. There are mediocre cyber-criminals that are taking advantage of the success of better-prepared, cyber-crime mafias. They do these second-rate jobs in order to simulate attacks that in reality don’t actually hijack your files, and then they reap the benefits. If you do not know how to distinguish a real threat from an imposter, make sure to consult an expert before forking the cash over to the bad guys.
Another important thing to consider: Do you have a backup? After you have verified that the attack is in fact a legitimate ransomware, the first thing you need to ask any security professional is if your company has backup copies of everything that is important. It is the only effective defense. If you have backups, you can eliminate the infected system completely, load your backups, and then everything will be back to normal.
Uses reliable tools. Not all programs are equally effective in creating backups. Unfortunately, many organizations have found that the software used to create a backup is not able replace the detailed information exactly the same as it was before the ransomware attack. Choose your work team carefully and protect your files. Good security solutions offer reliable tools.
For security reasons, it is better to keep your backups offline. In addition to this, if you want to keep ransomware from dragging you down, do not store backups on a shared disk. The more isolated your backups are from the network that is possibly infected, the more likely you are to survive and retrieve your sensitive information from them.
Make several different copies. Even if you are the most careful while carrying out these procedures, there is always a fragile moment. Those few minutes when the disk guarding your backup is copying the data, and is connected to the rest of the network. In that precise moment you are vulnerable to a cyber-criminal. In order to prevent infection, it is advisable to backups in several periods: in real time (if resources permit it), daily, weekly and monthly. They must be separate backups, and at least one of them should be disconnected from the rest of the network.
The post A Kidnapping Survival Guide: How to Combat Digital Ransomware (Part 2) appeared first on Panda Security Mediacenter.
Here’s some good news for victims who are trying to unlock and remove TeslaCrypt ransomware.
Now, you can decrypt all your important files that have been encrypted by TeslaCrypt ransomware.
So, stop Googling about How to decrypt TeslaCrypt Ransomware encrypted files, as the malware authors themselves provided the solution to your problem.
<!– adsense –>
Since its launch in March last year,
![]()
Jigsaw 2.0 is not fully-fledged ransomware, but it does try to feed off of ransomware’s current popularity amongst cybercriminals, writes ESET’s Ondrej Kubovič.
The post Jigsaw ransomware 2.0: A fake or work in progress? appeared first on We Live Security.
![]()
 Kidnappers can easily take your digital information using one of the most dreaded types of malware: ransomware. Cyber-criminals are relying more and more on these malicious programs to block our computers. Now, they are asking for larger amounts of money if you want them to “give back” access to your hard-drive.
Kidnappers can easily take your digital information using one of the most dreaded types of malware: ransomware. Cyber-criminals are relying more and more on these malicious programs to block our computers. Now, they are asking for larger amounts of money if you want them to “give back” access to your hard-drive.
The losses that a business can incur from an attack of this kind are enormous, which is why it is essential to be knowledgeable about the basic precautions that should be taken if you are in this type of situation. First to prevent these types of attacks; and then to fight them.
We have prepared a summarized guide with the essential things that you need to be aware of. Here they are:
The post A Kidnapping Survival Guide: How to Combat Digital Ransomware (Part 1) appeared first on Panda Security Mediacenter.
Should be “Shot at sunrise” is the opinion of U.S. politician Michael C.Burgess, the representative for Texas, when talking about the cybercriminals who distribute ransomware that victimizes consumers and businesses.
Ransomware, malicious software designed to block access to a computer system until a sum of money is paid, and the use of exploit kits to distribute it, are adding new challenges to threat detection and protection. And now Angler, an exploit kit, which has been a known Internet threat since 2013, is being used to distribute ransomware. With the sole intent of installing ransomware on victim’s machines.
Our AVG Web Threats team is tracking these widespread ransomware attacks being delivered by the Angler crimeware exploit kit.
The use of exploit kits to distribute ransomware is a new trend – one that could cause widespread ransomware distribution. Exploit kits are software packages readily available for sale and are used by malicious operators to easily create malware that performs a wide variety of malicious functions. The malware is installed on hacked web servers and attacks the machines of visitors to web sites, in many instances, without their knowledge.
There is a common misperception that web users are only at risk if they browse risky sites, however, hacked sites are often brand names and appear safe. Small business sites in particular can be prime targets because they have less security and their visitors typically know the company and trust their brand.
The malware on these sites seeks out vulnerabilities in commonly used tools that improve website experiences, such as Flash, Silverlight and other software that employs Java and PDF-format files. The malware then runs malicious code on the visitors’ machine to install ransomware, backdoors and Spybot clients.
Our AVG Web Threats team has researched a particular instance of a Java exploit commonly found in association with Angler. This threat is detected by AVG, which we’ve been detecting since January. AVG customers who participate in anonymous threat sharing reported 6,123 hacked domains serving Angler in January, 8,260 in February and 4,412 in March.
Angler ransomware installs
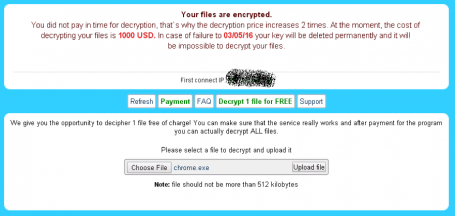
TeslaCrypt is the most common type of ransomware installation currently that’s associated with Angler, according to our AVG Web Threats team analysis of this threat. TeslaCrypt encrypts users’ files, including writeable shares, and messages the user to extort payment for recovering the encrypted data. Paying the ransom to unlock files typically does not result in the recovery of the files.
Below are screen shot examples of ransomware attacks that attempt to extort $1,000 USD, payable through the untraceable currency of bitcoins.
Backdoor installs
Our AVG Web Threats team track the Angler-infected host machines have also tracked incidences of downloading malware known as backdoor malcode (commonly Bedep). Backdoor, or Bedep, can snatch passwords and personal confidential data from visitors’ machines.
Protecting your desktop
AVG recommends that consumers and businesses take the following preventive measures:
Protecting web servers
Malicious code from the Angler exploit kit is initially installed on the web pages of vulnerable servers. For businesses, standard security precautions and monitoring are the basic defense. Researchers find a large number of Angler injections on WordPress and Apache servers – these should be given an extra measure of scrutiny.
Our AVG Web Threats team continue to monitor and track threats such as Angler, so that we can deliver the security you need to keep your devices and businesses safe.
![]()
![]()
Cerber ransomware leverages Dridex spambot network in massive new crypto-offensive targeting U.S. inboxes.