A variant of the Nymaim dropper has surfaced, and it includes new delivery methods, obfuscation techniques, and the use of PowerShell to download payloads.
Tag Archives: ransomware
Locky Ransomware Learns New Evasive Tricks
Microsoft malware researchers say Locky ransomware authors are changing tactics again to evade detection.
Crypt888 Ransomware Has Facelift as It Seeks Fresh Victims
We’ve been following the slow evolution of an interesting strain of ransomware we have named ‘Crypt888’, which is unlike other strains that have reported on over the past few months.
Crypt888 has been focused on experimenting with user interfaces rather than improving its code, serving up ransom instructions in a variety of languages including Italian and, most recently, Czech.
In June 2016, AVG’s Virus Lab released six free decryptors for the recent strains of ransomware. We continue to monitor the situation, ready to update the tools as the ransomware evolved.
Our research uncovered one strain, Crypt888, behaving differently to the others. Instead of improving the code, the malware authors were focused on experimenting with the user interfaces such as changing the language of the ransom message.
This means that the underlying Autolt script remains the same in the previous versions … but oddly, the ransom instructions are served up in the Czech language only in the latest version.
This is how we identified and tracked the evolution of Crypt888’s.
Tracking a threat
Crypt888, also known as MicroCop and Mircop, is one of the many ransomware strains discovered in 2016 and its evolution has been very specific. After analyzing various samples, we found that the wallpaper containing ransom instructions is the only part of Crypto888 that has changed.
The underlying AutoIt script has remained more or less the same in all the known versions of this strain. So too has the encryption algorithm, encryption key, file names, and various other components, which is not so usual. While this means our decryptor can rescue your encrypted files, it means that the way in which Crypt888 presents itself keeps changing. In the latest version, the instructions appear in Czech.
Changing the language in which the ransom message is delivered has been a hallmark of this particular threat. We tracked several evolutions of Crypt888 from its first appearance in June this year.
- The ‘Guy Fawkes’ version, June 22, 2016: first known version of this ransomware
- The ‘Business Card’ version, July 8, 2016: this version appears and looks like a test version as there are no payment instructions
- The ‘Italian’ version, July 29, 2016: this version had several new features and the errors in the language suggest machine translation
- The ‘Czech’ version, September 21, 2016: the latest variety appears in yet another language, again with errors suggesting the author is not a native speaker
The first encounter
The first known version of Crypt888 appeared as black wallpaper with the image of a Guy Fawkes mask, a notorious symbol usually associated with Anonymous. The message accused the victim of stealing 48.48 Bitcoins ($30,000) from ‘the wrong people’ and requesting its return.
The threat intimated there would be repercussions but there were no details about how to comply with repayment or how the decryption process would work after payment was made. This is probably the reason why we found only one transaction to the provided bitcoin address so far.

Testing, testing, 1 – 2 – 3
A few weeks later, we identified a second version. This time, the wallpaper with the story and related accusations were gone. In fact, there were no payment instructions at all and instead, the wallpaper contained the “business card” (as seen in this video).
We have no clear explanation why this particular image has been used but we think it was probably a test version based on a fact that there were no instructions or payment addresses provided to victims.
Just in case, however, we released a free Crypt888 decryption tool, which was able to recover files encrypted by both of this and the earlier version.
The Italian affair
Three weeks later, we identified yet another version of Crypt888 which had multiple changes. While the AutoIt code was once again similar to the previous versions and the same algorithms used – so our decryption tool is still fully functional for this version – the code was obfuscated.
There was a new image which contained ransom instructions in Italian, with typos and errors that suggest machine translation. In addition, this version of Crypt888 did not create the text file LEGGIMI.txt, which should contain the payment instructions. This means victims would find themselves left with encrypted files and no instructions as to how to recover them.

Czech-mate
Malware researcher S!Ri identified this latest version one month after the Italian version. We investigated further and found its code is no longer obfuscated, and essentially, it’s the same as the first two versions with the wallpaper being the only notable difference.
These ransom instructions this time appear in Czech and are a departure from previous versions in terms of content. Firstly, the ransomware claims that it is a ‘Petya ransomware 2017’. But don’t be fooled – it is not. This is probably a maneuver to fool victims hit by Crypt888 that are trying to find a free fix online.
Petya is a much more sophisticated piece of ransomware and it is not decryptable at the moment. This is not the first time one ransomware strain has pretended to be another; we observed lesser known ones have masqueraded as a more famous one, such as TeslaCrypt, CryptoLocker, or CryptoWall on a number of occasions.
The Czech version also differs in that the ransom amount is ‘only’ 0.8 Bitcoin ($480 at the time of writing). The number reflects an apparent fixation with the digit ‘8’ as it is heavily used across the program: in the ransom amounts, the configuration of the encryption algorithm, the created file names, etc. That’s why we chose the name Crypt888 when we identified it.
Another change is that victims are threatened with a five-day deadline to pay, and two email addresses are provided for the victim to send proof of payment (and to receive the decryption tool, allegedly) yet no penalties are mentioned if the deadline is missed.
Finally, the authors hint in the text about the ransomware’s origin with the sentence which, when translated, means “We belong to Czech/Russian Hackers”. Based on the accuracy of the available text and code quality, it is hard to believe those claims, as it contains many typos, incorrect word order, odd mixtures of text with and without Czech diacritics, and other errors. More likely, the text was created by machine translation, like the Italian version.

At the time of writing, we have not found any further language variants of this ransomware and can reassure people that our free decryption tool will work for all the versions described here.
We suspect the authors of Crypt888 are still producing new versions of their ransomware. Their technique is in contrast to authors of other ransomware families in that they focus primarily on changing graphics and preparing fake stories rather than on improving their code. We are continuing to monitor for any new variants that will make it necessary to adapt our decryption tool to ensure victims have a means to mitigate a Crypt888 attack.
![]()
![]()
Tales from Ransomwhere: Macros & Ransomware(s)
How does MW get into systems?
This ransomware’s initial infection vector occurs when it’s sent/received through Phishing campaigns.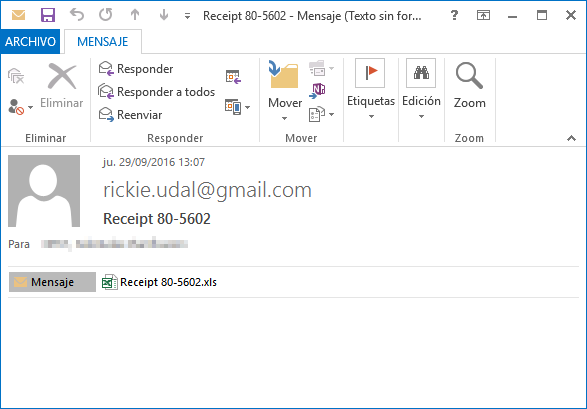
First, the user receives an email with the malicious file in zip format, giving the illusion it is a zip, but in this case, the user also receives some type of invoice; this varies depending on the message received or the name of the file. On this occasion, the received file has the following name: Receipt 80-5602.zip, as seen in the screen capture.
In this compromised file you will find a Microsoft Office document, or more specifically, an Excel with the extension “.xls” containing macros (codes are in Visual Basic Script)
How is this Code/Macro Executed?
By defect, unless we have the macro execution forced in Excel, the damaged code will not automatically run, unless, an advertisement appears indicating that the document contains macros, as demonstrated in the second screen capture.
And…What is this Macro?
The basic feature of this macro is to use the “dropper”, what we mean is, download and execute the other binary file, in this case a file encrypter or ransomware; although it could have been another malicious program like RATs, backdoors, bots, etc.
In this case, as with droppers, the file (or payload) runs on a remote server when executed.
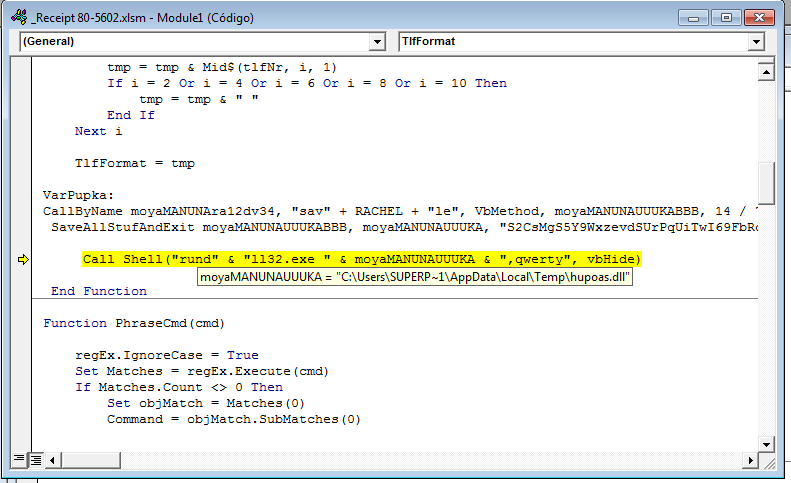
Once the macro is executed, it is now in charge of taking the next steps: downloading and deciphering the remote file that is encrypted, and afterwards, ejecting it.
If we look at the name of the file running from the macro, or its command-line execution, we will see that the ransomware comes by DLL format; this has become increasingly more common. In addition, it requires that an export is indicated to operate, in this case “qwerty”, as shown in the following screen shot:
Why do it this way? Simply because a lot of systems that update the malware analysis (sandboxes) have problems when they execute programs/codes/libraries that require parameters, that are sometimes unknown.
Once encrypted, this library’s MD5: 586aaaaf464be3a4598905b5f0587590
Finally, from PandaLabs we would like to give you the following advice: if you don’t want to have an unwanted surprise, when you receive Office documents from unknown senders do not click the button that says “activate macros”. Lastly, make sure your antivirus solutions and systems are always up-to-date!
The post Tales from Ransomwhere: Macros & Ransomware(s) appeared first on Panda Security Mediacenter.
Ransomware: Expert advice on how to keep safe and secure
ESET’s Lysa Myers offer a detailed and comprehensive overview on how to stay safe against ransomware attacks, a threat that is growing in prominence.
The post Ransomware: Expert advice on how to keep safe and secure appeared first on WeLiveSecurity.
![]()
Avira at it-sa 2016: New product portfolio for customers

We will present our latest security technology for small- and mid-size businesses, including management and OEM solutions, at this year’s it-sa in Nuremberg. From October 18 – 20, 2016, you can learn all about our latest product portfolio and get advice from Avira experts in Hall 12, Booth 662.
The post Avira at it-sa 2016: New product portfolio for customers appeared first on Avira Blog.
Locky ransomware goes Nordic with Odin…

… but don’t miss the forest for the trees! The latest Locky variant appropriates Nordic mythology with a vacuum-cleaner approach to encrypting victims’ files.
The post Locky ransomware goes Nordic with Odin… appeared first on Avira Blog.
MarsJoke Ransomware Targets .EDU, .GOV Agencies
Researchers have identified a new ransomware strain that spoofs tracking services via spam messages and contain URLs that link to malicious files.
Worldwide “Crysis†Through Remote Desktop Protocol
 Two weeks ago we saw a ransomware attack in a server belonging to a French company. It was a Crysis variant, a ransomware family that appeared earlier this year. We witness thousands of infection attempts by ransomware on a daily basis, but this one caught our attention as the file somehow showed up in the computer when no one was supposed to be using it and in fact, there were no email clients or Internet browsers running there.
Two weeks ago we saw a ransomware attack in a server belonging to a French company. It was a Crysis variant, a ransomware family that appeared earlier this year. We witness thousands of infection attempts by ransomware on a daily basis, but this one caught our attention as the file somehow showed up in the computer when no one was supposed to be using it and in fact, there were no email clients or Internet browsers running there.
How did it get into the computer?
Why did the security measures in place allow this file into the server? That’s what we wanted to find out, and so we began an investigation. It turns out that this server is running Remote Desktop Protocol (RDP) and these cybercriminals used a brute force attack until they could guess the credentials to obtain remote access.
Back to the story—as most users do not have 2FA enabled and the passwords are not that complex nor random, it is pretty easy to get into a server using this kind of brute-force attack, a good dictionary or with the most common combinations. This is not a new technique. More than a year ago, I remember one wave that hit Spanish companies with ransomware using the exact same technique. Cybercriminals usually perform these attacks at night or during weekends, when there are few people in the office, or none at all.
Cybercriminals get into a server using this kind of brute force attack, a good dictionary or with the most common combinations.
In this case, the attack to the server started on May 16th, where they performed 700 login attempts. These were performed automatically, usually for a period of two hours approximately. Most of these attacks have been happening from 1am to 3am, or from 3am to 5am. Each and every day. The number of login attempts changes, for example on May 18th there were 1,976 while on July 1st there were 1,342.
After almost four months and more than 100,000 login attempts, the attackers were finally able to get into the server and drop the Crysis ransomware.
This is a Worldwide Crysis
This week our colleagues from Trend Micro published an article that warned us about similar attacks happening in Australia and New Zealand that deploy Crysis variants. Unfortunately, we can say that those are not the only countries—this is happening at a worldwide level (at least since May).
Assuming you need to have RDP running and connected to the Internet, apart from monitoring connection attempts so you can learn that you are under attack, you should also enforce complex passwords. The best approach would be to implement 2FA, such as SMS passcode, so guessing passwords becomes useless.
We’ll continue to keep you informed with our Tales from Ransomwhere series!
The post Worldwide “Crysis” Through Remote Desktop Protocol appeared first on Panda Security Mediacenter.
Locky takes the wheel again

Ransomware returns to its earlier hands-on approach.
The post Locky takes the wheel again appeared first on Avira Blog.