Diamond rings and an Audi R8 can be mine just for the simple actions of liking and sharing on Facebook. NOT!
In the past week, three fake giveaways have come across my Facebook newsfeed – two of them today! These were shared by otherwise intelligent friends, so that makes me think all kinds of other people are falling for the scam. I’m sharing these with you, so you’ll know what to look out for.
Each scam promises that you could win a valuable prize just by liking and sharing the post. This one is for an Audi R8 V8, and every time I’ve seen it, it’s originates from a different page. The instructions are always the same – for a chance to win, you must like the page, request your desired color in the comments, and share the post with your friends.
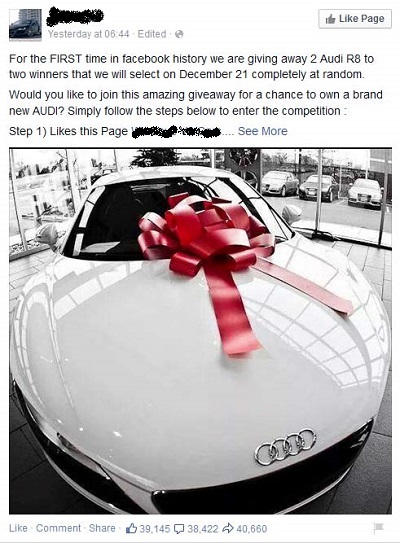
This type of social engineering scam is called like-farming. It is designed to gather many page likes and shares in a short amount of time, and since Facebook’s algorithms give a high weight to those posts that are popular, they have a high probability of showing up in people’s newsfeeds. Scammers go to all this trouble for two purposes: The pages can later be repurposed for survey scams and other types of trickery that can be served to a large audience. And pages with large numbers of fans can be sold on the black market to other scammers with creative ideas.
All that glitters…
Two posts for beautiful jewelry appeared in my newsfeed just today. One was from the famous jewelry company, Tiffany & Co. The post shows a video of a sparkling diamond band and asks for a like, share, and comment to win this ring.
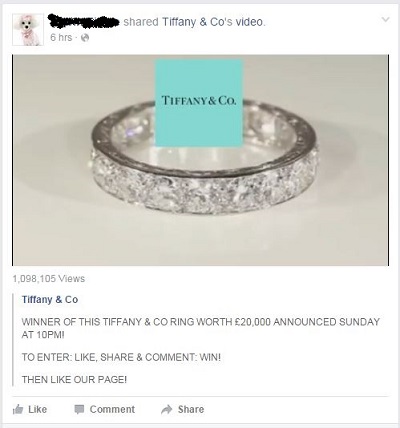
Click on the link and it takes you to a fake Tiffany & Co Facebook page.
There are two things to notice about the page; one, the Co in the name of the company does not have a period at the end. And two, the page does not have the blue Verified Page check mark beside the name. That mark is Facebook’s way of guaranteeing the authenticity of the company.

Here is the real Tiffany & Co. Facebook page with the verified page check mark.

The other jewelry scam came from a page called Sani Jewellery. The scam is the same as the one from the fake Tiffany page; users can win just for liking and sharing the post on their Facebook page.
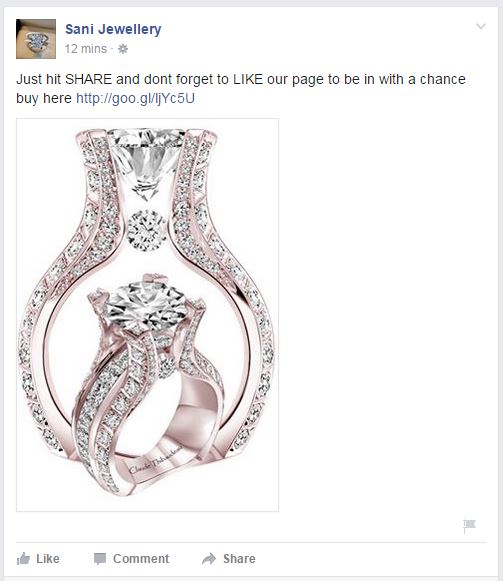
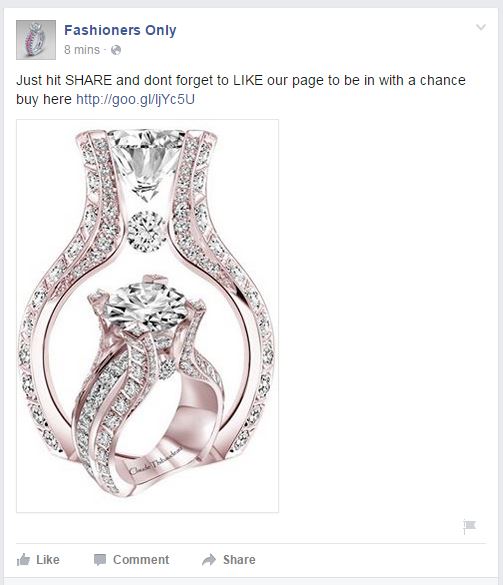
These scammers own another Facebook page called Fashioners Only, and run identical like-farming scams.
How to avoid like-farming scams on Facebook
- If you suspect that someone has shared a fake page with you, do not click on it or participate in the giveaway.
- Politely inform the person who posted it that the Facebook page they shared is a like-farming scam. You can even send them to this post.
- Report the page to Facebook by hovering over the top right corner of the post. Click the arrow and choose Report post.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.








