Dropbox officials on Monday said that a large cache of usernames and passwords posted online and alleged to have come from the company’s users are not related to Dropbox customer accounts. A spate of media reports reported yesterday that attackers had stolen several million sets of credentials from Dropbox and posted them online. The claim of […]
Tag Archives: Social Engineering
4Chan: destructive hoaxes and the Internet of Not Things
The media have associated a number of destructive hoaxes with 4chan: people need some historical perspective on how the site actually works.
The post 4Chan: destructive hoaxes and the Internet of Not Things appeared first on We Live Security.
![]()
Malware-Laced Emails Appear to Come From LogMeIn
Spam emails pretending to be a security update for LogMeIn users, including a new security certificate countering Heartbleed attacks, are making the rounds, warns the SANS Institute.
Free iPhone 6 Facebook scam does the rounds, right on time
Facebook scams tend to crop up in the run-up to a big Apple launch with around the same regularity as big Apple launches themselves. This week’s iPhone 6 launch is no exception, with Help Net Security noting that a Facebook page ‘offering’ free iPhone 6 units is, as usual, a total fraud.
This time, the scam promises a free iPhone 6 as soon as “three easy steps†are completed, which, as usual, involve a survey, which allows you to download a “participation application.â€
When a victim completes the free iPhone 6 survey, all their friends are spammed with the fake promotion, Hoax Slayer reveals, but the three “easy†steps are anything but.
Each time someone completes a survey, the page claims there is an error, and they are directed to a further survey, according to Help Net. As always, the “free iPhone 6†never materializes.
Free iPhone 6: Nope, it’s a scam
“Some of the available surveys want you to provide your mobile phone number, ostensibly to go in the draw for extra prizes or offers. But, by submitting your number, you will actually be subscribing to a very expensive text messaging ‘service’ that will charge you several dollars every time they send you a message,†Hoax Slayer says.
“Alternatively, you may be asked to provide your name, address, and phone details, again, to supposedly enter you into a prize draw. But, fine print on the page will state that your details will be shared with third-party marketers. Thus, after submitting your details, you will likely be inundated with annoying phone calls, emails, and junk mail.â€
“Meanwhile, the scammer who created the fake promotion will earn a commission. But, no matter how many surveys you complete, you will still not get to download your ‘application’.â€
The site cautions against clicking on any link this week which offers a free iPhone 6, as this sort of big product launch is a prime target for cybercriminals, and any link is potentially suspect.
Something for free?
Mark James, ESET security specialist, says, “We all like the idea of something for free, that’s the approach these type of scams use. Deep down we know it’s not going to happen, but a lot of people will still click the like button or share that simple post in the hope it’s going to arrive.â€
“We have seen these types of scams for years but they are still as effective today as they were when started, once we like or share the page we do all the marketing and advertising for the scammers thus providing a very valuable and potential dangerous page to initiate future scams or attacks.â€
“I still encourage people to use the “front door†policy, i.e treat it like your front door: ‘When was the last time someone banged on your front door to offer you an iPhone 5 or 6 just for filling out a survey or a £10/£50 supermarket voucher for free?’ It just does not happen.â€
The post Free iPhone 6 Facebook scam does the rounds, right on time appeared first on We Live Security.
![]()
‘Kyle and Stan’ Malvertising Network Targets Windows and Mac Users
A malvertising network that has been operating since at least May has been able to place malicious ads on a number of high-profile sites, including Amazon and YouTube and serves a unique piece of malware to each victim. The network, dubbed Kyle and Stan by the Cisco researchers who analyzed its activities and reach, comprises […]
TorrentLocker now targets UK with Royal Mail phishing
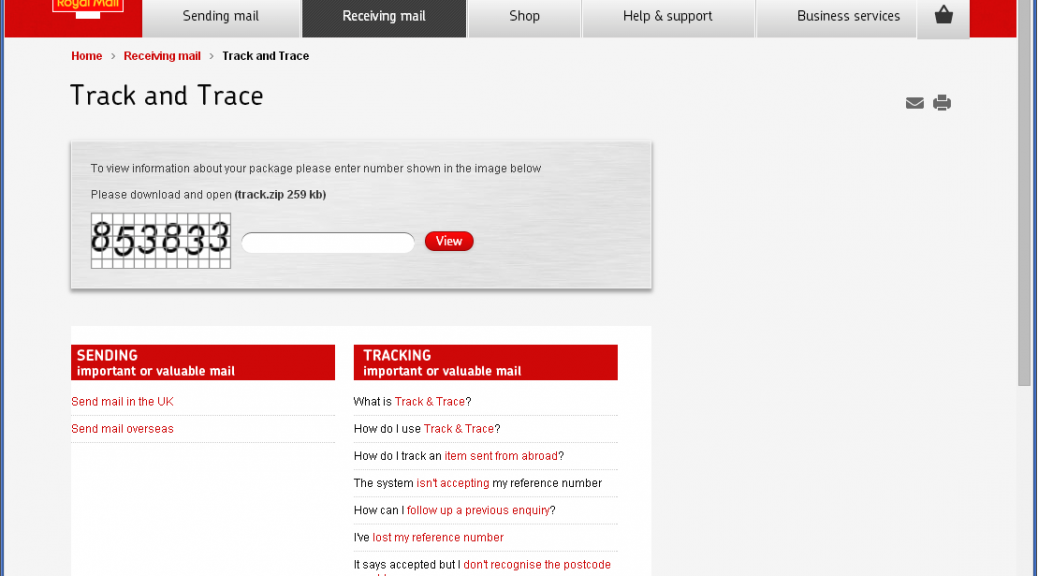
Three weeks ago, iSIGHT Partners discovered a new Ransomware encrypting victims’ documents. They dubbed this new threat TorrentLocker. TorrentLocker propagates via spam messages containing a link to a phishing page where the user is asked to download and execute “package tracking informationâ€. In August, only Australians were targeted with fake Australian Post package-tracking page.
While tracking this new threat, ESET researchers found the malicious gang is targeting new victims. Internet users from the United Kingdom should be aware that fake Royal Mail package-tracking pages are online and distributing TorrentLocker.
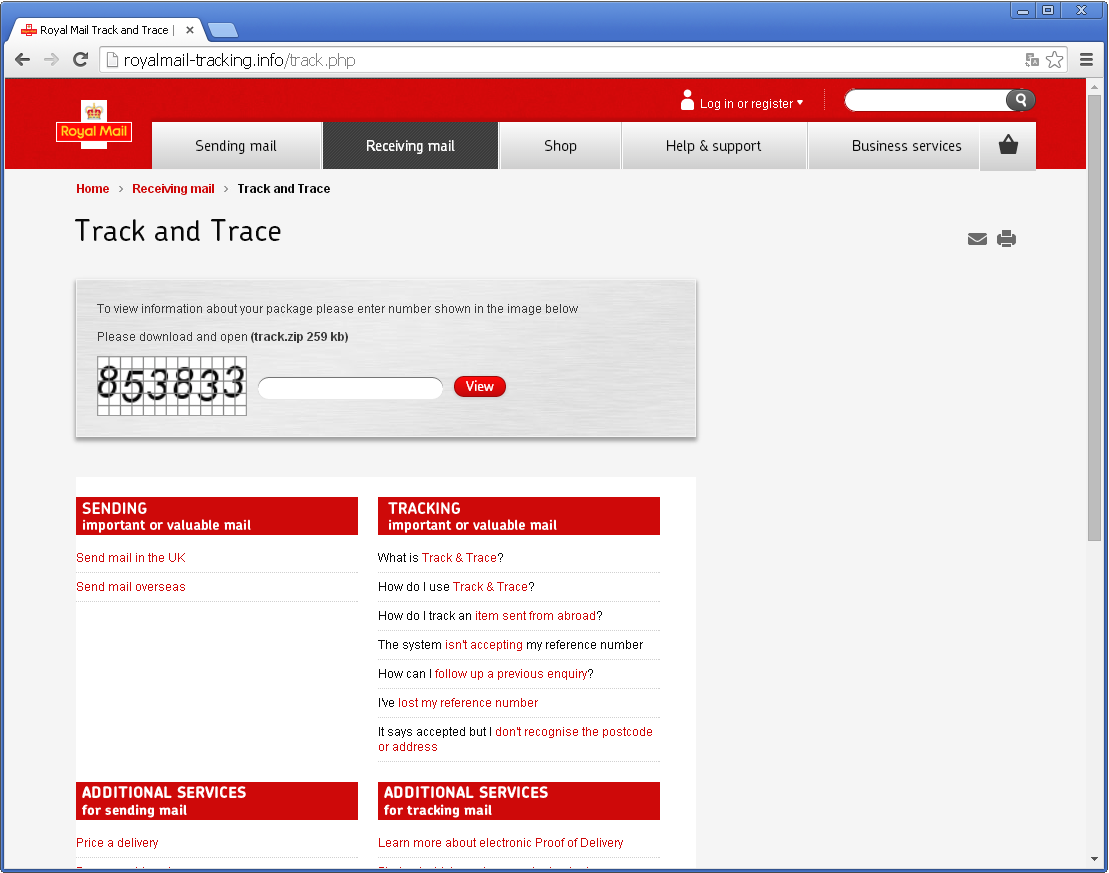
The scheme is the same: you type a captcha then click to download a zip file containing the executable payload. It is interesting to note that the fake Royal Mail page will only show if the visitor is from the UK. Filtering seems to be based on the IP address of the request. If the request does not come from a UK IP address, the victim will be redirected to google.com. Three new domains are hosting the fake Royal Mail page:
- royalmail-tracking.info
- royalmail-tracking.biz
- royalmail-tracking.org
![]() royalmail-tracking.info registration information
royalmail-tracking.info registration information
As you can see, registration date for these domains is September 2nd so this campaign started very recently.
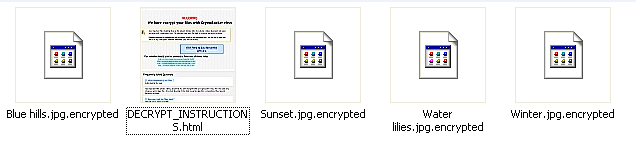 Encrypted files in users’ pictures
Encrypted files in users’ pictures
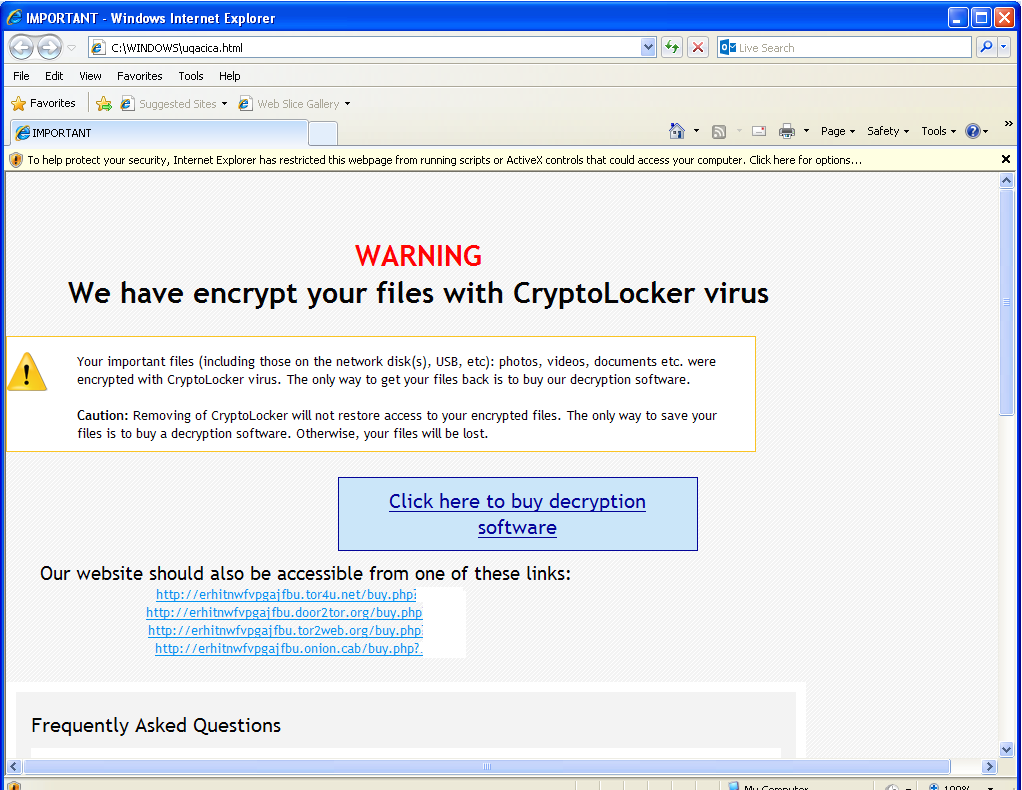 Warning is shown upon execution of the malware
Warning is shown upon execution of the malware
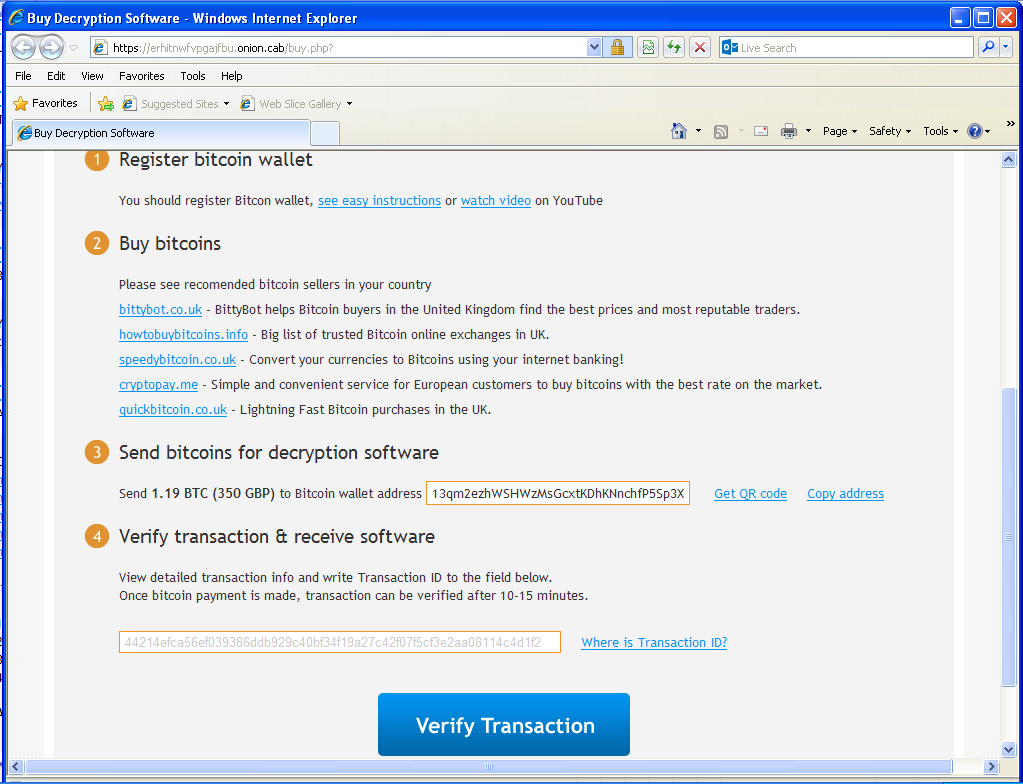
Once installed, victims’ documents are encrypted and they are being asked for a ransom of 350 GBP if paid within 72 hours or 700 GPB otherwise. Payment is done via Bitcoin transaction (1.19 BTC or 2.38 BTC). To hide their infrastructure, the web server is hosted on a .onion host on the Tor network.
To make it is easy for victims to access the web page, TorrentLocker is giving links to Tor2Web nodes so they don’t have to install additional software to reach the .onion website. Interestingly, door2tor.org, the domain name of one of the suggested Tor2Web node, was registered only 2 weeks ago. Perhaps its purpose is only to allow TorrrentLocker’s victims to contact the server selling the decryption software.
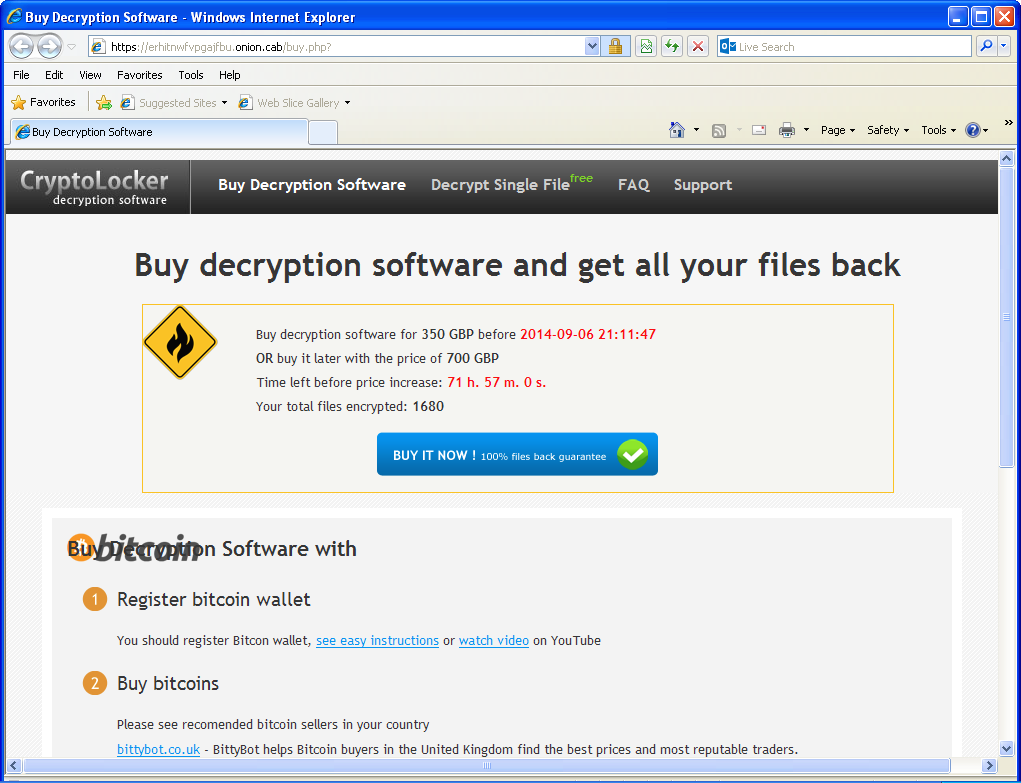 “Decryption software” sold on the Tor network
“Decryption software” sold on the Tor network
This threat caries the TorrentLocker name because it use the “Bit Torrent Application†Windows registry key to store its settings. It is unrelated to the BitTorrent protocol.
The Bitcoin trail
As discovered by iSIGHT Partners, the Australian variant they analyzed asked for Bitcoins to be sent to 15aBFwoT5epvRK69Zyq7Z7HMPS7kvBN8Fg. In our case, the Bitcoin address changed to 13qm2ezhWSHWzMsGcxtKDhKNnchfP5Sp3X. If you look at the transactions on both wallets, the Bitcoins are then transferred to 17gH1u6VJwhVD9cWR59jfeinLMzag2GZ43.
Since March 2014, this Bitcoin wallet has transferred over 82 272 BTC. With 1 BTC currently valued at US$480, the total transactions are roughly equal to 40 millions US$. This wallet has been associated with other scams in the past, including wallet stealing and selling fake mining hardware. We do not know if this account is owner by the TorrentLocker gang or it is some kind of exchange service used by different groups.
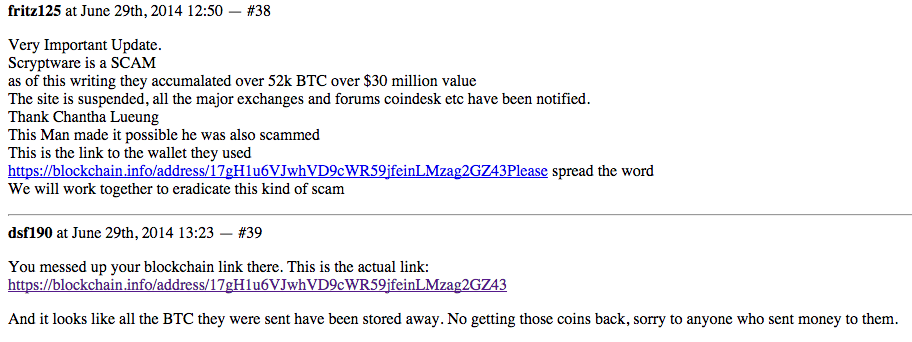 Screenshot of a discussion on Hashtalk (now offline, retrieved from Google Cache)
Screenshot of a discussion on Hashtalk (now offline, retrieved from Google Cache)
ESET products detect this threat as Win32/Filecoder.NCC or Win32/Injector.
SHA-1 hashes
- 491C8276667074B502BD98B98C74E4515A32189B (exe)
- 46A2426D7E062E76D49707B58A5DF28547CBC0F4 (zip)
- 7C62651C5F4CB1C780C8E9C4692F3BF24208A61E (exe)
References
The post TorrentLocker now targets UK with Royal Mail phishing appeared first on We Live Security.
![]()
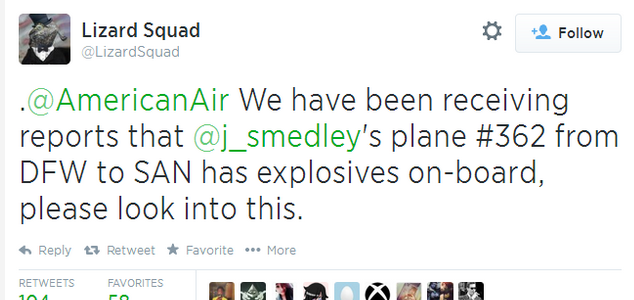
PSN hacked – Network back after cyber attack and bomb threat
Sony’s PlayStation Network was back online on Monday, and the information of its 53 million users was safe, despite a weekend-long cyber attack which left PSN hacked, and a reported bomb threat by the same group which caused the diversion of a flight carrying a Sony executive, according to Reuters report.
A Twitter user with the handle @LizardSquad claimed responsibility for the attack, according to ITV’s report.
Sony summed up in a blog post, “The networks were taken offline due to a distributed denial of service attack. We have seen no evidence of any intrusion to the network and no evidence of any unauthorised access to users’ personal information.â€
One of @LizardSquad’s Tweets said, “”Sony, yet another large company, but they aren’t spending the waves of cash they obtain on their customers’ (PlayStation Network) service. End the greed,”
PSN hacked – and bomb threat issued
The group’s motivation for its attack was unclear. Shack News reported that the group also aimed DDoS attacks at Blizzard’s Battle.net, Riot’s League of Legends and Grinding Gear Games’ Path of Exile.
In a series of Tweets, the group also claimed to be aiming similar attacks at Xbox Live. “We don’t comment on the root cause of a specific issue, but as you can see on Xbox.com/status, the core Xbox LIVE services are up and running,” Xbox spokesman David Dennis said in an interview with Reuters.
Vice commented, “Since Lizard Squad’s fake threat of explosives and media coverage citing it as responsible for the ‘hack,’the group has gained over 15,000 followers on Twitter. One of those followers includes Smedley himself.
Gained 15,000 Twitter followers
In a blog post timed for Cologne’s Gamescom this year, ESET Distinguished Researcher Aryeh Goretsky said, “Computer criminals don’t just target gamers: gaming companies themselves can be targeted as well.  Probably the most well-known example of this is the April 2011 breach of the Sony PlayStation Network gaming and Qriocity music streaming service, which resulted in the compromise of the names, addresses and credit card details of 77 million user accounts.
“ESET provided extensive coverage of the Sony data breach in our blog, starting from the initial report of the breach in April 2011 all the way up to the proposed settlement of a week ago. As a result, I am not going to discuss the details of the Sony breach in this article.
“Readers should be aware that this sort of problem is not unique to Sony, either. Almost exactly, two years ago, Blizzard Entertainment suffered a data breach themselves, although they responded in a different and — this author thinks — more responsible fashion.
The point here is that computer game companies and their associated services face real threats from criminals: if they charge customers for online play, the purchase of in-game items, or otherwise contain customer billing data in their computers, then those computers systems are targets for financial crime.â€
A We Live Security guide to staying safe from cybercriminals while gaming online can be found here.
The post PSN hacked – Network back after cyber attack and bomb threat appeared first on We Live Security.
![]()
Flight MH370 – did cyber attack steal its secret?
Classified documents relating to the missing Malaysian Airlines Flight MH370 were stolen using a carefully-crafted spear-phishing attack, targeting 30 government officials just one day after the disappearance of the still-missing aircraft.
The Malaysian Star claims that the attack targeted officials with a PDF document which appeared to be a news report about Flight MH370, and was sent to a group of investigators. Around 30 computers were infected by the malware.
“We received reports from the administrators of the agencies telling us that their network was congested with e-mail going out of their servers,†CyberSecurity Malaysia chief exec Dr Amirudin Abdul Wahab said.
Flight MH370: ‘Confidential data’
“Those e-mail contained confidential data from the officials’ computers, including the minutes of meetings and classified documents. Some of these were related to the Flight MH370 investigation.â€
Business Insider says that the attack occurred one day after the Boeing 777 went missing, and took the form of an .exe file disguised as a PDF (a common office file format).
It’s unclear who the attacker – or attackers – were, but information from infected computers was transmitted to an IP address in China. Officials in Malaysia blocked the transmission, The Star said.
‘Very sophisticated attack’
Department of Civil Aviation, the National Security Council and Malaysia Airlines were among those targeted by the hacker, the Telegraph reports. The infected machines were shut down, but “significant amounts†of information on Flight MH370 had been stolen.
“This was well-crafted malware that antivirus programs couldn’t detect. It was a very sophisticated attack,†Amirudin said.
CyberSecurity Malaysia suspects the motivation may have been curiosity about supposedly “secret†information held by the Malaysian government on Flight MH370.
“At that time, there were some people accusing the Government of not releasing crucial information,†Amirudin said.“But everything on the investigation had been disclosed.â€
The post Flight MH370 – did cyber attack steal its secret? appeared first on We Live Security.
![]()