Researchers from Dell SecureWorks infiltrated a Nigerian business email spoofing and business email compromise operation, shutting down a number of money mule accounts in the process.
Tag Archives: spearphishing
APT Groups Finding Success with Patched Microsoft Flaw
Researchers at Kaspersky Lab have identified six APT groups using exploits for a Microsoft Office flaw that was patched in September 2015.
Threatpost News Wrap, January 29, 2016
Mike Mimoso and Chris Brook discuss the news of the week, including the latest on the BlackEnergy APT Group, Amazon getting into the SSL certificate game, and government agencies being told to audit their systems for the Juniper backdoor.
Carbanak gang is back and packing new guns
A few days ago CSIS published details about new Carbanak samples found in the wild. In this blog we examine the latest developments in the Carbanak story.
The post Carbanak gang is back and packing new guns appeared first on We Live Security.
![]()
Latest APT 28 Campaign Incorporates Fake EFF Spearphishing Scam
An attack that uses the same path names, Java payloads, and Java exploit as one earlier this summer was found leveraging a fake EFF site.
Darkhotel APT Latest to Use Hacking Team Zero Day
The Darkhotel APT gang has extended its geographic reach to victims in a host of additional countries, and has added to its cache of zero days with its use of a HackingTeam exploit for a Flash zero-day vulnerability.
Don’t take the bait: Beware of web attack techniques

When it comes to cybercrime, it’s always better to be in the know. Here are a few ways that web attacks can find their way onto your device. Don’t be fooled — most cybercrooks design attacks to take place where you’d least expect it.
-
Social engineering preys on human weakness
“A lot of attacks are still using social engineering techniques; phishing emails – ways of convincing the user to give up valuable information,” said Avast CEO Vince Steckler.
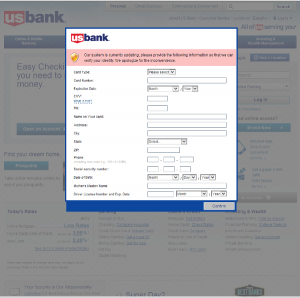
In a phishing or spearphishing attack, hackers use email messages to trick people into providing sensitive information, click on links, or download malware. The emails are seemingly sent from organizations or individuals the potential victims would normally get emails from, making them even more deceptive. Last July, Avast took a look at the Tinba Trojan, banking malware that used spearphishing to target its victims.
An example of an injected form from Tinba Trojan targeting U.S. Bank customers.
Web attacks also take place through SMS Text Phishing, also known as SMSishing. This method has become one of the most popular ways in which malicious threats are transmitted on Android devices. These text messages include links that contain malware, and upon clicking them, the malicious program is downloaded to the user’s device. These programs often operate as SMS worms capable of sending messages, removing apps and files, and stealing confidential information from the user.
-
Malicious apps attempt to fool you
Malicious programs can disguise themselves as real programs by hiding within popular apps or games. In February, we examined malicious apps posing as games on Google Play that infected millions of users with adware. In the case of malicious apps, cybercrooks tamper with the app’s code, inserting additional features and malicious programs that infect devices. As a result, the malware can attempt to use SMSishing in order to collect additional data.
The Durak card game app was the most widespread of the malicious apps with 5 – 10 million installations according to Google Play.
-
Ransomware uses scare tactics that really work
Another name that made headlines was a group of malware dubbed ransomware, such as CryptoLocker, and its variants Cryptowall, Prison Locker, PowerLocker, and Zerolocker. The most widespread is Cryptolocker, which encrypts data on a computer and demands money from the victim in order to provide the decryption key. Avast detects and protects its users from CryptoLocker and GameoverZeus.
Make sure you back up important files on a regular basis to avoid losing them to ransomware. Ransomware made its way from desktop to Android during the year, and Avast created a Ransomware Removal app to eliminate Android ransomware and unlocks encrypted files for free.
Count on Avast apps to keep mobile malware at bay
To keep your devices protected from other ransomware, make sure to also install Avast Free Mobile Security & Antivirus from the Google Play store. It can detect and remove the malware before it is deployed.
Install Avast Ransomware Removal to find out if your Android devices are infected and to get rid of an infection. Avast Ransomware Removal will tell you if your phone has ransomware on it. If you are infected, it will eliminate the malware. Android users who are clean can use the free app to prevent an infection from happening.Once installed, you can easily launch the app to scan the device, remove the virus, and then decrypt your hijacked files.
PlugX, Go-To Malware for Targeted Attacks, More Prominent Than Ever
The popular remote access tool PlugX enjoyed an ascent in popularity in 2014 and is now a go-to malware for attack groups.