Avast & AVG Technologies combine together to power the latest in flagship security and tune-up products to tackle ransomware, hackers and data thieves, while keeping PCs fast and clean.
Prague, Czech Republic, January 10, 2017 – Avast Software, the leader in digital security products for consumers and businesses, today announced the release of the 2017 editions of AVG’s flagship products, AVG AntiVirus FREE, AVG Internet Security and AVG TuneUp. Released less than 120 days after Avast’s acquisition of AVG, these new products combine the best of both Avast’s and AVG’s technology to deliver unrivalled, family-friendly, security protection together with performance enhancements for customers’ PCs, and a clean, simple look and feel.
People using the AVG AntiVirus FREE and AVG Internet Security products will now gain real-time protection against ‘zero-second’ malware thanks to CyberCapture, the company’s proprietary, cloud-based smart file scanner. The latest versions protect users from viruses and malware including ransomware, prevent hacking, secure web and email activities, and ensure that private data stays private. The new user interface makes it very easy to install, navigate and manage all from one place.
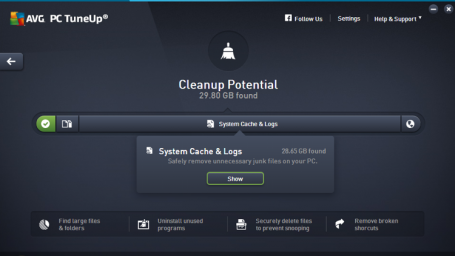
A free performance scan using AVG TuneUp has been integrated into the security products to help customers reduce data clutter and keep their PC running smoothly. The full AVG TuneUp product is enhanced with a completely new Software Updater tool which automatically checks and installs the latest updates for the most popular and critical PC applications to eliminate vulnerabilities, fix bugs and add new features.
- AVG AntiVirus FREE: the rapid increase in the quantity and impact of cyber threats today means protecting every PC is more important than ever before, and free users now benefit from:
- Computer Protection: real-time protection that updates people’s security automatically and keeps their computers free of viruses, spyware, ransomware, rootkits, Trojans, and other nasty malware. Using advanced artificial intelligence and real-time analysis, it stops even the newest threats from reaching users.
- Web & Email Protection: blocks unsafe links, downloads, and email attachments.
- Pushed Priority Updates: ensures immediate protection and was previously only available in the paid edition.
- New Passive Mode: allows people to personalize their security by allowing them to run two protection products together on their PC.
- New Online Shield: scans for dangerous websites, links and downloads to keep users safe while they visit their favorite websites.
- AVG Internet Security: for ironclad protection, users can upgrade to AVG Internet Security which additionally stops hackers, protects private data and secures payments.
- Hacker Protection: Prevents cybercriminals from accessing users’ private files, photos, and passwords.
- Private Data Protection: Allows users to encrypt and hide their most private photos and files, or permanently shred unwanted material.
- Payment Protection: Ideal for browsing, shopping, or bank protection. It blocks spam and scams, and helps people avoid fake copycat websites to prevent them from accidentally giving passwords or credit card numbers to the bad guy. Uses Avast Secure DNS to protect online payments made, includes Anti-Spam feature.
- New Secure DNS feature: verifies a website’s IP address using secure DNS servers to ensure the user is not being redirected to fake websites when shopping or banking online, therefore protecting people against fraud, scams and phishing attacks.
- AVG TuneUp: users can enjoy a range of new and improved features:
- Automatic Software Updater: AVG TuneUp builds on its core strengths of clearing out unnecessary files and improving PC performance using patented technologies to update most used applications, like Skype, Adobe reader, Flash and Chrome, automatically and silently in the background. AVG customers can choose to rely on the automatic updates, or perform manual checks as desired.
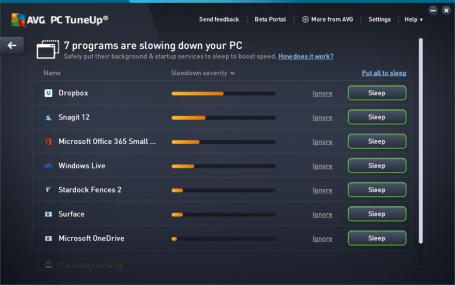
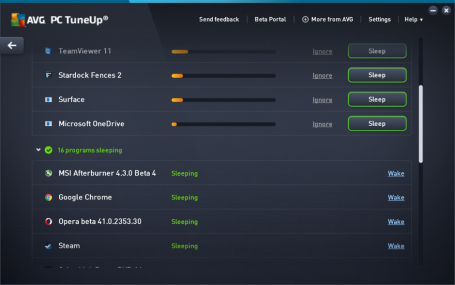
- Sleep Mode: AVG TuneUp’s patented enhanced Sleep Mode technology improves speed by putting unused applications to ‘sleep’ and only running the necessary ones. This reduces battery and network drain to a minimum so PCs perform like they are just out of the box.
Vince Steckler, Chief Executive Officer at Avast, said, “The combination of AVG and Avast threat detection and analysis capabilities gives us unparalleled insight into cybercrime trends. We tracked, for example, that ransomware alone increased by over 105% between 2015 and 2016 and, based on our data, predict that this is only going to soar. Consumer awareness of security exploits is also at its height given the many ransomware and hacking incidents reported last year. In an age where we are all connecting more of the time, security is becoming a conscious decision and we encourage people to pick the products that are right for their particular needs.”
Download AVG AntiVirus Free, AVG Internet Security and AVG TuneUp at www.avg.com.
About Avast
Avast Software (www.avast.com), the global leader in digital security products for consumers and businesses, protects over 400 million people online. Avast offers products under the Avast and AVG brands, that protect people from threats on the internet with one of the most advanced threat detection networks in the world. Avast digital security products for Mobile, PC or Mac are top-ranked and certified by VB100, AV-Comparatives, AV-Test, OPSWAT, ICSA Labs, West Coast Labs and others. Avast is backed by leading global private equity firms CVC Capital Partners and Summit Partners.
![]()
![]()