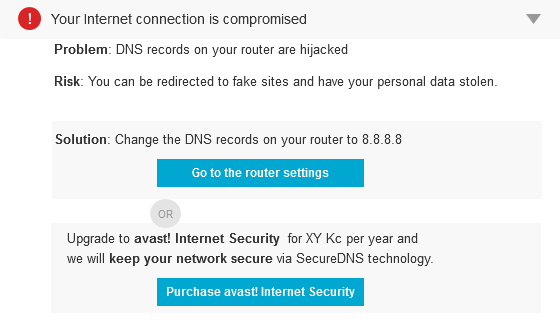
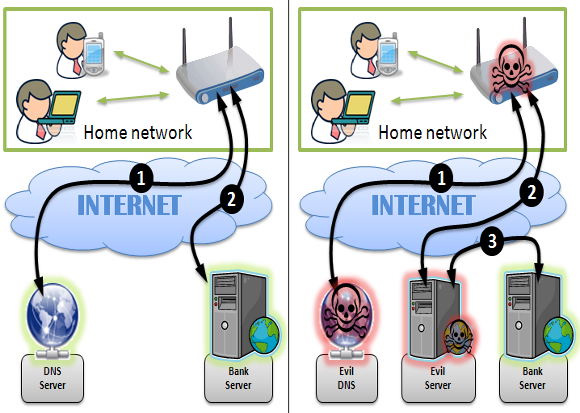
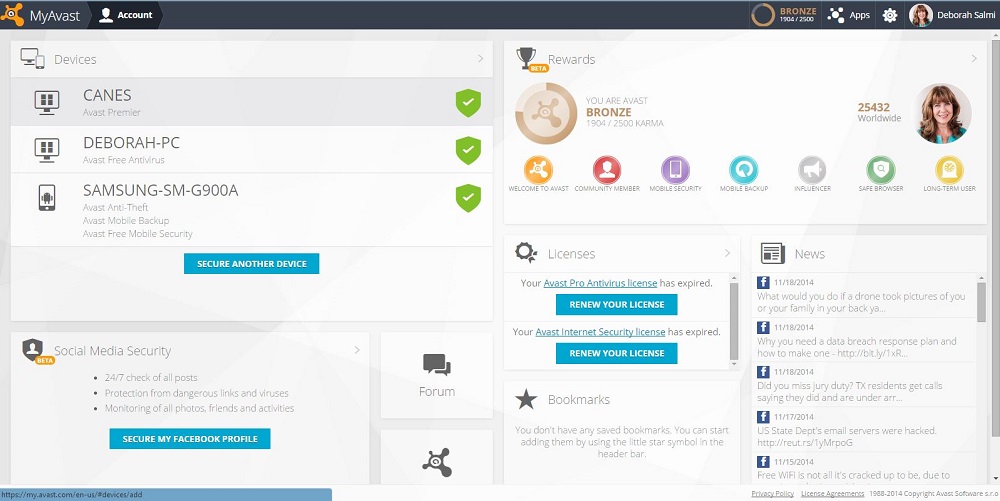
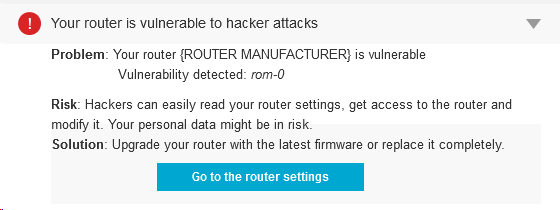
The Avast Mobile Security team showcased secure solutions for payment, identification and mobility at the CARTES conference.
The Avast Mobile team had a couple of busy days in November – we participated at CARTES Secure Connexions 2014 and showcased some of our best mobile apps in the “Mobile payments†pavilion. In our traditional and authentic guerrilla style, we drove a truck to Paris, we built the stand ourselves (and almost got killed dismantling it the last day), and we greeted our friends and product users in person, with no external hostesses; only Avast Mobile crew members equipped with mint candies, product fliers, and an unlimited dose of enthusiasm. 

You may ask yourself, what was my mobile antivirus provider doing at CARTES, a global event for the digital security industry?
Because of the experience the Inmite acquisition brought to Avast Mobile, the Avast team knows a thing or two about mobile payments security, and we believe we can bring additional value to this topic with our products.
Mobile payment security starts and ends with the customer
While there are many techniques app makers or payment institutions such as a banks use to secure their mobile applications, recent attacks show that the weakest part of the chain are end clients – in other words – you and me. Face it, most people tend to underestimate potential threats, they fall for phishing attacks or attacks by social engineering, they connect to insecure public Wi-Fi hotspots, and they know in most cases, that banks will handle possible issues they have gracefully. In many cases, banks will even refund complete financial loss in order to keep their reputation high. The value Avast can bring to the table is the fact that most of our solutions are oriented towards the end users and their devices – we help where the additional help is needed.
 Securing your mobile device better is simple
Securing your mobile device better is simple
At CARTES, we presented three products for mobile:
This selection of products was not random. Each of the products protect people and their payments at different “stagesâ€.
AIR BOND is our patent pending HW authentication token based on Bluetooth Low Energy. It wirelessly communicates with your smartphone or tablet and co-signs your transactions before they are sent to the server. It requires no special effort, like rewriting a numeric code or putting an NFC tag close to your iPhone (that does not support NFC this way anyway ;-). )You can use your mobile banking or payment app as long as your AIR BOND is nearby. If you lose your phone or somebody steals it, your banking is instantly safe – proximity to the AIR BOND device is required in order to execute transactions (all of them or only some of them depend on AIR BOND deployment type at each individual bank).
SecureLine VPN is an easy-to-use VPN solution for mobile and desktop. You can download the app from the iTunes App Store or from Google Play, turn the switch on and use your phone normally. No special setup is needed on your end; we take care of the server infrastructure and all the nasty configuration that is usually required for VPN solutions to work.
SecureLine encrypts and anonymizes your communication while your payments are being sent to the server. Since most of the mobile communication happens in the public space, often at an unknown and improperly secured Wi-Fi hotspots, this mechanism brings a great deal of “practical security†to normal people. Most of the current network security issues are with the nearest router or with ISP infrastructure – basically in the first 10 miles of communication.
 Avast Mobile Security & Antivirus is the hottest mobile product today and it recently got a major facelift in order to become even more sleek and sexy. It is an Android app that includes antivirus, anti-theft (must be installed separately to the app, since anti-theft goes deep in the system), and several very handy security / privacy features, like App locking (adds a PIN code login screen to any app you have), or Call & SMS filter (blocks annoying calls and unwanted SMS messages). This application can protect your payments when your Android phone is under fire and everything is about to go wrong. For example, when you install a potentially malicious application, or when you lose your phone or somebody steals it from you, this app is here to protect you.
Avast Mobile Security & Antivirus is the hottest mobile product today and it recently got a major facelift in order to become even more sleek and sexy. It is an Android app that includes antivirus, anti-theft (must be installed separately to the app, since anti-theft goes deep in the system), and several very handy security / privacy features, like App locking (adds a PIN code login screen to any app you have), or Call & SMS filter (blocks annoying calls and unwanted SMS messages). This application can protect your payments when your Android phone is under fire and everything is about to go wrong. For example, when you install a potentially malicious application, or when you lose your phone or somebody steals it from you, this app is here to protect you.
Every bank should suggest security products to their clients
In my personal experience, banks and payment institutions usually make mobile apps that are reasonably well secured in their implementation. However, security is a complex issue where an interplay of many components is needed to achieve good results. Protection at the end user level is one of these components, being a valuable addition to the built-in application security or security implemented within the bank’s back-end systems.
Banks and other payment institutions should educate their clients and recommend  products that protect their accounts and payments on their devices. Does your bank do that for you? If not, this is an opportunity – help us spread the word about Avast products! 
Did you like the article? Follow the author at @joshis_tweets.
Avast Software’s security applications for PC, Mac, and Android are trusted by more than 200-million people and businesses. Please follow us on Facebook, Twitter and Google+.
![]() Despite the orange color all over the place, Avast is a Prague- (that beautiful city in the Czech Republic that you read about in the travel magazines) based company with offices all over the world including Silicon Valley, Austin, Munich, and Hong Kong.
Despite the orange color all over the place, Avast is a Prague- (that beautiful city in the Czech Republic that you read about in the travel magazines) based company with offices all over the world including Silicon Valley, Austin, Munich, and Hong Kong.