Information security has become an even more critical factor of the business model, as it protects the most essential asset: information.
The post 5 steps to take after a company is infected appeared first on We Live Security.
Information security has become an even more critical factor of the business model, as it protects the most essential asset: information.
The post 5 steps to take after a company is infected appeared first on We Live Security.
Do your friends and family always call you when they run into a problem with their computer? Forget driving across town to help them out – if they are also Avast users, you can remotely access their computer.

Avast Remote Assistance makes it a lot easier on the family IT person.
If you are the IT expert, the person in need of help has to request assistance from you. Instruct them to open the Avast user interface. The easiest way to find it, is to go to one of the four tiles on the Overview screen, and click on the small menu icon in the top right corner. A drop-down selection will open. Choose Remote Assistance.
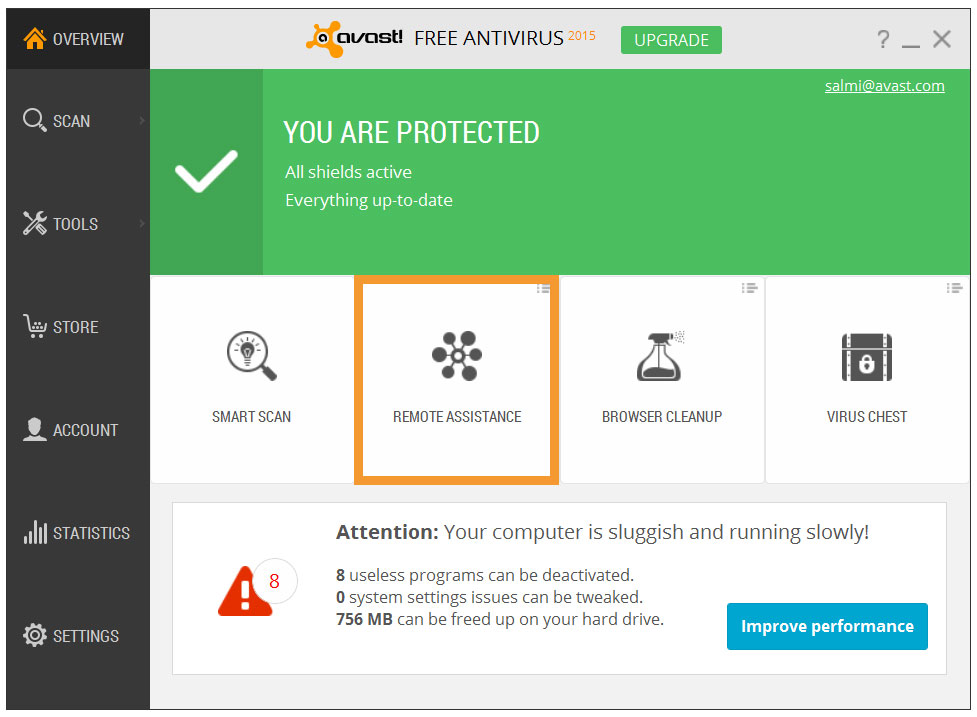
Customize your Avast Overview screen for fast access.
Next, tell them to click the blue Get Assistance button. Avast will generate a code that they need to provide to you. They can transfer the code to you by telephone, email, or chat. Make sure they understand that by sending the code they are granting you remote access to their computer. After you take control, this dialog disappears automatically.
When you receive the code, you will copy it into the box on your Avast’s Remote Assistance screen. Follow the directions to connect. When the connection is established, this dialog disappears and the remote desktop window appears.
To close the connection, press the Alt+Shift+End shortcut.
Today is World Backup Day, and it goes without saying that backing up data is a thoroughly sensible thing to routinely get into the habit of doing.
The post Six ways to backup your data appeared first on We Live Security.
The pressure for businesses to allow their employees to access work resources with their personal mobile devices may be overwhelming. How can healthcare IT and Security staff implement this without giving criminals the keys to the castle?
The post The future of security in healthcare: Mobile devices appeared first on We Live Security.
The Avast Virus Chest is a safe place to store potentially harmful files. These files are completely isolated from the rest of the operating system, meaning that they are not accessible for any outside process or software application. Files cannot be run while stored in the Virus Chest.
To open the Virus Chest, right click on Avast’s little orange ball icon in the system tray in the bottom right hand corner of your computer. Select Open Avast user interface from the menu. Another way to open the user interface is to double click the desktop icon.
From the main menu, select Scan, then Scan for viruses, and then click the Quarantine (Virus Chest) button at the bottom of the screen to open the Virus Chest window.
If Avast 2015 detects an infected or suspicious file, it will try to repair it at first. Unfortunately, some files cannot be repaired so Avast will try to move the file to the Virus Chest. If the infected file refuses to move to the Virus Chest, it will be automatically deleted from your computer.
For quick access to the Virus Chest, you can assign it to one of the four shortcut squares in the Avast user interface. To change which function you see, click on the drop-down menu icon in the top right hand corner of the square. There you will find a choice to place the Virus Chest right on the Overview of your Avast product.
Once you have the shortcut on the user interface, then simply click it to open the Virus Chest.
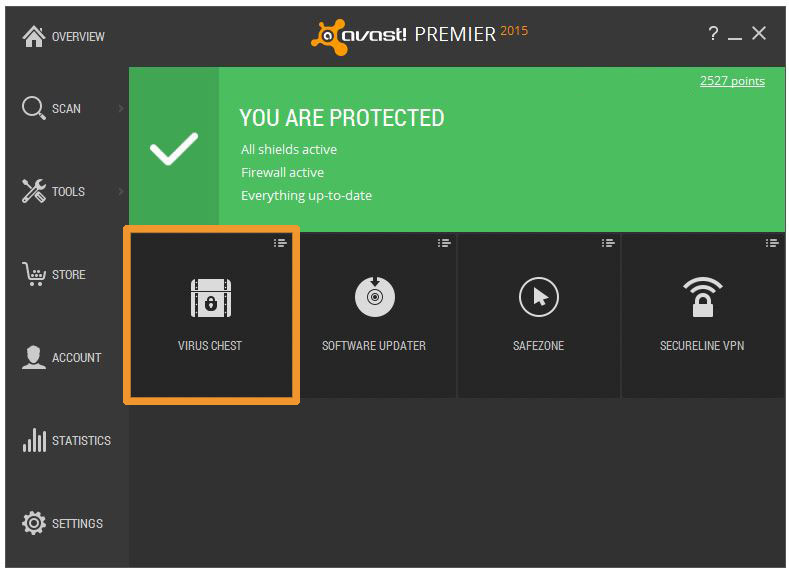
Set the shortcuts that you want in the Avast user interface.
You can perform different actions on the file inside the Virus Chest by right clicking. For example, you can
Once you have made the decision on which action to take, you will be asked to confirm your choice. When you have finished, close the Virus Chest to exit.
NOTE: Exercise extreme caution when restoring a file from the Virus Chest as it may still be infected. This is a high security risk action that requires advanced skills and experience handling infected files to avoid further potential infection of your computer.
If you need to move a file manually into the Virus Chest, right click anywhere on the contents table on the Virus Chest screen and select Add from the menu. A navigation dialog will open so all you need to do is locate the desired file that you want to move. Then click the Open button. The desired file will then appear in the contents table on the Virus Chest screen.
When you open the Virus Chest, you will see a list of files contained within it. Right click on the file that you want to restore and the drop-down menu will appear. Select the Extract option, then select the location to save the file and click OK to close your window.
Criminals are targeting medical records because of their value, and as a result, medical breaches are the fastest growing type of breach. What can healthcare businesses do to get themselves out of the crosshairs?
The post Premera Breach: Healthcare businesses in the crosshairs appeared first on We Live Security.
Heimdal asked a range of security experts for their essential security tips. 19 experts (including David Harley) offered over 50 tips.
The post Heimdal blog, 19 Experts, 50+ Security Tips appeared first on We Live Security.
There have been some high-profile Bitcoin thefts recently. Here are 10 tips on protecting your virtual bitcoin wallet.
The post 10 tips for protecting your virtual Bitcoin wallet appeared first on We Live Security.
Social media is a great way of communicating with friends and family, but’s also a fantastic tool to meet new people with similar interests. You should be careful though, as popular social networks can have fake accounts which can pose a risk to your privacy or security.
One way to help stay safe is to learn how to spot these fake accounts and how to report them to the social network.
Beware of bio links
Spammers, scammers and hackers often use links in their Twitter bios (as as their feed) to get users to visit malicious sites.
Compare their followers
Fake or spam Twitter accounts follow thousands of users of users but have very few followers themselves
Watch out for strange mentions from strangers
You may get a random tweet from or mention thats makes no sense, This is often a sure sign that it’s a fake or malicious account
Beware of links tweeted with popular hashtags
Scammers often use trending or popular hashtags to tweet malicious links or get you to view their bio link
Until next time, stay safe out there!
Lenovo’s installation of a security-breaking app called Superfish on some computers has customers justifiably angry, but some folks are now unnecessarily confused by false positive detection.
The post Lenovo and Superfish? Don’t panic, you may not be affected appeared first on We Live Security.