The security stakes only seem to be rising when it comes to the threats that affect us as modern-day consumers.

What behavior could a smart appliance reveal about you?
Over the past year, we have seen a list of notable mobile threats that put people’s privacy at risk. Previously unseen vulnerabilities surfaced, such as Certifi-gate and Stagefright, both of which can be exploited to spy on users. Certifi-gate put approximately 50 percent of Android users at risk, and Stagefright made nearly 1 billion Android devices vulnerable to spyware. In 2015, for the first time, cybercriminals were able to attack users on a vast level.
Another mobile threat on the rise in 2015 was mobile ransomware, using asymmetric cryptography, making it nearly impossible to recover the encrypted data on a smartphone. The most common mobile threats in 2015 were adware — often apps disguised as fun gaming apps that provide little value and spam users with ads. We believe that 2016 will be the year in which we see threats moving from smartphones to smart homes — and beyond.
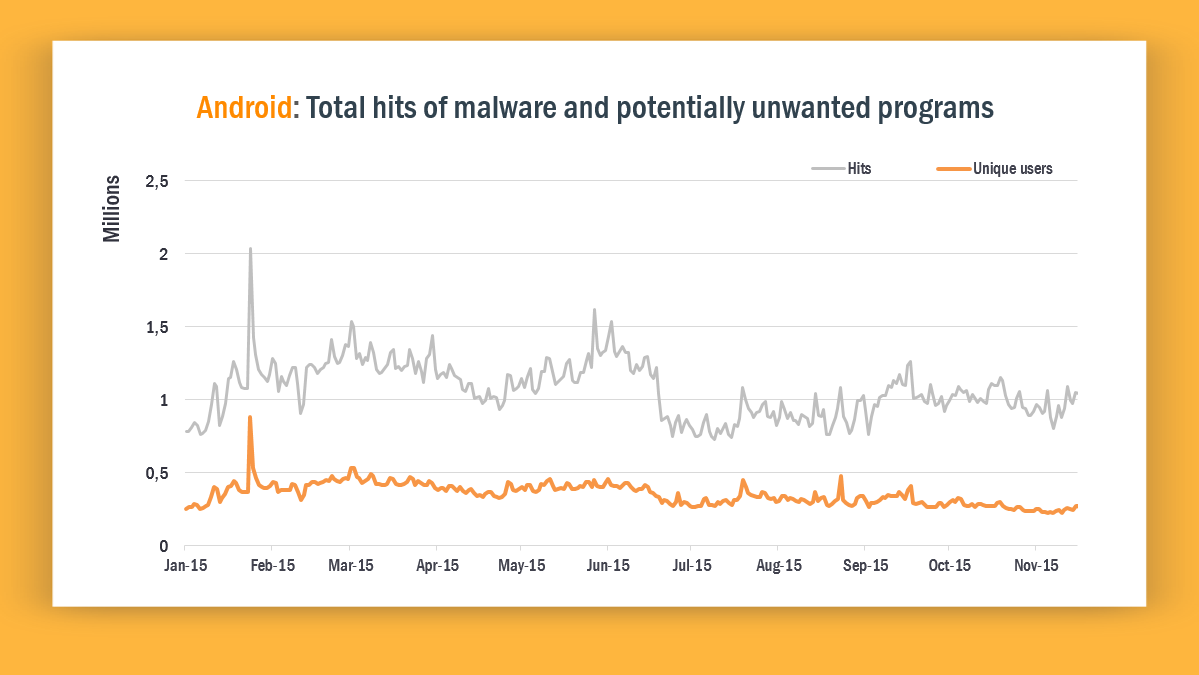
Total number of attacks on Android devices that Avast has detected in 2015
2016: Internet-connected devices will spell out your life to anyone who’s curious
In 2015, society has gotten a taste of what the future might look like with the rise of Internet-connected devices. While we’ve now become accustomed to our smartphones, the possibilities for both users and hackers are growing exponentially when it comes to gadgets and systems that comprise the budding Internet of Things (IoT).
We often forget about many of the devices that, in reality, fit into the “smart” category. Smart devices and gadgets can include anything from thermostats to microwaves, smart locks to smoke detectors to children’s toys. Since we make use of these gadgets in our daily tasks and endeavors, an attack on their security could result in dire threats to our privacy and security.
Smart devices, such as household appliances, cars and wearables are basically our life companions. Unlike a smartphone, which holds information about our communications, contacts, photos and videos, smart devices reveal more specific information about our behavior, such as our driving, fitness, and cooking habits, or our children’s learning behavior.
This provides optimal opportunities for hackers to target personal data, including information collected by wearable, Internet-connected devices. What’s more, this data can be used by governments for law enforcement purposes and for businesses, like insurance companies, to restrict payments or medical procedures from people who may have previously made unwise financial or health-related decisions. This year, we could see the first country enact a law that would give certain industries authorization to exploit consumer data through information collected by smart devices.
Ransomware that could turn your devices against you
We already know how dangerous ransomware can be — this aggressive malware family locks individuals out of their devices and renders them useless, leaving users with little choice other than to pay a specified amount of money demanded by hackers in order to regain access to their device. On a smartphone, a factory reset helps to remove the ransomware, and if the user has conducted a backup, the harm is minor. However, if and when ransomware makes its way into the IoT sphere, we must be prepared in order to prevent our own devices from being manipulated and turning against us.
But 2016 could be the year when we witness our first serious car hack. This year, Land Rover has recalled 65,000 cars from the market because of a software bug that could lead to car theft. Taking this point a step further, imagine if your car’s software actually locked you out of your primary mode of transportation. What lengths would you go to if your personal security system locked you out of your own home? There’s a good chance that these issues will need to be dealt with as we move into the heyday of IoT.
Kids’ safety: toys that put children’s privacy at risk
Now, people should think twice before buying their children the newest trinket that they see in the window — while seemingly harmless, children’s toys can be wolves in sheep’s clothing when it comes to security. This can be seen in the recent VTech scandal, around the toy manufacturer of network-enabled learning toys that stored email addresses, physical addresses, passwords, as well as names and birth dates of more than 6 million children without proper protection measures. Another example is the Internet-connected Hello Barbie doll that was vulnerable to hackers who could spy on children talking to their dolls.
These two examples could be the start of an uprising in hacks in 2016 that jeopardize kids’ privacy. No longer are parents the only ones taking photos of their children — with smart kids’ devices storing photo and video footage, leaked files could easily make their way into the wrong hands. These files are then sent to servers, and often, it remains unclear what happens to these files, how they are secured and whether or not they are shared with third parties.
Children’s toys even have the ability to potentially affect a child’s success later in life — if schools choose to examine data supplied and exploited by Internet-connected educational toys, admittance processes could change, resulting in children’s lives being directly affected.
New year, new threats on the horizon
When it comes to dealing with security threats in 2016, the rule of thumb is this: Consumers should always stay one large step ahead of their smart devices. As these gadgets continue to obtain more capabilities and gather more of our information, it’s important that we retain our common sense when managing our security and personal privacy. Making use of security solutions on both computers and mobile devices is a reliable way to ensure that consumers remain in control of what belongs to them. While staying protected, we can confidently look forward to what’s in store as the new year continues to unfold.

![]()



