More than five percent of all unique IP addresses accessing Google sites included some kind of ad injector software, and there are more than 50,000 of those injector browser extensions in use today, according to new research from Google.
Tag Archives: Privacy
Commercial Use for Drones Gets a Boost from FAA
This past weekend Drones, Data X Conference took place in Santa Cruz, CA where between 550 and 1,000 inventors, investors, regulators and the general public got to see what the future of drones may look like.
The big news from the conference came on Friday when Jim Williams, who is in charge of the FAA’s Unmanned Aircraft Systems (UAS) Integration Office, (UAS are drones for the rest of us) told a rapt audience that the FAA is re-considering its “line of sight” mandate. Basically, the line of sight rule means just that — that drones must be in the sight of their operators at all times.
Specifically, the FAA last summer announced a list of ‘do’s and don’ts’ regarding model aircraft, mostly focused on keeping them away from airports and within sight line of the user. The FAA followed this up with proposed regulations this February that would limit flights to daylight and visual-line-of-sight operations. The rule also addresses height restrictions, operator certification, optional use of a visual observer, aircraft registration and marking, and operational limits. (You can read more about it here.)
The line-of-sight rule has been key for businesses. You can imagine the chilling effect this proposed rule had on companies that were viewing drones as a key technology delivery method to add to their services, or, really for a hundred other commercial uses, from real estate to agriculture and more. So, this apparent change of view on the part of the FAA is huge.
“We understand there’s a lot of value in flying out of line of sight and that’s one of the areas we’re looking to get ahead rapidly in the next few years,” Williams said, in his presentation on Friday. (You can see a video from Mashable here.)
This has to be welcome news for those in the commercial food chain, from giant companies like Amazon to small start-ups dreaming up ways to use drones commercially. (Of note, Amazon Prime Air was a sponsor of the event).
If drones can be used safely, there are millions of great commercial and humanitarian uses ahead: from product delivery (including pizzas!) to autonomous personal air transportation via drones (hello Jetsons!), to rescuing lost hikers and delivering life-saving supplies in emergency situations, among those discussed at last week’s conference.
What also strikes me is that many of the same technologies that are coming to self-driving cars will be a way to ensure drone safety as well. Sensors, radar, lasers, cameras, and mapping technology all come into play.
“Every home is going to have a drone pretty soon,” predicted Parimal Keparekar, who works for NASA in air traffic management research, and is quoted in the Santa Cruz Sentinel describing efforts to build a highway in the sky for them. “Right now there is no congestion management problem, but eventually there will be.”
There’s still a lot to be figured out before that day arrives, including more focus on associated privacy and data concerns.
While the FAA works on getting the rules down, NASA Unmanned Aerial Systems announced it will host a UAS Traffic Management Convention, July 28-30 at NASA Ames Research Center, Moffett Field in Mountain View, CA. The focus will be on “low altitude traffic management with reference to policy issues such as privacy, safety and security, emerging markets and international perspectives.” To learn more and register: SVC-AUVSI.org.
![]()
![]()
Usbkill Script Can Render Computers Useless
The idea of needing to disable a computer quickly as the police–or another potential adversary–comes through the door typically has been the concern of criminals. But in today’s climate activists, journalists, and others may find themselves wanting to make their laptops unusable in short order, and that’s where usbkill comes in. The new tool is a […]
Mozilla Moving Toward Full HTTPS Enforcement in Firefox
The Mozilla Foundation announced yesterday that it is in the process making HTTP connections incompatible with its popular Firefox Web browser.
Unpredictability is key in password strength
The latest report from infosec provider Praetorian suggests that when it comes to hacking a password, the sequence and consistency of the characters is just as important as the actual strength of the password itself.
Using a technique called a mask attack, attackers break a password down into their component elements such as upper case letters (u), lower case letters (l), digits (d) and symbols (s).
In their example, Praetorian used “Password1234” which when viewed in this system becomes “ullllllldddd”. This string of letters is known as a mask. Each letter in the chain denotes the character type (u= upper case).
Using this technique, Praetorian analysed nearly 35 million leaked passwords from various sources. What they found was surprising.
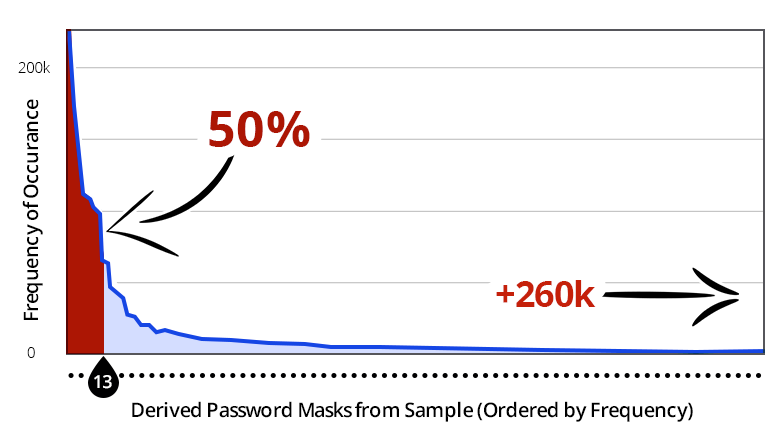
Of the 35 million analysed passwords, half of used the same 13 masks. This means that despite the millions of variants of characters, digits and symbols, in our passwords, as many as half of us are using a very limited selection of masks.
Naturally our predisposition for these certain masks makes our passwords much easier to hack. Not to mention that many people also use dictionary words and personally identifiable information in their passwords.
Why do we behave like this?
Praetorian posits that our preference masks is down to the way that we are informed to create strong passwords. A simple example of this would be to use a capital letter in the password. Conventional behavior leads us to use it at the start of a password and use symbols such as ‘!’ at the end.
How to improve your password safety.
The most important thing to do to help make your passwords more difficult to crack is to use an unusual mask. Don’t be tempted to start your password with a capital and insert your symbols and digits somewhere other than the end.
Password managers can also help you generate strong, long and random passwords that use a wide variety of masks.
![]()
![]()
Congress, Crypto and Craziness
A Congressional hearing on encryption and “frontdoors” produced a generous amount of the usual “crazy” from lawmakers and law enforcement.
Social Networks: How Their Privacy Settings Compare
Particularly Facebook has often been the in the media when it comes to privacy issues and concerns. But do you really know what can and cannot be set in the sometimes rather confusing options? And what about all the other social networks likes Twitter, LinkedIn, and Google+?
ITWorld decided to check out the top social networks and compare their privacy setting – in one handy chart. The list of things they checked out for you is rather extensive and includes the following points:
- Profile visibility limits upon sign-up
- Control how people can search for you
- Control who can connect with you
- Control whether people can message you
- Control who can see your connections
- Prevent users from tagging you in posts
- Choose who can see your photos
- Block users
- Opt out of photo tagging
- Disable facial recognition
- Opt out of search engine indexing
- Review recent logins
- Set login alerts
- Enable two-factor authentication
- Automatically supports a secure connection
- Control connected applications
- Limit data sharing with third-party apps
- Turn off location tracking
- Delete location information
- Manage advertising
- Opt out of all advertising
- Request an archive of your data
- Delete your account
Just head over to ITWorld to read the whole article which also includes instructions for finding and updating these options in the different social networks.
The post Social Networks: How Their Privacy Settings Compare appeared first on Avira Blog.
You can now download your Google Search history
When it comes to significant historic events, we can all remember where we were when we first heard the news. I can remember where I was on 9/11 and when man landed on the moon but can you remember what you searched for on the 29 November 2012?
Chances are you can’t, but it’s now possible to find out.
Search engines like Google can collect vast amount of data about us that can be used to build a profile of our interests, hopes, fears and activities. Imagine everything you searched for being stored and later analyzed.
College years, holidays, medical conditions, online dating, buying a car, having children or just my news preferences are all there in the keywords that I use when searching for content.
Is there any need for either you or anyone else to have this personal view into your life?
Two years ago, I switched off storage of Google search history with no noticeable effect on my ability to find things. On the other hand, I am sure its inconvenienced a couple of companies that would love to target me for advertising.
Google recently announced the ability to download your entire search history, which if you have a Google account is collected by default. This is a little known feature that comes with a forewarning about the sensitive nature of the data.
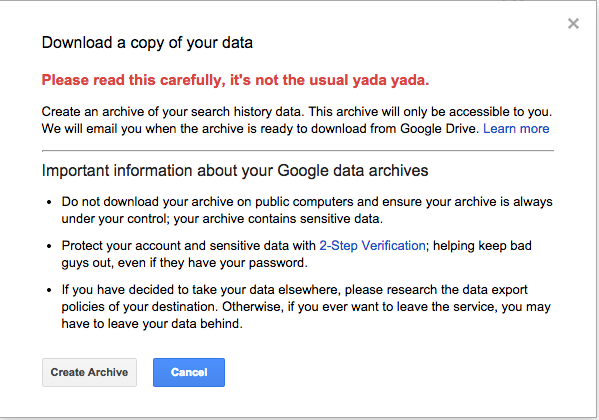
If the data is so sensitive then why was there no warning that someone was collecting it to start with? Maybe it should be an optional feature that I could choose to switch on?
I recommend that you make a conscious decision on whether someone needs to be collecting this or whether you feel that you may need this for some reason in the future (if you can think of one please let me know).
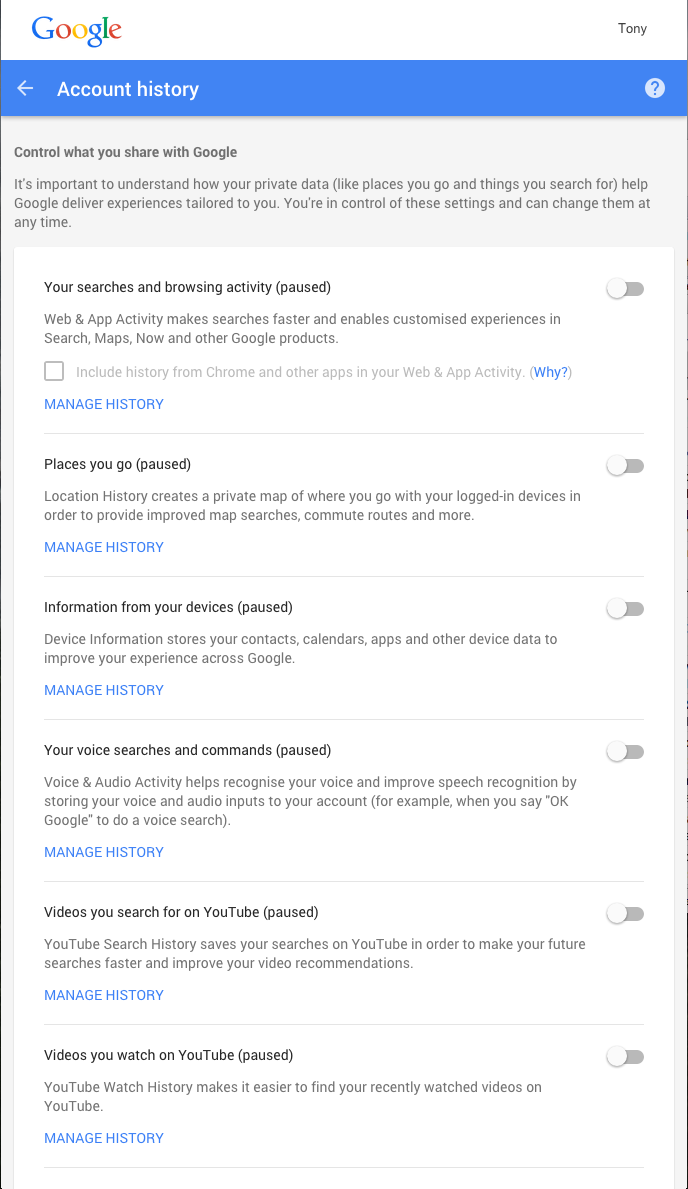
Changing the history storage options is in your Google account settings in the ‘Account Tools’.
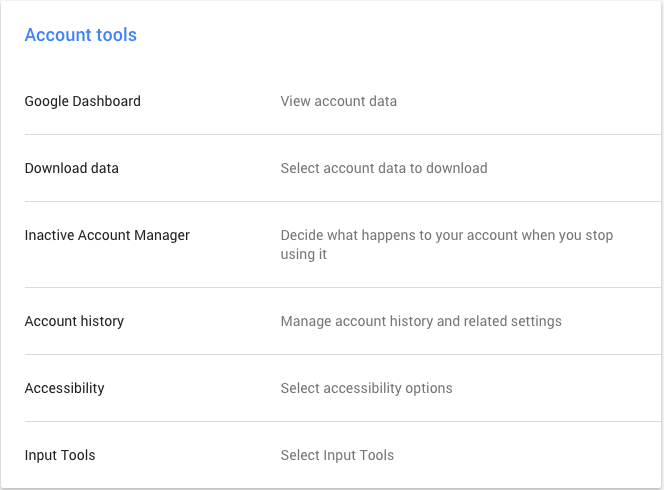
Selecting Account history then opens a screen that allows you to control not only search history but also voice searches, YouTube videos searched for or watched and even the location data that you may be storing. While on this page, be sure to review what history you are willing to share and make the appropriate selections as necessary. As you can see, I have selected to switch off all collection of my history.
Then there is the management of all the historic data, it might be amusing to go back and look at what you were browsing for before you remove it. This might just highlight to you the need to manage what is collected!
Mobile apps: The privacy insanity
Security expert Troy Hunt took a look at three apps (one of them being the Paypal one) and the results are shocking: While they were all way too invasive most of the tested apps had serious security issues as well.
When it comes to your privacy especially Paypal seems to want far more information from you than necessary. Hunt took the time to point out the extra personal requests on his blog:
- BSSID: This is the unique device ID of my home router which is the same as the MAC address. Google got themselves into hot water for siphoning this up via their mapping vehicles a little while back because that one unique ID ties back to my precise device.
- Device model and name: You could argue that comparable information is sent via your browser courtesy of the user agent, but that would only apply to the model and not the name of the device which is explicitly not passed in requests. This is private – it’s my device name.
- Internal IP address: The internal address assigned to my iPhone via the router when it associated to the network. This can give a sense of how many devices are on the network.
- Location: There’s my lat and long again and for all the same reasons I don’t really want to share it with Aussie Farmers, I also don’t really want to share it with PayPal.
- SSID: We’re talking about the name of my internal network here. I name mine in a non-identifying fashion because frankly, I want to keep it somewhat private and that’s from those in my immediate vicinity, let alone those on the other side of the world.
- Storage space: Ok, so it’s a 128GB iPhone, do they really need to know that? Back to the user agent comparison, this is not the sort of stuff that’s typically “leaked” by generic requests to the web because it’s an internal metric of no external consequence.”
In addition to that the security of two of the tested apps was so bad that he concluded: “Perhaps I should just stick to the browser that doesn’t leak this class of data yet one would assume is still sufficiently secure.”
Do you want to find out more? Then take a look at the whole in-depth article.
The post Mobile apps: The privacy insanity appeared first on Avira Blog.
Introducing Crumble – Surf Without Surveillance
We are happy to announce Crumble, a brand new Chrome extension designed by our colleagues from the Innovation Labs. The extension, currently in beta, will prevent companies from tracking you on the Internet via cookies, without breaking the websites you visit.
You can install the extension for free from here: Crumble Chrome extension.

While this is not the first solution of its kind, we do think that our implementation makes Crumble the best solution against online cookie tracking. Here’s why:
- Stops online tracking companies from creating your profile via cookies based on your online browsing
- It’s always up to date because it does not rely on a predefined list of online trackers.
- By design does not offer preferential treatment to selected ad networks (unlike some other extensions)
- Does not break the user experience on websites you visit
- Does not hide any content on the websites you visit
- Shows instantly who is tracking you on websites you visit
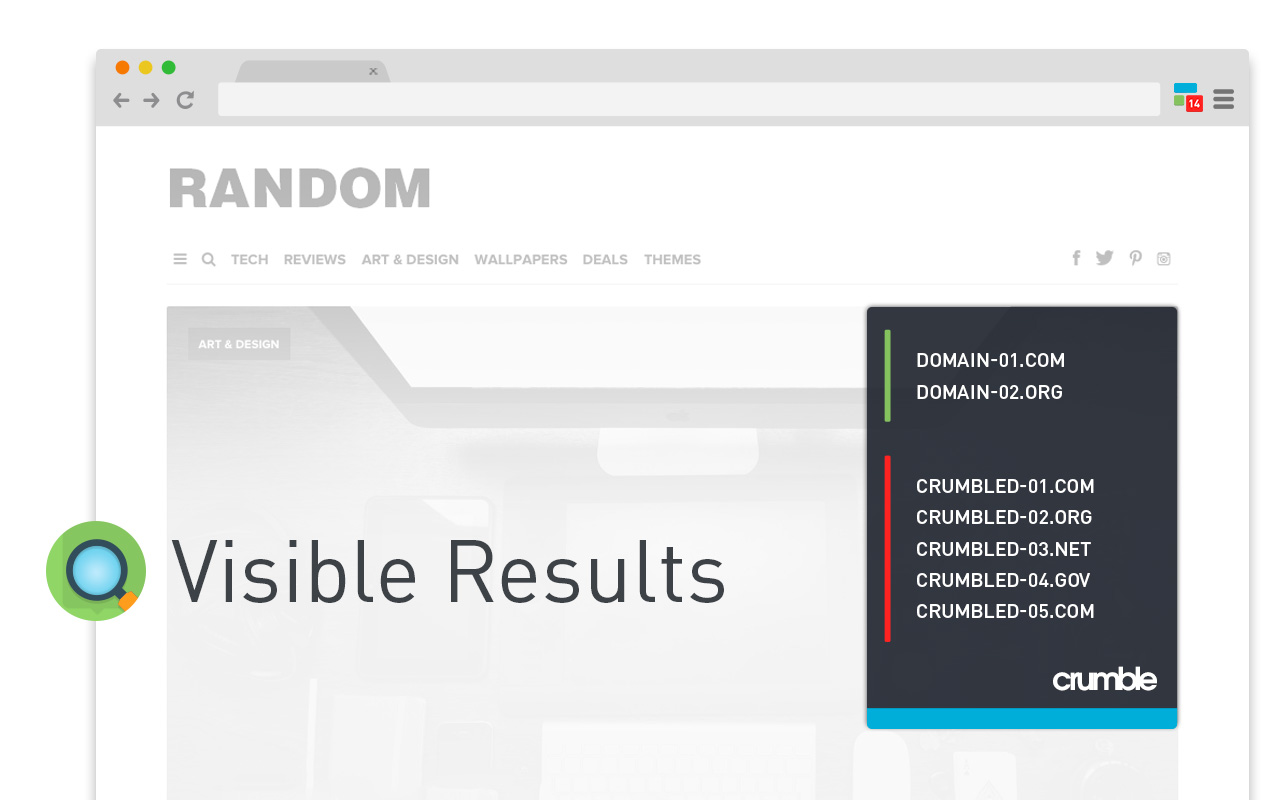
How does it work?
Crumble intercepts 3rd party cookies and controls what information is sent back to the web tracking companies. This way we can prevent trackers from following and profiling you based on the sites you visit.
Because, we manage rather than block 3rd party cookies, this means you will always get the full website experience; no broken plugins, no missing content, no weird behavior.
But wait! There’s more! Unlike other extensions that promise you a similar thing, we are doing all this by identifying the type of the cookie and not by keeping a blacklist of trackers. This allows us to block any new tracker as soon as it appears. No waiting time, no updating any list. Instant action.
This also means that we do not offer preferential treatment to trackers (aka whitelist them) unlike some other extensions.
Get in touch
This is Beta release from Innovation Labs by AVG. For more info you can find FAQ section of our website.
We would also love to hear your feedback at support.innovation [@] avg.com or tweet us @avginnovation.
![]()
![]()
