We love our fans and followers on Twitter because they frequently alert us to great resources. It happened today when we received a tweet from @LoveNerds4Ever letting us know that Avast Antivirus was mentioned on a Sacramento (California) News10 video segment. Thanks, Shawna!
@avast_antivirus You were mentioned! “Tech Mistakes” Ryan Eldridge #NerdsOnCallComputerRepair on #News10Sacramento https://t.co/pFAdSIN0N2
— Shawna M. Bell (@LoveNerds4Ever) May 14, 2015
The guest on this video segment is Ryan Eldridge, co-founder of Nerds on Call, a computer repair Business in Sacramento. He spoke to reporter Keba Arnold about technology mistakes that people typically make. These simple, but oh, so important points, are ones that we continually try to make, and Ryan puts it all together in one good video. Watch it now.
The security recommendations that Ryan makes:
- Run updates on your computer and mobile phone. Program updates and security patches are very important to keep your device up to date and running optimally.
- Download apps and programs from places you know and trust. On your mobile phone this would be the Google Play Store or Amazon App Store. For your computer, he says it’s a little bit harder, but suggest that you visit download.com, CNET’s well-known download site where you can read user reviews and see the reputation of the app before you download.
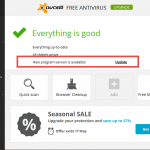
- Ryan reminds computer users that when they get a new device antivirus software may be pre-installed, but it is a trial for a limited time. After it expires, you need to get protected with a quality antivirus product. Ryan recommends Avast Free Antivirus for your computer, your Mac, and your mobile phone.
- Ms. Arnold confesses that she has one email address that acts as a catch-all for everything. Ryan says this is a no-no because if a hacker breaks into that email address, then he has access to everything. Ryan suggests that you have separate email addresses for friends and family, work, one for shopping, and one for banking.
- Passwords, admittedly are a pain in the you-know-what. Ryan suggests using an algorithm, or a kind of personal code, to construct your own passwords. For example, you can use a line from your favorite song, say Somewhere Over the Rainbow. Use the first letter of each word, use letters from the website name, and end with a series of numbers. Each password will be unique and known only to you.
And Ryan, we have a tip for you! Small businesses like yours need security protection too, and consumer antivirus like Avast Free Antivirus, doesn’t do the trick when you need to manage multiple devices, platforms, and people in remote locations. Adding to our collection of free products is the new Avast for Business. Avast for Business is free to use for as long as you want and for an unlimited number of admins and devices.








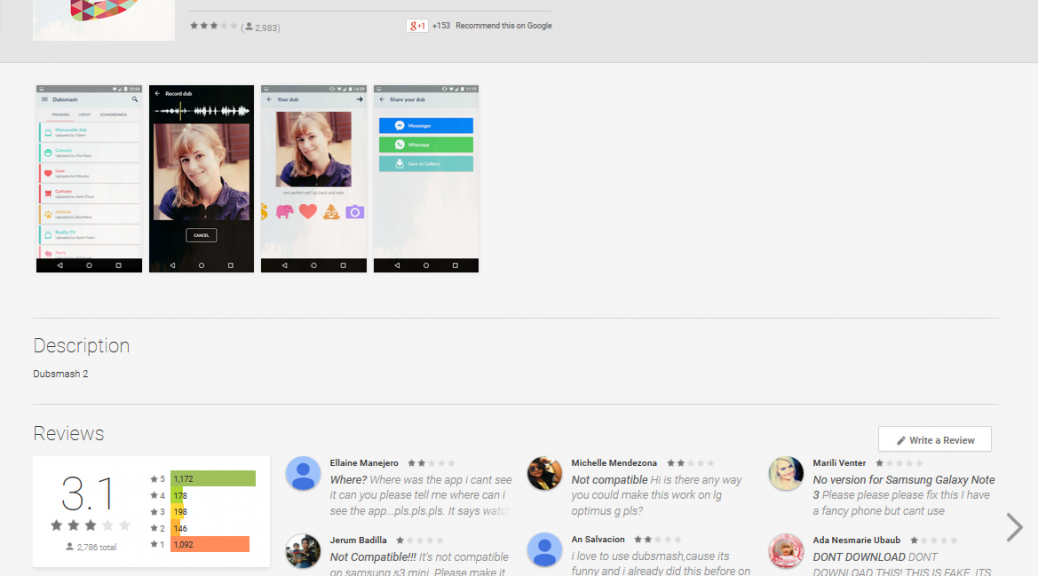
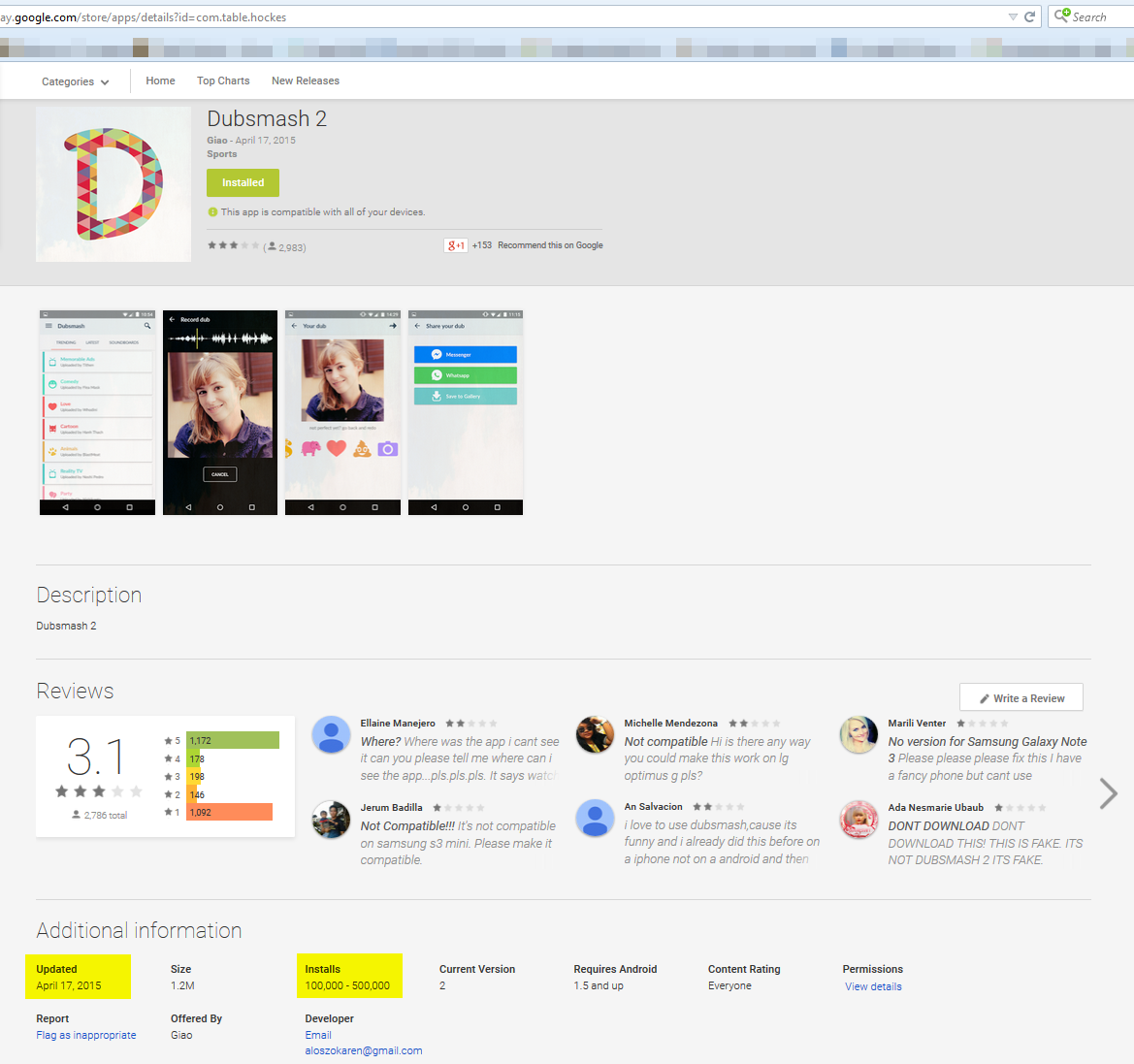
 The answer is a resounding YES. The Avast Virus Lab gives us an example from a trusted download source, Google Play: A
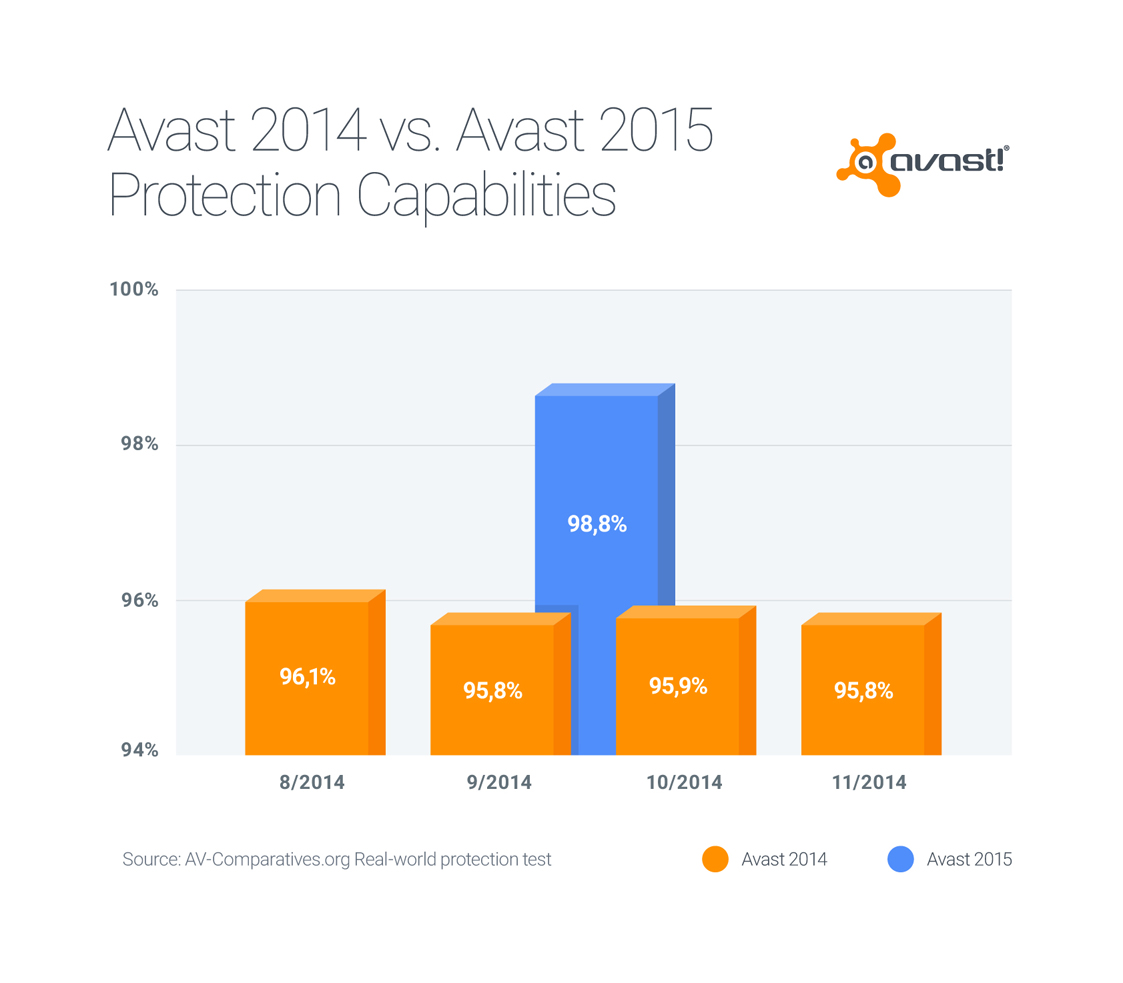
The answer is a resounding YES. The Avast Virus Lab gives us an example from a trusted download source, Google Play: A  Once you decide that you do want to protect your Android device, you can be confident in Avast Mobile Security, Avast’s free security app available on Google Play. A survey by AV -Comparatives said that
Once you decide that you do want to protect your Android device, you can be confident in Avast Mobile Security, Avast’s free security app available on Google Play. A survey by AV -Comparatives said that  One of the challenges with using a smartphone for so many activities, is that the battery gives out before we do. Our new free app
One of the challenges with using a smartphone for so many activities, is that the battery gives out before we do. Our new free app  Avast Battery Saver has only been available for a month or so but already 200,000 customers have downloaded it from the Google Play Store. For Earth Day we
Avast Battery Saver has only been available for a month or so but already 200,000 customers have downloaded it from the Google Play Store. For Earth Day we  Small and medium-sized businesses (SMBs) run the risk of data breaches just like there Enterprise cousins. Luke Walling, the General Manager of Avast for Business, explains that the biggest threat to SMBs is not actually hackers sitting somewhere far away.
Small and medium-sized businesses (SMBs) run the risk of data breaches just like there Enterprise cousins. Luke Walling, the General Manager of Avast for Business, explains that the biggest threat to SMBs is not actually hackers sitting somewhere far away.  Speaking of Avast for Business, our new disruptive free security offering for SMBs has 75,000 new customers in just 2 months. If you have a start-up, a small business, if you work in a school or non-profit organization, then
Speaking of Avast for Business, our new disruptive free security offering for SMBs has 75,000 new customers in just 2 months. If you have a start-up, a small business, if you work in a school or non-profit organization, then  Our researchers are constantly surprised by the creativity of malware authors. Recently, they found a new way
Our researchers are constantly surprised by the creativity of malware authors. Recently, they found a new way  Most people have security protection on their computers. That’s great when there are things like the banking malware we wrote about. With all that great protection why is it that they don’t trust the warnings? The Avast Virus Lab explored
Most people have security protection on their computers. That’s great when there are things like the banking malware we wrote about. With all that great protection why is it that they don’t trust the warnings? The Avast Virus Lab explored