The latest campaign to leverage Skype – a botnet circulating adware, composed entirely of Skype users – was recently disrupted by researchers.
Tag Archives: botnet
Popular Free VPN Hola Sells Users Bandwidth for Botnets
Sounds good, right? Especially in times when you just want to access Netflix U.S. for this one show but can’t because of licensing restrictions; or when everyone might be spying on you. Yes, now is the perfect time for a VPN (Virtual Private Network). Normally you have to pay for the service though. And that’s where Hola comes into play. Hola is a free Chome browser plugin and according to the ratings left on its’ Chrome page VERY popular.
So how come a service like this can afford to stay free? It’s pretty simple really: they sell your bandwidth. “When a user installs Hola, he becomes a VPN endpoint, and other users of the Hola network may exit through his internet connection and take on his IP. This is what makes it free: Hola does not pay for the bandwidth that its VPN uses at all, and there is no user opt out for this,” says Fredrick Brennan, the operator of 8chan in a note on his site. He continues: “Hola has gotten greedy. They recently (late 2014) realized that they basically have a 9 million IP strong botnet on their hands, and they began selling access to this botnet (right now, for HTTP requests only) at https://luminati.io. […] An attacker used the Luminati network to send thousands of legitimate-looking POST requests to 8chan’s post.php in 30 seconds, representing a 100x spike over peak traffic and crashing PHP-FPM.”
This is definitely not cool, but what does it mean for you? Well, if you are using Hola your connection will be used by other users to access pages in your country that are blocked for their IP but are available with yours. This is perhaps annoying, but not all that bad. But what of you IP might be one of those that get abused by people to perform illegal acts online?
Now is probably the best time to rethink using this specific free service.
The post Popular Free VPN Hola Sells Users Bandwidth for Botnets appeared first on Avira Blog.
Mass-Scale Abuse of Routers Due to Lax Security
The reason why botnets like that can even exist? According to a study by Incapsula it’s simple negligence – by ISPs, vendors and users alike.
The attacks were first spotted last year in December and seem to be ongoing ever since. More than 40,000 infected routers from 1,600 ISPs all over the world have been documented. When not used to execute DDoS (distributed denial of service) attacks the routers do something rather scary: In their idle time they use their resources to scan for additional routers to recruit!
“Our analysis reveals that miscreants are using their botnet resources to scan for additional routers to add to their “flock.” They do so by executing shell scripts, searching for devices having open SSH ports which can be accessed using default credentials.
Facilitating the infiltration, all of these under-secured routers are clustered in the IP neighborhoods of specific ISPs, which provide them in bulk to end users. For perpetrators, this is like shooting fish in a barrel, which makes each of the scans that much more effective. Using this botnet also enables perpetrators to execute distributed scans, improving their chances against commonplace blacklisting, rate-limiting and reputation-based defense mechanisms”, the study says.
The researchers believe that the routers were not hacked by means of vulnerabilities in the firmware but were hijacked due to other issues: all units are remotely accessible via HTTP and SSH on their default ports and nearly all of them are configured with vendor-provided default login credentials.
This combination invites trouble and DDoS attacks are only one of the possible threats resulting from it. Attackers could just as well:
- eavesdrop on all communication.
- perform man-in-the-middle (MITM) attacks (e.g., DNS poisoning).
- hijack cookies.
- gain access to local network devices (e.g., CCTV cameras).
What can you do?
Make sure to always change the default login credentials. That’s something every router owner should do from the start. You should also think twice before enabling remote access to your router management interface.
The post Mass-Scale Abuse of Routers Due to Lax Security appeared first on Avira Blog.
Coordinated Takedown Puts End to Simda Botnet
A coordinated operation between international police and private technology companies shuts down the Simda botnet.
ESET Research: Operation Buhtrap
The Operation Buhtrap campaign targets a wide range of Russian banks, used several different code signing certificates and implements evasive methods to avoid detection.
The post ESET Research: Operation Buhtrap appeared first on We Live Security.
![]()
Banking Trojan Vawtrak: Harvesting Passwords Worldwide
Over the last few months, AVG has tracked the rapid spread of a banking Trojan known as Vawtrak (aka Neverquest or Snifula).
Once it has infected a system, Vawtrak gains access to bank accounts visited by the victim. Furthermore, Vawtrak uses the infamous Pony module for stealing a wide range of login credentials.
While Vawtrak Trojans are not new, this particular sample is of great interest.
How and where is it spreading?
The Vawtrak Trojkan spreads in three main ways:
- Drive-by download – in the form of spam email attachments or links to compromised sites
- Malware downloader – such as Zemot or Chaintor
- Exploit kit – such as Angler
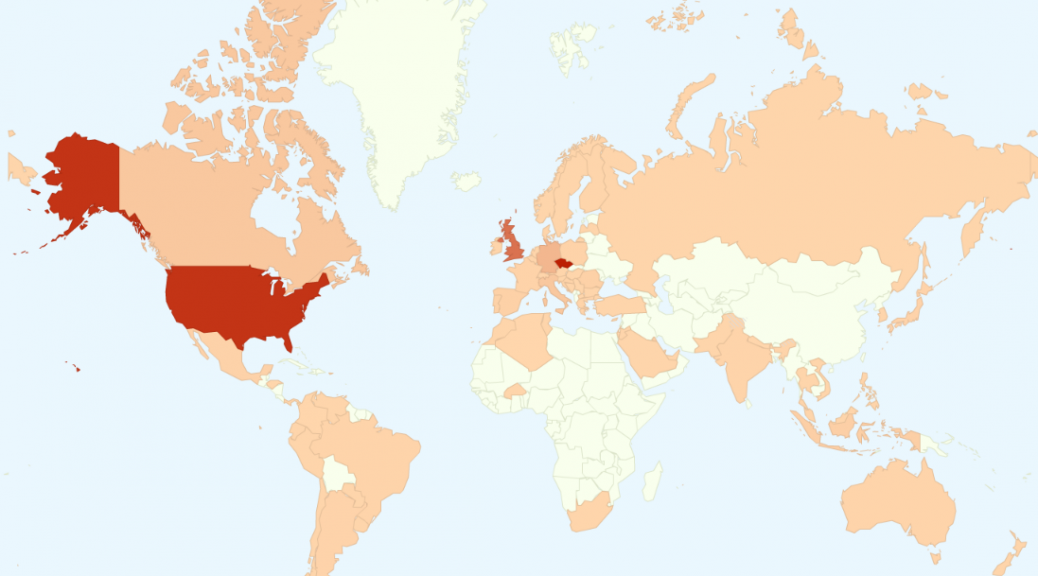
Based on our statistics, the Czech Republic, USA, UK, and Germany are the most affected countries by the Vawtrak campaigns this year.
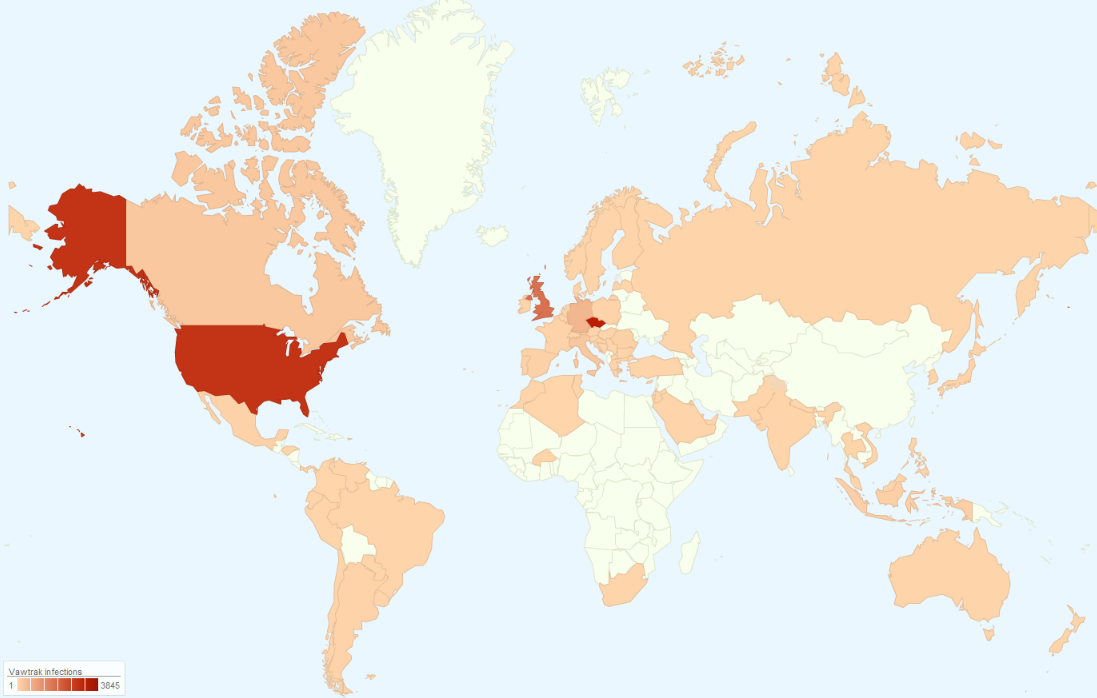
What are the features of this Vawtrak?
This Vawtrak sample is remarkable for the high number of functions that it can execute on a victim’s machine. These include:
- Theft of multiple types of passwords used by user online or stored on a local machine;
- Injection of custom code in a user-displayed web pages (this is mostly related to online banking);
- Surveillance of the user (key logging, taking screenshots, capturing video);
- Creating a remote access to a user’s machine (VNC, SOCKS);
- Automatic updating.
Of particular interest from a security standpoint is that by using Tor2web proxy, it can access update servers that are hosted on the Tor hidden web services without installing specialist software such as Torbrowser.
Moreover, the communication with the remote server is done over SSL, which adds further encryption.
This Vawtrak sample also uses steganography to hide update files inside of favicons so that downloading them does not seem suspicious. Each favicon is only few kilobytes in size, but it is enough to carry a digitally signed update file hidden inside.
Detailed analysis
Our complete analysis of this malware is too long to publish in full on this blog so we have prepared a detailed white paper that describes this infection, its internals and functions in detail.
You can also download the report here
Stay Safe
While this Vawtrak Trojan is very flexible in functionality, it’s coding is mostly basic and can be defended against. At AVG, we protect our users from Vawtrak in several ways:
- AVG LinkScanner and Online Shield provide real-time scanning of clicked links and web pages containing malicious code.
- AVG Antivirus for generic detection of malicious files and regular scans.
- AVG Identity Protection, that uses a behavioral-based detection, will detect even the latest versions of such infections.
- AVG Firewall prevents any unsolicited network traffic, such as communication with a C&C server.
Obama administration seeks more power to tackle botnets
The Obama administration wants greater power to shut down botnets, responding to the growing threat of cybercrime and increasingly complex, modern techniques.
The post Obama administration seeks more power to tackle botnets appeared first on We Live Security.
Europol shuts down Ramnit botnet used to steal bank details
The Ramnit botnet that is said to have affected 3.2 million computers has been shut down by European police.
The post Europol shuts down Ramnit botnet used to steal bank details appeared first on We Live Security.
Nine bad botnets and the damage they did
Responsible for a great deal of the hacking, spamming and malware every day: here are some of the worst botnets of all time.
The post Nine bad botnets and the damage they did appeared first on We Live Security.
Facebook ThreatExchange Platform Latest Hope for Information Sharing
Facebook announced ThreatExchange, an API-based platform for the exchange of attack and threat data.