There are two noteworthy risks associated with owning a smartphone or a tablet. The first one is malware and the second is loss. You need to protect yourself against both, and these days there are plenty of choices for each. Some are free security apps and some are paid-for solutions.
Protect your smartphone or tablet with mobile antivirus software
Last year more than 1 billion Android devices were shipped out to customers around the world. With Android winning the majority of the smartphone market, it offers a tempting target to malware authors. I have read in some publications that the average users need not worry about being infected with a virus on their phone or tablet, but with 2,850 new mobile threats being created every day by hackers the odds are getting worse.
Even if you think your chances are low, we suggest that you go ahead and install a good mobile antivirus software. The great thing about Avast Mobile Security is that it’s free, so your investment is minimal – just a few minutes of setup and you’re done.
Avast Mobile Security includes antivirus protection which scans your apps to see what they are doing, and a Web shield that scans URLs for malware or phishing. Malicious apps allow malware to enter your phone, so it’s good to have Avast on your side to detect when a bad one slips by on Google Play or another app store.

Avast Mobile Security gives Android users 100% protection against malicious apps.
To compare the choices of mobile antivirus software, you can look at the January 2015 “Mobile Security Test” conducted by the independent labs at AV-TEST. They looked at 31 popular Android security apps. Avast Mobile Security tops the list because it detected 100% of malicious apps without any impact on the battery life or slowing down of the device.
Install Avast Mobile Security and Antivirus from the Google Play store.
Protect your smartphone or tablet against loss or theft
Hackers aren’t the only risk – theft or loss of your device is more probable. In a famous stat from 2 years ago, Norton figured that 113 phones were lost or stolen every minute at the tune of $7 million a day! With all the personal and maybe even company data you have stored, losing your phone could be devastating.
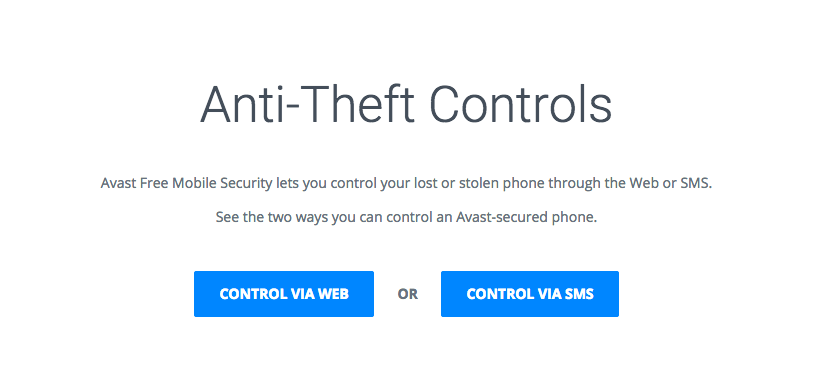
You can protect your device and the data on it by following some easy tips and installing Avast Anti-theft. Avast Anti-theft is an app that you can download with Avast Mobile Security for free. The anti-theft feature is hidden from thieves and allows you to remotely control your smartphone using SMS or via your MyAvast account. You can back up personal data and track your phone or sound an alarm if it’s lost or stolen.