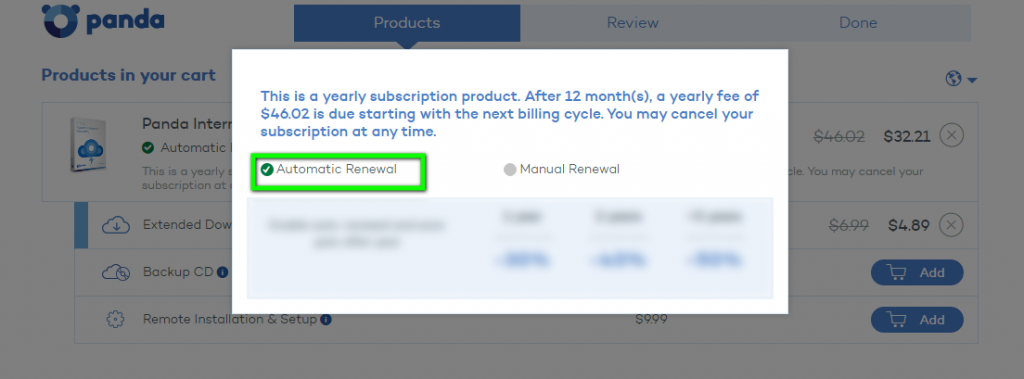
Could be your eReader a potential target for attack?
Most people think that hackers only target PCs and laptops. Some may also be aware that cybercriminals are now targeting smartphones too. But did you know that virtually any device – including your eReader – could be a potential target for attack?
Tablets as eReaders
With the exception of the Amazon Kindle, dedicated eReaders are now quite rare. Most people actually use cheap Android-powered tablets to read ebooks.
Obviously this is perfectly sensible – a reader that can be used to browse the web is really useful. But just like any other Android-powered tablet, there is a risk of security compromise.
These eReader tablets can install and run apps, just like Android smartphones – and this is there the problems arise. Malware infected apps are depressingly common; once installed they can steal personal information, access your passwords, allow criminals to commit identity theft and even use your tablet to attack other systems.
Malware is not just restricted to apps however. Determined hackers may disguise their apps as ebooks in the hope of tricking people into downloading them. Once loaded, these fake ebooks will install malware in the background, so you may not even know that there is something wrong.
The Internet of Things
Even if you never download apps to your eReader app, there is still a risk that cyber criminals could break in. WiFi connected devices are increasingly popular, allowing you to do all kinds of automated tasks. Remote light switches, connected thermostats, CCTV cameras and the like can all be joined to your home WiFi network to make your life easier through automation.
Known as the Internet of Things, these new technologies promise to change the way we live our lives at home. Unfortunately, every WiFi connected device also provides criminals with a range of potential targets to attack. Once in, they can then begin stealing data from the other devices attached to your network – including your eReader tablet.
Protecting your eReader
Because of these risks, you must protect your eReader in the same way you do your PC and smartphone. You should only ever download ebooks and apps from recognised, reputable stores like Amazon and Google Play for instance. This will help greatly reduce the risk of downloading an infected file.
You should also ensure that you have a suitable mobile security app installed on your eReader – like Panda Mobile Security. This will help prevent malicious apps from installing themselves, and alert you when there is a potential problem. You can then stop your information being stolen, or your device damaged.
If you suspect that your eReader has already been hacked, you should download Panama Mobile Security immediately. The longer an infection is left untreated, the greater the potential loss and damage caused.
For more help and advice on protecting your eReader, please get in touch.
The post Did you know your eReader can be hacked? appeared first on Panda Security Mediacenter.



 Visibility: Traceability and visibility of every action taken by running applications.
Visibility: Traceability and visibility of every action taken by running applications. Detection: Constant monitoring of all running processes and real-time blocking of targeted and zero-day attacks, and other advanced threats designed to slip past traditional antivirus solutions.
Detection: Constant monitoring of all running processes and real-time blocking of targeted and zero-day attacks, and other advanced threats designed to slip past traditional antivirus solutions. Response: Providing forensic information for in-depth analysis of every attempted attack as well as remediation tools.
Response: Providing forensic information for in-depth analysis of every attempted attack as well as remediation tools. Prevention: Preventing future attacks by blocking programs that do not behave as goodware and using advanced anti-exploit technologies.
Prevention: Preventing future attacks by blocking programs that do not behave as goodware and using advanced anti-exploit technologies.