Imagine your smartphone, tablet, and TV talking about you behind your back.
The post Avira now identifies SilverPush ad-tracking as malware appeared first on Avira Blog.
Imagine your smartphone, tablet, and TV talking about you behind your back.
The post Avira now identifies SilverPush ad-tracking as malware appeared first on Avira Blog.
Since Android already became the most used operating system among devices worldwide, it indirectly caught the attention of malware creators as well – around 97% of malicious mobile software is now targeting Android.
The post Dissecting MKero, the premium SMS service subscriber trojan found on Google Play appeared first on Avira Blog.
Earlier this year, a new type of trojan caught the attention of ESET researchers. This article will take a deep dive into how the exploit works and briefly describe the final payload.
The post Multi-stage exploit installing trojan appeared first on We Live Security.
![]()
Despite blocking efforts, online advertising is a daily part of our lives. Most of us get used to the large volume of adverts displayed daily, but authors of malicious code are trying to push the limits much further nowadays via advert-injection techniques used in malware threats.
In this post, we present a case study of one such malware that we detected via our AVG Identity Protection (IDP) component. Based on our telemetry, this infection is highly active and it is reaching its maximal peak. The most affected countries are the United States and Germany, followed by Saudi Arabia and the United Arab Emirates.
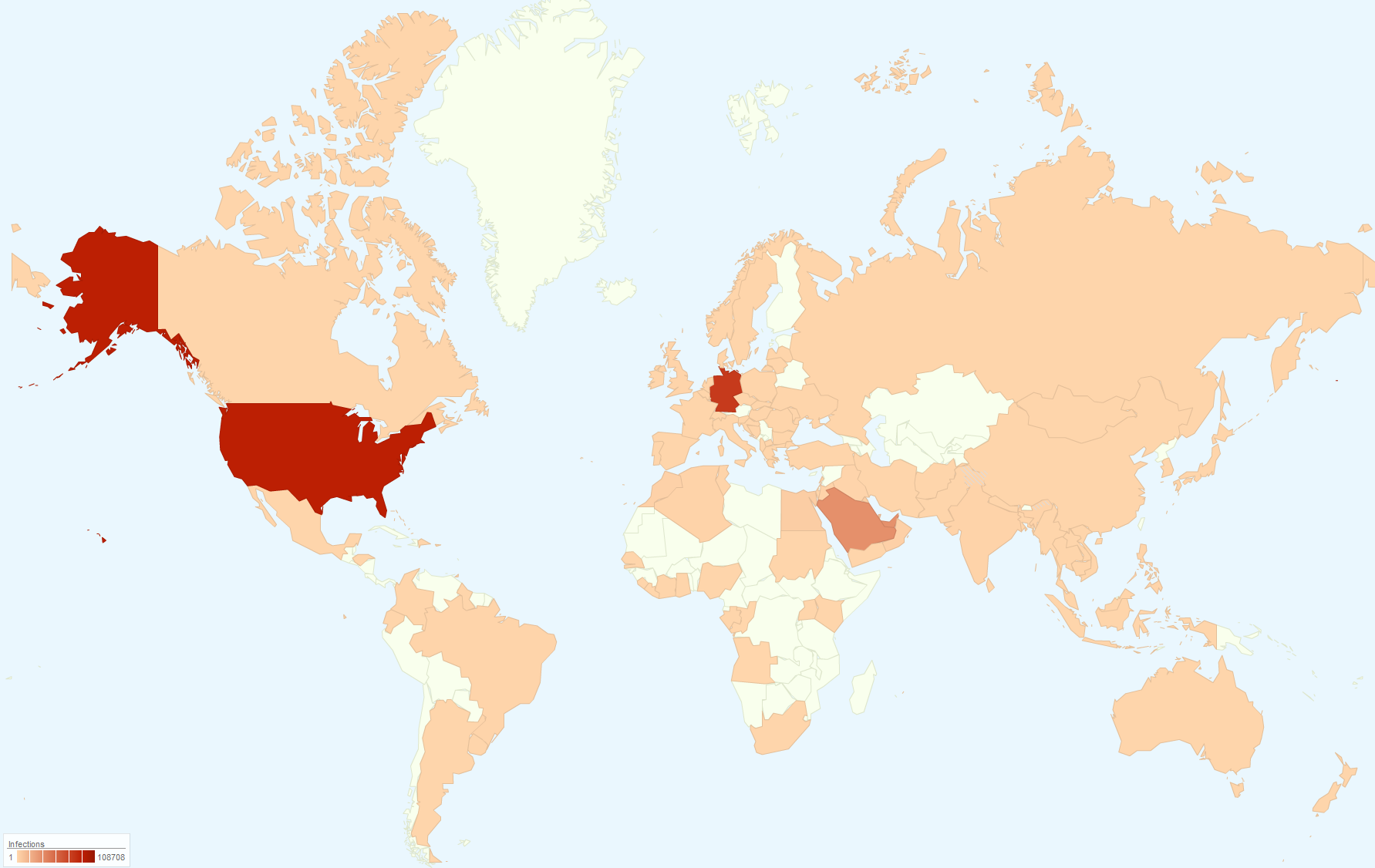
The user infection starts while installing an application proclaimed by its authors as a “Weather Forecast Application”. However, once installed, this application silently downloads and installs other components that are purely malicious – this threat tries to infect all installed browsers and inject additional adverts in browser pages. It also periodically loads sets of adverts in the background without user notification. As a side-effect, it sacrifices security and performance of the infected systems for the purpose of making money via ad providers.

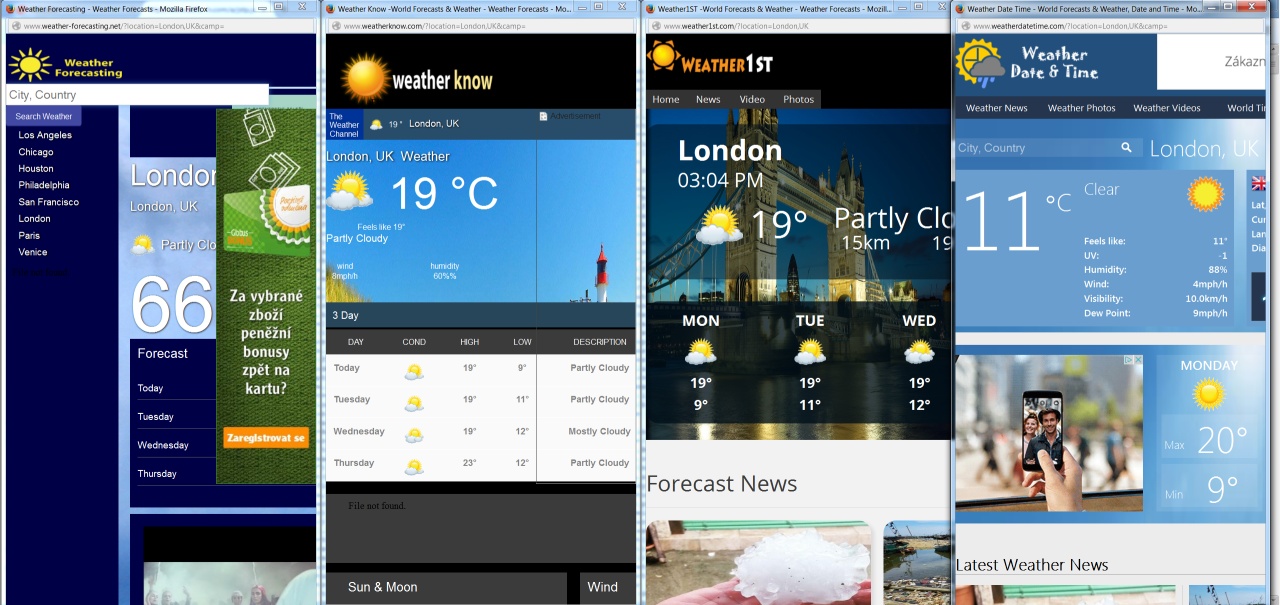
Details about this threat are described in the following technical analysis.
You can also download the report now.
AVG customers are protected against this threat via our multi-level protection in AVG Internet Security. If you’re not protected, you might want to check your systems using the indicators of compromise (IOC) listed in the aforementioned technical analysis.
![]()
![]()
ESET recently discovered an interesting stealth attack on Android users, an app that is a regular game but with an interesting addition: the application was bundled with another application.
The post Android trojan drops in, despite Google’s Bouncer appeared first on We Live Security.
![]()
Every now and again, ESET comes across an attack that “stands out”. Odlanor malware fits that bill – this unique trojan targets players of online poker.
The post The Trojan Games: Odlanor malware cheats at poker appeared first on We Live Security.
![]()
A few days ago CSIS published details about new Carbanak samples found in the wild. In this blog we examine the latest developments in the Carbanak story.
The post Carbanak gang is back and packing new guns appeared first on We Live Security.
![]()

Trusted websites can be hit with malvertising
Popular dating site Plenty of Fish (POF) and Australian telco giant Telstra were infected with malicious advertising from late last week over the weekend. The infection came from an ad network serving the advertisements that the websites displayed to their visitors.
Malvertising happens when cybercrooks hack into ad networks and inject malicious code into online advertising. These types of attacks are very dangerous because web users are unaware that anything is wrong and do not have to interact in any way to become infected. Just last week, other trusted sites like weather.com and AOL were attacked in the same way. In the Telstra and POF attacks, researchers say that a malicious advertisement redirected site visitors via a Google URL shortener to a website hosting the Nuclear Exploit kit which infected users with the Tinba Banking Trojan.
Malwarebytes researchers observed an attack before the POF discovery and surmised in their blog, “Given that the time frame of both attacks and that the ad network involved is the same, chances are high that pof[dot]com dropped that Trojan as well.” In turn, the Telstra attack was similar to the Plenty of Fish attack.
In an interview with SCMagazineUK.com, Senior Malware Analyst Jaromir Horejsi said,
“To protect themselves from malvertising, people should keep their software, such as browsers and plugins up-to-date, adjust browser settings to detect and flag malvertising. They should also have antivirus software installed to detect and block malicious payloads that can be spread by malvertising.”
The people at the highest risk are those website visitors with out-of-date software like Adobe Flash, Windows, or Internet Explorer. They could find their PC infected with the Tinba Banking Trojan, which is known for stealing banking credentials. Tinba aka Tiny Banker went global last year when it targeted banks like Wells Fargo, HSBC, Bank of America, and ING Direct. The success of the Trojan relied heavily on a bank customer’s system being vulnerable because of out-of-date software.
For more protection, use security software such as Avast Antivirus with the Software Updater feature. Software Updater informs you about updates and security patches available for your computer.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
The computer system in the Bundestag is now offline, to allow technicians to perform essential maintenance work.
The post Bundestag computer system goes offline appeared first on We Live Security.
![]()

Certifi-gate and Stagefright are two recent threats that have put many Android devices at risk. Photo via Ars Technica.
When it comes to security, it seems that Android has seen better days. A slew of vulnerabilities and threats have been cropping up recently, putting multitudes of Android users at risk. Certifi-gate and Stagefright are two threats that, when left unprotected against, could spark major data breaches.
Certifi-gate leaches permissions from other apps to gain remote control access
Certifi-gate is a Trojan that affects Android’s operating system in a scary way. Android devices with Jelly Bean 4.3 or higher are affected by this vulnerability, making about 50% of all Android users vulnerable to attacks or to their personal information being compromised.
What’s frightening about this nasty bug is how easily it can execute an attack – Certifi-gate only requires Internet access in order to gain remote control access of your devices. The attack takes place in three steps:
The good news here is that Avast Mobile Security blocks the installation packages that make it possible for Certifi-gate to exploit the permissions of your other apps. Breaking this down further, Avast Mobile Security would block the package before the action in Step 2 is carried out, making it impossible for a remotely-controlled server to take control of an insecure app that contains a vulnerable remote access backdoor.
Google’s Stagefright patch can be bypassed
We’ve already told you about the Stagefright bug, which has exposed nearly 1 billion Android devices to malware. Whereas Certifi-gate uses Internet access to control your device, Stagefright merely needs a phone number in order to infect users.
Due to the scope and severity of this threat, Google quickly put out a security patch that was intended to resolve the Stagefright issue once and for all. Unfortunately, it hasn’t been fully successful — it’s possible for the patch to be bypassed, which leaves Android users with a false sense of security and a vulnerable device.
As Avast security researcher Filip Chytry explains in his original post examining Stagefright, Avast encourages users to disable the “auto retrieve MMS” feature within their default messaging app’s settings as a precautionary measure. You can read our full set of instructions for staying safe against Stagefright in the post.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()