Cross-site scripting (XSS) vulnerability in Trend Micro InterScan Messaging Security Virtual Appliance 8.5.1.1516 allows remote authenticated users to inject arbitrary web script or HTML via the addWhiteListDomainStr parameter to addWhiteListDomain.imss.
Monthly Archives: May 2014
WatchGuard Technologies First To Deliver True Integration of Wired and Wireless Network Security
Malware creation breaks all records in the first quarter of 2014, with 160,000 new samples every day
Panda Security, The Cloud Security Company, has announced the latest findings of the PandaLabs quarterly report for Q1 2014. The main conclusions of the study include the fact that malware creation has broken all records during this period, with a figure of more than 15 million new samples, and more than 160,000 new samples appearing every day.
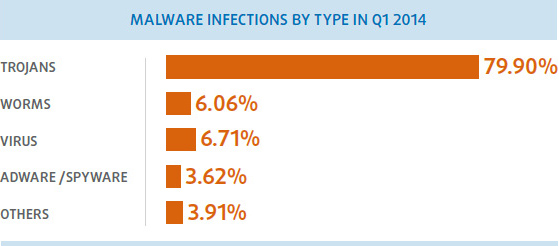
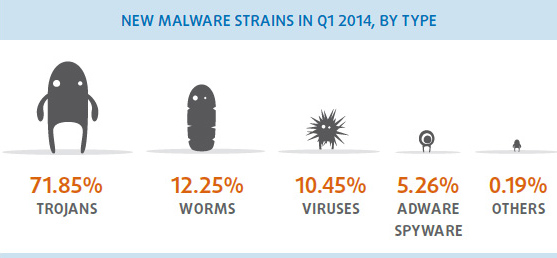
Trojans are still the most abundant type of new malware, accounting for 71.85% of new samples created during Q1. Similarly, infections by Trojans were once again the most common type of infection over this period, representing 79.90% of all cases.
In the area of mobile devices, there have been increasing attacks on Android environments. Many of these involve subscribing users to premium-rate SMS services without their knowledge, both through Google Play as well as ads on Facebook, using WhatsApp as bait.
Along these lines, social networks are still a favorite stalking ground for cyber-criminals, The Syrian Electronic Army group, for example, compromised accounts on Twitter and Facebook, and tried to gain control of the facebook.com domain in an attack that was foiled in time by MarkMonitor.
During the first three months of the year we have witnessed some of the biggest data thefts since the creation of the Internet, and as expected, Cryptolocker, the malicious file-encrypting ransomware which demands a ransom to unblock files, has continued to claim victims.
“Over these months, levels of cyber-crime have continued to rise. In fact, we have witnessed some of the biggest data thefts since the creation of the Internet, with millions of users affectedâ€, explains Luis Corrons, Technical Director of PandaLabs in Panda Security.
Trojans, the malware of choice for hackers
So far in 2014, Trojans are still the malware most commonly used by cyber-criminals to infect users. According to data from PandaLabs, four out of five infections around the world were caused by Trojans, that’s 79.90% of the total. Viruses are in second place, accounting for 6.71% of infections, followed by worms, with a ratio of 6.06%.
Trojans, the most frequently created malware
Trojans also top the ranking of newly created malware, accounting for 71.85% of the total, followed by worms, at 12.25%, and viruses at 10.45%.
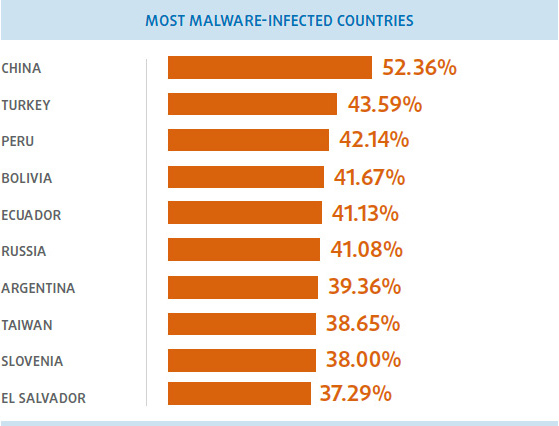
Infections by country
The global infection rate during the first three months of 2014 was 32.77%. China is once again the country with most infections, with a rate of 52.36%, followed by Turkey (43.59%) and Peru (42.14%). Although Spain is not in the top ten of this ranking, it is still above the global average with 33,57%.
European countries ranked high among the least infected countries, with the best figures coming from Sweden (21.03%), Norway (21.14%), Germany (24.18%) and Japan, which with a ratio of 24.21%, was the only non-European country in the top ten of this list.
The full report is available here.
![]()
Cross-Site Scripting in gridelements
Release Date: May 27, 2014
Component Type: Third party extension. This extension is not a part of the TYPO3 default installation.
Affected Versions: 2.0.2 and below, 1.5.0 and below
Vulnerability Type: Cross-Site Scripting
Severity: Low
Suggested CVSS v2.0: AV:N/AC:L/Au:S/C:P/I:P/A:N/E:F/RL:O/RC:C (What’s that?)
CVE: CVE-2014-3949
Problem Description: Failing to properly sanitize user input, the layout wizard provided by the extension gridelements is susceptible to Cross-Site Scripting. A valid backend user login with permission to access the layout wizard is required for this vulnerability to be exploited.
Solution: Updated versions 2.0.3 and 1.5.1 are available from the TYPO3 extension manager and at http://typo3.org/extensions/repository/download/gridelements/2.0.3/ and http://typo3.org/extensions/repository/download/gridelements/1.5.1/t3x/t3x/. Users of the extension are advised to update the extension as soon as possible.
Credits: Credits go to Security Team Member Georg Ringer who discovered and reported the issue.
General advice: Follow the recommendations that are given in the TYPO3 Security Guide. Please subscribe to the typo3-announce mailing list to receive future Security Bulletins via E-mail.
MS14-029 – Critical: Security Update for Internet Explorer (2962482) – Version: 1.2
Severity Rating: Critical
Revision Note: V1.2 (May 27, 2014): Bulletin revised to correct the update replacement for the Internet Explorer 11 updates and to announce a detection change in the 2961851 update. This is a detection change only. Customers who have already successfully updated their systems do not need to take any action.
Summary: This security update resolves two privately reported vulnerabilities in Internet Explorer. The vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
CVE-2014-1770 (internet_explorer)
Use-after-free vulnerability in Microsoft Internet Explorer 6 through 11 allows remote attackers to execute arbitrary code via crafted JavaScript code that interacts improperly with a CollectGarbage function call on a CMarkup object allocated by the CMarkup::CreateInitialMarkup function.
Multiple Vulnerabilities in TYPO3 CMS
Component Type: TYPO3 CMS
Vulnerability Types: Cross-Site Scripting, Insecure Unserialize, Improper Session Invalidation, Authentication Bypass, Information Disclosure and Host Spoofing
Overall Severity: Medium
Release Date: May 22, 2014
Vulnerability Type: Host Spoofing
Affected Versions: Versions 4.5.0 to 4.5.33, 4.7.0 to 4.7.18, 6.0.0 to 6.0.13, 6.1.0 to 6.1.8 and 6.2.0 to 6.2.2
Severity: Medium
Suggested CVSS v2.0: AV:N/AC:M/Au:N/C:N/I:P/A:N/E:F/RL:O/RC:C (What’s that?)
CVE: CVE-2014-3941
Problem Description: Failing to properly validate the HTTP host-header TYPO3 CMS is susceptible to host spoofing. TYPO3 uses the HTTP host-header to generate absolute URLs in several places like 404 handling, http(s) enforcement, password reset links and many more. Since the host header itself is provided by the client it can be forged to any value, even in a name based virtual hosts environment. A blog post describes this problem in great detail.
Solution: Update to TYPO3 versions 4.5.34, 4.7.19, 6.0.14, 6.1.9 or 6.2.3 and check or update your web server configuration as described below.
Additional Notes: These versions introduce a new configuration option:
$GLOBALS['TYPO3_CONF_VARS']['SYS']['trustedHostsPattern']
This option can contain either the value “SERVER_NAME” or a regular expression pattern that matches all host names that are considered trustworthy for the particular TYPO3 installation. “SERVER_NAME” is the default value shipped with the above mentioned TYPO3 versions. With this option value in effect, TYPO3 checks the currently submitted host-header against the SERVER_NAME variable. The SERVER_NAME variable contains trusted values in the following cases:
Apache Webserver: Apache is set up to use name based virtual hosts while the TYPO3 installation is part of one virtual host and not the default host. Only values that are part of the ServerName or ServerAlias values in the virtual host configuration are then set as SERVER_NAME.
Nginx Webserver: Nginx is set up with different servers blocks while the TYPO3 installation is not part of the “catch all” server block. By default only the first value of the server_name option is taken into account to populate the SERVER_NAME variable. If you specified more than one server name in your Nginx configuration you have to additionally add the following configuration:
fastcgi_param SERVER_NAME $host;
If TYPO3 is served by Apache from the default host, updating to the current TYPO3 versions is not enough! Apache then sets the SERVER_NAME variable directly to the (untrusted) host-header value. In such a setup you must either set “UseCannonicalName yes” in your Apache configuration, or change the TYPO3 configuration option to a regular expression that matches all trusted host names in your TYPO3 installation.
IMPORTANT: We tried hard to avoid a breaking change with these new versions and at the same time deliver a secure default setup for most users. We may have missed edge cases (like other web servers than the above, or a complex reverse proxy setup) where the default configuration breaks your site after the update. If you have a (server) setup that is considerably different from the scenarios described above, you should test if your TYPO3 installation still works after the update with the provided default configuration.
Credits: Credits go to Security Team Member Helmut Hummel who discovered and reported the issue and to Wouter van Dongen who discovered and reported a particular exploit possibility.
Vulnerable subcomponent: Color Picker Wizard
Vulnerability Type: Insecure Unserialize
Affected Versions: Versions 4.5.0 to 4.5.33, 4.7.0 to 4.7.18, 6.0.0 to 6.0.13 and 6.1.0 to 6.1.8
Severity: Low
Suggested CVSS v2.0: AV:N/AC:M/Au:S/C:N/I:P/A:P/E:F/RL:O/RC:C (What’s that?)
CVE: CVE-2014-3942
Problem Description: Failing to validate authenticity of a passed serialized string, the color picker wizard is susceptible to insecure unserialize, allowing authenticated editors to unserialize arbitrary PHP objects.
Solution: Update to TYPO3 versions 4.5.34, 4.7.19, 6.0.14 or 6.1.9 that fix the problem described. TYPO3 version 6.2 is not affected by this vulnerability.
Credits: Credits go to Security Team member Helmut Hummel who discovered and reported the issue.
Vulnerable subcomponent: Backend
Vulnerability Type: Cross-Site Scripting
Affected Versions: Versions 4.5.0 to 4.5.33, 4.7.0 to 4.7.18, 6.0.0 to 6.0.13, 6.1.0 to 6.1.8 and 6.2.0 to 6.2.2
Severity: Low
Suggested CVSS v2.0: AV:N/AC:M/Au:S/C:P/I:P/A:N/E:F/RL:O/RC:C (What’s that?)
CVE: CVE-2014-3943
Problem Description: Failing to properly encode user input, several backend components are susceptible to Cross-Site Scripting, allowing authenticated editors to inject arbitrary HTML or JavaScript by crafting URL parameters.
Solution: Update to TYPO3 versions 4.5.34, 4.7.19, 6.0.14, 6.1.9 or 6.2.3 that fix the problem described.
Credits: Credits go to Security Team members Georg Ringer and Franz Jahn and Marc Bastian Heinrichs who discovered and reported the issues.
Vulnerable subcomponent: ExtJS
Vulnerability Type: Cross-Site Scripting
Affected Versions: Versions 4.5.0 to 4.5.33, 4.7.0 to 4.7.18, 6.0.0 to 6.0.13, 6.1.0 to 6.1.8 and 6.2.0 to 6.2.2
Severity: Medium
Suggested CVSS v2.0: AV:N/AC:M/Au:N/C:P/I:P/A:N/E:F/RL:O/RC:C (What’s that?)
related CVE: CVE-2010-4207, CVE-2012-5881
Problem Description: The ExtJS JavaScript framework that is shipped with TYPO3 also delivers a flash file to show charts. This file is susceptible to Cross-Site Scripting. This vulnerability can be exploited without any authentication.
Solution: Update to TYPO3 versions 4.5.34, 4.7.19, 6.0.14, 6.1.9 or 6.2.3 that fix the problem described or delete the file typo3/contrib/extjs/resources/charts.swf as it is not used by TYPO3 at all.
Credits: Credits go to Ronald Klomp who discovered and reported the issue.
Vulnerable subcomponent: Authentication
Vulnerability Type: Improper Session Invalidation
Affected Versions: Versions 6.2.0 to 6.2.2
Severity: Low
Suggested CVSS v2.0: AV:L/AC:M/Au:N/C:P/I:P/A:N/E:F/RL:O/RC:C (What’s that?)
CVE: CVE-2014-3944
Problem Description: Failing to properly invalidate user sessions that have timed out, it is possible to successfully transmit one authenticated request before the session finally is discarded.
Solution: Update to TYPO3 version 6.2.3 that fix the problem described.
Credits: Credits go to Markus Klein who discovered and reported the issue.
Vulnerability Type: Authentication Bypass
Affected Versions: All TYPO3 versions not configured to use salted passwords
Severity: medium
Suggested CVSS v2.0: AV:N/AC:H/Au:N/C:P/I:P/A:N/E:F/RL:O/RC:C (What’s that?)
CVE: CVE-2014-3945
Problem Description: When the use of salted password is disabled (which is enabled by default since TYPO3 4.6 and required since TYPO3 6.2) passwords for backend access are stored as md5 hash in the database. This hash (e.g. taken from a successful SQL injection) can be used directly to authenticate backend users without knowing or reverse engineering the password.
Solution: Update to TYPO3 version 6.2 or higher or configure TYPO3 to make use of salted passwords by installing and configuring the saltepasswords system component.
Note: In TYPO3 version 6.2 it is still possible to disable password salt hashing for frontend users. It should be apparent that such setup is insecure and not recommended.
Vulnerable subcomponent: Extbase Framework
Vulnerability Type: Information Disclosure
Affected Versions: Versions 6.2.0 to 6.2.2
Severity: Medium
Suggested CVSS v2.0: AV:N/AC:L/Au:N/C:P/I:N/A:N/E:F/RL:O/RC:C (What’s that?)
CVE: CVE-2014-3946
Problem Description: Failing to respect user groups of logged in users when caching queries, Extbase is susceptible to information disclosure. The query caching (introduced in Extbase 6.2) used to cache queries that query results for a specific user group were presented to a different group.
Solution: Update to TYPO3 version 6.2.3 that fix the problem described.
Credits: Credits go to Jan Kiesewetter who discovered and reported the issue.
General Advice: Follow the recommendations that are given in the TYPO3 Security Guide. Please subscribe to the typo3-announce mailing list.
General Note: All security related code changes are tagged so that you can easily look them up on our review system.
Arbitrary code execution in extension "powermail" (powermail)
Release Date: May 22, 2014
Component Type: Third party extension. This extension is not a part of the TYPO3 default installation.
Affected Versions: powermail: Versions 2.0.13 and below, 1.6.10 and below
Vulnerability Type: Arbitrary Code Execution
Severity: Critical
Suggested CVSS v2.0: AV:N/AC:L/Au:N/C:C/I:C/A:C/E:F/RL:O/RC:C (What’s that?)
CVE: CVE-2014-3947
Problem Description: The extension powermail offers the possibility to upload files. It was discovered that it was possible to upload files with specially crafted file extensions, which could be executed as PHP files on the server when using Apache as web server with mod_mime available (default). Uploading files in powermail is possible without finally submitting the form, so a malicious file could be uploaded without further discovery. Failing to check the uploaded file name against the fileDenyPattern pattern, powermail is susceptible to arbitrary code execution.
Please also read an older bulletin and a blog article for further information about this issue in combination with Apache as web server.
Solution: Updated versions 2.0.14 and 1.6.11 are available from the TYPO3 extension manager and at http://typo3.org/extensions/repository/download/powermail/2.0.14/t3x/ and http://typo3.org/extensions/repository/download/powermail/1.6.11/t3x/. Users of the extension are advised to update the extension as soon as possible.
Credits: Credits go to Wouter van Dongen who discovered and reported the issue.
Affected Versions: powermail: Versions 1.6.10 and below
Vulnerability Type: Cross-Site Scripting
Severity: Low
Suggested CVSS v2.0: AV:N/AC:L/Au:S/C:P/I:P/A:N/E:F/RL:O/RC:C (What’s that?)
CVE: CVE-2014-3948
Problem Description: It was discovered that versions 1.6.10 and below are susceptible to Cross-Site SCripting within the HTML export wizard in the backend module.
Solution: An updated version 1.6.11 is available from the TYPO3 extension manager and at http://typo3.org/extensions/repository/download/powermail/1.6.11/t3x/. Users of the extension are advised to update the extension as soon as possible.
Credits: Credits go to Florian Grunow who discovered and reported this issue.
General advice: Follow the recommendations that are given in the TYPO3 Security Guide. Please subscribe to the typo3-announce mailing list to receive future Security Bulletins via E-mail.
CVE-2014-3716 (xen)
Xen 4.4.x does not properly check alignment, which allows local users to cause a denial of service (crash) via an unspecified field in a DTB header in a 32-bit guest kernel.
CVE-2014-3717 (xen)
Xen 4.4.x does not properly validate the load address for 64-bit ARM guest kernels, which allows local users to read system memory or cause a denial of service (crash) via a crafted kernel, which triggers a buffer overflow.





