Defending your devices in our hyperconnected world is no simple task. Your protection should include a wide range of defense mechanisms, a necessary deployment that, until now, has forced IT organizations to purchase and maintain a variety of products from different providers.
In December, AV-Comparatives gave their stamp of approval to the three principles of the Adaptive Defense 360 security model: continuous monitoring of all applications on company servers and workstations, automatic classification of endpoint processes using big data and machine learning techniques in a Cloud-based platform, and the possibility, should a process not be automatically classified, of a PandaLabs expert technician analyzing the behavior in depth.
“The evaluation by AV-Comparatives is a good reflection of the value of Adaptive Defense to our customers,” said Iratxe Vázquez, Product Manager at Panda Security. “We protect from and detect all types of known and unknown malware and zero-day security attacks (ransomware, bot networks, exploits, fileless malware, APTs, etc.), all thanks to the continuous monitoring of all processes running on our customers’ devices.”
The Adaptive Defense 360 solution has been endorsed as the first and only product that combines endpoint protection (EPP) and endpoint detection and response (EDR) in a single platform.
“As this solution classifies all executed processes, it cannot fail to record any malware.”
Efficacy Test
Panda Security’s advanced cybersecurity solution detects and blocks malware that other protection systems don’t even see. “We know that Adaptive Defense is easily one of the best solutions on the market, and we needed this to be certified by a prestigious laboratory in the world of security,” said Luis Corrons, Technical Director of PandaLabs.
Adaptive Defense 360 achieved 99.4% detection in the 220 analyzed samples and 0 false positives in the independent analysis performed by the esteemed AV-Comparatives Institute, which establishes this solution as the most advanced end-user cybersecurity software.
“For us it was essential that the tests were done with the utmost rigor, as we were looking for an environment that would perfectly simulate the real world and the threats to which companies are constantly exposed,” says Corrons.
The Intelligent Control Platform, a Synthesis of Machine Learning and Big Data
Artificial intelligence and machine learning are booming trends this 2017, allowing companies to use data science to optimize resources and improve their productivity. Imagine the effectiveness of a cybersecurity software that combines both of these trends.
“The protection that Adaptive Defense 360 offers is much more than a marketing strategy,” said Iratxe Vázquez. “This solution is a protection strategy, a new security model that our customers will need in order to deal with cyber threats. The attacker continually adapts his behavior, easily avoiding traditional antiviruses. He infiltrates and acts quietly, making all kinds of lateral movements that we monitor, analyze and block before he reaches his targets.”
Adaptive Defense 360 is part of an intelligent cyber security platform, capable of merging contextual intelligence with defense operations.
“We continuously monitor and evaluate the behavior of everything running on our clients’ machines, using Machine Learning’s adaptive techniques in Big Data environments, which gives way to exponentially increasing knowledge of malware, tactics, techniques, and malicious processes, along with reliable application information, “explains Iratxe Vázquez.
Adaptive 360 is also integrated with SIEM solutions (Security Information and Event Management), which add detailed information on the activity of running applications at workstations. For those customers who do not have a SIEM, Adaptive Defense 360 incorporates its own security event management and storage system for real-time analysis of information collected with the Advanced Reporting Tool.
AV-Comparatives has seen what we can do, and they liked what they saw. How about you? Have you witnessed intelligent cybersecurity in action yet?
Follow the links to download the first infographic on the most notable examples of ransomware in 2016.
The post Adaptive Defense 360 Given Stamp of Approval by AV-Comparatives appeared first on Panda Security Mediacenter.



 Visibility: Traceability and visibility of every action taken by running applications.
Visibility: Traceability and visibility of every action taken by running applications. Detection: Constant monitoring of all running processes and real-time blocking of targeted and zero-day attacks, and other advanced threats designed to slip past traditional antivirus solutions.
Detection: Constant monitoring of all running processes and real-time blocking of targeted and zero-day attacks, and other advanced threats designed to slip past traditional antivirus solutions. Response: Providing forensic information for in-depth analysis of every attempted attack as well as remediation tools.
Response: Providing forensic information for in-depth analysis of every attempted attack as well as remediation tools. Prevention: Preventing future attacks by blocking programs that do not behave as goodware and using advanced anti-exploit technologies.
Prevention: Preventing future attacks by blocking programs that do not behave as goodware and using advanced anti-exploit technologies.



 In addition to paralyzing and reducing services, which was what happened to the Venezuelan oil company PDVSA when it was hit by an attack that reduced production from 3 million barrels a day to 370,000, such attacks can also have a significant financial impact. One of the largest car manufacturers in the USA was left with losses of around US$150 million thanks to an attack using SQLSlammer, which spread rapidly and affected 17 production plants.
In addition to paralyzing and reducing services, which was what happened to the Venezuelan oil company PDVSA when it was hit by an attack that reduced production from 3 million barrels a day to 370,000, such attacks can also have a significant financial impact. One of the largest car manufacturers in the USA was left with losses of around US$150 million thanks to an attack using SQLSlammer, which spread rapidly and affected 17 production plants.
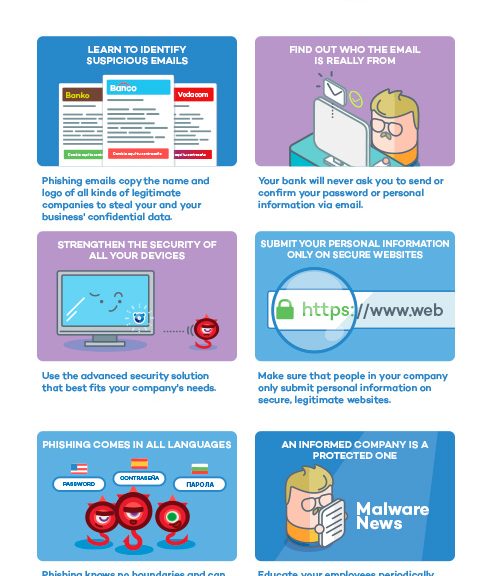
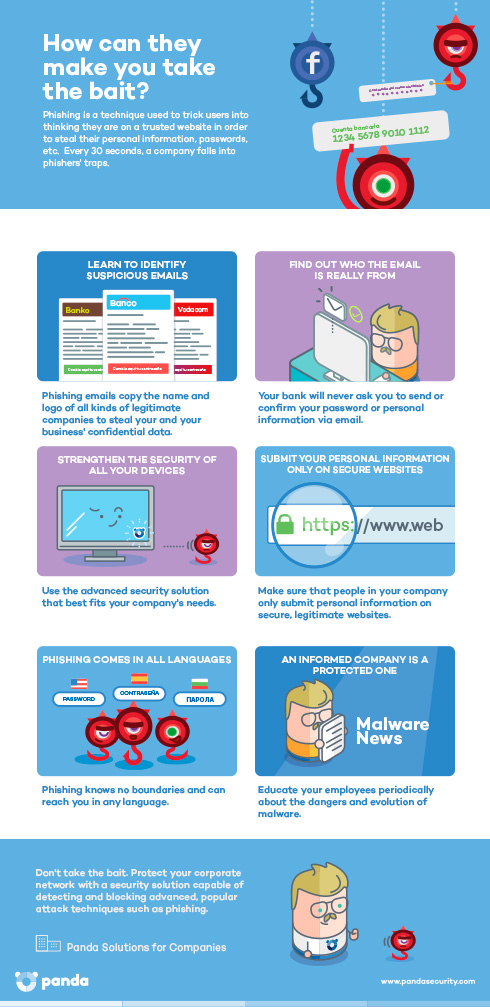




 New, but not that dangerous… why the panic?
New, but not that dangerous… why the panic?
 Knock knock! Trick or treat! Companies and cybercriminals play the same game. You could be opening back doors to cybercriminals this year, without even knowing it. You’ll lose this game if you don’t fight back. Ransomware attacks will capture your documents and the attackers will be expecting a big juicy reward (if you want your files back, that is). This Halloween, beware!
Knock knock! Trick or treat! Companies and cybercriminals play the same game. You could be opening back doors to cybercriminals this year, without even knowing it. You’ll lose this game if you don’t fight back. Ransomware attacks will capture your documents and the attackers will be expecting a big juicy reward (if you want your files back, that is). This Halloween, beware! Attacks by staff with privileged access represents one of the greatest threats for the security of the corporate information and data of your customers. Research conducted by
Attacks by staff with privileged access represents one of the greatest threats for the security of the corporate information and data of your customers. Research conducted by  At the beginning of this month, an employee from the US government, Harold Thomas Martin,
At the beginning of this month, an employee from the US government, Harold Thomas Martin,  Start using a cybersecurity solution that has advanced protection features, and that also has the capacity to detect and remedy possible threats.
Start using a cybersecurity solution that has advanced protection features, and that also has the capacity to detect and remedy possible threats.