Red Hat Security Advisory 2014-1351-01 – Red Hat JBoss Fuse, based on Apache ServiceMix, provides a small-footprint, flexible, open source enterprise service bus and integration platform. Red Hat JBoss A-MQ, based on Apache ActiveMQ, is a standards compliant messaging system that is tailored for use in mission critical applications. This patch is an update to Red Hat JBoss Fuse 6.1.0 and Red Hat JBoss A-MQ 6.1.0. It includes bug fixes and enhancements, which are documented in the readme.txt file included with the patch files. The following security issues are addressed in this release: It was discovered that Apache Shiro authenticated users without specifying a user name or a password when used in conjunction with an LDAP back end that allowed unauthenticated binds.
Monthly Archives: October 2014
Bash Me Some More
This is information regarding more bash vulnerabilities and how the original bash patches are ineffective.
Epicor Password Disclosure / Cross Site Scripting
Epicor suffers from cross site scripting and password disclosure vulnerabilities.
VMware Security Advisory 2014-0010
VMware Security Advisory 2014-0010 – VMware product updates address Bash security vulnerabilities.
UPDATED VMSA-2014-0010.1 – VMware product updates address critical Bash security vulnerabilities
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA1
VMware Security Advisory
Advisory ID: VMSA-2014-0010.1
Synopsis: VMware product updates address critical Bash
security vulnerabilities
Issue date: 2014-09-30
Updated on: 2014-10-01
CVE numbers: CVE-2014-6271, CVE-2014-7169, CVE-2014-7186,
CVE-2014-7187, CVE-2014-6277, CVE-2014-6278
- ------------------------------------------------------------------------
1. Summary
VMware product updates address Bash security vulnerabilities.
2. Relevant Releases (Affected products for which remediation is present)
ESX 4.1 without patch ESX410-201410401-SG
ESX 4.0 without patch ESX400-201410401-SG
vCenter Server Appliance prior to 5.5 U2a
vCenter Server Appliance prior to 5.1 U2b
vCenter Server Appliance prior to 5.0 U3b
vCloud Director Appliance prior to 5.5.1.3
VMware Data Recovery prior to 2.0.4
VMware Mirage Gateway prior to 5.1.1
vSphere Storage Appliance prior to 5.5.2
vCenter Log Insight prior to 2.0U1
3. Problem Description
a. Bash update for multiple products.
Bash libraries have been updated in multiple products to resolve
multiple critical security issues, also referred to as Shellshock.
The Common Vulnerabilities and Exposures project (cve.mitre.org)
has assigned the identifiers CVE-2014-6271, CVE-2014-7169,
CVE-2014-7186, and CVE-2014-7187, CVE-2014-6277, CVE-2014-6278
to these issues.
VMware products have been grouped into the following four
product categories:
I) ESXi and ESX Hypervisor
ESXi is not affected because ESXi uses the Ash shell (through
busybox), which is not affected by the vulnerability reported
for the Bash shell.
ESX has an affected version of the Bash shell. See table 1 for
remediation for ESX.
II) Windows-based products
Windows-based products, including all versions of vCenter Server
running on Windows, are not affected.
III) VMware (virtual) appliances
VMware (virtual) appliances ship with an affected version of Bash.
See table 2 for remediation for appliances.
IV) Products that run on Linux, Android, OSX or iOS (excluding
virtual
appliances)
Products that run on Linux, Android, OSX or iOS (excluding
virtual appliances) might use the Bash shell that is part of the
operating system. If the operating system has a vulnerable
version of Bash, the Bash security vulnerability might be
exploited through the product. VMware recommends that customers
contact their operating system vendor for a patch.
MITIGATIONS
VMware encourages restricting access to appliances through
firewall rules and other network layer controls to only trusted IP
addresses. This measure will greatly reduce any risk to these
appliances.
RECOMMENDATIONS
VMware recommends customers evaluate and deploy patches for
affected products in Table 1 and 2 below as these
patches become available.
Column 4 of the following tables lists the action required to
remediate the vulnerability in each release, if a solution is
available.
Table 1 - ESXi and ESX Hypervisor
=================================
VMware Product Running Replace with/
Product Version on Apply Patch
============== ======= ======= =============
ESXi any ESXi Not affected
ESX 4.1 ESX ESX410-201410401-SG*
ESX 4.0 ESX ESX400-201410401-SG*
* VMware has made VMware ESX 4.0 and 4.1 security patches available
for the Bash shell vulnerability. This security patch release is an
exception to the existing VMware lifecycle policy.
Table 2 - Products that are shipped as a (virtual) appliance.
=============================================================
VMware Product Running Replace with/
Product Version on Apply Patch
============== ======= ======= ================
vCenter Server Appliance 5.x Linux 5.5 U2a, 5.1 U2b,
5.0 U3b
Horizon DaaS Platform 6.x Linux Patch Pending
Horizon Workspace 1.x, 2.x Linux Patch Pending
IT Business Management Suite 1.x Linux Patch Pending
NSX for Multi-Hypervisor 4.x Linux Patch Pending
NSX for vSphere 6.x Linux Patch Pending
NVP 3.x Linux Patch Pending
vCenter Converter Standalone 5.x Linux Patch Pending **
vCenter Hyperic Server 5.x Linux Patch Pending
vCenter Infrastructure Navigator 5.x Linux Patch Pending
vCenter Log Insight 1.x, 2.x Linux 2.0 U1
vCenter Operations Manager 5.x Linux Patch Pending
vCenter Orchestrator Appliance 4.x, 5.x Linux Patch Pending
vCenter Site Recovery Manager 5.x Linux Patch Pending **
vCenter Support Assistant 5.x Linux Patch Pending
vCloud Automation Center 6.x Linux Patch Pending
vCloud Automation Center
Application Services 6.x Linux Patch Pending
vCloud Director Appliance 5.x Linux 5.5.1.3
vCloud Connector 2.x Linux Patch Pending
vCloud Networking and Security 5.x Linux Patch Pending
vCloud Usage Meter 3.x Linux Patch Pending
vFabric Application Director 5.x, 6.x Linux Patch Pending
vFabric Postgres 9.x Linux Patch Pending
Viewplanner 3.x Linux Patch Pending
VMware Application Dependency
Planner x.x Linux Patch Pending
VMware Data Recovery 2.x Linux 2.0.4
VMware HealthAnalyzer 5.x Linux Patch Pending
VMware Mirage Gateway 5.x Linux 5.1.1
VMware Socialcast On Premise x.x Linux Patch Pending
VMware Studio 2.x Linux Patch Pending
VMware TAM Data Manager x.x Linux Patch Pending
VMware Workbench 3.x Linux Patch Pending
vSphere App HA 1.x Linux Patch Pending
vSphere Big Data Extensions 1.x, 2.x Linux Patch Pending
vSphere Data Protection 5.x Linux Patch Pending
vSphere Management Assistant 5.x Linux Patch Pending
vSphere Replication 5.x Linux Patch Pending
vSphere Storage Appliance 5.x Linux 5.5.2
** This product includes Virtual Appliances that will be updated, the
product
itself is not a Virtual Appliance.
4. Solution
ESX
---
Downloads:
https://www.vmware.com/patchmgr/findPatch.portal
Documentation:
http://kb.vmware.com/kb/2090859
http://kb.vmware.com/kb/2090853
vCenter Server Appliance
------------------------
Downloads:
https://my.vmware.com/web/vmware/details?productId=353&downloadGroup=VC55U2
(scroll down to 5.5 Update 2a Appliance)
https://my.vmware.com/web/vmware/details?productId=285&downloadGroup=VCL-VS
P510-VC-51U2A
(scroll down to 5.1 Update 2b Appliance)
https://my.vmware.com/web/vmware/details?productId=229&downloadGroup=VC50U3
A
(scroll down to 5.0 Update 3b Appliance)
Documentation:
http://kb.vmware.com/kb/2091085
http://kb.vmware.com/kb/2091018
http://kb.vmware.com/kb/2091017
vCloud Director Appliance
-------------------------
Downloads:
www.vmware.com/go/try-vcloud-director
Documentation:
http://kb.vmware.com/kb/2091071
VMware Data Recovery
--------------------
Downloads:
https://my.vmware.com/web/vmware/details?productId=229&downloadGroup=VDR204
Documentation:
http://kb.vmware.com/kb/2091015
VMware Mirage Gateway
---------------------
Downloads:
https://my.vmware.com/web/vmware/details?downloadGroup=MIRAGE-510&productId
=407&rPId=6565
(See VMware Mirage Gateway Software)
Documentation:
http://kb.vmware.com/kb/2091090
vSphere Storage Appliance
-------------------------
Downloads:
https://my.vmware.com/web/vmware/details?downloadGroup=VSP55-VSA-552&produc
tId=354&rPId=6585
Documentation:
http://kb.vmware.com/kb/2091000
vCenter Log Insight
-------------------
Downloads:
https://my.vmware.com/web/vmware/details?downloadGroup=STRATA20&productId=4
12&rPId=5804
Documentation:
http://kb.vmware.com/kb/2091065
5. References
VMware Knowledge Base Article 2090740
http://kb.vmware.com/kb/2090740
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271 ,
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7169
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7186
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7187
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6277
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6278
- ------------------------------------------------------------------------
6. Change Log
2014-09-30 VMSA-2014-0010
Initial security advisory in conjunction with the release of
vCenter Log Insight 2.0 U1 on 2014-09-30.
2014-10-01 VMSA-2014-0010.1
Updated advisory in conjunction with the release of ESX 4.x patches,
vCenter Server Appliance 5.5 U2a, 5.1 U2b, and 5.0 U3b, vCloud Director
Appliance 5.5.1.3, VMware Data Recovery 2.0.4, VMware Mirage Gateway
5.1.1 and vSphere Storage Appliance 5.5.2 on 2014-10-01. Added
CVE-2014-6277 and CVE-2014-6278 as confirmed fixed.
- ------------------------------------------------------------------------
7. Contact
E-mail list for product security notifications and announcements:
http://lists.vmware.com/cgi-bin/mailman/listinfo/security-announce
This Security Advisory is posted to the following lists:
security-announce at lists.vmware.com
bugtraq at securityfocus.com
fulldisclosure at seclists.org
E-mail: security at vmware.com
PGP key at: http://kb.vmware.com/kb/1055
VMware Security Advisories
http://www.vmware.com/security/advisories
VMware Security Response Policy
https://www.vmware.com/support/policies/security_response.html
VMware Lifecycle Policy
https://www.vmware.com/support/policies/lifecycle.html
Twitter
https://twitter.com/VMwareSRC
Copyright 2014 VMware Inc. All rights reserved.
-----BEGIN PGP SIGNATURE-----
Version: Encryption Desktop 10.3.2 (Build 15337)
Charset: utf-8
wj8DBQFULDR2DEcm8Vbi9kMRAno8AKChLzy32utif3LnJt4DduKNpmH1MgCgqKl+
ycAq/Gx4gCwu6SjbjBdgmSs=
=81FF
-----END PGP SIGNATURE-----
UPDATED VMSA-2014-0010.1 – VMware product updates address critical Bash security vulnerabilities
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA1
VMware Security Advisory
Advisory ID: VMSA-2014-0010.1
Synopsis: VMware product updates address critical Bash
security vulnerabilities
Issue date: 2014-09-30
Updated on: 2014-10-01
CVE numbers: CVE-2014-6271, CVE-2014-7169, CVE-2014-7186,
CVE-2014-7187, CVE-2014-6277, CVE-2014-6278
- ------------------------------------------------------------------------
1. Summary
VMware product updates address Bash security vulnerabilities.
2. Relevant Releases (Affected products for which remediation is present)
ESX 4.1 without patch ESX410-201410401-SG
ESX 4.0 without patch ESX400-201410401-SG
vCenter Server Appliance prior to 5.5 U2a
vCenter Server Appliance prior to 5.1 U2b
vCenter Server Appliance prior to 5.0 U3b
vCloud Director Appliance prior to 5.5.1.3
VMware Data Recovery prior to 2.0.4
VMware Mirage Gateway prior to 5.1.1
vSphere Storage Appliance prior to 5.5.2
vCenter Log Insight prior to 2.0U1
3. Problem Description
a. Bash update for multiple products.
Bash libraries have been updated in multiple products to resolve
multiple critical security issues, also referred to as Shellshock.
The Common Vulnerabilities and Exposures project (cve.mitre.org)
has assigned the identifiers CVE-2014-6271, CVE-2014-7169,
CVE-2014-7186, and CVE-2014-7187, CVE-2014-6277, CVE-2014-6278
to these issues.
VMware products have been grouped into the following four
product categories:
I) ESXi and ESX Hypervisor
ESXi is not affected because ESXi uses the Ash shell (through
busybox), which is not affected by the vulnerability reported
for the Bash shell.
ESX has an affected version of the Bash shell. See table 1 for
remediation for ESX.
II) Windows-based products
Windows-based products, including all versions of vCenter Server
running on Windows, are not affected.
III) VMware (virtual) appliances
VMware (virtual) appliances ship with an affected version of Bash.
See table 2 for remediation for appliances.
IV) Products that run on Linux, Android, OSX or iOS (excluding
virtual
appliances)
Products that run on Linux, Android, OSX or iOS (excluding
virtual appliances) might use the Bash shell that is part of the
operating system. If the operating system has a vulnerable
version of Bash, the Bash security vulnerability might be
exploited through the product. VMware recommends that customers
contact their operating system vendor for a patch.
MITIGATIONS
VMware encourages restricting access to appliances through
firewall rules and other network layer controls to only trusted IP
addresses. This measure will greatly reduce any risk to these
appliances.
RECOMMENDATIONS
VMware recommends customers evaluate and deploy patches for
affected products in Table 1 and 2 below as these
patches become available.
Column 4 of the following tables lists the action required to
remediate the vulnerability in each release, if a solution is
available.
Table 1 - ESXi and ESX Hypervisor
=================================
VMware Product Running Replace with/
Product Version on Apply Patch
============== ======= ======= =============
ESXi any ESXi Not affected
ESX 4.1 ESX ESX410-201410401-SG*
ESX 4.0 ESX ESX400-201410401-SG*
* VMware has made VMware ESX 4.0 and 4.1 security patches available
for the Bash shell vulnerability. This security patch release is an
exception to the existing VMware lifecycle policy.
Table 2 - Products that are shipped as a (virtual) appliance.
=============================================================
VMware Product Running Replace with/
Product Version on Apply Patch
============== ======= ======= ================
vCenter Server Appliance 5.x Linux 5.5 U2a, 5.1 U2b,
5.0 U3b
Horizon DaaS Platform 6.x Linux Patch Pending
Horizon Workspace 1.x, 2.x Linux Patch Pending
IT Business Management Suite 1.x Linux Patch Pending
NSX for Multi-Hypervisor 4.x Linux Patch Pending
NSX for vSphere 6.x Linux Patch Pending
NVP 3.x Linux Patch Pending
vCenter Converter Standalone 5.x Linux Patch Pending **
vCenter Hyperic Server 5.x Linux Patch Pending
vCenter Infrastructure Navigator 5.x Linux Patch Pending
vCenter Log Insight 1.x, 2.x Linux 2.0 U1
vCenter Operations Manager 5.x Linux Patch Pending
vCenter Orchestrator Appliance 4.x, 5.x Linux Patch Pending
vCenter Site Recovery Manager 5.x Linux Patch Pending **
vCenter Support Assistant 5.x Linux Patch Pending
vCloud Automation Center 6.x Linux Patch Pending
vCloud Automation Center
Application Services 6.x Linux Patch Pending
vCloud Director Appliance 5.x Linux 5.5.1.3
vCloud Connector 2.x Linux Patch Pending
vCloud Networking and Security 5.x Linux Patch Pending
vCloud Usage Meter 3.x Linux Patch Pending
vFabric Application Director 5.x, 6.x Linux Patch Pending
vFabric Postgres 9.x Linux Patch Pending
Viewplanner 3.x Linux Patch Pending
VMware Application Dependency
Planner x.x Linux Patch Pending
VMware Data Recovery 2.x Linux 2.0.4
VMware HealthAnalyzer 5.x Linux Patch Pending
VMware Mirage Gateway 5.x Linux 5.1.1
VMware Socialcast On Premise x.x Linux Patch Pending
VMware Studio 2.x Linux Patch Pending
VMware TAM Data Manager x.x Linux Patch Pending
VMware Workbench 3.x Linux Patch Pending
vSphere App HA 1.x Linux Patch Pending
vSphere Big Data Extensions 1.x, 2.x Linux Patch Pending
vSphere Data Protection 5.x Linux Patch Pending
vSphere Management Assistant 5.x Linux Patch Pending
vSphere Replication 5.x Linux Patch Pending
vSphere Storage Appliance 5.x Linux 5.5.2
** This product includes Virtual Appliances that will be updated, the
product
itself is not a Virtual Appliance.
4. Solution
ESX
---
Downloads:
https://www.vmware.com/patchmgr/findPatch.portal
Documentation:
http://kb.vmware.com/kb/2090859
http://kb.vmware.com/kb/2090853
vCenter Server Appliance
------------------------
Downloads:
https://my.vmware.com/web/vmware/details?productId=353&downloadGroup=VC55U2
(scroll down to 5.5 Update 2a Appliance)
https://my.vmware.com/web/vmware/details?productId=285&downloadGroup=VCL-VS
P510-VC-51U2A
(scroll down to 5.1 Update 2b Appliance)
https://my.vmware.com/web/vmware/details?productId=229&downloadGroup=VC50U3
A
(scroll down to 5.0 Update 3b Appliance)
Documentation:
http://kb.vmware.com/kb/2091085
http://kb.vmware.com/kb/2091018
http://kb.vmware.com/kb/2091017
vCloud Director Appliance
-------------------------
Downloads:
www.vmware.com/go/try-vcloud-director
Documentation:
http://kb.vmware.com/kb/2091071
VMware Data Recovery
--------------------
Downloads:
https://my.vmware.com/web/vmware/details?productId=229&downloadGroup=VDR204
Documentation:
http://kb.vmware.com/kb/2091015
VMware Mirage Gateway
---------------------
Downloads:
https://my.vmware.com/web/vmware/details?downloadGroup=MIRAGE-510&productId
=407&rPId=6565
(See VMware Mirage Gateway Software)
Documentation:
http://kb.vmware.com/kb/2091090
vSphere Storage Appliance
-------------------------
Downloads:
https://my.vmware.com/web/vmware/details?downloadGroup=VSP55-VSA-552&produc
tId=354&rPId=6585
Documentation:
http://kb.vmware.com/kb/2091000
vCenter Log Insight
-------------------
Downloads:
https://my.vmware.com/web/vmware/details?downloadGroup=STRATA20&productId=4
12&rPId=5804
Documentation:
http://kb.vmware.com/kb/2091065
5. References
VMware Knowledge Base Article 2090740
http://kb.vmware.com/kb/2090740
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271 ,
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7169
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7186
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7187
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6277
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6278
- ------------------------------------------------------------------------
6. Change Log
2014-09-30 VMSA-2014-0010
Initial security advisory in conjunction with the release of
vCenter Log Insight 2.0 U1 on 2014-09-30.
2014-10-01 VMSA-2014-0010.1
Updated advisory in conjunction with the release of ESX 4.x patches,
vCenter Server Appliance 5.5 U2a, 5.1 U2b, and 5.0 U3b, vCloud Director
Appliance 5.5.1.3, VMware Data Recovery 2.0.4, VMware Mirage Gateway
5.1.1 and vSphere Storage Appliance 5.5.2 on 2014-10-01. Added
CVE-2014-6277 and CVE-2014-6278 as confirmed fixed.
- ------------------------------------------------------------------------
7. Contact
E-mail list for product security notifications and announcements:
http://lists.vmware.com/cgi-bin/mailman/listinfo/security-announce
This Security Advisory is posted to the following lists:
security-announce at lists.vmware.com
bugtraq at securityfocus.com
fulldisclosure at seclists.org
E-mail: security at vmware.com
PGP key at: http://kb.vmware.com/kb/1055
VMware Security Advisories
http://www.vmware.com/security/advisories
VMware Security Response Policy
https://www.vmware.com/support/policies/security_response.html
VMware Lifecycle Policy
https://www.vmware.com/support/policies/lifecycle.html
Twitter
https://twitter.com/VMwareSRC
Copyright 2014 VMware Inc. All rights reserved.
-----BEGIN PGP SIGNATURE-----
Version: Encryption Desktop 10.3.2 (Build 15337)
Charset: utf-8
wj8DBQFULDR2DEcm8Vbi9kMRAno8AKChLzy32utif3LnJt4DduKNpmH1MgCgqKl+
ycAq/Gx4gCwu6SjbjBdgmSs=
=81FF
-----END PGP SIGNATURE-----
[ MDVA-2014:017 ] python-django
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Advisory MDVA-2014:017 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : python-django Date : October 1, 2014 Affected: Business Server 1.0 _______________________________________________________________________ Problem Description: A regression with the MDVSA-2014:179 advisory was discovered. This advisory solves the problem by adding the missing get_random_string function. _______________________________________________________________________ Updated Packages: Mandriva Business Server 1/X86_64: 0766538572edf71d8c3f2908a465e047 mbs1/x86_64/python-django-1.3.7-1.6.mbs1.noarch.rpm 48b0d60ba0bbdba4e2a01559420e508c mbs1/SRPMS/python-django-1.3.7-1.6.mbs1.src.rpm _______________________________________________________________________ To up
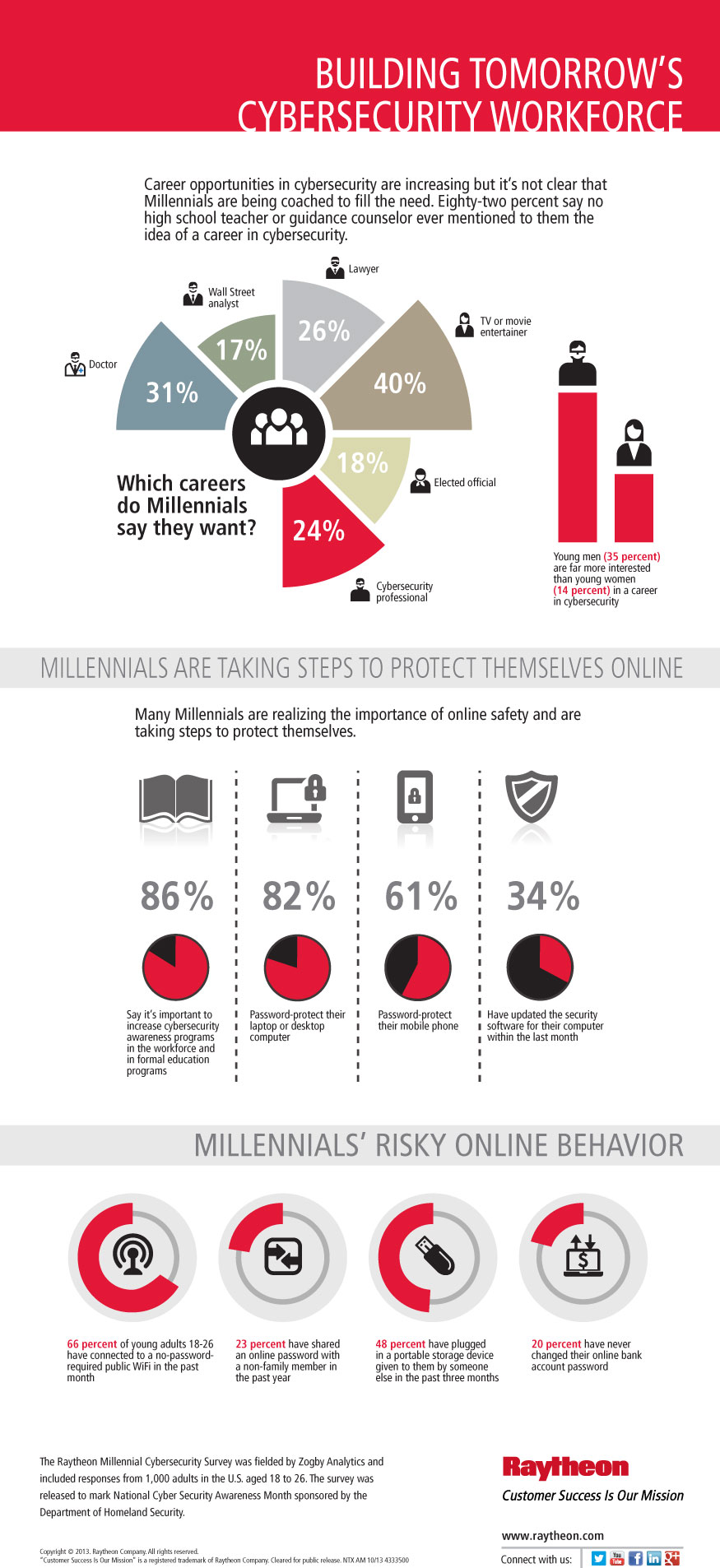
Millennials take responsibility for their own cybersecurity
A new trend has started – people are taking responsibility for their own safety online!
Last October when National Cyber Security Awareness Month (NCSAM) was getting started, it was reported that the incoming workforce of millennials was lax about cyber-risks. They engaged in risky online behavior like:
- Connecting to unprotected public WiFi networks
- Using a storage device that wasn’t their own
- Sharing a password with a non-family member
- Never changing their online banking password
2014 brings more awareness among “Digital Nativesâ€
For this year’s NCSAM, a new survey was done by defense contractor Raytheon in partnership with the U.S. Department of Homeland Security and the National Cyber Security Alliance. It showed that awareness of online safety is rising, with 70% of millennials saying they follow cybersecurity concerns and are up-to-date on the topic. Eighty-seven percent believe they are personally responsible for their online safety.
Millennials are known as the “Facebook generation†or “Digital natives†because they grew up in the “digital age†with internet-connected devices. But just because they were born after the digital age began, doesn’t mean they were any more concerned about security than the so-called digital immigrants who had to replace analog skills with digital. But this year, maybe because of the high profile data breaches that have occurred repeatedly, millennials are concerned about their devices being infected by malware, credit or debit card theft, someone hacking into financial information, or falling victim to online scams or fraud.
While many are aware of the risks – roughly 60% have experienced some sort of online violation – identity theft, a computer virus, or a bad experience on social media – they’re still engaging in some risky behaviors, such as 72% using public WiFi that doesn’t require a password.
Interestingly enough, this increased awareness is also driving interest in a career in cybersecurity with millennials expressing a desire to make the Internet safer and more secure. The problem is that almost two-thirds of the total don’t know or aren’t sure what the “cybersecurity†profession is.
STOP. THINK. CONNECT.
For millennials and everyone else, improving cybersecurity involves absorbing the STOP. THINK. CONNECT. message: Take a few safety precautions, understand the consequences of behaviors, and enjoy the Internet with more peace of mind.
To stay safer and more secure online everyone should:
- Keep a clean machine. Keep software up-to-date on all Internet-connected devices to reduce risk of infection and malware.
- Get two steps ahead. Switch on two-step verification or multi-factor authentication wherever offered to make your accounts more secure.
- When in doubt, throw it out. Links in email, posts, and texts are often the ways cybercriminals try to steal your information or infect your devices.
- Think before you app. Understand and be comfortable with what information (i.e., location, your contacts, social networking profiles, etc.) the app would access and share before you download it.
- Use a better password. Improve your defenses by making passwords that you can remember, are hard to guess, preferably use numbers, capital and lowercase letters and symbols and are different for all accounts.
- Post only about others what you would have them post about you. It’s the golden rule on the Internet, too.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.
Packet Storm New Exploits For September, 2014
This archive contains all of the 158 exploits added to Packet Storm in September, 2014.
Debian Security Advisory 3041-1
Debian Linux Security Advisory 3041-1 – Multiple security issues have been discovered in the Xen virtualisation solution which may result in denial of service, information disclosure or privilege escalation.