The VMware driver in OpenStack Compute (Nova) before 2014.1.4 allows remote authenticated users to cause a denial of service (disk consumption) by deleting an instance in the resize state.
Monthly Archives: October 2014
CVE-2014-8081
lib/execute/execSetResults.php in TestLink before 1.9.13 allows remote attackers to conduct PHP object injection attacks and execute arbitrary PHP code via the filter_result_result parameter.
CVE-2014-8495
Citrix XenMobile MDX Toolkit before 9.0.4, when used to wrap iOS 8 applications, does not properly encrypt cached application data, which allows context-dependent attackers to obtain sensitive information by reading the cache.
CVE-2014-8399
The default configuration in systemd-shim 8 enables the Abandon debugging clause, which allows local users to cause a denial of service via unspecified vectors.
CVE-2014-8334
The WP-DBManager (aka Database Manager) plugin before 2.7.2 for WordPress allows remote authenticated users to execute arbitrary commands via shell metacharacters in the (1) $backup[‘filepath’] (aka “Path to Backup:” field) or (2) $backup[‘mysqldumppath’] variable.
CVE-2014-8577
Multiple cross-site scripting (XSS) vulnerabilities in Croogo before 2.1.0 allow remote attackers to inject arbitrary web script or HTML via the (1) data[Contact][title] parameter to admin/contacts/contacts/add page; (2) data[Block][title] or (3) data[Block][alias] parameter to admin/blocks/blocks/edit page; (4) data[Region][title] parameter to admin/blocks/regions/add page; (5) data[Menu][title] or (6) data[Menu][alias] parameter to admin/menus/menus/add page; or (7) data[Link][title] parameter to admin/menus/links/add/menu page.
CVE-2014-8509
The lazy_bdecode function in BitTorrent bootstrap-dht (aka Bootstrap) allows remote attackers to execute arbitrary code via a crafted packet, which triggers an out-of-bounds read, related to “Improper Indexing.”
Google Working on Tool to Gather Stats While Preserving Privacy
Google is working on a new system that enables the company to collect randomized information about the way that users are affected by unwanted software on their machines, without gathering identifying data about the users. The system is known as RAPPOR (Randomized Aggregatable Privacy-Preserving Ordinal Response) and Google currently is testing it in Chrome. The […]
Over 20 million new strains of malware were identified in Q3 2014
The growth of malware appears unstoppable. In total, some 20 million new strains were created worldwide in the third quarter of the year, at a rate of 227,747 new samples every day.
Similarly, the global infection ratio was 37.93%, slightly up on the previous quarter (36.87%).
These are just a few of the figures presented by Luis Corrons, Technical Director of PandaLabs, from the latest quarterly report.

As you can see, this latest presentation had a slightly different feel to it from others in the past. We’ll show you more later. ![]()
Trojans are on the increase
Trojans are still the most common type of malware (78.08%). A long way behind in second place come viruses (8.89), followed by worms (3.92%).
Luis explained that “In these last months we have seen how cyber-crime has continued to grow. Criminals haven’t ceased to create malware in order to infect as many systems as possible so as to access sensitive or confidential information.â€
“Corporate environments are also under attack,†he added. “In the last three months many large companies have been drawn into numerous scandals, including the so-called ‘Celebgate’, where nude photos of actresses and models hosted on Apple’s iCloud service were leaked, or the theft of passwords for Gmail and Dropbox.”
Trojan infections rise while PUPs drop
On the other hand, Trojans also accounted for most infections during this period, some 75% of the total, compared with 62.80% in the previous quarter.
PUPs are still in second place, responsible for 14.55% of all infections, which is down on the second quarter figure of 24.77. These are followed by adware/spyware (6.88%), worms (2.09%), and viruses (1,48).
Infections by country
With respect to the data across different countries, China still has the highest infection rates, at 49.83%, followed by Peru (42.38%) and Bolivia (42.12%).
In fact, the ranking of countries with the highest infection rates is dominated by Asian and Latin American countries. Spain (at 38.37%) is also among the countries with infection rates above the global average.
Europe is the region with least infections, with nine countries in the top ten most secure. Norway (23.07%) and Sweden (23.44%) top the list, followed by Japan (24.02%), the only non-European country in the ranking.
Presentation of the PandaLabs Quarterly Report
As we mentioned before, this quarter’s presentation had a slightly spooky feel to it, with skulls, ghosts, presents and plenty of other surprises!
Here are some photos of our Halloween presentation.




The post Over 20 million new strains of malware were identified in Q3 2014 appeared first on MediaCenter Panda Security.
Don’t fall for these scams this Halloween!
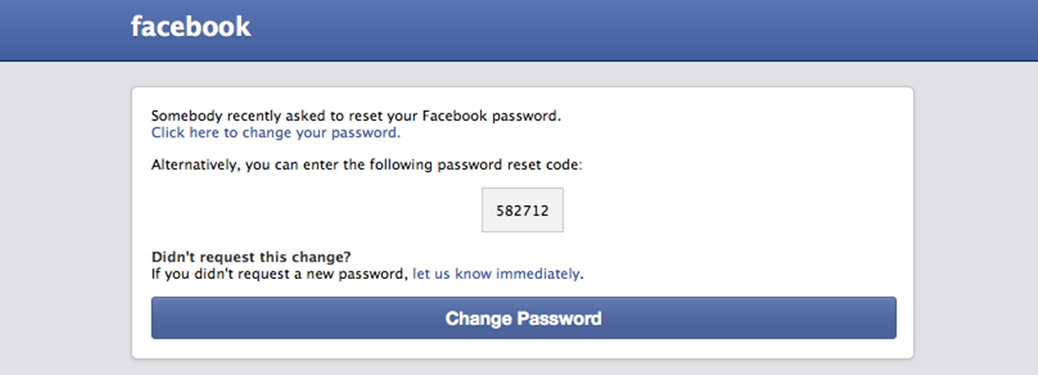
Facebook Reset Scam
The Facebook reset requests arrived via email and text message: “Somebody asked to reset your Facebook password.†At first it was annoying; then it was worrisome – a possible scam/phishing target.
Facebook says that these alerts are sometimes triggered due to a person mistakenly entering the same name and then, when their password doesn’t work, the customer asks for a reset. That might be possible in certain cases, but just based on the constant messaging, this was clearly beyond a normal user mistake, and an imitator scam.
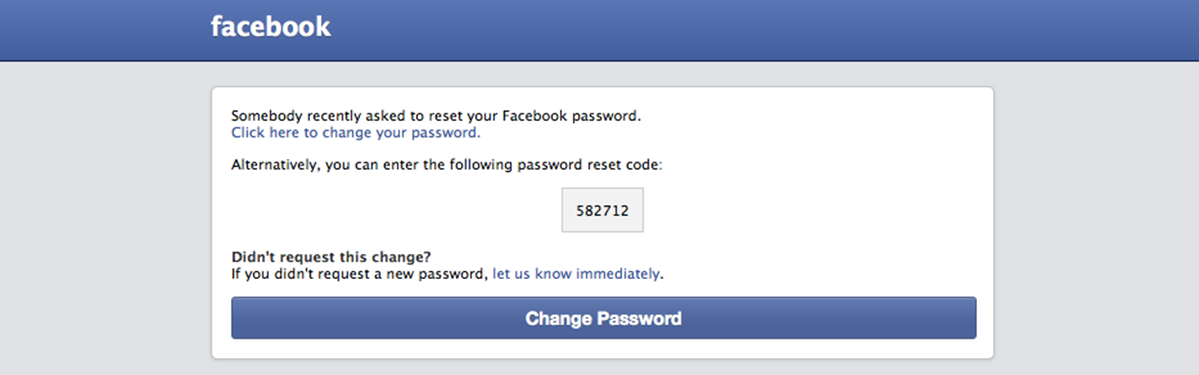
Let’s set aside the fact that although I have unlimited mobile data, many people don’t, and would end up paying for these unwanted texts. What’s more problematic is thinking about the many users who unsuspectingly fall for the request, click away and sign away their passwords.
Facebook says it will never ask you for your password, so if this happens to you, resist the urge to click. Any time you receive an urgent call to action in an email, be wary.  Don’t click on links contained in emails as a general rule. Instead, go to Facebook manually and look at the notifications. Needless to say, keep your anti-virus software up-to-date and use a password manager to keep your passwords safe and secure.
Facebook itself advocates the following steps:
- Use an up-to-date browser
- Use unique logins and passwords for each of the websites you use.
- Check to see that you’re logging in from a legitimate Facebook page with the facebook.com domain.
- Be cautious of any message, post or link you find on Facebook that looks suspicious or requires an additional login.
IRS and Other Scary Calls
You might imagine getting a voice message from the IRS wouldn’t be good news. And it’s not! This is a current scam making the rounds: Someone claiming to be an officer of the Internal Revenue Office leaves a message for you or your legal representative to call their hotline regarding an extremely time sensitive issue – before they take legal action. I was immediately suspicious: Would the IRS really leave me a phone message if there were an issue? The answer is “No.â€
What’s really scary is that the IRS reported in August 2014 it had received 90,000 complaints and identified approximately 1,100 people who have fallen victim, given up credit card numbers, etc. and lost an estimated $5 million from these scams.  You can learn more about the same on IRS. gov.
Fast forward to another cell scam: persistent calls received from an unknown number in the local area code. No voicemails were left. But after the calling persisted several times a day for a few days, you become curious as to who was calling. When I rang the number I got a “This number has been disconnected†message…
Lots of research later and it’s unclear as to whether this is just some weird harassment or part of the “One-ring†cell phone scam that the FTC has issued warnings about. In the latter scenario, scammers are using auto-dialers to call cell phone numbers across the country. They let the phone ring once and hang up — hoping you’ll call back, either because you believe a legitimate call was cut off, or you will be curious about who called. If you do, chances are you’ll hear something like, “Hello. You’ve reached the operator, please hold.†While waiting, you rack up some hefty charges — a per-minute charge on top of an international rate. The FTC notes: There’s no danger in getting the call: the danger is in calling back and racking up a whopping bill. If you’re tempted to call back, try checking the number first through online. Go here to learn more.
As for persistent calls, you can block them. You can block calls on both Android and iOS phones. On an iPhone look on your list of recent calls, just click the “i” in the circle to the right of the number. It will open an info tab, just scroll to the bottom and click block number. You should also report the number to your service provide (AT&T, Verizon, etc.) to get them blocked there.Halloween comes and goes, but scary scams will continue, and it requires a higher level of awareness from all of us! Check out AVG’s Facebook page for ongoing alerts and simple tips to help your friends be more safe online!
![]()
![]()