Monthly Archives: February 2015
BMW Fixes Security Flaw That Left Locks Open To Hackers
DNS Hijack in D-Link Routers, No Authentication Required
There is a remotely exploitable domain name system hijack vulnerability in D-Link’s DSLR2740R router.
Apple ID user? Careful! There is a new phishing attack!
Careful! We have detected a new phishing attack!
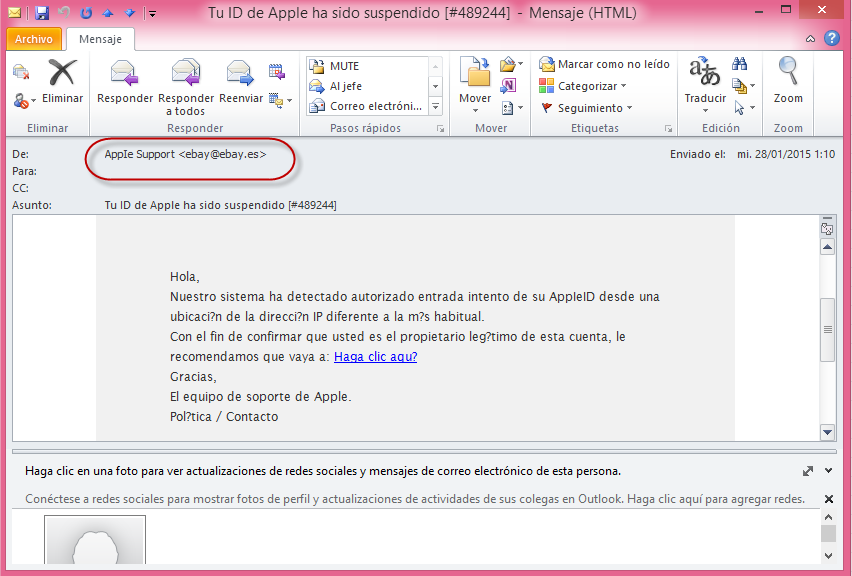
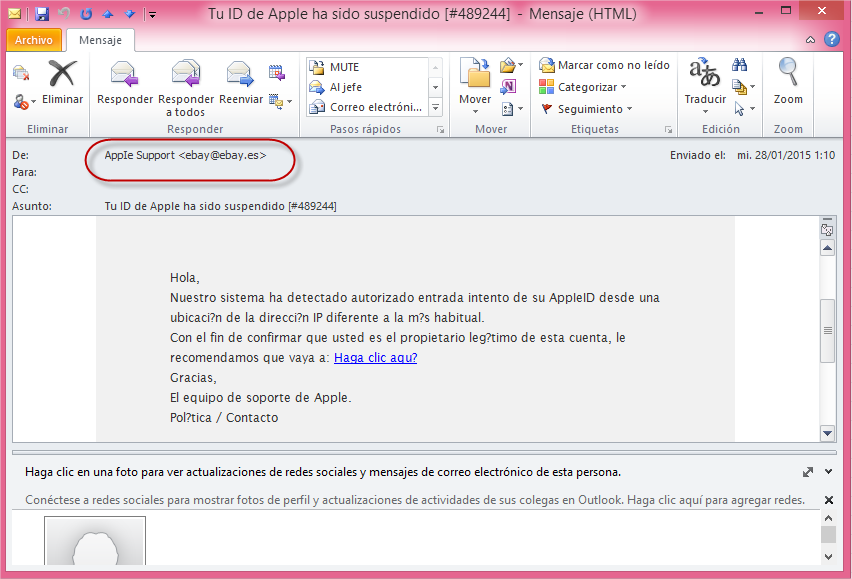
If you receive an email with the Spanish text: “Hola, nuestro sistema ha detectado autorizado entrada intento de su Apple ID…” (“Hello, our system has detected authorized access attempt of your Apple ID…,”) careful, it is phishing!
Below is an example of the email and the first thing that should catch your attention is the sender’s email address: AppIe Support <[email protected]>
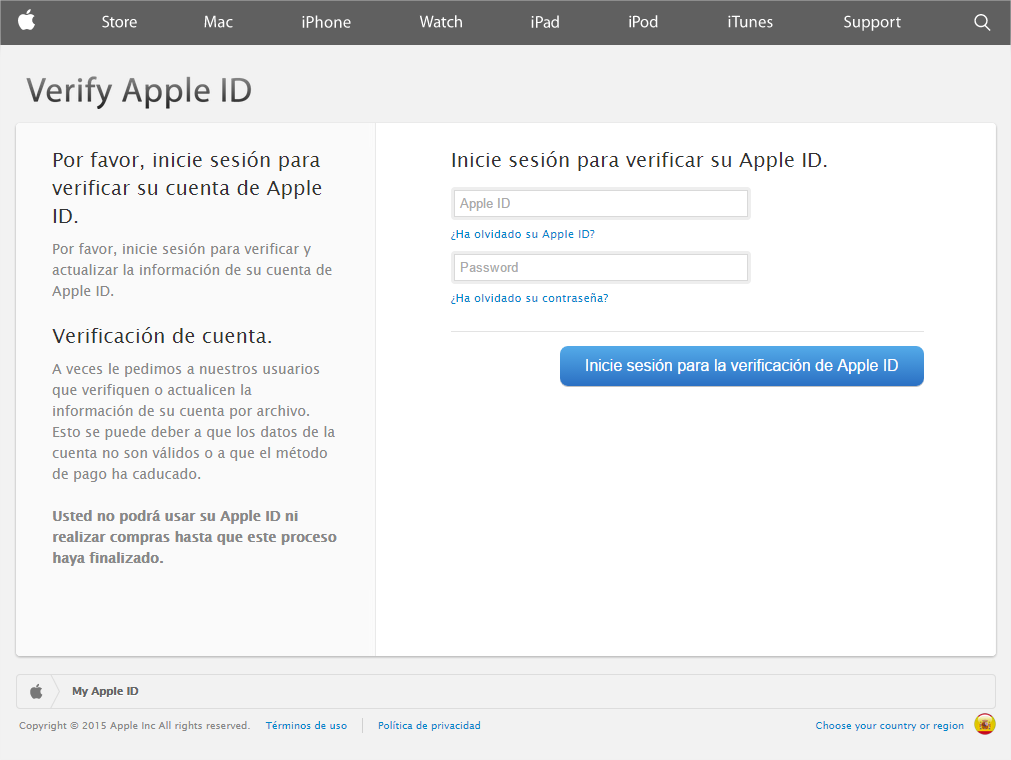
Using the excuse that someone has tried to access your Apple ID account, the cyber-criminals ask you to change your details. When you click on the link, a page opens that is an almost perfect imitation of Apple’s website:
After signing in with your Apple ID login details, the next step is to update your personal details.
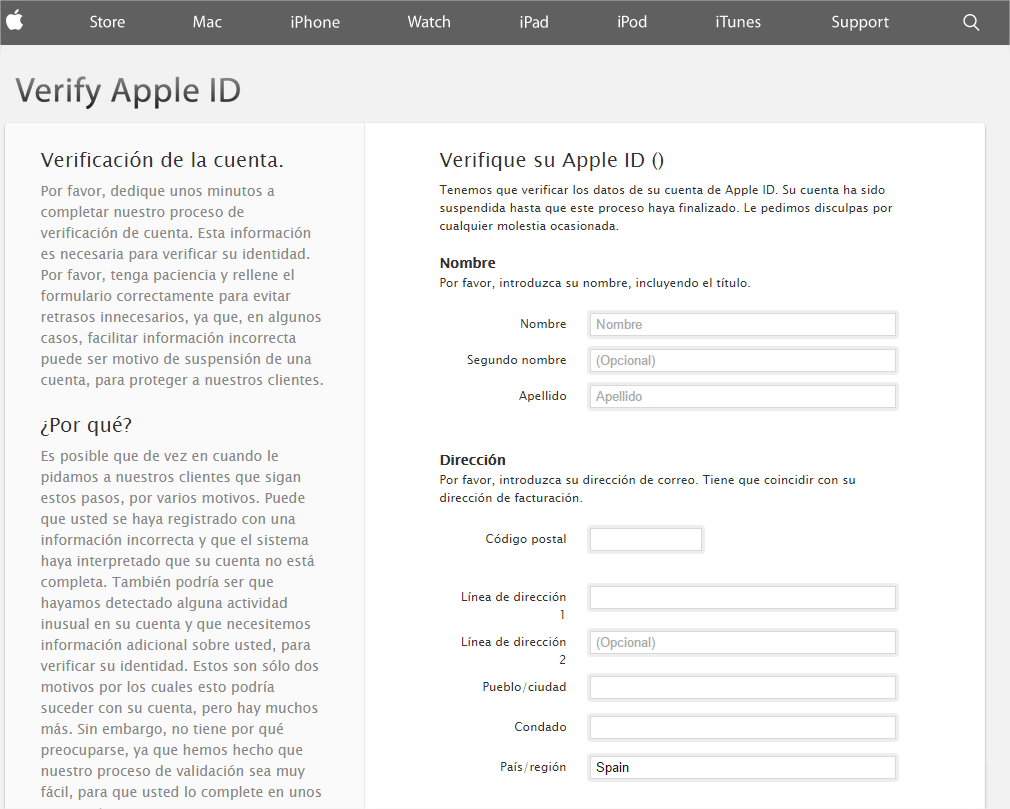
In addition to your name, address or telephone number, it requests your bank and credit card details in order to verify your identity and as the default method of payment for purchases and for iTunes or the App Store.
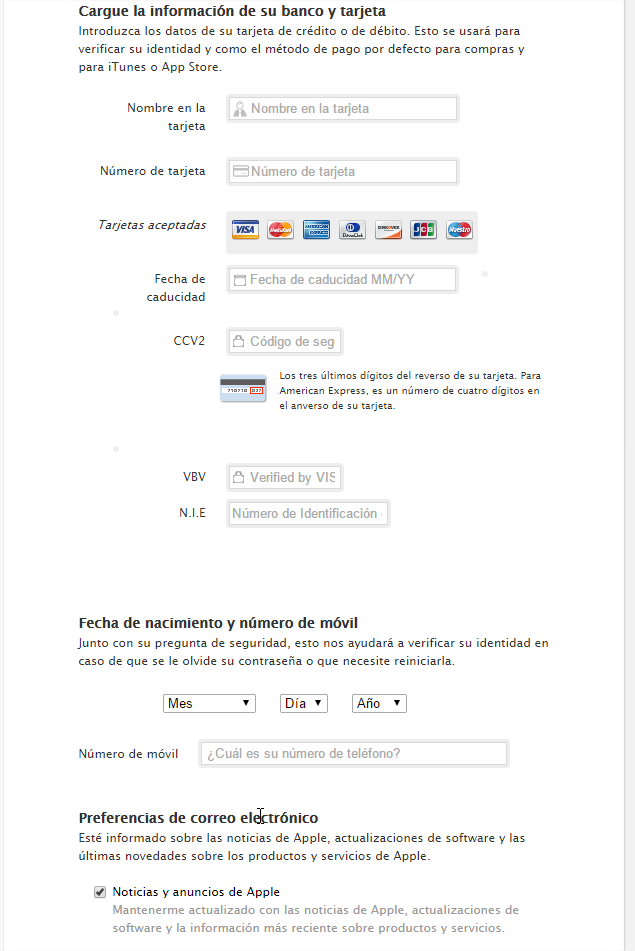
So, if you fall into the trap and enter all of this data, you will be giving the criminals access to this sensitive information.
As we always say, no company will ever ask you to send your personal details to them via email. If they do, be suspicious! In addition, in this case prevention is better than cure and it is important to have an extra layer of protection by installing one of the antivirus software from our 2015 line.
The post Apple ID user? Careful! There is a new phishing attack! appeared first on MediaCenter Panda Security.
Panda Security improves its positon in the Visionaries Quadrant of Gartner Magic Quadrant
Panda Security, Cloud Security, announces that it has been included as a Visionary in the ‘Gartner Magic Quadrant for Endpoint Protection Platforms’, published on December 22, 2014. The company, which has been included in this quadrant for the seventh consecutive year, has improved its positioning.
The Gartner report evaluated all of the vendors in the endpoint protection platforms market based on their products, completeness of vision and ability to execute.
“We believe industry has assessed positively the new technologies incorporated by Panda Security in the fight against malware. We feel this emphasizes that Panda Security is the first vendor in the endpoint protection platforms market to offer a service that classifies all executables running on endpoints, which represents a significant innovation compared to the current products”, said Josu Franco, VP Corporate Development at Panda Security.
We feel this new evaluation strengthens the path taken years ago by Panda Security towards a strategy that is fully committed to offering cloud-based services and a new protection model.
A complimentary copy of the Gartner, Magic Quadrant for Endpoint Protection Platforms, Peter Firstbrook, John Girard, Neil MacDonald, December 22, 2014 is available here.
The post Panda Security improves its positon in the Visionaries Quadrant of Gartner Magic Quadrant appeared first on MediaCenter Panda Security.
CVE-2015-0866
Multiple cross-site scripting (XSS) vulnerabilities in Zoho ManageEngine SupportCenter Plus 7.9 before hotfix 7941 allow remote attackers to inject arbitrary web script or HTML via the (1) fromCustomer, (2) username, or (3) password parameter to HomePage.do.
CVE-2015-1049
The web server on Siemens SCALANCE X-200IRT switches with firmware before 5.2.0 allows remote attackers to hijack sessions via unspecified vectors.
CVE-2015-1357
Siemens Ruggedcom WIN51xx devices with firmware before SS4.4.4624.35, WIN52xx devices with firmware before SS4.4.4624.35, WIN70xx devices with firmware before BS4.4.4621.32, and WIN72xx devices with firmware before BS4.4.4621.32 allow context-dependent attackers to discover password hashes by reading (1) files or (2) security logs.
CVE-2015-1383
Cross-site scripting (XSS) vulnerability in the geo search widget in the Geo Mashup plugin before 1.8.3 for WordPress allows remote attackers to inject arbitrary web script or HTML via the search key.
CVE-2015-1385
Cross-site scripting (XSS) vulnerability in the Blubrry PowerPress Podcasting plugin before 6.0.1 for WordPress allows remote attackers to inject arbitrary web script or HTML via the cat parameter in a powerpress-editcategoryfeed action in the powerpressadmin_categoryfeeds.php page to wp-admin/admin.php.