Resolved Bugs
1186358 – moarvm requires update to build on aarch64<br
update to 2015.04
Monthly Archives: May 2015
HUAWEI MobiConnect 23.9.17.216 – Privilege Escalation Vulnerability
Posted by Vulnerability Lab on May 04
Document Title:
===============
HUAWEI MobiConnect 23.9.17.216 – Privilege Escalation Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1389
Release Date:
=============
2015-05-04
Vulnerability Laboratory ID (VL-ID):
====================================
1389
Common Vulnerability Scoring System:
====================================
6.7
Product & Service Introduction:…
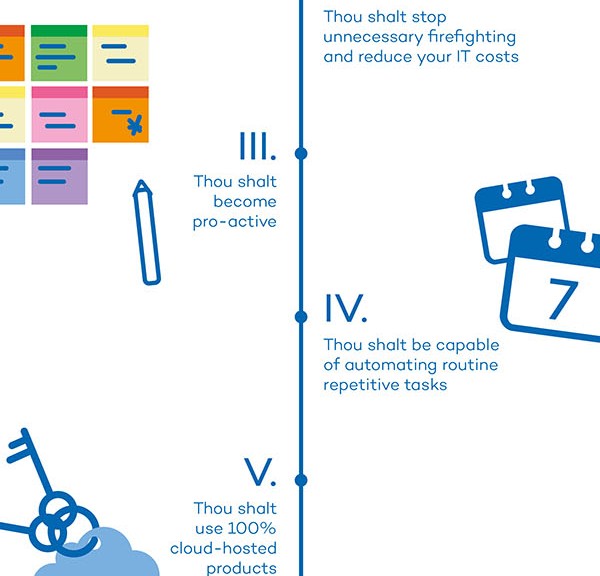
10 commandments for remote desktop managers – Infographic
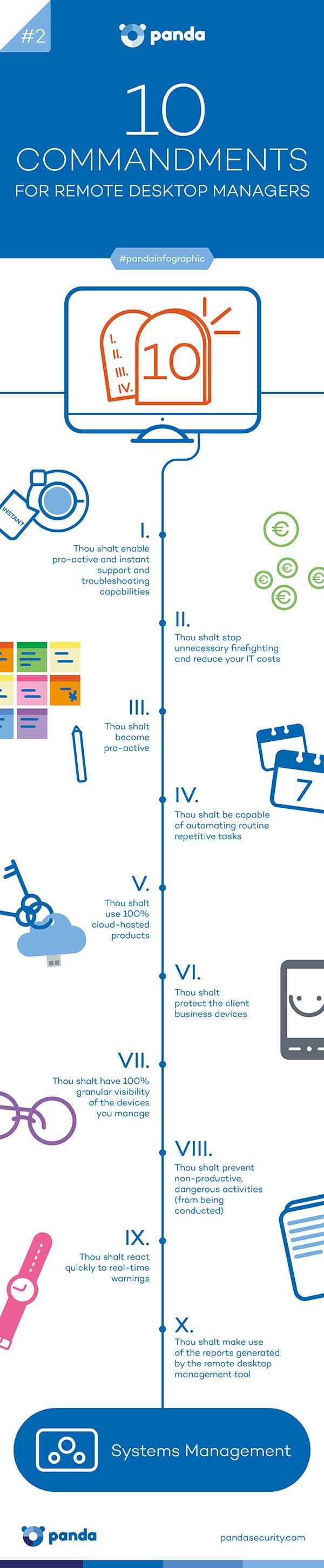
Try Systems Management, the new way to manage, monitor and support IT systems!
If you want to share this infographic, here you have the code:
The post 10 commandments for remote desktop managers – Infographic appeared first on MediaCenter Panda Security.
[ MDVSA-2015:220 ] curl
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:220 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : curl Date : May 4, 2015 Affected: Business Server 1.0 _______________________________________________________________________ Problem Description: Updated curl packages fix security vulnerabilities: NTLM-authenticated connections could be wrongly reused for requests without any credentials set, leading to HTTP requests being sent over the connection authenticated as a different user (CVE-2015-3143). When doing HTTP requests using the Negotiate authentication method along with NTLM, the connection used would not be marked as authenticated, making it possible to reuse it and send requests for one user over the connection authenticated as a different user (CVE-2015-3148)
[ MDVSA-2015:219 ] curl
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:219 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : curl Date : May 4, 2015 Affected: Business Server 2.0 _______________________________________________________________________ Problem Description: Updated curl packages fix security vulnerabilities: NTLM-authenticated connections could be wrongly reused for requests without any credentials set, leading to HTTP requests being sent over the connection authenticated as a different user (CVE-2015-3143). When parsing HTTP cookies, if the parsed cookie's path element consists of a single double-quote, libcurl would try to write to an invalid heap memory address. This could allow remote attackers to cause a denial of service (crash) (CVE-2015-3145). When doing HTTP re
DSA-3250 wordpress – security update
Multiple security issues have been discovered in WordPress, a weblog
manager, that could allow remote attackers to upload files with invalid
or unsafe names, mount social engineering attacks or compromise a site
via cross-site scripting, and inject SQL commands.
DSA-3249 jqueryui – security update
Shadowman131 discovered that jqueryui, a JavaScript UI library for
dynamic web applications, failed to properly sanitize its title
option. This would allow a remote attacker to inject arbitrary code
through cross-site scripting.
CVE-2015-0714
Multiple cross-site scripting (XSS) vulnerabilities in Cisco Finesse Server 10.0(1), 10.5(1), 10.6(1), and 11.0(1) allow remote attackers to inject arbitrary web script or HTML via unspecified parameters, aka Bug ID CSCut53595.
Fedora 21 Security Update: kernel-3.19.6-200.fc21
Resolved Bugs
1208999 – iscsi issues on 3.19 kernel
1204390 – [abrt] WARNING: CPU: 6 PID: 790 at drivers/media/v4l2-core/v4l2-ioctl.c:1025 v4l_querycap+0x41/0x70 [videodev]() [videodev]
1206036 – Impossible to reduce the display brightness under the new kernel – Toshiba Z30 laptop
1215989 – Backlight is non-responsive on Toshiba Satellite
1205083 – [abrt] WARNING: CPU: 3 PID: 644 at drivers/net/wireless/iwlwifi/mvm/tx.c:952 iwl_mvm_rx_ba_notif+0x525/0x5c0 [iwlmvm]() [iwlmvm]
1214030 – CVE-2015-3339 kernel: race condition between chown() and execve()<br
The 3.19.6 stable update contains an number of fixes across the kernel tree
Fedora 21 Security Update: rubygem-sup-0.21.0-1.fc21
Resolved Bugs
1024650 – CVE-2013-4479 rubygem-sup: command injection flaw in content type handling [fedora-all]<br
Add new source tarball and updated dependecies