Resolved Bugs
1205083 – [abrt] WARNING: CPU: 3 PID: 644 at drivers/net/wireless/iwlwifi/mvm/tx.c:952 iwl_mvm_rx_ba_notif+0x525/0x5c0 [iwlmvm]() [iwlmvm]
1208999 – iscsi issues on 3.19 kernel
1214030 – CVE-2015-3339 kernel: race condition between chown() and execve()
1204390 – [abrt] WARNING: CPU: 6 PID: 790 at drivers/media/v4l2-core/v4l2-ioctl.c:1025 v4l_querycap+0x41/0x70 [videodev]() [videodev]
1206036 – Impossible to reduce the display brightness under the new kernel – Toshiba Z30 laptop
1215989 – Backlight is non-responsive on Toshiba Satellite<br
The 3.19.6 stable updates contains a number of important fixes across the tree
Monthly Archives: May 2015
Fedora 22 Security Update: python-keystonemiddleware-1.3.1-1.fc22
Resolved Bugs
1209527 – CVE-2015-1852 OpenStack keystonemiddleware/keystoneclient: S3Token TLS cert verification option not honored<br
Update to upstream 1.3.1 + S3token incorrect condition expression for ssl_insecure CVE-2015-1852
Fedora 22 Security Update: rubygem-sup-0.21.0-1.fc22
Resolved Bugs
1024650 – CVE-2013-4479 rubygem-sup: command injection flaw in content type handling [fedora-all]<br
Add new source tarball and updated dependecies
The famous reversible USB could be a ‘malware’ loophole for your devices

Wouldn’t it be nice not having to turn around several times your USB before connecting it to the computer? You won’t remember that feeling, very soon. The new connector Type-C USB, better known as reversible USB, is the answer to your problems, with the same number of pins or connectors in both sides. It will allow you to transfer data much faster as video signals or electric energy, with a similar size of a micro USB.
It is predicted that this new connector will be the standard in the future and maybe someday we will be able to charge all our devices with it. This specification, announced a couple of months ago by the USB Implementers Forum (USB-IF), is already been included in some laptops. Apple’s new MacBook integrates a USB-C port which allows you to charge your phone and to connect it with conventional devices, though you will have to buy a separate adapter.
Google has followed up and will include two new USB-C ports in their new ultra-thin laptop, the Chroomebook Pixel. The incorporation of these ports will be the trend to follow in the next months.

But it’s not all good news here: the new USB-C brings serious safety issues. After all it is based on the standard USB so it is vulnerable to ‘firmware’ attacks and other kinds of attacks that would affect the device in which the USB is connected to.
None of these issues are new, probably your USB drive has been infected more than once after connecting it to different computers. However, if we consider that the purpose of this new USB is to create a universal connector we will be facing more and more sophisticated attacks, which will be more difficult to avoid, so the port will become a malware loophole.
BadUSB vulnerability
One of the biggest concerns is the recent discovered BadUSB vulnerability, which lives in the firmware and modifies it, allowing the connected mobile device to become an attack vector.
“The additional openness and flexibility of USB Type-C comes with more attack surface,” says Karsten Nohl, one of the researchers who first discovered this type of attacks. “No solution for BadUSB is in sight even with this new standard.” USB is an open standard built on backwards compatibility and easy third-party access, which implies a serious security problem and which is not even near to fix it.

In practical terms, this means MacBook and Chromebook Pixel users are exposed to what we call a “borrowed charged attack”. Although new chargers don’t have the necessary firmware to carry the BasUSB malware, it would be very easy to infect a device and spread it within the compatible gadgets. After all, who doesn’t share almost daily a USB cable with another person?
Although Apple includes an authentication chip in all their power cords to verify that the firmware has not been changed, the port remains vulnerable to older devices.
If you have already decided to buy the latest MacBook or the new Chromebook, the best thing you can do to protect it, is to avoid connecting it to a device or charger you haven’t purchased. Despite all the benefits these reversible USB ports have, like high speed and efficiency, security must be improved to enjoy all the advantages of USB-C on laptops.
The post The famous reversible USB could be a ‘malware’ loophole for your devices appeared first on MediaCenter Panda Security.
TGIF: Avast news wrap up for April 18 – May 1
The Avast bi weekly wrap-up is a quick summary of what was on the Avast blog for the last two weeks.
 Most everyone knows their PC needs antivirus protection, but they don’t think about their smartphone. These days smartphones are just about as powerful and have as much or more personal information as our desktop PC at home. We answer the question do Android devices really need protection?
Most everyone knows their PC needs antivirus protection, but they don’t think about their smartphone. These days smartphones are just about as powerful and have as much or more personal information as our desktop PC at home. We answer the question do Android devices really need protection?
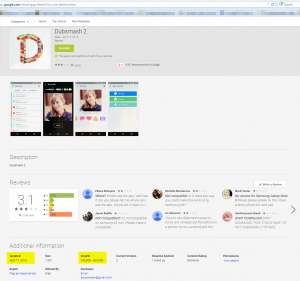 The answer is a resounding YES. The Avast Virus Lab gives us an example from a trusted download source, Google Play: A porn clicker app slipped into Google Play imitating the popular Dubsmash app. If we cannot completely rely on trusted app stores to weed out nasty apps, then it’s time to add an extra layer of security.
The answer is a resounding YES. The Avast Virus Lab gives us an example from a trusted download source, Google Play: A porn clicker app slipped into Google Play imitating the popular Dubsmash app. If we cannot completely rely on trusted app stores to weed out nasty apps, then it’s time to add an extra layer of security.
 Once you decide that you do want to protect your Android device, you can be confident in Avast Mobile Security, Avast’s free security app available on Google Play. A survey by AV -Comparatives said that Avast was the #1 choice for mobile security in the entire world. No need to wait any longer to protect your smartphone or tablet.
Once you decide that you do want to protect your Android device, you can be confident in Avast Mobile Security, Avast’s free security app available on Google Play. A survey by AV -Comparatives said that Avast was the #1 choice for mobile security in the entire world. No need to wait any longer to protect your smartphone or tablet.
 One of the challenges with using a smartphone for so many activities, is that the battery gives out before we do. Our new free app Avast Battery Saver raises the bar with new Wi-Fi based smart profiles that can increase battery life by an average of 7 hours.
One of the challenges with using a smartphone for so many activities, is that the battery gives out before we do. Our new free app Avast Battery Saver raises the bar with new Wi-Fi based smart profiles that can increase battery life by an average of 7 hours.
 Avast Battery Saver has only been available for a month or so but already 200,000 customers have downloaded it from the Google Play Store. For Earth Day we highlighted battery saver users for their positive impact on the environment. Who knew that Avast Battery Saver would be so green? A cool infographic shows just how much they saved – not only from their own battery – but in energy costs too. Now Earth Day can be everyday!
Avast Battery Saver has only been available for a month or so but already 200,000 customers have downloaded it from the Google Play Store. For Earth Day we highlighted battery saver users for their positive impact on the environment. Who knew that Avast Battery Saver would be so green? A cool infographic shows just how much they saved – not only from their own battery – but in energy costs too. Now Earth Day can be everyday!
 Small and medium-sized businesses (SMBs) run the risk of data breaches just like there Enterprise cousins. Luke Walling, the General Manager of Avast for Business, explains that the biggest threat to SMBs is not actually hackers sitting somewhere far away. The biggest threat to your SMB could be sitting in your office!
Small and medium-sized businesses (SMBs) run the risk of data breaches just like there Enterprise cousins. Luke Walling, the General Manager of Avast for Business, explains that the biggest threat to SMBs is not actually hackers sitting somewhere far away. The biggest threat to your SMB could be sitting in your office!
 Speaking of Avast for Business, our new disruptive free security offering for SMBs has 75,000 new customers in just 2 months. If you have a start-up, a small business, if you work in a school or non-profit organization, then it’s time to stop paying for security protection.
Speaking of Avast for Business, our new disruptive free security offering for SMBs has 75,000 new customers in just 2 months. If you have a start-up, a small business, if you work in a school or non-profit organization, then it’s time to stop paying for security protection.
 Our researchers are constantly surprised by the creativity of malware authors. Recently, they found a new way cybercrooks trick people in giving up their banking information. It’s a crafty combination of spam email, social engineering, and a macro code embedded in an innocent looking Word document.
Our researchers are constantly surprised by the creativity of malware authors. Recently, they found a new way cybercrooks trick people in giving up their banking information. It’s a crafty combination of spam email, social engineering, and a macro code embedded in an innocent looking Word document.
 Most people have security protection on their computers. That’s great when there are things like the banking malware we wrote about. With all that great protection why is it that they don’t trust the warnings? The Avast Virus Lab explored why some people would rather be right than believe a malware warning.
Most people have security protection on their computers. That’s great when there are things like the banking malware we wrote about. With all that great protection why is it that they don’t trust the warnings? The Avast Virus Lab explored why some people would rather be right than believe a malware warning.
Re: #WorldPenguinDay or this cant be right, can it?
Posted by PIN on May 02
Really? Because leaking a heap address in windows, openbsd, etc doesn’t
yield a full collapse of all loaded modules randomization given the
preconditions; I’m asking that it’s not just my box exhibiting this
behavior- which is a long story why it must just be mine.
considered a
Well, you are somewhat missing the gravity here. If this is generally
reproducible, you don’t need the address to leak, you just need a series of…
Re: #WorldPenguinDay or this cant be right, can it?
Posted by Tavis Ormandy on May 02
That wasn’t what I said.
Sure, If code with knowledge of an address is willing to act as an
oracle, then ASLR is not useful. This is really just an indirect (and
unlikely) way of leaking an address though.
Well, if you know in advance which address to leak you can arrange for
it to be a useless one, it would usually have to be MMAP_FIXED and be
sanitized (think KUSER_SHARED_DATA on Windows or the vsyscall page on
Linux) so as not to weaken…
Re: #WorldPenguinDay or this cant be right, can it?
Posted by PIN on May 02
We’ll but keep in mind here that the knowledge we are talking about is
based on the binary image as far as I can tell and knowledge of the order
of mapping, which given the mechanisms in place for privilege separation or
at least common forking a child is not that far of a stretch. “I am mapping
X and there will be Y mappings with a total size of Z before me whose base
address is A from the first/last loaded module”
Well but these…
DSA-3247 ruby2.1 – security update
It was discovered that the Ruby OpenSSL extension, part of the interpreter
for the Ruby language, did not properly implement hostname matching, in
violation of RFC 6125. This could allow remote attackers to perform a
man-in-the-middle attack via crafted SSL certificates.
DSA-3245 ruby1.8 – security update
It was discovered that the Ruby OpenSSL extension, part of the interpreter
for the Ruby language, did not properly implement hostname matching, in
violation of RFC 6125. This could allow remote attackers to perform a
man-in-the-middle attack via crafted SSL certificates.