 This whole FBI-Apple debate has the technology world up in a frenzy about national security vs. personal security. Apple’s refusal to give up classified information to a government agency tells us something about the current state of our online safety, and lots of tech companies are stepping up to fight for our privacy.
This whole FBI-Apple debate has the technology world up in a frenzy about national security vs. personal security. Apple’s refusal to give up classified information to a government agency tells us something about the current state of our online safety, and lots of tech companies are stepping up to fight for our privacy.
Recently, Google conducted a study to see if the most-popular websites follow something called HTTPS Protocol. HTTPS (the added ‘S’ for secure) provides authentication of a website, ensuring its credibility for its users by encrypting the communication on its server. This makes it so that important data like our usernames, passwords, or personal messages cannot be intercepted; kind of like having our own online-bodyguard who lets us know when we are browsing a trusted site.
The results of the study could not be more discouraging.
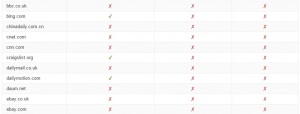
From the one hundred sites studied, 79 do not use HTTPS by default and 67 use an obsolete encryption technology, aka no security method at all. “According to our calculations, the list of web sites that we have presented constitute about 25% of all global traffic”, a Google spokesperson stated. Does this mean that these ultra-popular sites don’t worry about our online security? It sure seems that way.
What’s even more shocking is the prestige of these sites; among them are pages like The New York Times or CNN, e-commerce platforms like eBay or Aliexpress, and well-known industry leaders such as Softonic. Google has declared war with these non-users (it searches index sites that use HTTPS and crosses out the rest with a red x in the Chrome address bar) and offers tools so that any developer can easily implement this protocol. This Mountain View company believes in “[making] the Web a safer place not only for Google users, but for everyone in general.”
 Implementing this technology to add that ‘additional layer’ of security is extremely easy. Maybe the reason companies aren’t using this protocol is due to a lack of interest rather than a technical issue. Until recently, it took time and effort to develop a site with HTTPS but now there are platforms that facilitate the necessary certificates, for free.
Implementing this technology to add that ‘additional layer’ of security is extremely easy. Maybe the reason companies aren’t using this protocol is due to a lack of interest rather than a technical issue. Until recently, it took time and effort to develop a site with HTTPS but now there are platforms that facilitate the necessary certificates, for free.
Thankfully we have Google leading the crusade in making the Internet a safer place. Let’s continue to do what we do from the comfort of our laptop, like filling up that online shopping cart or making that bank transfer, but make sure to protect yourself. Always check for that extra ‘S’ and use a dependable antivirus service, like Panda, who will help you do it safely and smoothly.
The post Your favorite sites don’t use a secure connection appeared first on Panda Security Mediacenter.


 Implementing this technology to add that ‘additional layer’ of security is extremely easy. Maybe the reason companies aren’t using this protocol is due to a lack of interest rather than a technical issue. Until recently,
Implementing this technology to add that ‘additional layer’ of security is extremely easy. Maybe the reason companies aren’t using this protocol is due to a lack of interest rather than a technical issue. Until recently, 