GDPR is coming into play in May 2018, but a lot of companies remain unprepared, which could have implications on how they process data.
The post 10 ways to prepare your organization for GDPR appeared first on WeLiveSecurity
![]()
Antivirus Vendors
GDPR is coming into play in May 2018, but a lot of companies remain unprepared, which could have implications on how they process data.
The post 10 ways to prepare your organization for GDPR appeared first on WeLiveSecurity
![]()
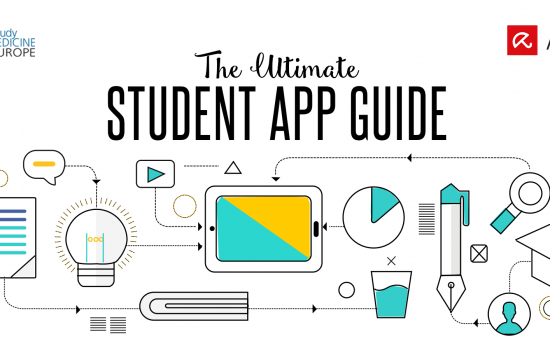
If you would like to be efficient, it is all about organization. There are a lot of apps which can help you to organize yourself – but what apps do you need to succeed in your studies? This student app guide provides you with the best possibilities to organize yourself. Starting your life as a student […]
The post [Infographic] The ultimate student app guide appeared first on Avira Blog.
TeamViewer, a remote control program, can be very handy when you need remote IT support. The cybercriminals behind TeamSpy, unfortunately, also find the tool to be quite useful and use it to carry out malicious activity.
![]()
ESET researchers have discovered and reported scammers stealing PayPal and Paxful credentials disguised as a tool for YouTube monetization, and a bitcoin trading marketplace.
The post Real or virtual currency? Scammers accept both appeared first on WeLiveSecurity
![]()
It’s not enough to say you are good. The moment of truth is when an outside expert or peer takes a hard look at what you do – and then gives you an educated thumbs up. In academia, this is a peer review and it is essential for any worthwhile paper. For software developers, it […]
The post Scout Browser goes under peer review appeared first on Avira Blog.
The Internet Society says that current perceptions of data encryption are misguided and need to change for the sake of the digital economy.
The post Internet Society: Encryption is key to growing world economy appeared first on WeLiveSecurity
![]()

Latvian-born hacker Alexsey Belan, a Russian citizen, has been on the FBI’s list of most wanted cybercriminals for some time. His latest misdeed was the theft of 500 million Yahoo accounts in order to spy on Russian journalists and officials from both the US government and the Kremlin itself.
The Department of Justice of the United States has officially accused him of the crime. The department suspects that he have committed the crime in collaboration with another cybercriminal and with two spies from the Russian Federal Security Service. Antichat was one of the cybercrime forums which Belan frequented. It is also one of those used by the Russian spyware company OpenGSM to recruit cybercriminals and increase their sales.
According to a Forbes investigation, OpenGSM has resold a tool to spy iPhones and Android smartphones that was developed by an American. Killer Mobile, a company headed by Joshua Alner, created a surveillance software called Tracer that has made its way to Russian shores.
A researcher who preferred to remain anonymous found an OpenGSM document that redirects users to a website owned by Alner from which a spyware kit could be obtained as part of a 600 euro package.
He also found Killer Mobile malware for Android on an OpenGSM website, proof that the company bought the vendor’s surveillance tools. In fact, Alner could have pocketed between 150 and 500 thousand dollars for that sale.
Neither Alner nor OpenGSM, which sells its software to government agencies and consumers, have come forth to comment about their research. Killer Mobile, a company with only ten employees, offered its malware — which is legally defined as a “hidden listening device” — to about sixty resellers in at least ten countries, an activity requiring an export license .
The spy software that OpenGSM commercialized served to host spyware on the devices of almost 800 users in Russia, Kazakhstan and the European Union in 2015. Another tool that OpenGSM offered, which was not developed by Killer Mobile, appears to have had mobile users in the US in its crosshairs.
Tensions are on the rise between geopolitical actors, both big and small, in the cyber-sphere, and as such we are collectively entering a period of uncertainty about where we stand in terms of our own personal security on our devices. Wherever the threat may come from, be it a government agency or a malware entrepreneur, it’s always best to be protected by an advanced cybersecurity solution.
The post The US Malware Developer who Helped Russia Spy on Devices appeared first on Panda Security Mediacenter.
There is no magic in machine learning. It’s a field of computer science that gives computers the ability to find patterns in huge amounts of data.
The post Don’t buy the elixir of youth: Machine learning is not magic appeared first on WeLiveSecurity
![]()

A NFC chip the size of a rice could turn you into a cyborg.
The post Here come the new office cyborgs: One of them could be you appeared first on Avira Blog.

We’re all familiar with the massive data leaks that Yahoo suffered last year. But until recently, we had very little in the way of clues as to who was behind the attacks which started at the beginning of 2014. As more evidence comes to light, it’s becoming increasingly apparent that this is not your run-of-the-mill cybercrime. According to a recent indictment by the US Department of Justice, the folks behind that attack appear to be agents of the Russian Federal Security Service.
The theft of 500 million Yahoo accounts three years ago was allegedly used as a way for the Russian government to access information on a series of targets ranging from the White House itself to cloud computing companies. Military officials, executives of financial companies, and even an airline company were also among the targeted.
In the name of espionage, this attack gave hackers the means of stealing data such as names, email addresses, and credentials. According to information provided by Yahoo in their announcement of the breach, the culprits would not have been able to access data of a more confidential nature, such as sensitive financial information.
In a somewhat ironic turn of events, the information provided by the Justice Department indictment appears to indicate that the stolen data was also used to spy on Russian government officials.
While this would not be the first time that Russian cybercriminals have been accused of data theft, it is in fact the first time that charges have been filed against officials operating in the shadow of Vladimir Putin. Although the agency is supposed to help agencies of other countries track down Russian cybercriminals, in this case two of its own operatives allegedly collaborated to conceal the robbery from their superiors.
“The involvement and direction of F.S.B. officers with law enforcement responsibilities makes this conduct that much more egregious,” said acting assistant US Attorney General Mary B. McCord.
Although the Russian administration has not given an official response to the US indictment, the country’s press has called into question the US Department of Justice’s movement.
In any case, and regardless of who is responsible for these or other breaches, massive data leaks at services such as Yahoo highlight the need to use secure credentials and a protection that is suited to the needs of your company to prevent the theft of confidential information, or even considerable sums of money, in the event of a cyberattack.
The post Who’s Behind the Yahoo Attack? It might be Russian Agents appeared first on Panda Security Mediacenter.