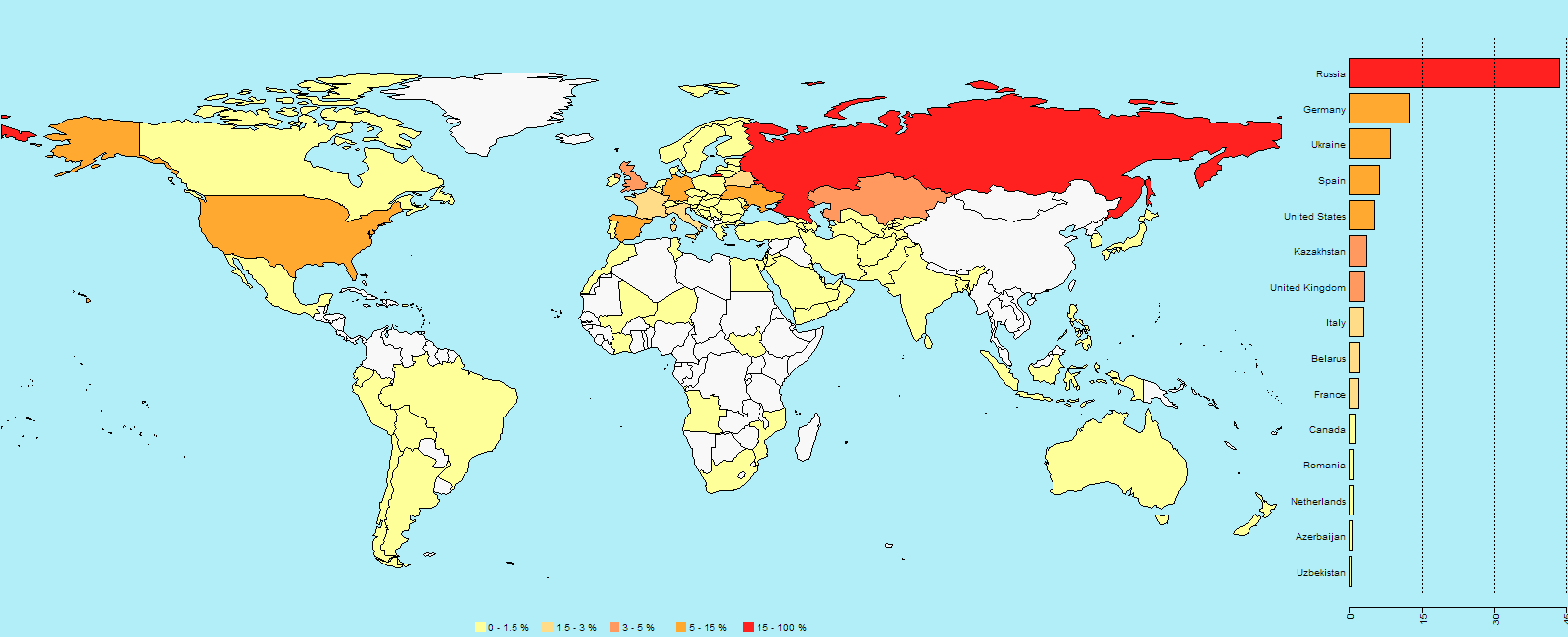
Sensitive business data is at risk when you travel. Take precautions to protect it.
Cybersecurity is not limited to your office or home. Nowadays, many of us use the same devices for work and personal business, so when traveling we need to be extra diligent to protect our devices and the data we have on them. If you use common sense and a bit of Avast technology, all your devices – laptops, smartphones, and tablets, can remain secure wherever you are.
Here are a few things you can do before you go and while you’re on-the-road:
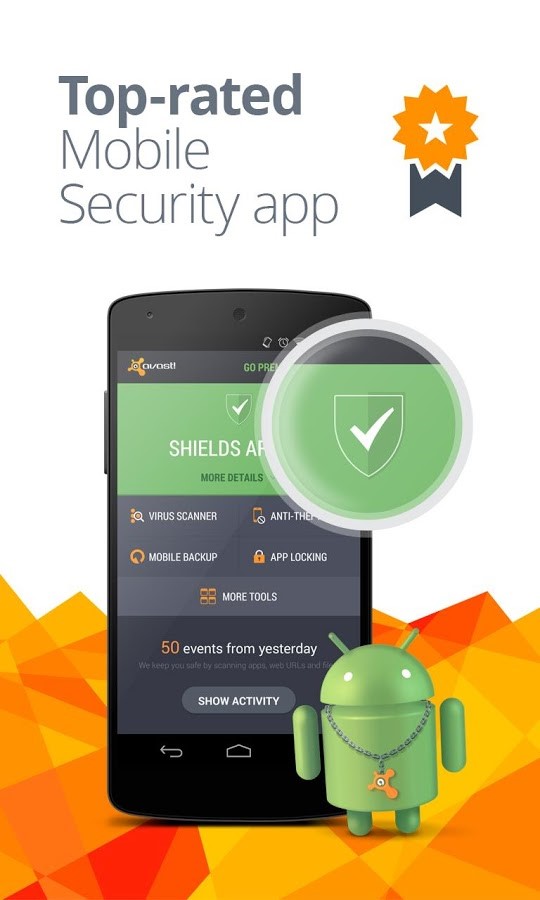
1. Install antivirus protection. Your first and best line of defense on your PC or Android device is antivirus protection. Install it and make sure it is up-to-date.
2. Keep your operating system and software up-to-date. Hackers take advantage of software with security holes that have not been plugged, so take time regularly to make sure that your software and apps have patches and updates applied.
3. Lock down your device. Make it a habit to lock your PC and phone with a PIN, password, or even a fingerprint. Avast Mobile Security even allows you to password-protect your apps. Before you travel, make sure your critical apps, like access to your bank, are protected.
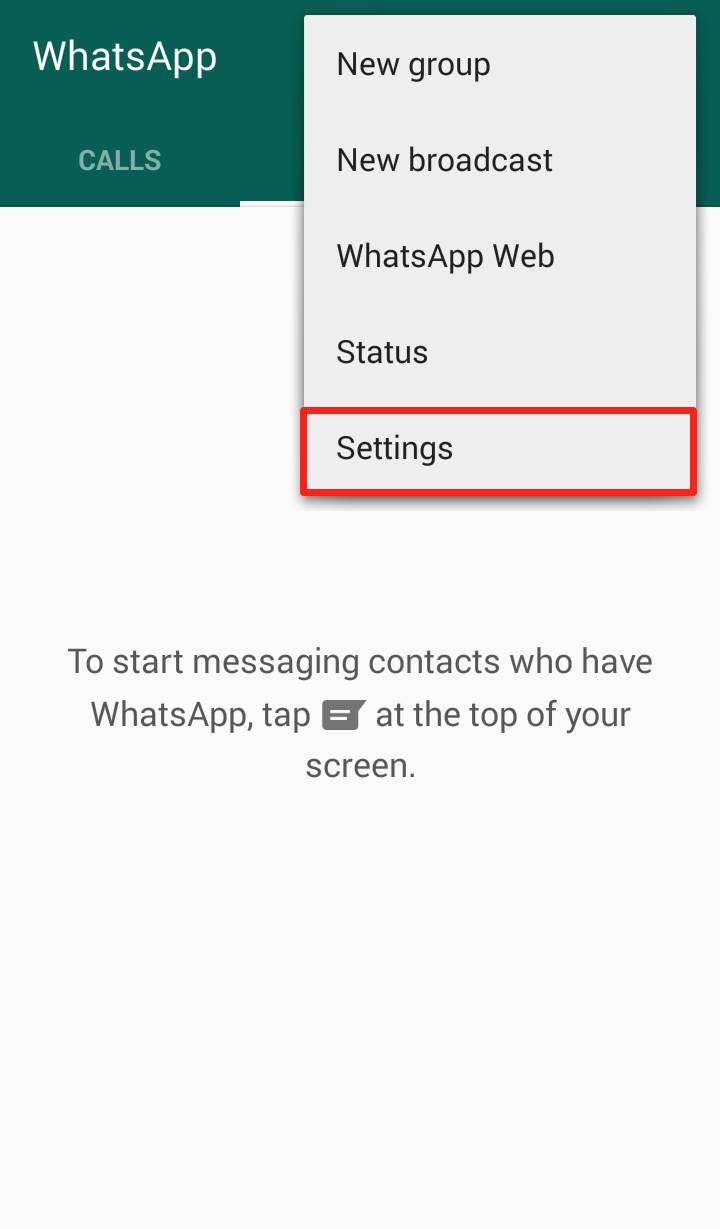
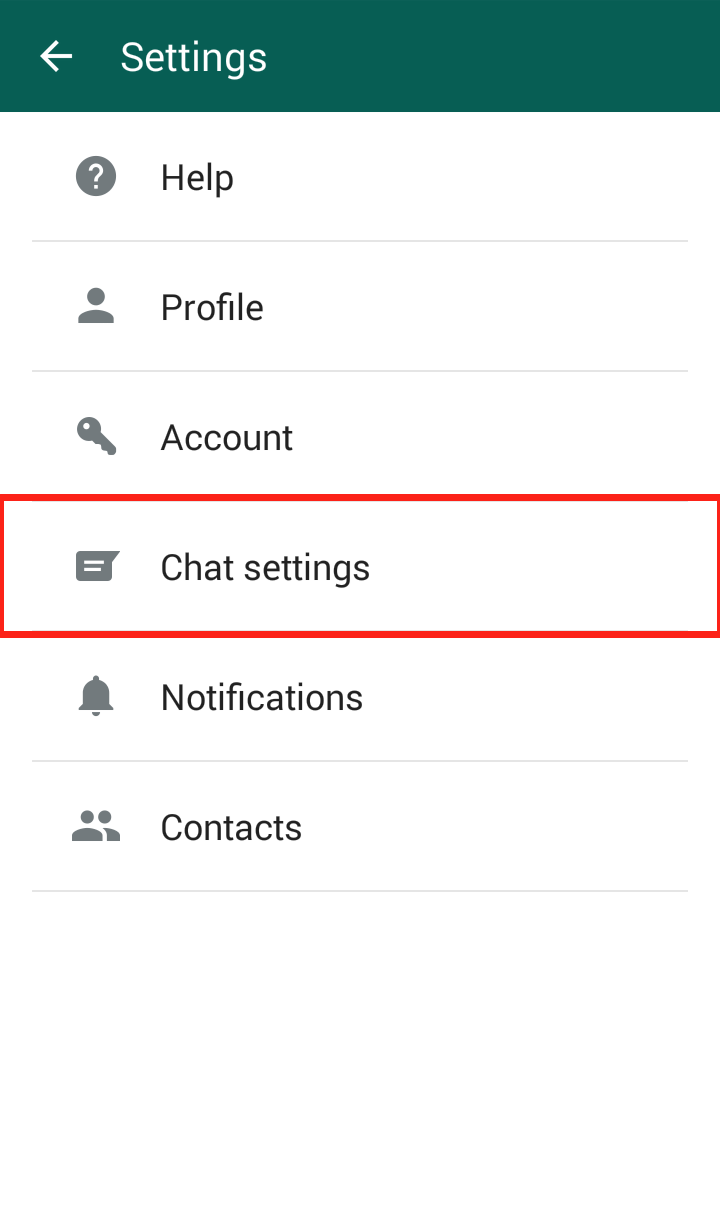
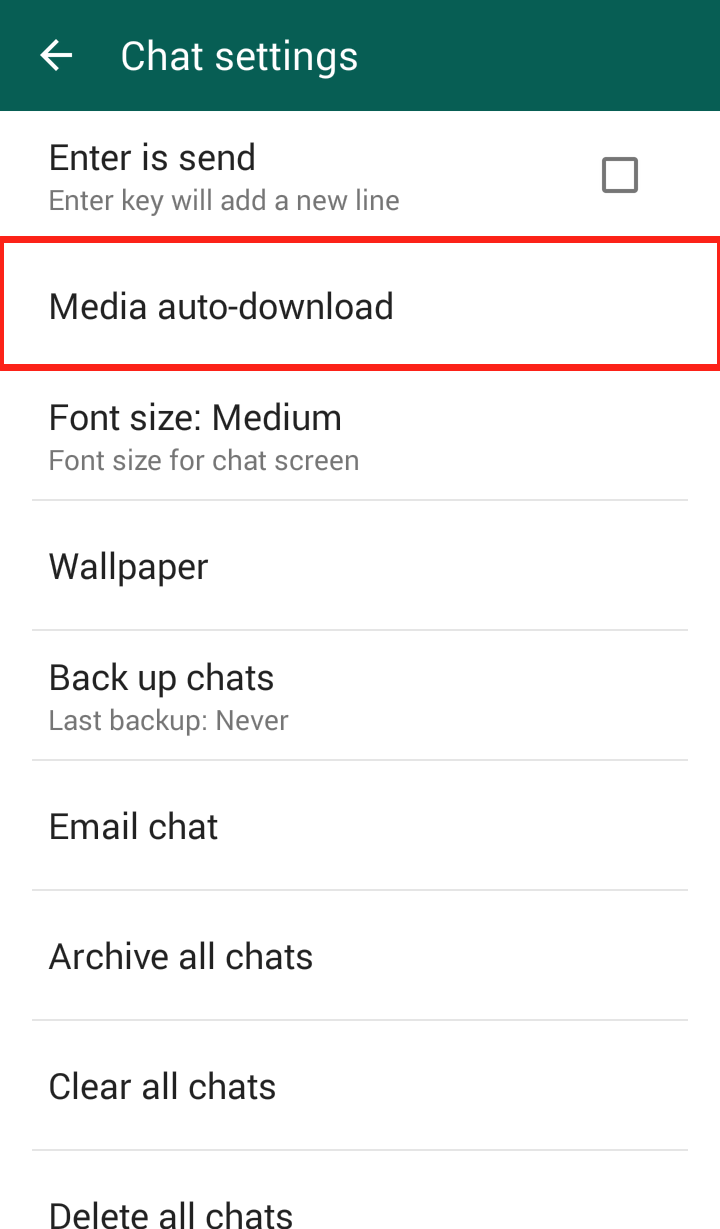
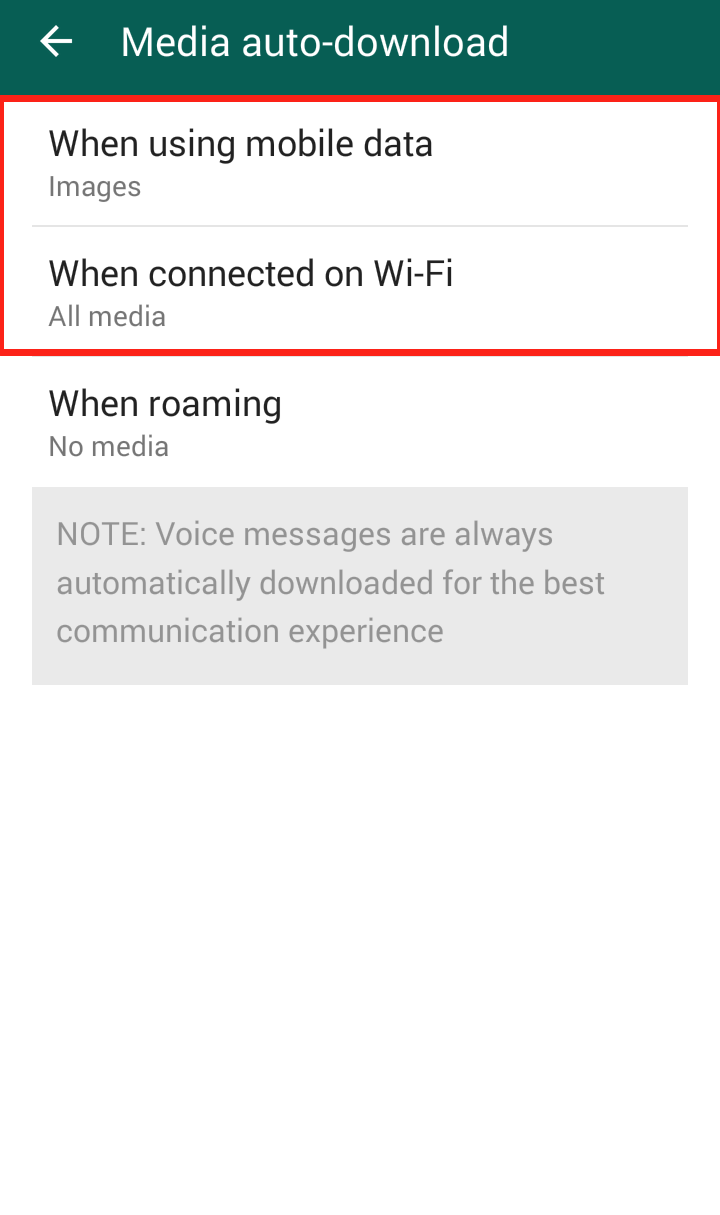
4. Turn off auto-connect. If you have your phone set to automatically detect and connect to available wireless networks, then turn it off. It’s much better to choose yourself. The new Avast W-Fi Finder can help you find secure Wi-Fi hotspots. Look for it to be released soon.
5. Avoid unencrypted Wi-Fi networks. Free Wi-Fi hotspots sure are nice, but they are not worth the risk to your personal data. They are unsecured and can give cybercrooks access to your internet-enabled devices. The safest way to use free Wi-Fi, even that supplied by your hotel, is to connect via a virtual private network, otherwise known as a VPN. The name sounds complicated, but with Avast SecureLine VPN, it is as easy as pushing a button.
6. Use smart passwords. Using a password like 1234 or password is not a smart thing to do at any time. But discovering that your account was hacked when you are traveling can ruin your trip. Plan ahead and manage your passwords in an intelligent way. There are plenty of memory tricks you can use to create unique passwords or you can let a password manager take care of the heavy lifting for you. Look for a new Avast password manager coming soon.
7. Think before you overshare. There are differing opinions about oversharing your location on social networks. Some say that broadcasting to the world that you are away invites a burglar into your home. Others say that broadcasting your whereabouts with regular updates is security in and of itself, because your friends and family know where you are in case something happens. And it could protect your contacts from the “I was arrested in Niagara Falls and need you to send bail money via Western Union” scam. Talk with your family and decide how you want to handle that.
8. Guard your devices. Thieves often target travelers. Don’t let yourself get so distracted that you lose track of your devices. Install Avast Anti-Theft before you leave. One of its useful features is called Geofencing. This allows you to set a perimeter, say around a table at an airport cafe, and if your mobile phone leaves that perimeter, an alarm will sound. If you discover any time that your smartphone or tablet has been stolen, Avast Anti-theft lets you control your cell phone remotely. You can locate and track your lost phone, remotely lock or wipe the memory, and even activate a customizable siren or alarm.
The best thing about all these tools is that they are free (or in the case of SecureLine, a free trial), so the next time you start packing for your business trip, make sure that your devices are ready to go too.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()