More easy things you can do to secure your smartphone and tablet.
On our blog last week, we shared the first 7 easy security measures to protect your Android devices and the data stored there. But we haven’t finished them. Let’s go a little further.
8. Keep an eye in your phone or, if you can, set Geofencing protection
Don’t put your phone down and go somewhere else. And if you’re having fun in a bar and drinking a beer with friends, have a lucid thought before starting: Turn the Avast Geofencing module on. It’s easy. Open Avast Premium Mobile Security > Anti-Theft > Advanced Settings > Geofencing.
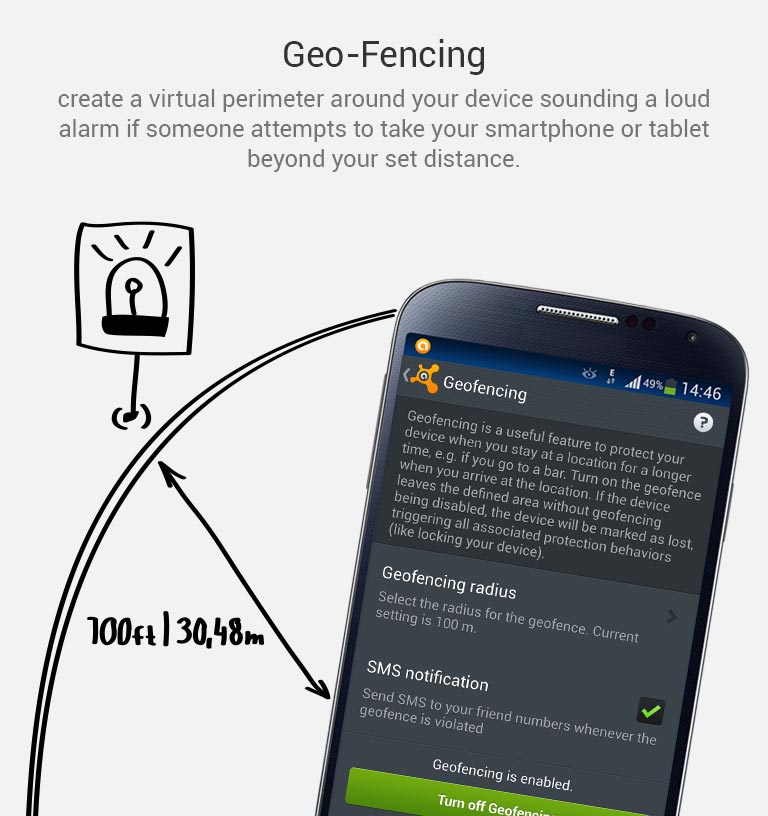
Set Avast Geofencing on your phone to protect it from theft while you are occupied.
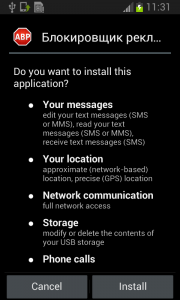
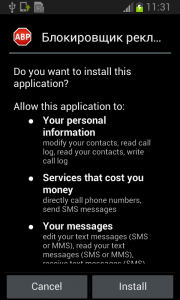
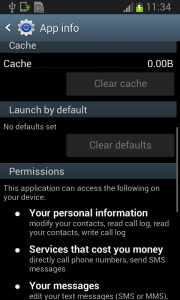
9. Be aware of what permissions apps require
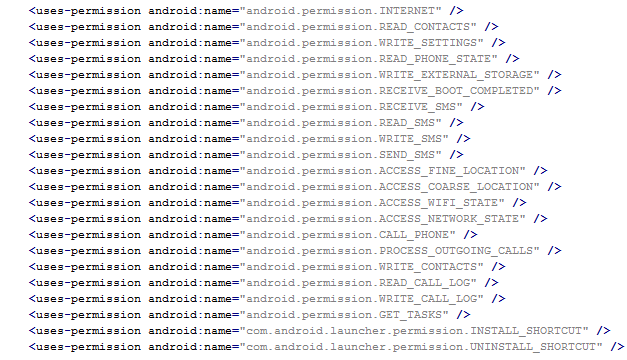
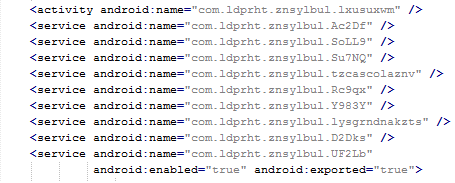
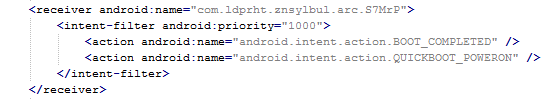
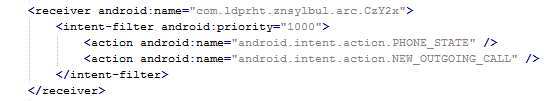
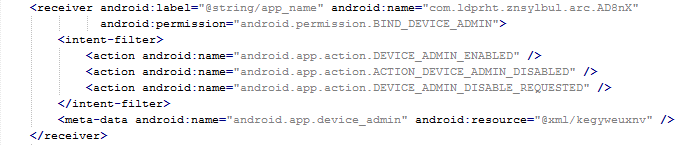
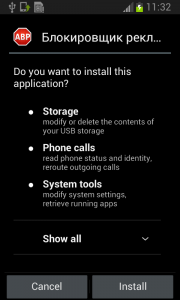
Why should a flashlight app need access to your contacts? Why would a calculator need access to your photos and videos? Shady apps will try to upload your address book and your location to advertising servers or could send premium SMS that will cost you money. You need to pay attention before installing or, at least, uninstall problematic apps. It’s not easy to find a way (if any) to manage permissions in a non-rooted Android phone.
We have written about this before as apps could abuse the permissions requests not only while installing but also on updating. Read more to learn and be cautious: Google Play Store changes opens door to cybercrooks.
10. Keep your device up-to-date
Google can release security updates using their services running in your devices. Developers can do the same via an app update. Allow updates to prevent vulnerabilities, the same as you do in your computer. But pay attention to any changes. See tip #9.
11. Encryption
You can encrypt your account, settings, apps and their data, media and other files. Android allows this in its Security settings. Without your lockscreen PIN, password or gesture, nobody will be able to decrypt your data. So, don’t forget your PIN! Nevertheless, this won’t encrypt the data sent or received by your phone. Read the next tip for that.
12. In open/public Wi-Fi, use a VPN to protect your communication
Cybercrooks can have access to all your data in a public, open or free Wi-Fi hotspot at the airport or in a cafe. Avast gives you the ability to protect all inbound and outbound data of your devices with a secure, encrypted and easy-to-use VPN called Avast SecureLine. Learn more about it here.
13. Set the extra features of Lollipop (Android 5)
If you’re with Android Lollipop (v5), you can set a user profile to allow multiple users of the same device. You can create a restricted user profile that will keep your apps from being messed with by your kids or your spouse.
You can also pin the screen and allow other users to only see that particular screen and nothing more. It will prevent your friends and coworkers from accidentally (or on purpose) looking into your device.
14. Backup. Backup. Backup.
Well, our last tip is common digital sense. If everything fails, have a Plan B, and C and D… With Avast Mobile Backup you can protect all your data: contacts, call logs, messages, all your media files (photos, musics and videos) and your apps (with their data if you’re rooted) in safe servers. If your device gets broken, lost or stolen, everything will be there, encrypted and safe, for you to restore to your new device.
Have you followed all our tips? Are you feeling safe? Do you have an extra protection or privacy tip? Please, leave a comment below.


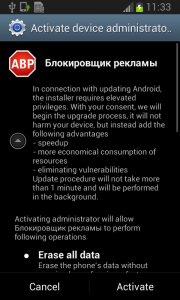
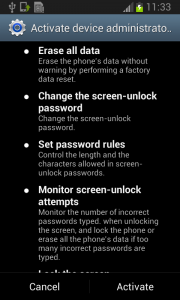
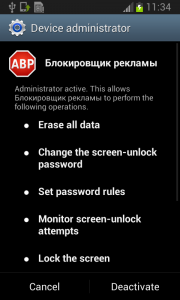
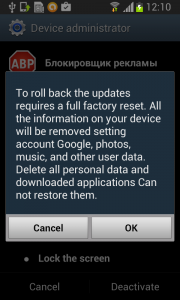
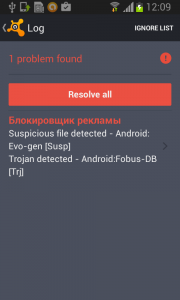
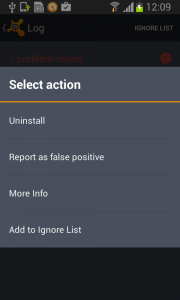
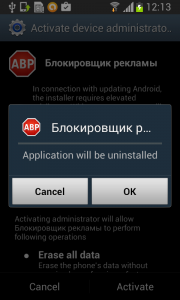
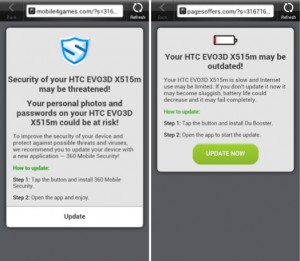 Each time you unlock your device an ad is presented to you, warning you about a problem, e.g. that your device is infected, out of date or full of porn. This, of course, is a complete lie. You are then asked to take action, however, if you approve you get re-directed to harmful threats on fake pages, like dubious app stores and apps that attempt to send premium SMS behind your back or to apps that simply collect too much of your data for comfort while offering you no additional value.
Each time you unlock your device an ad is presented to you, warning you about a problem, e.g. that your device is infected, out of date or full of porn. This, of course, is a complete lie. You are then asked to take action, however, if you approve you get re-directed to harmful threats on fake pages, like dubious app stores and apps that attempt to send premium SMS behind your back or to apps that simply collect too much of your data for comfort while offering you no additional value.