There is another same-origin policy bypass vulnerability in the Android browser in versions prior to 4.4 that allows an attacker to steal data from a user’s browser.
Tag Archives: Android
Flaw in Android Browser Allows Same Origin Policy Bypass
There’s a serious vulnerability in pre-4.4 versions of Android that allows an attacker to read the contents of other tabs in a browser when a user visits a page the attacker controls. The flaw is present in a huge percentage of the Android devices in use right now, and there’s now a Metasploit module available […]
AVG makes privacy crystal clear with Short Privacy Notice
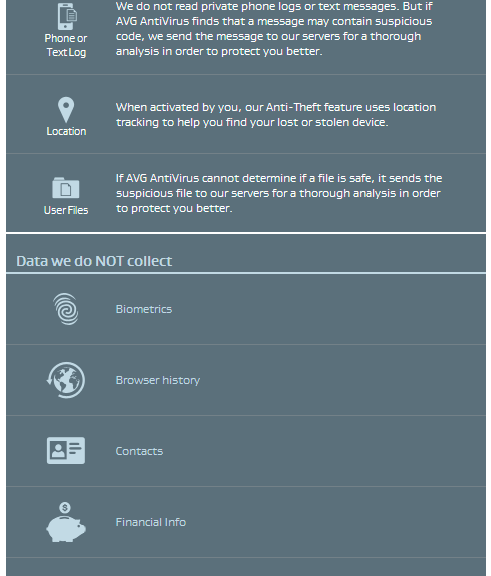
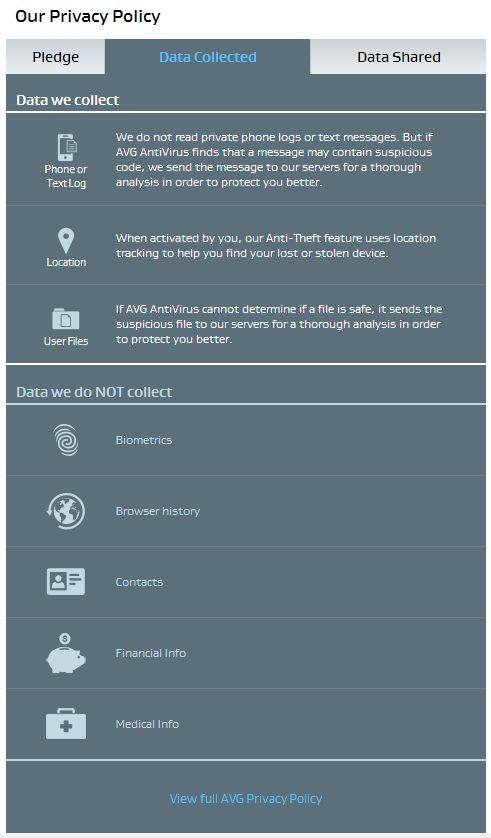
In our connected world, mobile technology is an integral part of daily living. Apps help us find the stores we are looking for, meet our friends at the right time and place, and keep us safe online. We trust these apps with our personal information in exchange for these services, which are often free. Sometimes we share sensitive information with the app in order to optimize that service. But do we ever think about what these apps do with the data they collect, and do we really know why they collect it?
At AVG, we believe that building trust in relationships is important. Transparency is a key element to build that trust which means you have to know what’s going with the data behind the app. The mobile environment is even more challenging because of the limited space and form factor. We’ve been innovating in this area to better show users what data is collected and how it is used. We’ve done this with initially with a Short Data Privacy Notice that tells our customers in a clear, straightforward, and transparent way what our apps collect and share in an easy to read form. Today I am delighted to tell you that the AVG Short Data Privacy Notice has been launched on our following apps: AVG AntiVirus FREE for Android, AVG Privacy Fix and AVG Cleaner for Android. Overtime we expect this approach will become the standard in mobile and desktop environments.
This simple-to-use feature is accessed from the corner menu of the app main screen. To ensure full transparency for all our customers, we still give quick and easy access to our full privacy policy notice at the bottom of each page of the AVG Short Data Privacy Notice.
In the video below, AVG’s Chief Legal Officer Harvey Anderson explains how to use the AVG Short Data Privacy Notice and what we disclose to you through it.
![]()
![]()
As Mobile Malware Hits the Million Samples Mark It Becomes More Devious than Ever Before
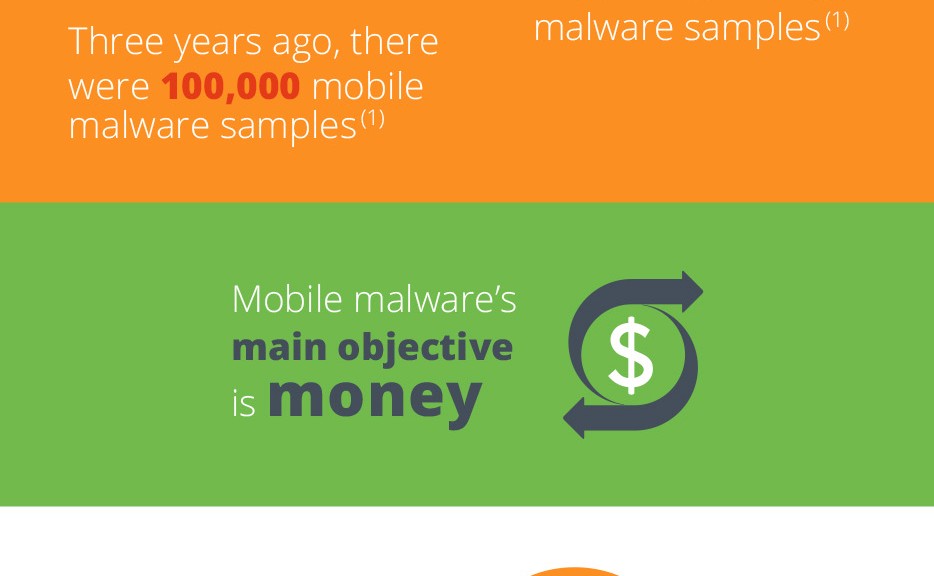
Mobile malware is growing exponentially. We now have more than 1 million malicious samples in our database, up from 100,000 in 2011. Still relatively young, most mobile malware has a pretty simple structure, yet it is designed to effectively steal people’s money. Newer mobile malware is, however, adapting and evolving, slowly embracing more deceitful and complex tactics to target users.
PC malware authors started in a garage, mobile malware authors in an office
Mobile malware is undergoing a similar development as PC malware did years ago with two significant differences: First, PC malware, in its early stages, was created by hobbyists and has only slowly evolved into a serious business within the last 10 years. Mobile malware, even with its simple structure, has been a serious business from the get-go. Smartphones and tablets are capable of gathering and storing more personalized data than PCs ever did – there is an abundance of valuable data to collect, including personal data and financial information. Thus, the focus of mobile malware has always been on monetization, meaning that even early mobile malware posed real-life threats to its victims, stealing money from them. Secondly, even though malware targeting smartphones and tablets is still young, it’s developing much faster than PC malware did in its initial years.
There are multiple entry points for mobile malware; apart from malicious apps placed in app stores and in-app ads linking to malicious content, malware authors also often take advantage of bugs in mobile operating systems, in popular apps or carrier billing structures. In 2013, around 60 to 70% of malware was tailored to send premium text messages behind users’ backs, a simple trick malware authors took advantage of to get into people’s wallets. The industry is catching up to malware and retaliating – carriers in the US and other countries have banned premium text messaging services. As the industry reacts, mobile malware authors start thinking of and using much more sophisticated and deceitful ways to get to people’s money.
The next generation of mobile malware
Elaborate malware, such as ransomware and spyware, is on the rise and is slowly taking control of mobile devices and the pool of potential victims can only get larger. Google now has more than 1 billion Android users. Formerly only known on the PC platform, a Cryptolocker-like ransomware has recently targeted Android devices for the first time, scaring users by holding their devices hostage, claiming to encrypt files until the user paid the ransom. Mobile spyware, on the other hand, is capable of tracking user location and a variety of other personal data, which can later be used to hack accounts or for identity theft.
We predict that with the emergence of new technologies, malware authors will find new ways of taking advantage of them. For example, as the use of new payment methods like Near Field Payment (NFC) increases, we expect hackers will change the way they go after money.
Users need to become aware of how valuable smartphones really are – not just the hardware, but the data it contains
Mobile threats are increasing – we expect them to reach the same magnitude as PC malware by 2018. However, out of the more than 1 billion smartphones that were shipped globally last year, only a small percentage are currently protected with antivirus software.
To make mobile devices safer and more secure, we need to collectively work together – the security industry, carriers, app store providers and consumers. At AVAST, we are constantly refining our tactics to detect mobile malware, to protect our users with our free and paid solutions. Actions like major carriers in the US, Brazil and the UK no longer billing customers for most forms of commercial Premium SMS messages, thus shutting an important door for malware creators, are a great initiative – and we hope carriers in other countries will follow this step, soon. Also, stricter security rules for apps on Google Play and other app stores could help make some types of malware extinct.
In the end, it’s also up to users to protect their devices and data with security solutions. People need to understand that there are new threats being built to target their mobile devices. Phones and tablets contain people’s personal treasures, in the form of data, whether that be personal information about loved ones or bank details – all of which is interesting for cybercriminals. Therefore, it is essential that people care for their smartphones and tablets in the same way as they protect their PC, the majority of which has antivirus installed.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.
Â
Chat apps leak: Billion app users from OKCupid to Grindr at risk
Nearly a billion users of a dozen chat apps for Android including popular apps such as Instagram, Oovoo, OKCupid and Grindr could be at risk from eavesdroppers and snoopers after University of New Haven researchers found serious data leakage problems.
With many of the most popular chat apps on Android affected, tech news site CNET calculates that nearly a billion (968 million) users could be putting highly private data in the hands of apps that transmit and store it unencrypted.
Many of the Android apps (the researchers focused on Android rather than iOS, although there is no evidence the iOS apps behave differently), send text wirelessly unencrypted, and store images on servers for weeks without encryption or authentication.
Chat apps leak: 12 Android apps leak text and images
According to CNET’s report, the following apps sent text, images, location maps and video unencrypted – Instagram, OKCupid, OoVoo, Tango, Kik, Nimbuzz, MeetMe, MessageMe, TextMe, Grindr, HeyWire, Hike and TextPlus.
The site notes that not every app sent every form of media unencrypted, but said that all sent at least some forms, from pictures to text in unencrypted forms.
Others stored media such as images on servers unencrypted and without any form of authentication “for weeksâ€.
‘Sniffer’ software reveals leaks
The researchers used PC ‘sniffer’ software such as Wireshark and Network Miner to monitor the data transmitted by the apps, and found images and text transmitted and stored unencrypted – and potentially at risk from snoopers.
In the series of YouTube videos, one researcher says, “We recorded network traffic in Wireshark, to see if files remained on the server. For Instagram, we found an image stored in their servers, unencrypted and without authentication.â€
“Next, we opened up Oovoo and sent the keyword “Sparklehorse,†and it was picked up in Network Miner. Next we had Oovoo send an image. It was also picked up in Network Miner.â€
CNET reports that few of the apps had replied to requests for further information, but that Grindr had said, “We monitor and review all reports of security issues regularly. As such, we continue to evaluate and make ongoing changes as necessary to protect our users.”
The post Chat apps leak: Billion app users from OKCupid to Grindr at risk appeared first on We Live Security.
![]()
avast! Mobile Security quiz winners!
AVAST recently surpassed a major milestone:Â More than 100 million downloads of avast! Mobile Security & Antivirus for Android.
To celebrate the phenomenal popularity of avast! Mobile Security, we organized a test-your-knowledge quiz on our popular avast! Facebook page. Our goal was not only to test your knowledge and award participants, but also bring your attention to and educate users about mobile security. Our knowledge quiz wasn’t easy, but we made sure that you received a hint to answer the questions correctly. Thousands of you submitted answers to our 5 questions as well as shared your thoughts about what the greatest threat to mobile security is today.
Here are the quiz questions and answers:
- How many Smartphones are lost or stolen every minute of every day? The correct answer was 100! The answer was found in this blog post.
- avast! Anti-theft helps you locate your lost or stolen mobile device. There are various methods used. Which of following is NOT one of the methods? The correct answer was ‘Communicate via your GPS device.’ The hint was hidden in this blog post.
- Based on users’ answers in an AVAST survey, which group of people are more vulnerable to mobile malware? The correct answer was ‘Males.’ The answer was found in this infographic.
- When was the first version of avast! Mobile Security released? The correct answer was ‘December 2011.’ The hint was hidden in this YouTube video.
- The AVAST team demonstrated our Mobile Security product at one of the largest mobile conferences in the world. In which great city did it take place? The correct answer was ‘Barcelona.’ The hint was hidden in the following blog post.
Here are the results:
- 2,400 participants answered all the questions correctly
- 1,900 participants answered four questions correctly
- 1,400 participants answered three questions correctly
- 3,300 participants answered one or two questions correctly
We promised to give away 1,000 Premium licenses to participants. However, we changed our mind. We decided that we want to protect your Android phone and tablets, so we well be awarding everyone who answered 3 and more answers correctly with a  free license for the most trusted Android security product in the world! 
Now check your mailbox and search for the email from us. It will contain a special voucher with instructions on how to activate your Premium license. It might end up in the Junk/Spam folder, so please make sure you double check it too. In the following blog post we will announce winners of our VIP #AVASTteddy and the lifetime license, so please stay tuned!
For those who didn’t succeed this time, we have also something.  Install avast! Mobile Security and Antivirus for FREE from the Google Play store, https://play.google.com/store/apps/details?id=com.avast.android.mobilesecurity
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.
Android security mystery – ‘fake’ cellphone towers found in U.S.
[There have been many comments to this story from people who are assuming that these ‘towers’ are physical installations. There’s no reason to assume this is the case: it’s far likelier that they are mobile installations of the kind used not only by law enforcement and government agencies, but also by scammers and other criminals. (David Harley)]
Seventeen mysterious cellphone towers have been found in America which look like ordinary towers, and can only be identified by a heavily customized handset built for Android security – but have a much more malicious purpose, according to Popular Science.
The fake ‘towers’ – computers which wirelessly attack cellphones via the “baseband” chips built to allow them to communicate with their networks, can eavesdrop and even install spyware, ESD claims. They are a known technology – but the surprise is that they are in active use.
The towers were found by users of the CryptoPhone 500, one of several ultra-secure handsets that have come to market in the last couple of years, after an executive noticed his handset was “leaking” data regularly.
Its American manufacturer boasts that the handset has a “hardened†version of Android which removes 468 vulnerabilities from the OS.
Android Security:Â Towers throughout the US
Despite its secure OS, Les Goldsmith of the handset’s US manufacturer ESD found that his personal Android security handset’s firewall showed signs of attack “80 to 90†times per hour.
The leaks were traced to the mysterious towers. Despite having some of the functions of normal cellphone towers, Goldsmith says their function is rather different. He describes them as “interceptors†and says that various models can eavesdrop and even push spyware to devices. Normal cellphones cannot detect them – only specialized hardware such as ESD’s Android security handsets.
Who created the towers and maintains them is unknown, Goldsmith says.
Origin of towers ‘unknown’
“Interceptor use in the U.S. is much higher than people had anticipated,†Goldsmith says.  “One of our customers took a road trip from Florida to North Carolina and he found eight different interceptors on that trip.  We even found one at South Point Casino in Las Vegas.†[Editor’s note: Goldsmith has asked us to stress that the tower was actually in the vicinity of the casino, not within the casino itself.]
Their existence can only be seen on specialized devices, such as the custom Android security OS used by Cryptophone, which includes various security features – including “baseband attack detection.”
The handset, based on a Samsung Galaxy SIII, is described as offering, a “Hardened Android operating system” offering extra security. “Baseband firewall protects against over-the-air attacks with constant monitoring of baseband processor activity, baseband attack detection, and automated initiation of countermeasures”, claims the site.
“What we find suspicious is that a lot of these interceptors are right on top of U.S. military bases.” says Goldsmith.  “Whose interceptor is it?  Who are they, that’s listening to calls around military bases? The point is: we don’t really know whose they are.â€
Baseband attacks are considered extremely difficult – the details of the chips are closely guarded. “Interceptors” are costly devices – and hacking baseband chips is thought to be technically advanced beyond the reach of “ordinary†hackers, ESD says. The devices vary in form, and are sold to government agencies and others, but are computers with specialized software designed to defeat the encryption of cellphone networks. The towers target the “Baseband†operating system of cellphones – a secondary OS which sits “between†iOS or Android, for instance, and the cellular network.
Goldsmith says that the devices cost “less than $100,000†and does not mention what level or type of device his team has detected. Most are still out of reach of average hackers, although freely advertised. One model is the VME Dominator, which is described as, “a real time GSM A5.1 cell phone interceptor. It cannot be detected. It allows interception of voice and text. It also allows voice manipulation, up or down channel blocking, text intercept and modification, calling & sending text on behalf of the user, and directional finding of a user during random monitoring of calls.â€
What has come as a surprise is how many “interceptors” are in active use in the U.S., and that their purpose remains mysterious.
The post Android security mystery – ‘fake’ cellphone towers found in U.S. appeared first on We Live Security.
![]()
Win a free avast! Mobile Premium license
AVAST is celebrating 100 million downloads of avast! Mobile Security & Antivirus for Android.
We want to protect your Android phone and tablets, so we’re giving you the chance to win a free license for the most trusted Android security product in the world!
How much do you know about your phone’s security?
Do you know all the ways to use avast! Mobile Security’s anti-theft feature to track your phone?
Do you know who is more at risk for getting malware on their mobile device?
Do you know how many phones are stolen every minute of every day?
Take the avast! Mobile Security quiz and find out! Answer all 5 questions correctly (don’t worry, we’ll give you hints) and you’ll be in the running to win a free 1-year license for avast! Mobile Premium! One lucky winner will win LIFETIME protection, and 10 lucky winners will receive a rare avast! teddy bear.
Here’s what to do:
- Become an AVAST fan on Facebook
- Enter the quiz and answer 5 questions correctly
- Write what you think is the most serious threat to your mobile security
- Share the quiz with your friends
Take the avast! Mobile Security quiz now!
Make sure all the Android’s in your life have protection. Install avast! Mobile Security and Antivirus from the Google Play store, https://play.google.com/store/apps/details?id=com.avast.android.mobilesecurity
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.