Ahoy, me hearties!
 at there is a Pirate language and that AVAST is one of the key words of the language? You can even set up your avast! Antivirus in Pirate language and change your sound notifications to pirate language! How we are participating?
at there is a Pirate language and that AVAST is one of the key words of the language? You can even set up your avast! Antivirus in Pirate language and change your sound notifications to pirate language! How we are participating?Th’ wenches ‘o Social Media ‘n HR, along wit’ a few scurvy dogs, have planned a right jolly day ‘o piratey hijinks fer th AVAST pirates. Every hour when th’ bell chimes, a new task is assigned. The treasure hunting has finished and prizes given away.
Th’ best scurvy pirates come from AVAST!
Our team received seven tasks in different categories to challenge geeky and creative minds. The response was great and we are sharing with you only a fraction of what has been happening here. ![]()
Jolly good idea ya social media ‘n HRÂ wenches, garrr!
But run out of rum and you walk the plank! ~ Jan, accounting department
Avast who is coming next
you will need your pirate vest.
Hide your hook and say ahoy
to not scare this little boy
~Pavla  Marketing
Ya lazy bums, hurry and up,
avast! they come, our blood thirsty foes,
let’s cut their throats with our smart codes
ahoy! we’ll grab, the scavengers boats!One more yer’old powder monkeys!
The floor is dirty and supplies are rotten,
but we keep on sailing, we won’t be forgotten,
we rockin’n’surfin’n’fixin the mast,
we are the sailors working for Avast! ~ Tomas, BI
Advance, ye mates! Cross your lances full before me. Let me touch the axis and drink thy rum, ye harpooneers! ~ Andre e-commerce
A pirate ship named Avast,
Was sailing accross the sea,
The sailors organized a party and had a blast,
But the Captain was pissed as his glass was empty,
Where did all the rum go?
Where did all the rum go?
Arrrgh, the Captain was complaining over and over,
They will all be hangover! ~ Sarah e-commerce
Ahoj sailors developers!
I see some red,
Better when green,
Oops it’s again red,
Now code is clean,
And #TDD is great!
Code is poetry when #coding at Avast ~ Jonas BI
Malware are #FF0000
AVAST is the #FF9900
All my rums are belong to you!
ARrrrr!
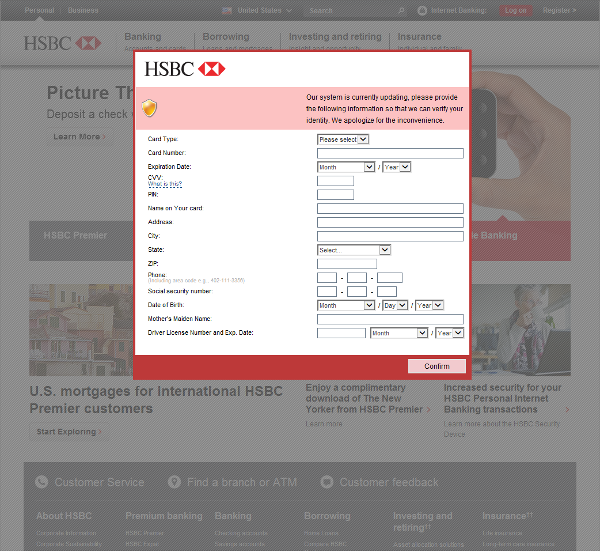
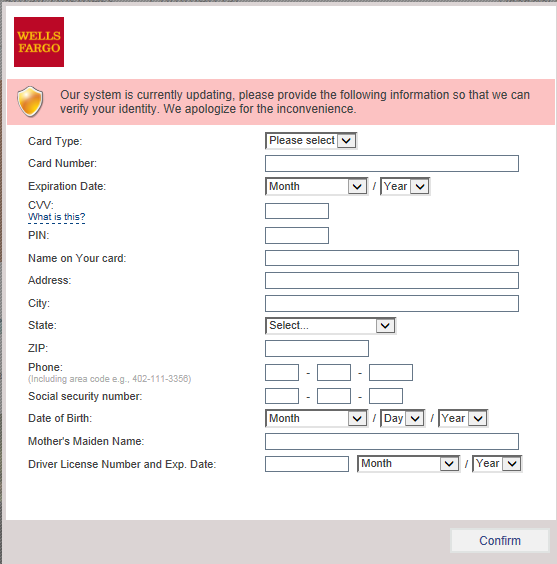
01000001 01010110 01000001 01010011 01010100 ~ Nikolas, virus lab
Avast! Bloody Avast! Hey,
Pirates gonna crunch the bay.
Jump, shot & sink the boats.
Down the sea of rum & dry throats. ~ Pavel BI
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.