The danger of public Wi-Fi spots has been exposed by a seven year old girl following a short video tutorial, reports ITV.
The post Public Wi-Fi hacked by seven year old in 10 minutes appeared first on We Live Security.
The danger of public Wi-Fi spots has been exposed by a seven year old girl following a short video tutorial, reports ITV.
The post Public Wi-Fi hacked by seven year old in 10 minutes appeared first on We Live Security.
President Barack Obama intends to persuade Congress to increase the sentence for hackers, as well as widen the definition of what hacking means, according to Ars Technica.
The post Obama to call for longer hacking prison sentences with revised Computer Fraud and Abuse Act appeared first on We Live Security.
News broke earlier in January that Facebook has acquired Wit.ai, an 18 month old startup that specializes in voice recognition technology. At first, this might seem like a strange move but upon closer inspection, the rationale is clear.
Millions of users are turning to mobile as their preferred platform, where typing long messages and interacting with friends is far more challenging than on a PC keyboard.
It’s clear that companies like Facebook face a challenge to make mobile interaction easier and more engaging.
Using Wit.ai’s expertise, Facebook can build a mobile-first platform with a voice activated interface and text-to-speech messaging some obvious steps.
The Facebook acquisition highlights the excitement and potential behind voice recognition technology. We are potentially witnessing a fundamental shift in the way we interact with our technology forever.
As we start integrating voice activated functionality into new smart devices and services we use on a daily basis, my primary concern isn’t one of convenience but of security.
As I wrote in this blog in September 2014, there is much work to be done in securing our digital devices from voice commands.
Most voice recognition technologies scan commands for meaning and then execute them. I believe there is a need for an additional step, one of authentication.
Does the person issuing the command have the authority to do so? When I ask the device to execute a command, does it validate that it is really me and not someone else?
As I demonstrate in the below video, it is quite simple to have a device act upon a voice command issued by a synthetic voice or by a 3rd party that has an access to the device – even remotely:
As Facebook and other leading companies add more voice activation technologies to their roadmap, it’s important to realize that we are also increasing the number of services and devices that are potentially vulnerable to voice attacks. So considering this, , let’s build it with safety in mind.
The Anonymous hacking collective has “declared war” against the terrorists said to be responsible for the shootings of staff at France’s satyrical Charlie Hebdo magazine, reports The Telegraph.
The post Anonymous hackers ‘declare war’ on al Qaeda and Islamic State appeared first on We Live Security.
Are hacking victims “hacking back”? That question was recently posed in headlines like this one from Bloomberg: FBI Investigating Whether Companies Are Engaged in Revenge Hacking. The Marketplace reporter, Ben Johnson, speculated that 2015 might be the year of “hacking back” when he asked me about revenge hacking. As I told Ben, there are several good
The post 5 reasons not to “hack back” appeared first on We Live Security.
The holiday season is a time of relaxation with family and friends. However, the news doesn’t stop and over while on the road with my family I read a story that seemed to take a sensationalist and quite negative angle.
The story titled “Politician’s fingerprint ‘cloned from photos’ by hacker” was posted on the BBC News website. It explains how, in October 2014, a hacker took photos of a politician’s hands at a news conference and managed to replicate their fingerprint from the photos. The ‘hacker’ quips that after this discovery, all politicians will most likely start wearing gloves.
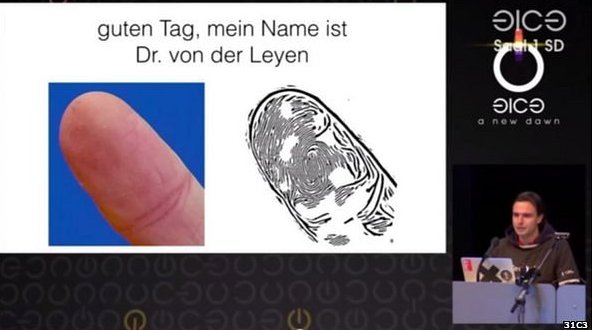
In the article, reference is made to the fact that both Apple and Samsung devices use biometric fingerprint technology to secure their mobile devices. It seems that this is meant to scare us into thinking the technology is not safe and that we cannot rely on our fingerprints to secure us.
We need to start the year with some perspective on this story. The process of recreating someone’s fingerprint this way is both difficult and time consuming and therefore unlikely to be an issue for the mass consumer audience.
It goes without saying that we have all seen locks being picked in movies yet continue to lock our doors with similar keys. Nobody is writing articles about how easy it would be to take a picture of your keys and accurately reproduce them.
I believe we should be celebrating that authentication mechanisms once only used by large companies and government agencies have found their way into our everyday lives.
If you look back a few years, only a few people used PIN numbers on their phones. If the introduction of swipe codes and biometric security increases the number of people with locked phones, isn’t that a good thing? It shows that more consumers than ever are protecting their devices in some way to stop people stealing their information.
I do of course understand that research into weaknesses in security such as this should be carried out and exposed so that better technologies can be developed.
But my final thought is to encourage people to use security on their phones rather than trying undermine the systems that might well protect them.
So how can you keep your mobile device safe? Here are some tips from AVG Academy on securing your Android mobile:
A hacking group has ‘mistakenly taken down’ a local bus website under the impression that it is a far more significant target, The Guardian reports.
The post Hackers ‘mistakenly’ take down local bus schedule website appeared first on We Live Security.
Realtime call-monitoring and GPS tracking of partners by domestic abusers is on the rise, both via dedicated electronic listening devices or using sophisticated spyware software.
The post Spyware abuse – partner tracking reaching “epidemic proportions” appeared first on We Live Security.
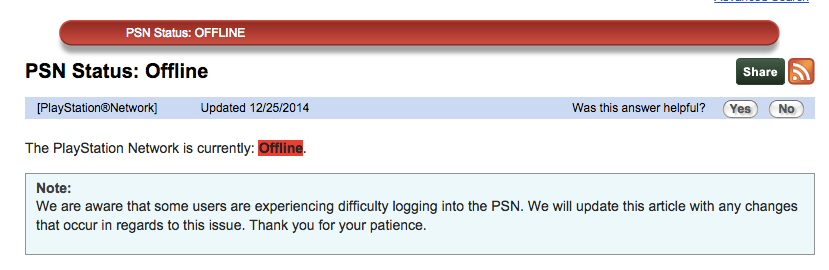 Earlier this month, as the Sony Entertainment breach was making headlines, Sony’s PlayStation Network (PSN) was knocked offline due to an alleged hacking attack. On Christmas morning, just as kids everywhere were unwrapping their new PlayStation and Xboxes, the PSN and Microsoft’s Xbox Live network were both disrupted leading to speculation that they were once again hacked. A group calling themselves Lizard Squad claiming responsibility for the attacks via Twitter.
Earlier this month, as the Sony Entertainment breach was making headlines, Sony’s PlayStation Network (PSN) was knocked offline due to an alleged hacking attack. On Christmas morning, just as kids everywhere were unwrapping their new PlayStation and Xboxes, the PSN and Microsoft’s Xbox Live network were both disrupted leading to speculation that they were once again hacked. A group calling themselves Lizard Squad claiming responsibility for the attacks via Twitter.
As of now, PlayStation is still offline and PSN is directing users to their @AskPlayStation Twitter account for updates.
Please follow @AskPlayStation to get the latest updates as we work to restore full network functionality.
— Ask PlayStation (@AskPlayStation) December 26, 2014
Xbox Live Status reports that its core services are running, but there is limited access to apps for IGN, Maxim, and MLG.tv.
Related article: Sony PlayStation Network down due to hacker attack
Malicious DDoS attack blamed for taking major gaming networks Xbox Live and Playstation Network offline for Christmas…
The post Playstation Network and Xbox Live offline for Xmas appeared first on We Live Security.