Sometimes, Google Chrome tells us to distrust a website and warns us that that site can be dangerous. But instead of listening to it, we ignore it. We are so obsessed on quickly reaching the neck click, that we don’t even read the message.
A study published by Google’s Chrome team stated that only one in four users pays attention to the SSL security certificate warnings and takes their advice. That’s why they decided to redesign them, reducing and simplifying the text, and adding more graphic information. Hoping, this will make users read the information before taking risks.
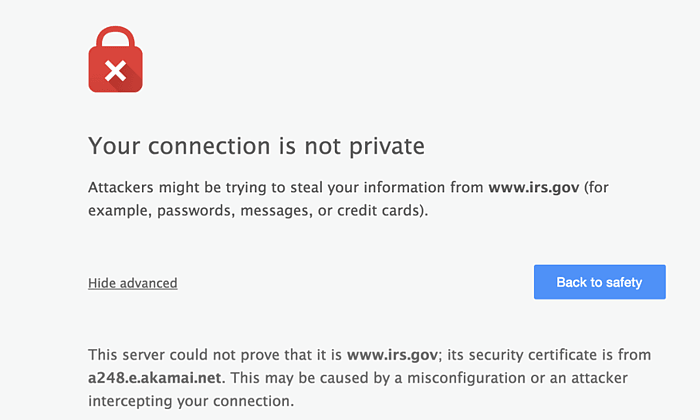
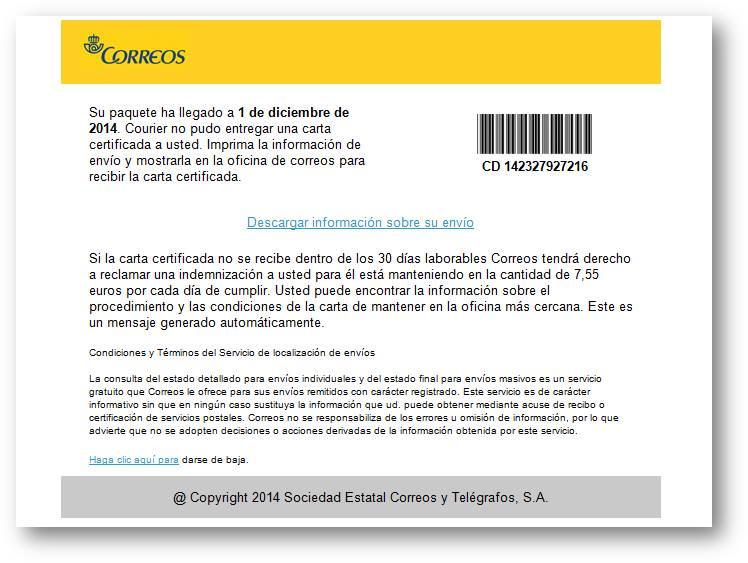
But what does SSL stands for? This acronym refers to “Security Sockets Layer”, a secure connection protocol that enables you to browse the Internet with maximum guarantees. When a browser visits a webpage, it checks the site’s identity and its SSL. It informs you when something goes wrong, the site’s certificate is not from a trusted organization, it has expired, or the connection between the browser and the website is not secure. What’s the objective? The main objective is to prevent the users, letting them know that the site could threaten their safety. For example, if you were making a purchase, someone could steal your credit card information.
Many users may not take into account their browser’s opinion. If their browser simply tells them that the SSL is out of date, likely they won’t understand what this means or the risk this entails. Nevertheless, if they, like Chrome already does, point out that an attacker could steal your information, you would be more vigilant.
“Even though we prefer that the user decides things, in some cases, it simply doesn’t make sense. It’s simply impossible to explain something as complex as cryptography to many users,” says Andreas Gal, chief technology officer at Mozilla. Gal refers in this way to the difficulty of transferring and translating information about privacy to those users who should worry about it.
Lujo Bauer, Associate Research Professor CyLab at Carnegie Mellon University, published a paper in which recommended that web browsers present the information in a comprehensible and concise way, and offer the top options to users. This is why Chrome decided to reduce the text and make the warning signal more visible, even highlighting in blue the “Go Back” option and diminishing the “Advanced Options” that allows access to the not safe site.
Would these measures be useful? Or, are we so lazy that we will continue to ignore the information about our own security? The underlying problem is still there: we stop paying attention after viewing new sites several times. According to a research by Brigham Young University, in which after analyzing a variety of 40 different warnings – like anti-virus, software updates, or SSL– the results showed that after seeing them more than once, we stop noticing them.

Communicating security problems is complicated if we don’t read the warnings, and the only thing we want is to keep on browsing without being disturbed. “The immediate cost of heeding the warning is high, because I will not be able to achieve my immediate goal, which is to reach the site and complete the bill payment or the status update that I had in mind,” says Raluca Budiu, senior researcher at usability consulting firm Nielsen Norman Group.
Can they steal our information if we dismiss the warnings? The answer is yes.
Do we have a lack of education about Internet? What else can browsers do to draw our attention in order to stop us from entering untrusted sites? Should they block the accss? Or, it is better that they keep letting us choose? You can reflect on it, or look up your browsers security options, so next time it warns you not to enter a site, you’ll pay more attention.
The post Browsers security: Why do we ignore their warnings? appeared first on MediaCenter Panda Security.