What inspires our innovation most is our customers – and finding solutions to better protect them, their personal data and their devices. In order to do this, we are constantly tracking new security threats in today’s ever-changing digital world.
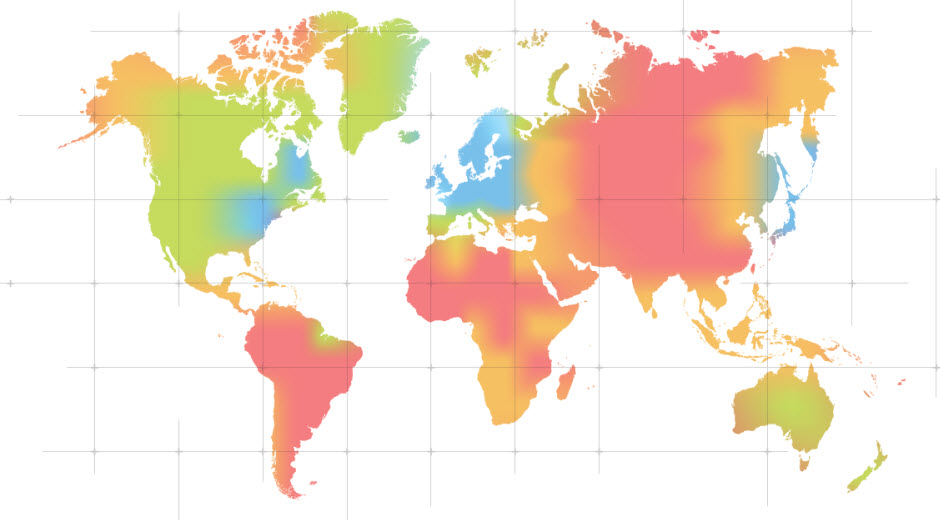
As a starting point for the day, we showed a Live Global Threat Map. This dynamic map provides a snapshot of virus/malware activity we are tracking real-time on PCs and mobile devices all around the world. On our map, you can zoom in and actually see the number of infections in each country over a period of time. With 188 million active users, 90 million of which are mobile, we have a pretty good pulse on the threats around the world.
Most of our demos for the day were focused on the new generation of attacks uniquely focused on mobile functionality. While the first generation of mobile attacks were primarily using vectors and methods used in the PC world, now we are starting to see the second generation mobile attacks.
These new attacks include the use of voice, social engineering, rough access points and exploitation of various vulnerabilities in apps.
Here are a few of the mobile threats we demoed:
Voice Activation
Voice activated software is a standard feature on smartphones and is also appearing in smart TVs and other Internet-connected devices. It also, unfortunately, can be used maliciously. Did you know some applications can respond to voice, even when a phone is locked? We demonstrated how the mobile operating system will respond to a synthetic voice and allow a malicious app to bypass the limitations of a locked device or permissions, allowing it to call a phone number, send mail and other malicious actions. The flaw is very simple and it impacts a broad range of products utilizing voice activation technologies; they simply do not authenticate the source of the voice.
App Vulnerabilities
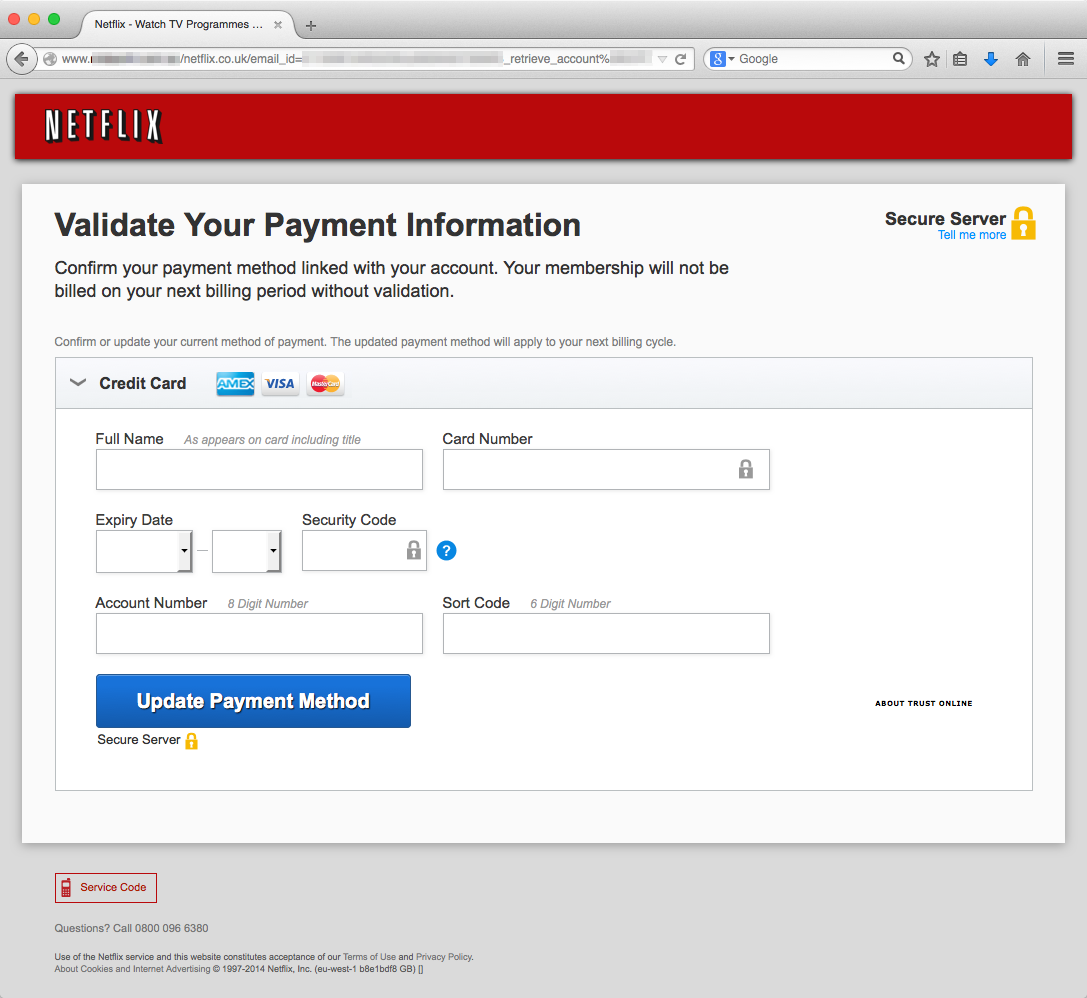
In the PC world, software can be distributed and installed on the PC from any source. As a result we are seeing many malicious programs impacting this platform. The mobile world has learned this lesson and is centralizing app distribution via app stores. This approach improves control and scan the apps for malicious intent. However, the fact that an app is not malicious doesn’t mean it isn’t vulnerable. We showed an app available on an app store that was downloaded over 5 million times, but is vulnerable. Our demo showed how easy it would be to exploit the vulnerability and take over the mobile device from a remote – allowing streaming video and voice from the device to the hacker.
iOS Threats
All mobile platforms share security issues and we at AVG always keep an eye on emerging threats in all mobile platforms. For example, we demoed the recent Apple iOS “Masque Attack” technique. This technique allows an attacker to substitute malware for a legitimate iOS application under a limited set of circumstances. It works by luring users to install an application from a source other than the iOS app store or their organization’s provisioning system, such as delivered through a phishing link. This technique takes advantage of a security weakness that allows an untrusted application with the same “bundle identifier” as that of a legitimate application to replace the legitimate application on an affected device, while keeping all of the user’s data. This vulnerability exists because iOS does not enforce matching certificates for applications with the same bundle identifier. Apple’s own iOS platform apps, such as Mobile Safari, are not vulnerable. In our demo we created a malicious iOS application named ‘FakeBook’ that steals all the user’s data that the legitimate Facebook application have access to.
Visual ID Hijacks
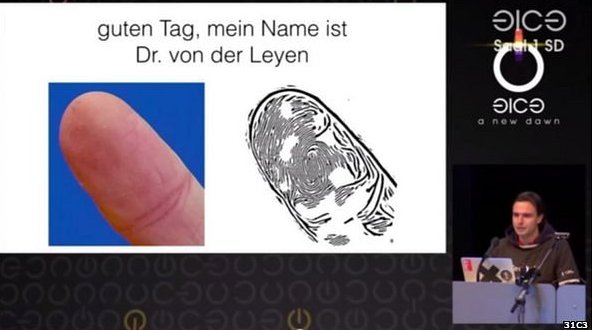
Malicious apps that assume visual identification of a “real” well-known brand (think about banking and social media applications) can replace a legitimate app and wreak havoc. Take Droidphish, a new attack vector we discovered, for example. If a hacker registers with a specific URL, when a link within the real app or even on a web page is clicked, the malicious app can assume the identity of the legitimate application. In our demo, the attacker gains complete control over your device, your email and data, even to the point of taking a photo of you using the device.
Texting Hijinks
We’ve all been warned to beware of URLs sent via a text (SMS) message. When clicked, they can redirect you to a malicious website. In our demo we showed media that a malicious app can even read and reply to incoming text messages without any visual appearance and without the owner of the device being aware that something is going on!
Cross-Platform Infection
Another demo scenario involved an app that creates a malicious PDF that is later automatically synced—via a cloud-based, file sharing service like DropBox – between a PC and mobile device, infecting the other device without even knowing. Imagine if the PDF had an “interesting” name that may trick the user into opening it.
Wi-Fi Hacks
We are constantly warned that public open Wi-Fi is unsafe, but there are millions of public Wi-Fi hot spots open and that means a lot of security risks ahead. Here are three scenarios we demonstrated on public Wi-Fi:
- Sniffing – Via free Wi-Fi, anyone sitting next to you in a coffee shop could be looking at the traffic you are sending if your data is unencrypted, including your chats, messages, emails etc.
- Spoofing – You connect to a malicious hotspot thinking it is legitimate- i.e. it could be named for a well-known coffee shop. (A colleague in Amsterdam ran an experiment and 60 people connected to his network in less than an hour!)
- Tracking- Walk into a retail store and SSID info allows tracking of your location. In some cases, a trusted retailer may be seeking to personalize your experience when you walk into a department. But in other cases, the tracking could be for nefarious purposes.
For these very scenarios, our Innovations Labs team created AVG Wi-Fi Assistant to smartly turn your Wi-Fi on/off along with a secure Virtual Private Network (VPN) service – so that no one can track you through Wi-Fi, or look at your data being transmitted. Additionally, AVG Wi-Fi Assistant also offers substantial battery life improvements.
Finally, we also demoed some current innovative mobile security products that help people protect themselves: AVG Zen and new apps from Location Labs, a new AVG company.
This was our first Experiential Lab day and we look forward to hosting many more in the future!