If you’re a regular online shopper like me, you’re sure to be familiar with your credit card security code – otherwise known as the card verification value (or CVV).
If not, you can find the 3-4 digit code on the back of your VISA/MasterCard (the final 3 digits of the number printed on the signature strip) or on the front of your Amex card (the separate 4 digit code above the card number).
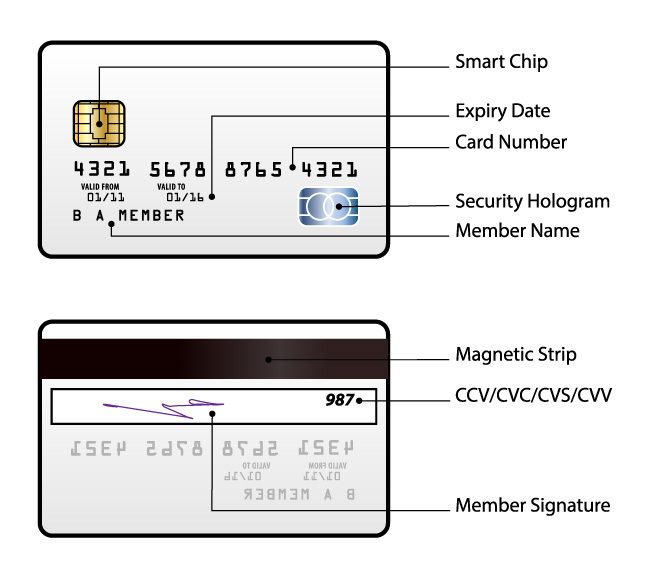
The intended purpose of the CVV is to provide added security when making purchases over the internet – it helps to verify that you’re in possession of the card, as the code shouldn’t be known to anyone other than you as the card holder. So it’s essentially a way of counteracting credit card fraud.
Is it safe to give out your CVV?
For online shopping, the answer is generally yes – it’s just simply a good idea to stick with well-known, reputable companies that you trust. You’ll find that most online retailers nowadays do require a CVV for purchases, which is encouraging because it means that they’re actively trying to prevent fraudulent transactions occurring on their site.
You may also be asked for your credit card security code when processing a payment over the telephone. As with online transactions, it’s usually safe to do this – you just need to be sure that no one overhears the details you give out (so avoid public places when doing this).
On the other hand, when purchasing an item or service in person, you should never provide the details of your CVV. In fact, there’s no need for the retailer or service provider to request this – it doesn’t show up when the card is scanned normally and they have other ways of verifying that you’re the authorised card holder (signature or another form of identification) should they need to.
Handing over your CVV for purchases completed offline serves no purpose other than providing someone with the opportunity to steal the information. Because if they were to do this, they’d have everything they need to go ahead and make a bunch of fraudulent online transactions – on you!
Tips for staying safe
To avoid any issues with security or credit card fraud, there are a few things you can do:
- Only transact with reputable websites that you trust. And when you do, follow our 10 golden rules for safe online shopping.
- Install internet security software on your PC, tablet and/or smartphone. Doing this will help you steer clear of malware and phishing messages that could lead you to fake websites designed to steal your personal details.
- Always keep a close eye on your bank statement to identify any charges that haven’t been authorised.
- Never read out the full details of your credit card in a public place, or write them down anywhere for someone else to find.
- Avoid making payments over the phone with a credit card, unless you make the call directly and obtain the number from a trusted source. Scammers have been known to cold call victims and convince them that money is owed immediately for a problem that doesn’t exist!
- Don’t provide your CVV when processing a payment in person. It should never be required and if someone tells you otherwise, it’s a reason to be highly suspicious!
Have you had any dramas when using your credit cards online? Share your story with us below.