Apple fixed hundreds of bugs, 223 to be exact, across macOS Sierra, iOS, Safari, watchOS, and tvOS on Monday.
Tag Archives: Safari
Hackers Take Down Reader, Safari, Edge, Ubuntu Linux at Pwn2Own 2017
On the first day of Pwn2Own 2017 hackers poked holes in Adobe Reader, Apple Safari, Microsoft Edge, and Ubuntu Linux.
Apple Patches Trident Vulnerabilities in OS X, Safari
Apple has patched the Trident vulnerabilities in OS X and Safari. The flaws were originally disclosed in iOS and used to spy on a UAE human rights activist.
Outdated, Unpatched Software Rampant in Businesses
A Duo Labs report reveals the dangers of unpatched and outdated software used in business world.
Deluge of Apple Patches Fix iMessage Crypto Bug, Much More
Apple deployed patches for nearly all of its products, including Safari, OS X, iOS, Apple TV’s tvOS, and watchOS on Monday.
Pwn2Own Day Two: Safari, Edge Go Down And Winner Crowned
Tencent Security Team Sniper (KeenLab and PC Manager) takes top honors and is Master of Pwn for Pwn2Own 2016 earning $142,500.
Safari, Flash Fall at Pwn2Own 2016 Day One
Hackers took down Apple Safari and Adobe Flash earning $282,500 in prizes on Wednesday, the first day of the annual Pwn2Own hacking challenge in Vancouver.
How iOS users can stay protected against iScam threat
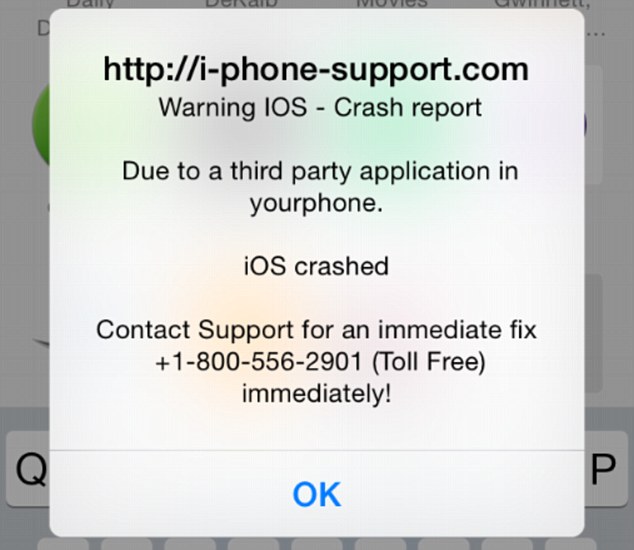
iScam displays a “crash report” to affected users. (Photo via Daily Mail)
It’s a common belief (and myth) that Apple products are invincible against malware. This false line of thinking has recently again been refuted, as iPhone and iPad users have been encountering a ransomware threat that freezes their Internet browsers, rendering their devices unusable. The ploy, commonly known as iScam, urges victims to call a number and pay $80 as a ransom to fix their device. When users visit an infected page while browsing using the Safari application, a message is displayed saying that the device’s iOS has crashed “due to a third party application” in their phone. The users are then directed to contact customer support to fix the issue.
How to clean your system if you’ve been infected by iScam
- Turn on Anti-phishing. This can be done by visiting Settings > Safari and turn on ‘Fraudulent Website Warning’. When turned on, Safari’s Anti-phishing feature will notify you if you visit a suspected phishing site.
- Block cookies. For iOS 8 users, tap Settings > Safari > Block Cookies and choose Always Allow, Allow from websites I visit, Allow from Current Websites Only, or Always Block. In iOS 7 or earlier, choose Never, From third parties and advertisers, or Always.
- Allow JavaScript. Tap Settings > Safari > Advanced and turn JavaScript on.
- Clear your history and cookies from Safari. In iOS 8, tap Settings > Safari > Clear History and Website Data. In iOS 7 or earlier, tap Clear History and tap Clear Cookies and Data. To clear other stored information from Safari, tap Settings > Safari > Advanced > Website Data > Remove All Website Data.
Check out Apple’s support forum for additional tips on how to keep your device safe while using Safari.
![]()
URL-Spoofing: Apple Safari Can Be Manipulated Easily
What it’s about
All you need to do so is a bit of Javascript. With just a few lines of it Safari users can be deceived by what’s commonly known as URL-spoofing: During such an attack, a computer user innocently visits a web site and sees a familiar URL in the address bar such as http://www.avira.com but is, in reality, sending information to an entirely different location that would typically be monitored by a cybercriminal.
The security issue was discovered by David Leo, who put together a proof-of-concept for it. When clicking on OK a new website is being loaded. While the address bar tells you that you are visiting dailymail.co.uk the actual page is definitely a different one.
The URL-spoofing itself is done with just a few lines of code:
function f()
{
location=”http://www.dailymail.co.uk/home/index.html?random=”+Math.random();
}
setInterval(“f()”,10);
The last part, setInterval(“f()”,10); , makes sure that the address bar is reloaded ever 10 milliseconds (so you might as well say, that it’s kind of a DDoS attack, too), just before the browser can get the real page and so the user sees the “real” web address instead of the fake one. This causes the spoofed URL to flicker; sometimes it’s even possible to briefly see the actual URL.
What you can do
Your first step should always be to make sure that your browser is up to date so that security updates can be installed once available. In addition to that open up the Safari settings, go to the advanced tab, and choose “Show full website address”. The browser will then show the results of MathRandom in the address bar.
Alternatively you could also just use another browser for the time being: The code will not work in Google Chrome and Mozilla Firefox.
The post URL-Spoofing: Apple Safari Can Be Manipulated Easily appeared first on Avira Blog.
Apple Fixes WebKit Vulnerabilities in Safari Browser
Apple has issued a series of bulletins for its Safari browser fixing various security vulnerabilities in its WebKit rendering engine.