This week in security news saw two of the scariest targets for hacks ever – nuclear plants and city-wide traffic systems. The stories delivered the goods, too — the traffic-light hack could basically have been carried out by anyone, and paralyze any one of 40 American cities, and America’s  Nuclear Regulatory Commission was successfully attacked three times within the past three years, by unknown attackers, some foreign – and largely using standard phishing emails and similar techniques. It is still unknown who the attackers were.
In terms of novel malware, it was a bit of a dry week (always a good thing) bar the return of scareware  – this time armed with an even more annoying method of making you pay up.
In Cologne, gamers gathered for Gamescom – and ESET’s Aryeh Goretsky took a look at how gaming has evolved, and cybercrime along with it, with discussions of gold-farming, theft of virtual goods, and how gaming companies are now fully awake to the threat of cybercrime.
Hackers get a “green†for go!
Often, when one reads a paper behind a cybercrime story, it’s disappointing – not so in the case of the novel attack against city-wide traffic systems described by University of Michigan researchers, which is genuinely terrifying. Little skill was required – radios are unencrypted, or used default passwords, and control units had known vulnerabilities.
An attacker, like the film’s ‘crew’ on robbery, could control a series of lights to give himself passage through intersections, and then turn them red to slow emergency vehicles in pursuit, according to the BBC’s report.
The researchers at the University of Michigan, who say that networked traffic systems are left vulnerable by unencrypted radio signals and factory-default passwords, and that access to individual lights – or even a city-wide attack, as in the film, is possible, according to Time’s report.
“This paper shows that these types of systems often have safety in mind but may forget the importance of security,†the researchers write. Technology Review points out that Michigan’s system, which networks 100 lights, is far from unique. Similar systems are used in 40 states.
Scareware II: The return
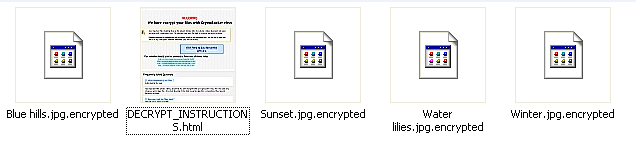
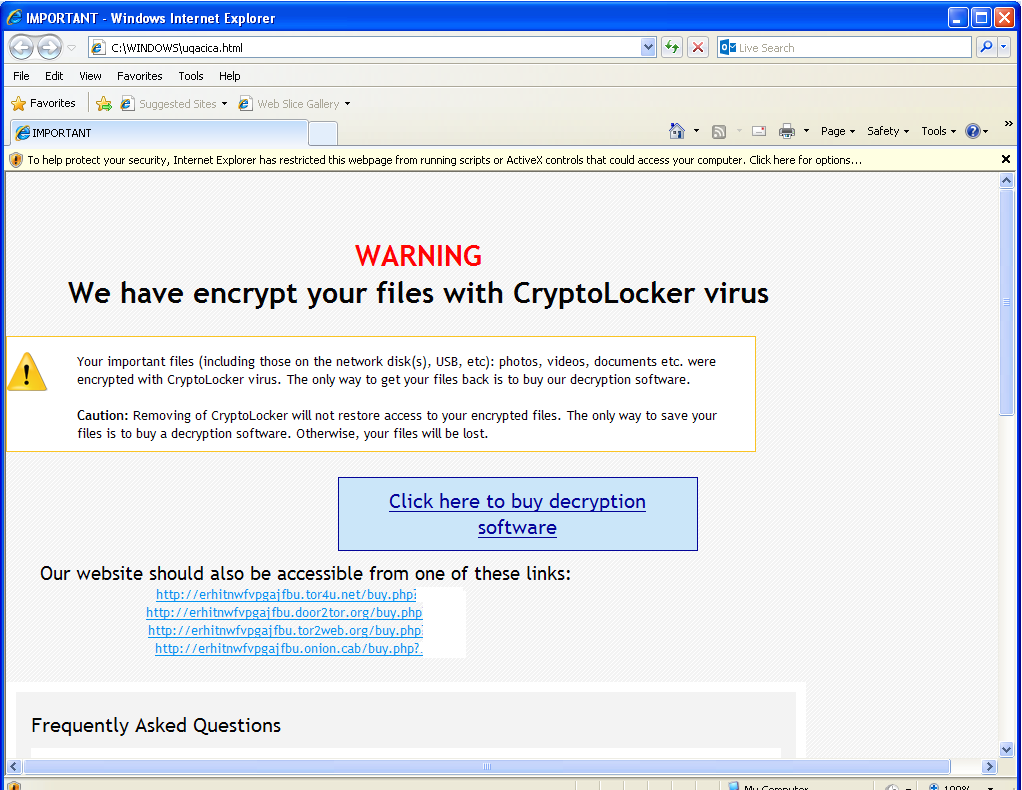
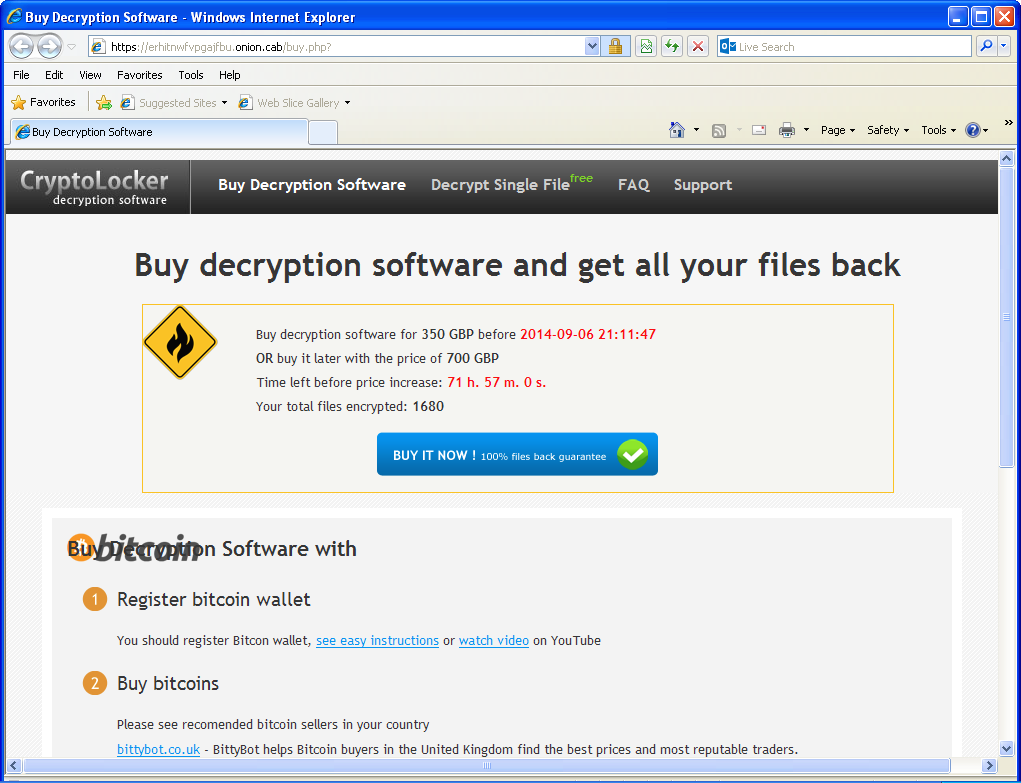
Over the past months, ‘scareware’ – windows that warn users that their machine is infected, then, ironically, persuade them to download malware – has dropped, says Microsoft, as users wise up.
But a new variant, Win32/Defru has a different and simpler approach on how to trick the user and monetize on it. Basically, it prevents the user from using the internet – it displays warning windows instead of sites. Now that really is cruel.
The malware targets 300 websites, and when a user tries to access them, they instead see the following fake message, ““Detected on your computer malicious software that blocks access to certain Internet resources, in order to protect your authentication data from intruders the defender system Windows Security ® was forced to intervene.â€
Rogue AV is still found – indeed ESET has been repeatedly ‘honored’ with fake scareware versions of  of its products such as when ESET researchers discovered a Trojan packaged to look like antimalware products,  – but Microsoft reports that in the past 12 months, scareware had fallen out of fashion.
Microsoft researcher Daniel Chipiristeanu says, “Lately we’re seeing a dropping trend in the telemetry for some of the once most-prevalent rogue families,  It’s likely this has happened due to the anti-malware industry’s intense targeting of these rogues in our products, and better end-user awareness and security practices.â€
Chipiristeanu says that “education†has played a part – but new gangs have simply moved on to new methods to target victims.
Pay for privacy? Yes we would!
Silent Circle, makers of Blackphone, are not smarting overly from their handset’s humiliation, it seems – and their mission to stop everyone spying on us continues. They have support, it seems - a poll of 2,000 people found that almost all of us believe we are being spied on, and about a third would pay to stop it.
Privacy issues have become an increasing concern outside the security community – in part thanks to revelations of government surveillance, as discussed by ESET researcher Stephen Cobb. Silent Circle carried out the survey in May this year, via OnePoll and found that 88% of UK workers believe their calls and texts are being listened to, versus 72% of Germans – it’s not clear by whom.
Nearly a third – 31% – of Germans would pay for a service which guaranteed their texts and calls were not being listened to. In Britain, 21% would do so. Germany is traditionally more privacy-conscious – services such as Google StreetView are not permitted there.
The scandal over Facebook’s Messenger app – and the overstated responses of many media outlets, served to highlight this. Cosmopolitan writes, “Basically, it can control your whole phone. And, most scarily of all, CALL PEOPLE.†Cosmopolitan had not been previously known for its concern with online privacy.
Nuclear Armageddon: Virtually here
A report released by America’s Nuclear Regulatory Commission highlighted how depressingly ordinary cyber attacks can still be effective against even the highest value targets.
The spear-phishing attacks against the Nuclear authority were hardly hacker whizkid territory, but nonetheless, hundreds fell for them.
CNET reports that one incident led 215 employees of the nuclear agency to “a logon-credential harvesting attempt,†hosted on “a cloud-based Google spreadsheet.†The information was obtained through a specific request by NextGov. A second spearphishing attack targeted specific employees with emails crafted to dupe them into clicking a link which led to malware on Microsoft’s cloud storage site SkyDrive.
The third attack was a spearphishing attack directed at a specific employee. Once his account credentials were obtained, emails were sent to 15 further employees, with malware-laced PDFs.
“It’s still unclear which country originated the attacks, and whether the attackers were acting independently or as a part of a larger state action.
NRC spokesman David McIntyre said that his security team “thwarts†most such attempts.
Conspiracy theorists, start your engines!
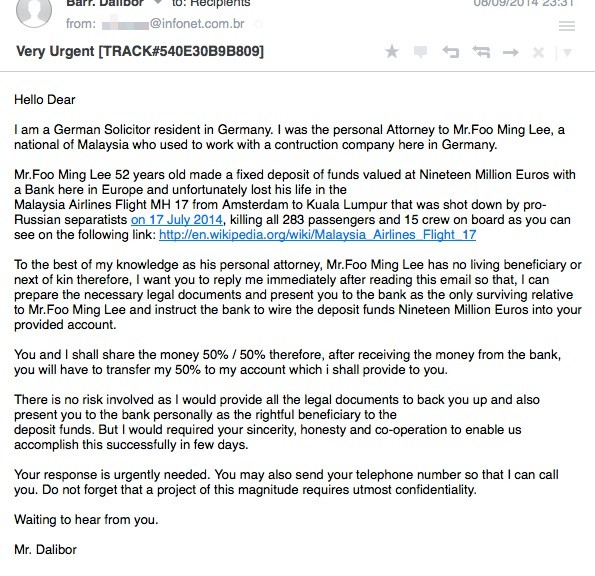
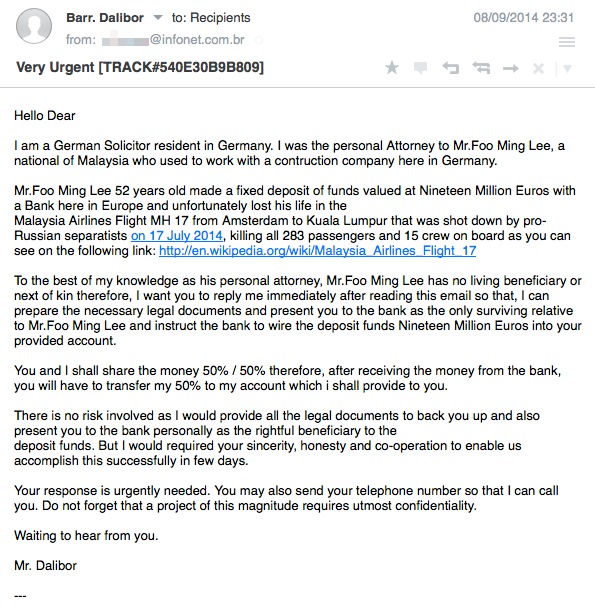
Our last story really is the stuff of conspiracy theorist’s dreams: the very next day after Malaysia Airlines Flightt MH370 disappeared, “sophisticated†malware was used to steal documents from government officials working the case.
A mysterious attacker in China purloined “classified documents†in “significant amounts”, details of which remained vague – stoking the fires of conspiracy still further.
The Malaysian Star claims that the attack targeted officials with a PDF document which appeared to be a news report about Flight MH370, and was sent to a group of investigators. Around 30 computers were infected by the malware.
“We received reports from the administrators of the agencies telling us that their network was congested with e-mail going out of their servers,†CyberSecurity Malaysia chief exec Dr Amirudin Abdul Wahab said.
“Those e-mail contained confidential data from the officials’ computers, including the minutes of meetings and classified documents. Some of these were related to the Flight MH370 investigation.â€
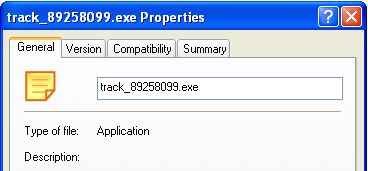
Business Insider says that the attack occurred one day after the Boeing 777 went missing, and took the form of an .exe file disguised as a PDF (a common office file format).
It’s unclear who the attacker – or attackers – were, but information from infected computers was transmitted to an IP address in China. Officials in Malaysia blocked the transmission, The Star said.
The post Week in security: Nuclear attack, scareware back and traffic-light hack appeared first on We Live Security.

![]()