A cyberespionage campaign pulled off by pro-Syrian hackers against Assad opposition fighters used social engineering to steal military planning documents.
Tag Archives: Social Engineering
Gitrob Combs Github Repositories for Secret Company Data
Gitrob, an open source intelligence tool, helps security analysts search Github organization repositories for files not meant for public consumption.
Dridex Banking Trojan Spreading Via Office Macros
Spam campaigns in the U.K. are using Office macros to spread the Dridex banking Trojan, researchers at Trustwave report.
New Emomet Variant Targets Banking, Email Credentials
Security researchers are tracking a new version of the Emomet malware that is targeting users’ banking credentials and also has the ability to steal email usernames and passwords, which are then used to send spam from compromised accounts. The new variant of Emomet has mostly been seen targeting users in Germany, but researchers at Microsoft […]
‘Worst virus ever’ POSTCARD hoax still circulating
[AUDIO VERSION: This is an audio version of this blog post. Click below to listen.]
During the Christmas holidays, my mother received this email from a well-meaning friend. Since her daughter works for the most trusted security company in the world, she immediately asked me about the authenticity of the message.
Here’s the email:
Subject: VIRUS COMING !
Hi All,
PLEASE FORWARD THIS WARNING AMONG FRIENDS, FAMILY AND CONTACTS!
You should be alert during the next few days. Do not open any message
with an attachment entitled POSTCARD FROM HALLMARK , regardless of who sent it to you.
It is a virus which opens A POSTCARD IMAGE, which ‘burns’ the whole
hard disc C of your computer.
This virus will be received from someone who has your e -mail address
in his/her contact list.
This is the reason you need to send this e -mail to all your contacts.
It is better to receive this message 25 times than to receive the virus
and open it.
If you receive an email entitled “POSTCARD,” even though it was sent to
you by a friend, do not open it! Shut down your computer immediately.
This is the worst virus announced by CNN.
It has been classified by Microsoft as the most destructive virus ever.
This virus was discovered by McAfee yesterday, and there is no repair
yet for this kind of Virus.
This virus simply destroys the Zero Sector of the Hard Disc, where the
vital information is kept.
COPY THIS E-MAIL AND SEND IT TO YOUR FRIENDS.
REMEMBER: IF YOU SEND IT TO THEM, YOU WILL BENEFIT ALL OF US
This particular email has been around for years, and you have probably seen one of its incarnations. Although there are real incidents of malware being distributed via e-cards, this is a bogus, unsubstantiated hoax.
 The language is quite strong – phrases like the worst virus and the most destructive virus ever are sure to get the attention of security-minded people. The problem is that the email fails to provide any authentic details to learn more about the threat, just vague announcements and classifications.
The language is quite strong – phrases like the worst virus and the most destructive virus ever are sure to get the attention of security-minded people. The problem is that the email fails to provide any authentic details to learn more about the threat, just vague announcements and classifications.
“The email doesn’t actually mention a specific virus,” said Jan Zika, an Avast Virus Lab analyst. “Sure some viruses use the “Postcard” social engineering method to trick users to click the link, but this email has been circulating for a couple of years now, and it never says which virus it is.”
The email does say what the virus can do, This virus simply destroys the Zero Sector of the Hard Disc, where the vital information is kept, and it burns the whole hard disc C of your computer. Pretty scary stuff!
“No, it cannot burn anything, and no, it is not most destructive virus ever,” said Zika. His advice? “It’s best to avoid such messages unless you can confirm that the threat is real.”
Protect yourself against email hoaxes
- Keep you antivirus protection up-to-date and scan regularly for viruses and malware. Both Avast Internet Security and Avast Premier include anti-spam filters to keep your inbox free of this kind of nonsense.
- Use caution when opening attachments or downloading files. Double check that it’s from a sender you know and trust.
- Before clicking on any links or attachments, try to verify that the email came from a legitimate source. If you can’t, then don’t click.
On Neuroscience and Phishing Attacks
All kinds of fun facts bounce around the internet. You might have seen the one about contextual reading: It deson’t mttaer in waht oredr the ltteers in a wrod aepapr, you can sitll raed it wouthit pobelrm. See how this neuro-scientific peculiarity helps phishing criminals earn lots of money and what simple things you can do to protect yourself.
Why are URLs so important?
As I work in the URL detection team of Avira’s Protection Labs, you might not be surprised by me saying that URLs are a very important part of our daily lives. In ancient times, ten or fifteen years ago that is, data was shared through floppy disks, which were still in heavy use back then. (You know, the legacy industrial equipment that looks like the ‘Save’ button in your applications.) Times have changed and so has the industry. In today’s world, files are distributed over the Internet. File hosting services, like Dropbox and OneDrive, flourish like never before. The Internet actually consists of many subsystems like email, file sharing and the Word Wide Web. Also known as just the Web, the latter represents what you usually do in your browser: click on links, enter URLs in the browser bar, search the web; those are all examples of how you use URLs to access the Web.
What is a domain?
Avira’s domain entered in a web browser
Domains exist because they are easier to remember than IP addresses (which domains point to). They operate pretty much like a phone book. You do not remember the phone number of a person to call, you look them up in the phone book. This establishes the connection between person and callable number. While you still have to enter the number yourself on the phone, your browser will take that burden off of you. So, when you enter www.wikipedia.org in your browser, it will look up and redirect you to the proper IP address of the web server that hosts the site. If you enter www.wikkepedia.org, you will not be redirected to the site you intended to visit but rather receive a browser warning, stating that the website does not exist – just like the well-known “The person you’ve called is temporarily not available” message you hear on the phone when you dial the wrong number.
Some typos are intentional
“Where does the neuroscience bit come into play?”, you might ask. Cyber criminals are able to register this domain and host advertisements. Once you accidentally enter the wrong URL, you will be redirected to this so-called typosquatted domain and thus will have accessed ads. This in turn generates money for the advertiser. Check out my other article about online advertisements for further information. The important thing to remember is, that this is possible not due to careless surfing. It works because the human brain operates with contextual sections.
Some just want to make a few bucks by registering a misspelled domain in order to sell it back to the brand owner. One could register www.citybank.com and sell it to www.citibank.com, as this is a common misspelling.
From Malware to Phishing
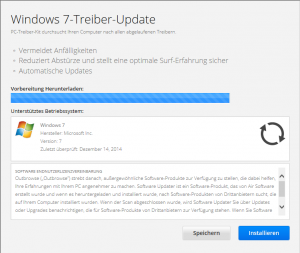
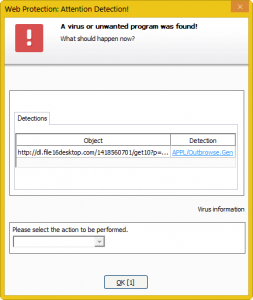
Other unfair practices include redirection to potentially unwanted applications (abbreviated PUA). Your browser will typically show a warning about the state of your computer – telling you it might be infected, your drivers might be out of date or that you have won a million dollars. To give you a practical example: I found this software recommending driver updates for my computer while going through misspelled Wikipedia links (I omit the direct URL for obvious reasons). A click on “Installieren” (region-specific, as I am browsing from Germany), tries to install the software that I do not actually intend to have on my PC. Fortunately, I am one of the lucky people having Avira security products installed. The Web Protection kicks in and saves me from accidentally installing PUA on my PC.
What to do about it?
No antimalware solution will ever give you 100% security. They are considered to provide you with something in between base and enhanced detection of malicious software on your PC. Nowadays, those programs also include effective web protection like cloud-based scanning of URLs. Avira offers both traditional antimalware solutions and an unobtrusive browser plugin to protect you against most of it. However, you should never solely rely on software to protect you. It helps a lot to know about the risks. You just might look twice the next time. ![]()
Resources and recommended reading
Breaking the Code: Why Yuor Barin Can Raed Tihs
Typosquatting
We knew the web was big…
How Big Is The Internet?
TypoSquatting – Malicious Domains Malware Domains
The post On Neuroscience and Phishing Attacks appeared first on Avira Blog.
Attackers Compromise ICANN, Access Zone Files System
Unknown hackers were able to compromise vital systems belonging to ICANN, the organization that manages the global top-level domain system, and had access to the system that manages the files with data on resolving specific domain names. The attack apparently took place in November and ICANN officials discovered it earlier this month. The intrusion started […]
When it comes to dangers on the internet, we are our own worst enemies
Today’s biggest threat to the normal consumer is the consumer themselves.
This bold statement was made by Avast CEO Vincent Steckler in an interview with German technology website Valuetech in Munich last week. That’s a daring position to take after this year’s revelations about NSA spying, the theft of tens of millions of customer passwords from major retailers like Target and Home Depot, the recent Sony Pictures hack, and the normal parade of Trojan horses, worms and viruses, but it’s one that Steckler stands behind.
Watch the interview here (04:00),
Mr. Steckler has good reason for his conclusion. Here’s a few of the main points he made during the interview.
Social engineering preys on human weakness
“A lot of attacks are still using social engineering techniques; phishing emails – ways of convincing the user to give up valuable information,” said Steckler.
An example of phishing emails just occurred after Black Friday, when cybercrooks sent millions of fake purchase confirmation emails to customers of major retailers. You can read about that, as well as what to do if you are a victim, in our blog, Fake confirmation emails from Walmart, Home Depot, others in circulation.
The Mac misconception
Mac users are well-known for proudly touting that they don’t use antivirus protection because they never have a problem with viruses. But, it’s really a numbers game.
“There is no fundamental difference,” Steckler says of the security of PCs and Macs. “Mac is not inherently any safer, as a technology, than Windows is. What makes a difference there is what is more opportune for a bad guy to attack.”
He explains that malware written for Windows can attack up to 93% of the world’s PCs. Mac malware only reaches 7-8% of the world’s PCs. The safety then lies in the lower numbers of Mac devices rather than a technical safety advantage.
Households networks are as complicated as small business networks
With the interconnectivity of household devices from household computers, mobile phones, TVs and even refrigerators, Steckler compares the typical household network to that of a small business.
“The central weakness in this ‘Internet of Things’ will be that home router – the thing that connects everything together,” says Steckler, “and basically doesn’t have any security on it.”
Avast 2015 seeks to address this lack in security by including the new Home Network Security scanner.
Attackers Using Compromised Web Plug-Ins in CryptoPHP Blackhat SEO Campaign
Researchers have discovered a group of attackers who have published a variety of compromised WordPress themes and plug-ins on legitimate-looking sites, tricking developers into downloading and installing them on their own sites. The components then give the attackers remote control of the compromised sites and researchers say the attack may have been ongoing since September 2013. […]
Myths about malware: an exploit is the same as malware
In this post we want to share with you a question that arose from the first post in this series: whether exploits are the same as malware. What are we talking about? The best way to debunk any myth is to start by understanding what it is we are talking about.
The post Myths about malware: an exploit is the same as malware appeared first on We Live Security.
![]()