We leave a huge digital footprint on Facebook. Did you ever think about what will happen with your data when you pass away?

The social giant Facebook has existed long enough to realize that it is part of a human’s life events. We announce the most important milestones on our timelines by sharing with our Facebook friends the joy of getting married, having babies, or moving abroad. But what will happen with all that data when we pass away? Discussing your digital legacy isn’t pleasant, but it’s important is our reality. Don’t leave it up to your family member, friends, or even worse: Facebook itself. In this article I will guide you through all the options you have, so you can make a conscious decision about your data, using the tools that Facebook offers to its users.
Decide what to do with your data!
In short you have two options: To delete your account or agree to memorialize your person within the social network. In case you decide on the second option, it is recommended to set up a Legacy Contact: A person who will take care of your account, if something happens to you.
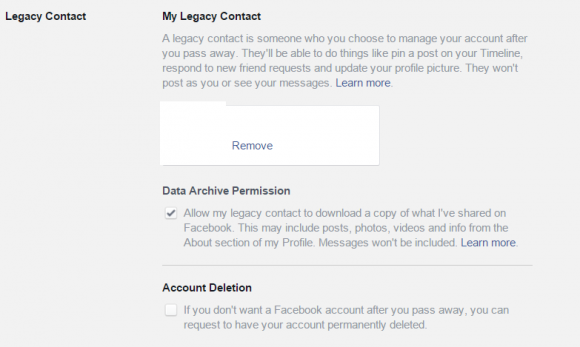
Legacy contact settings
Delete your account
Deleting an account is the easier and more radical option. All your data – pictures, posts, comments, connections, messages, apps you have ever installed – simply everything, will be permanently removed.
Here are the steps you have to take first, to set this option in your profile:
- From the top right of Facebook, click and select Settings
- From the left menu, click Security
- Click Legacy Contact
- Click have your account permanently deleted and follow the on-screen instructions.
This is however only an initial step to remove your account. If something happens to you, Facebook still needs to be notified. Your immediate family member needs to contact Facebook to inform about the lose. There is a Special Request for Deceased Person’s Account where all the information, including a death certificate needs to be sent. Only after that will Facebook permanently remove the profile.
Setting up a Legacy Contact
A Legacy Contact is a trusted person, a friend or a family member, that will make sure your profile is memorialized and that will take care of it afterwards. According to Facebook, the Legacy Contact will be able to:
- Write a post to display at the top of the memorialized Timeline (for example, to announce a memorial service or share a special message)
- Respond to new friend requests from family members and friends who were not yet connected on Facebook
- Update the profile picture and cover photo
- Archive your data (Only if you check this option in the settings): Photos and videos you uploaded, wall posts, profile and contact info, events, and friends list. The following data can’t be downloaded: Messages, ads you clicked, pokes, security and settings info, photos you automatically synced but didn’t post.
How to set up a Legacy Contact?
Select the person first and talk about it in advance. You can always change your selection and chose another person, but it is always better to discuss this responsibility in person ahead. It is also important to educate your Legacy Contact what to do.
Here is how to add a legacy contact:
- Click in the top right of Facebook and select Settings
- In the left menu, click Security
- Click Legacy Contact
- Type in a friend’s name and click Add
- To let your friend know they’re now your legacy contact, click Send
- Your friend will be notified with the following message
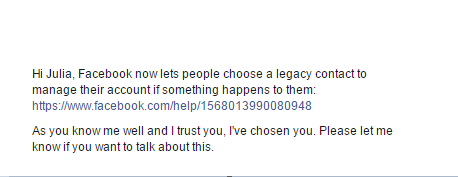
What to do, if you are appointed to be a Legacy Contact?
Respecting your deceased friend or family member is a responsibility. The first thing you will have to do is request memorialization of the profile. Once it is set up as a memorial, the profile will receive the “Remembering” label just above the name, next to the deceased person’s profile picture. Memorialized profiles don’t appear in public spaces such as in suggestions for People You May Know, ads, or birthday reminders. As a Legacy Contact you can manage a profile in a limited way. To do it you have to go to the profile, in the bottom right of the cover photo click Manage and than you can:
- Add a pinned post to announce to the circle of the friends what has happened
- Respond to new friend requests
- Change the profile picture and cover photo
Please visit our blog often for more updates on security and privacy on Social Media.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.


![]()