Have you ever wondered why the advertisements that appear on your Facebook feed offer you the exact product and service that you are supposedly interested in? Have you also stopped to think about what information Candy Crush holds on you, or do you just click play anyway?
Facebook offers you information on your privacy, although it’s like that few users have ever reviewed it. Hardly surprising when you consider that it would take it 76 days to read all of the terms and conditions of the services that we use over the course of a year, according to a study carried out by the Carnegie Mellon University.
It’s likely that lots of workers include information relating to their role in the company on their Facebook profile, so both you and they could benefit from a better level of privacy control on the social media site. Here are a few tips to make it harder for companies to follow your tracks online.
Stop giving away personal information to applications
Every time that you install an application from Facebook it tells you what information you will share with it. In that moment, you can edit the information you wish to share. Seeing as you’ve probably ignored this or have logged into Facebook from the external website, we’ll explain to you how to restrict the details that you give away to the apps.
- The first thing you have to do is click on the lock in the top right part of the Facebook page. Click on “see more” form the expandable menu and access “settings and privacy tools”.
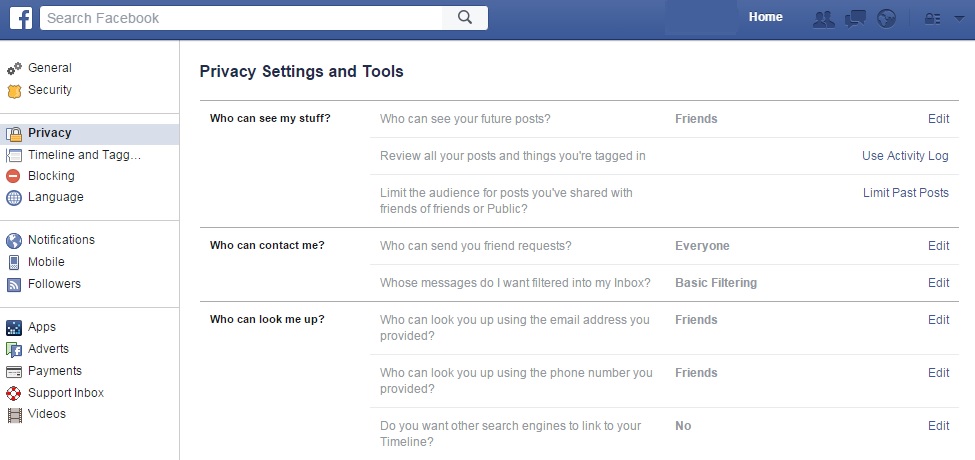
- Then, search the left column for the button marked “applications” and click on “see all”. We bet you never expected to see so many websites associated with your Facebook page! Now, it’s time to organize it all.
- You can click beside each application to delete it from your account, or you can click on the pencil icon to edit the information that each app keeps on you. Keep in mind that there may be some details that are obligatory and you can’t keep them hidden.
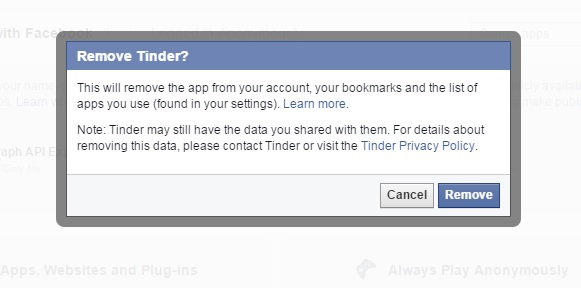
- When you’ve finished this process, go to the bottom of the page where you’ll find two very interesting options. The first of these is the option to activate “always play anonymously” and the second is to edit the information on Facebook that others can see in the apps that you use by clicking on “applications used by others”.
Repel the advertising
If you want to stop Facebook from using your personal information to show you predetermined advertisements, then there are a few ways you can go about it.
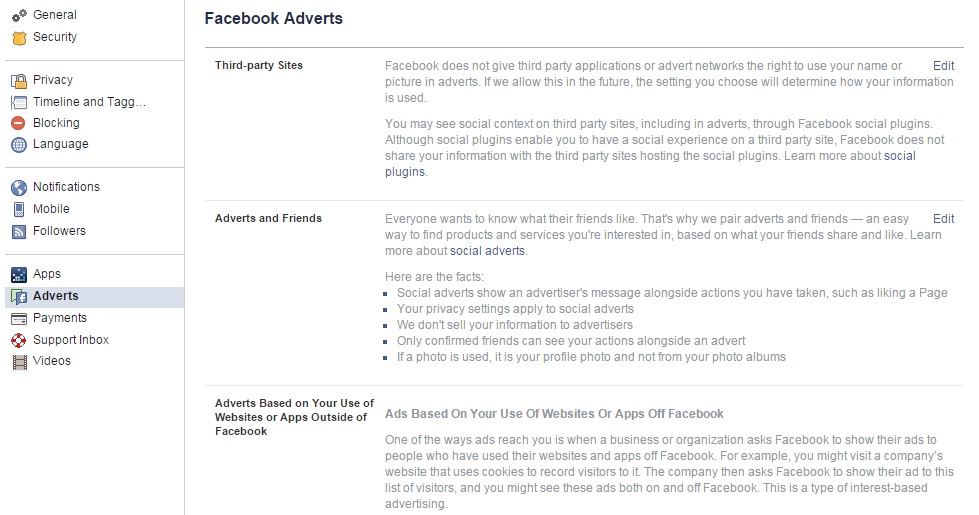
- The first is click on the arrow at the top of the page, beside the lock icon, and access the part for “settings”. In the left column you’ll see “adverts”. From there you can deny Facebook the right to use your actions (for example, things you indicate you like) to offers ads to your friends and that you don’t receive ads based on their preferences either.
To do this, you need to click on the “edit” option for both “other websites” as well as “adverts and friends” in order to change the default setting from “only friends” to “nobody”.
You can also use other tools to avoid this personalized advertising such as Facebook Disconnect or Adblock Plus. So, if you want to improve your privacy on Facebook and control what businesses can analyze from your information, you know what to do. It is also recommended that you read the policy of the company so as you know what you’re getting yourself into.
The post Facebook ads. How to avoid them? appeared first on MediaCenter Panda Security.