An overwhelming flood of apps that used location data became available, and down to this day, new ones are continuing to be launched all the time.
While there’s still interest in apps that use location data, some of that enthusiasm has started to die down. Quite frankly, many users are suffering from Location Fatigue. Since most users were once all too willing to share their location with anyone and anything, app developers have assumed that this is still the case and continue to use location data to the point that it feels like almost every app you download wants to access your location for some odd reason, even when it’s totally not required.
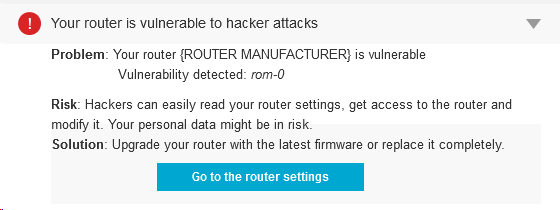
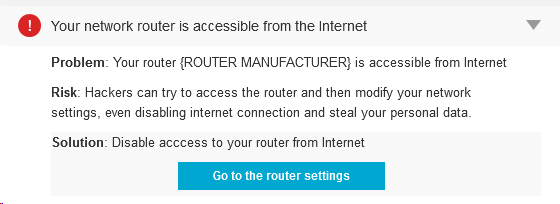
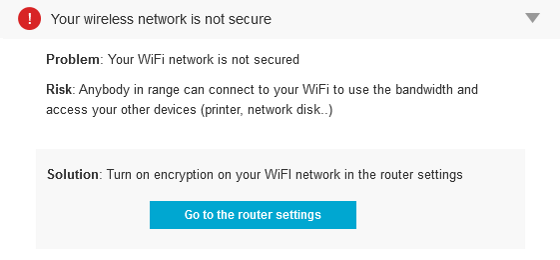
As you can imagine, this reality brings a host of privacy concerns with it. Not only might social apps share your location with your friends or possibly strangers, but other apps could even use that data for advertising purposes. When an app uses your location in a way that you understand and derive benefits from, then that can be a great experience, but having your location data observed and shared just because it can be done doesn’t always lead to a great user experience, especially when it’s being done in a way that’s not transparent.
If you look at the location settings in your smartphone right now, you’ll probably be shocked by how many apps have location functionality. Take a good look at your list of apps and decide which ones you actually want to be able to see where you are at any given moment. Additionally, whenever you download a new app, think for a moment about the location data that it might be accumulating and what the purpose of it is.
There are still plenty of smartphone users who don’t have a care in the world about the location data that their apps have access to, but if privacy is important to you, then you might want to make your location data available to apps on more of a need-to-know basis.
The post How to cure Location Fatigue appeared first on Avira Blog.







 This is not very attractive.
This is not very attractive.