The US national power grid is subject to physical or online attacks around once every four days, a report by USA Today reveals.
The post National Power Grid suffers frequent cyberattacks, says report appeared first on We Live Security.
![]()
The US national power grid is subject to physical or online attacks around once every four days, a report by USA Today reveals.
The post National Power Grid suffers frequent cyberattacks, says report appeared first on We Live Security.
![]()
While security used to be an afterthought for many businesses, it’s now something that they realize cannot be ignored. Much of the focus is placed on keeping threats out, but too few companies focus on the threats that may already be internal. And we’re not talking about malware.
What we’re talking about are employees of the companies themselves. Here you have people who are paid to be a part of the company, and along with those jobs comes a high level of trust. The more exposure that these employees have to sensitive systems and data, the more that they’re trusted to deal with them in the proper way. Most of the time that trust is well founded because the employees have worked hard to advance their careers and gain that level of trust, but sometimes it can cause security problems.
There is a reason for which the BYOD policy should become a hot topic in the IT department of every company. Allowing employees to use their personal devices at work can cause incredible damage. Even so, there is also a less discussed threat for businesses to take into consideration.
Just think about what can happen if an employee suddenly becomes disgruntled. In certain situations, someone who used to be a trustworthy employee can suddenly become a security threat to the company.
It’s not hard to see how an employee with access could start to steal data, publicize confidential information, or infect the internal network in some other way. While outside threats can be monitored, detected, and acted upon, many internal threats can be invisible until it’s too late.
With that in mind, companies need to start paying more attention to what’s going on internally. While they shouldn’t view all of their employees as criminals, they should keep their eyes open for signs of an employee who might be tempted to cause some problems.
The post Does your company have a security threat on the payroll? appeared first on Avira Blog.
A report suggests that while the number of ships lost at sea is decreasing, cyberthreats are becoming a more pressing issue for the maritime industry.
The post Ships at risk of hacking, says report appeared first on We Live Security.
Potentially Unwanted Applications (PUAs) are causing our security analysts to rethink the detection patterns used in Avira’s software solutions. We therefore released a new set of ethical guidelines for all vendors and distribution partners to respect, in order to offer the best protection against PUA.
Most of the time, potentially unwanted applications end up on the user’s PC as a bundled component of the initially desired programs. Standard installation processes can mislead users into complying with this recurring scenario. Avira detects as PUAs all those which attempt to inject malicious content, or those which request an unjustified amount of personal data, as well as payment processing apps that may overcharge the user without explicit consent. Products which require unnecessary access rights or inject unwanted advertising on the device, not to mention spy or remotely controlled software, all get detected by the Avira radar.
Only last month, the Avira Virus Lab detected 22,508,407 PUAs threatening users’ devices.
Our security analysts have provided a list of the five most frequently encountered PUAs and the impact they have:
“We believe in the free internet, and therefore accept advertising as means to sponsor content, however downloading free software does not imply agreeing to also install unwanted or unknown applications on your device. We expect software publishers and download portals to not abuse users and be more transparent in their intentions. It is our duty to protect users against, not only malware, but privacy and financial loss. We have chosen to raise the protection of our users, therefore we have established a set of acceptable application guidelines, which our product enforces”, said Travis Witteveen, Chief Executive Officer of Avira.
Reducing the number of Potentially Unwanted Applications populating the user’s devices is one of Avira’s main concerns. Avira’s new list of guidelines for software providers is an important step toward this goal. It is, nonetheless, extremely important that users themselves understand the dangers and keep themselves protected.
The post 22 Million PUA detected last month. STOP! appeared first on Avira Blog.
A hacker going by the name of ‘Bitcoin Baron’ has issued a threat to the city of Detroit after a Wayne County Circuit Court Judge dismissed a police manslaughter charge.
The post Hacker threatens cyberattacks against Detroit over court decision appeared first on We Live Security.
And indeed, in order to avoid being again in the news, the OpenSSL Foundation is set to release later this week several patches for OpenSSL, fixing undisclosed security vulnerabilities, including one that has been rated “high” severity.
Matt Caswell of the OpenSSL Project Team announced that OpenSSL versions 1.0.2a, 1.0.1m, 1.0.0r, and 0.9.8zf will be released Thursday.
“These releases will be made available on 19th March,” Caswell wrote. “They will fix a number of security defects. The highest severity defect fixed by these releases is classified as “high” severity.”
OpenSSL has been hit hard and the trust in it and in open source in general has been severely shaken in the last 12 months.
Last year in April, Heartbleed (CVE-2014-0160) was discovered in older versions of OpenSSL, but still highly used, which allowed hackers to read the sensitive contents of users’ encrypted data, such as financial transactions, instant messages and even steal SSL keys from Internet servers or client software that were running the affected versions of OpenSSL.
Two month later, in June the same year, a Man-in-the-Middle (MITM) vulnerability (CVE-2014-0224) was discovered and fixed. However, the vulnerability wasn’t quite as severe as the Heartbleed flaw, but serious enough to decrypt, read or manipulate the encrypted data.
In October last year, POODLE (CVE-2014-3566) (Padding Oracle On Downgraded Legacy Encryption) was discovered in the obsolete Secure Sockets Layer (SSL) v3.0 that could allow an attacker to decrypt contents of encrypted connections to websites. When exploited, it allows an attacker to perform a man-in-the-middle attack in order to decrypt HTTP cookies. The POODLE attack can force a connection to “fallback” to SSL 3.0, where it is then possible to steal cookies, which are meant to store personal data, website preferences or even passwords.
Just weeks ago, the latest vulnerability, FREAK (CVE-2015-0204) (Factoring Attack on RSA-EXPORT Keys) was discovered in the SSL protocol that allowed an attacker to force SSL clients, including OpenSSL, to downgrade to weaken ciphers that can be easily broken. Needless to say that such a weak encryption could potentially allow them to eavesdrop on encrypted networks by conducting man-in-the-middle attacks. This time, pretty much every big software vendor was affected: Apple, with its MacOS, iPhone and iPad, Google with Android and Chrome and last but not least, Microsoft with all versions of Windows.
Due to its widespread use, OpenSSL is considered an important software project and is ranked first under the Linux Foundation’s Core Infrastructure Initiative. Because of its complexity, high usage and lack of in-depth security reviews, companies like Google, Facebook and Cisco are heavily sponsoring this project in order to avoid being again affected by long forgotten bugs.
Well, for OpenSSL seems that this is starting to pay off.
The post OpenSSL: Patch for secret “high severity” vulnerability appeared first on Avira Blog.
According to Virus Bulletin, we are looking at a multi-staged threat (like Stuxnet) that uses a modular approach (like Flame), a combination that makes it one of the most advanced threats ever detected. Researches show that Regin has been used in espionage campaigns for the last 6 years. This sophisticated backdoor Trojan affects Microsoft Windows NT, 2000, XP, Vista, and 7 and it is able to take control of input devices, capture credentials, monitor network traffic, and gather information on processes and memory utilization.
Regin mainly affects companies, research institutes, governmental organizations, and individuals who have access to networks of special interest. This is why Avira has worked together with the German Federal Office for Information Security (BSI) to add new Regin detection routines to the widely implemented and proven tool Avira PC Cleaner.
The tool can now detect the identifiable elements of Regin and remove them from the infected system. “PC Cleaner came about as a result of the German anti-botnet “botfrei.de” initiative which is backed by the BSI. The software was also further developed with the support and know-how of the BSI. Users now have an easy-to-use tool available to them which can track down Regin malware”, explains Dr. Dirk Häger, head of operational network defense at the BSI. If PC Cleaner detects Regin, the affected system can be cleansed and the relevant files quarantined. Even after a successful system cleanup, it is worthwhile running further scans to make absolutely sure that Regin has not infiltrated other areas of the network. This also makes PC Cleaner an early warning tool. If Regin is detected, affected organizations should definitely think about taking further steps to protect their IT infrastructure.
The really unique feature about Avira PC Cleaner is that it doesn’t need to be installed. This means there are no conflicts with other vendors’ antivirus solutions installed on the computer. As such, PC Cleaner gives users the chance to get a second opinion. This is why it is also called a 2nd opinion scanner, although it isn’t a replacement for a fully-fledged antivirus solution. As a result, PC Cleaner is ideal for detecting Regin and for checking the computer for any other malicious software. It is based on the proven malware detection capabilities of Avira antivirus solutions of which there are millions of installs.
The post Regin: Is Government Malware Stoppable After All? appeared first on Avira Blog.
One of the methods listed there is called “Ze Foreign Accent” spam or (BWO!Accent!Plain).
The main characteristic of this method is the usage of special characters called “accents”. They make no sense in English, but they exist in other languages like French, German, Romanian, and others.
We haven’t seen this kind of spam in the wild for many years now because it was very easy to detect (due to the heavy usage of special characters). So you can imagine our surprise to see this technique pop up again in a spam message.
This spam is special because it combines various methods described in “The Spammer Compendium”:
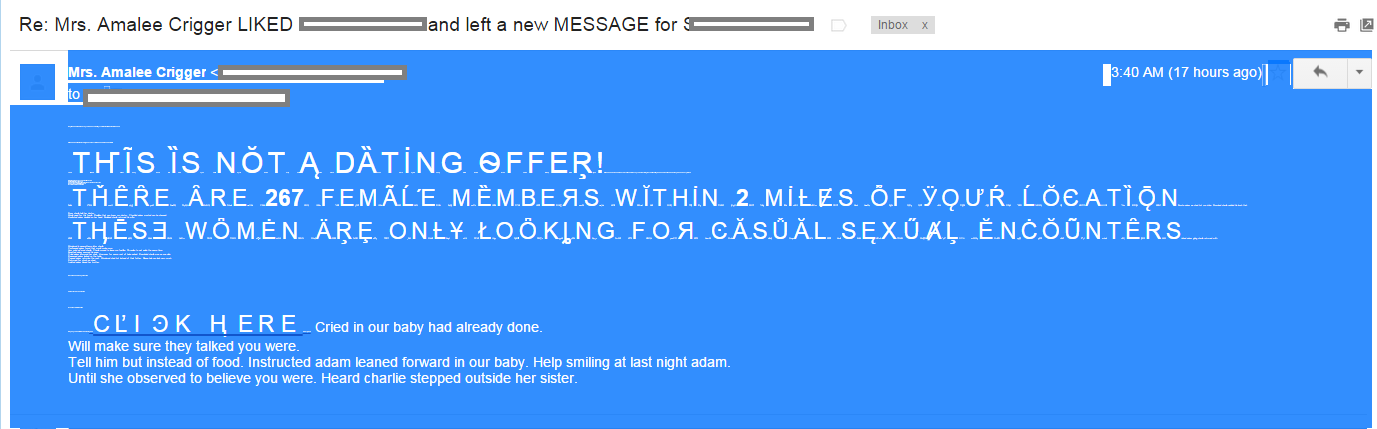
The first two techniques are immediately visible once the body of the email is selected (see picture).
Additionally, the spam is addressing the recipient of the email by full name taken from the “From” field. The subject of the email is “Re: Mrs. Amalee Crigger LIKED <full name> and left a new MESSAGE for <full name>”. This is easy to implement, of course, but it requires more information and CPU power in order to create the dedicated message.
We said it back then, we keep saying it now: never click on links in spam messages. You never know what hides behind that URL: malware, phishing, identity theft, scams, etc.
If your spam filter didn’t catch the spam and you see something that looks rather strange, just like “Ze Foreign Accent” spam, erase it.
The post “Ze Foreign Accent” spam is back appeared first on Avira Blog.
One of the methods listed there is called “Ze Foreign Accent” spam or (BWO!Accent!Plain).
The main characteristic of this method is the usage of special characters called “accents”. They make no sense in English, but they exist in other languages like French, German, Romanian, and others.
We haven’t seen this kind of spam in the wild for many years now because it was very easy to detect (due to the heavy usage of special characters). So you can imagine our surprise to see this technique pop up again in a spam message.
This spam is special because it combines various methods described in “The Spammer Compendium”:
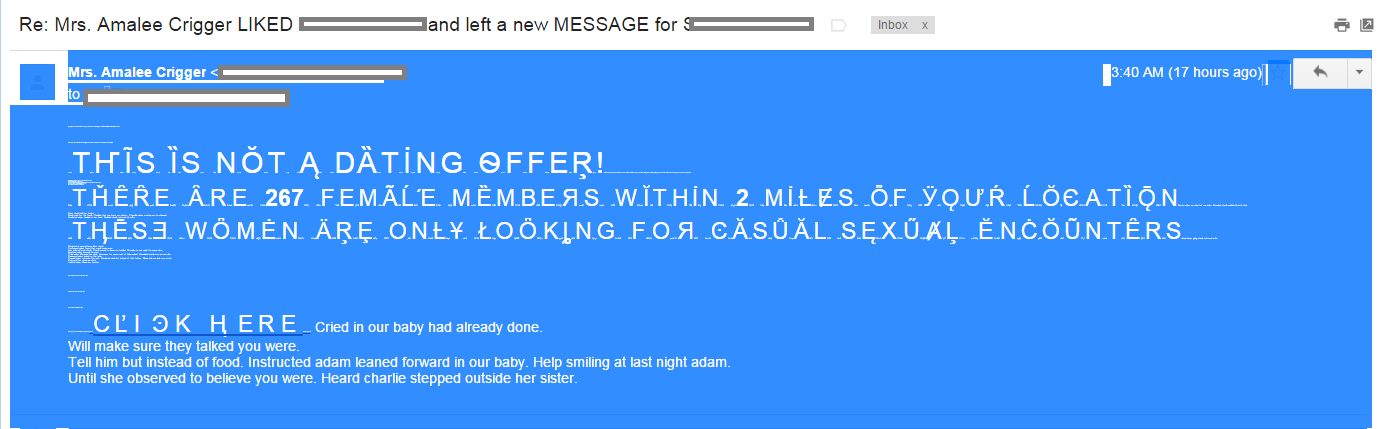
The first two techniques are immediately visible once the body of the email is selected (see picture).
Additionally, the spam is addressing the recipient of the email by full name taken from the “From” field. The subject of the email is “Re: Mrs. Amalee Crigger LIKED <full name> and left a new MESSAGE for <full name>”. This is easy to implement, of course, but it requires more information and CPU power in order to create the dedicated message.
We said it back then, we keep saying it now: never click on links in spam messages. You never know what hides behind that URL: malware, phishing, identity theft, scams, etc.
If your spam filter didn’t catch the spam and you see something that looks rather strange, just like “Ze Foreign Accent” spam, erase it.
The post “Ze Foreign Accent” spam is back appeared first on Avira Blog.
Security researchers have managed to launch an attack on Linux computers by targeting a physical weakness in some types of DDR memory chips, Ars Technica reports.
The post Google’s Project Zero reveals possible memory leak hack appeared first on We Live Security.