Storing passwords
Passwords may look to you like doors and keys:
they just have to match…

…but a system (website, network…) has to store the passwords of many users!
If a system stores all the users passwords
in their original form, like a secret in a chest,

…then once the chest is opened,
all passwords are instantly known!
The weakness:

So you probably guess that there is a huge potential security risk,
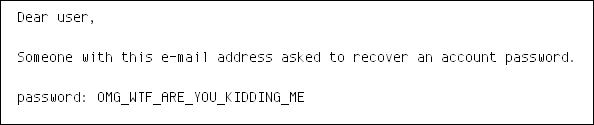
and when you receive an e-mail mentioning your actual password…
…then it means that the system actually knows your original password!
So, in a single attack, someone could just open the chest, and instantly get the password of every user.
This means only one thing for the security of such a system:
The solution:
So, you want to check if an entered password is correct, yet you need to store many passwords without leaking them.
There’s one answer:
Instead of storing passwords, you store a key that is derived from the password: this makes it possible to authenticate the user without actually storing the password:
- take the entered password
- calculate the key
- compare with the key generated with the original password
For example, a bcrypt-derived key of “password” is “$2a$10$3BY0wQ3rgzBf6VlG0YFLoekcGrrHKYdSUdSSrN37TqClNg7Oouzey“.
It’s much longer, and in practice, it’s very difficult to determine the original password that it was derived from.
Why not using just any complex hash function to derive the keys?
Because such key derivation functions are specifically designed to prevent an attacker to generate in advance a list of keys from all standard passwords, or better, a well-organised table.
Conclusion
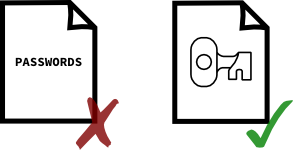
To prevent the risk of an instant and complete leak, one should never store passwords, but only derived keys, generated via dedicated algorithms.

These keys are mathematically derived from the entered passwords.
That way, you have a real strong authentication system without a vulnerable list of passwords.
For a multi-user system, storing passwords is a big risk !
In a next blog post, we can show how that influences Windows security…
The post Storing passwords appeared first on Avira Blog.