Users who don’t pay attention to warning messages on their iPhones or iPads run the risk of becoming infected with malware that can steal their personal information such as text messages, contact lists, pictures and even their location.
If you’ve followed our advice in the past for keeping your iOS device secure, you’ll know that you should be doing the following:
- Install updates – keep up to date, and that includes your apps too.
- Keep a backup – use iCloud or Dropbox for photos and backup your device.
- Never “jailbreak” – this is the method for breaking the factory security.
- Activate anti-theft – such as “Find my iPhone/iPad” to locate a lost or stolen device.
BUT despite this, did you know you could still be just one tap away from disaster?
As reported in Macworld, security researchers uncovered spyware dubbed “XAgent” that is delivered via a phishing attack and can spread to other iOS users via contacts in your address book.
For more tips on staying safe from phishing, check out my blog “How To Protect Yourself from Phishing Attacks”
The good news is that you can do something about this, as all the users affected by this particular threat (and previous ones using the same technique) almost certainly “infected themselves” by ignoring vital warning message prompts.
Apple advise iOS users here to be mindful to only download and install apps from the Apple App Store and to be cautious of so-called “enterprise apps” that are only intended for employees of large businesses.
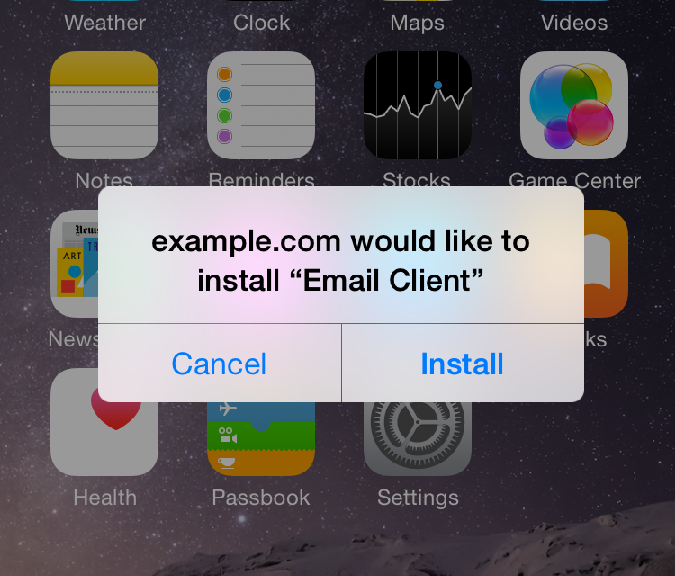
Therefore, if you don’t work for a company that is specifically requesting you to install an app and you see these following prompts – make sure you answer them correctly to protect yourself from inadvertently installing malware.
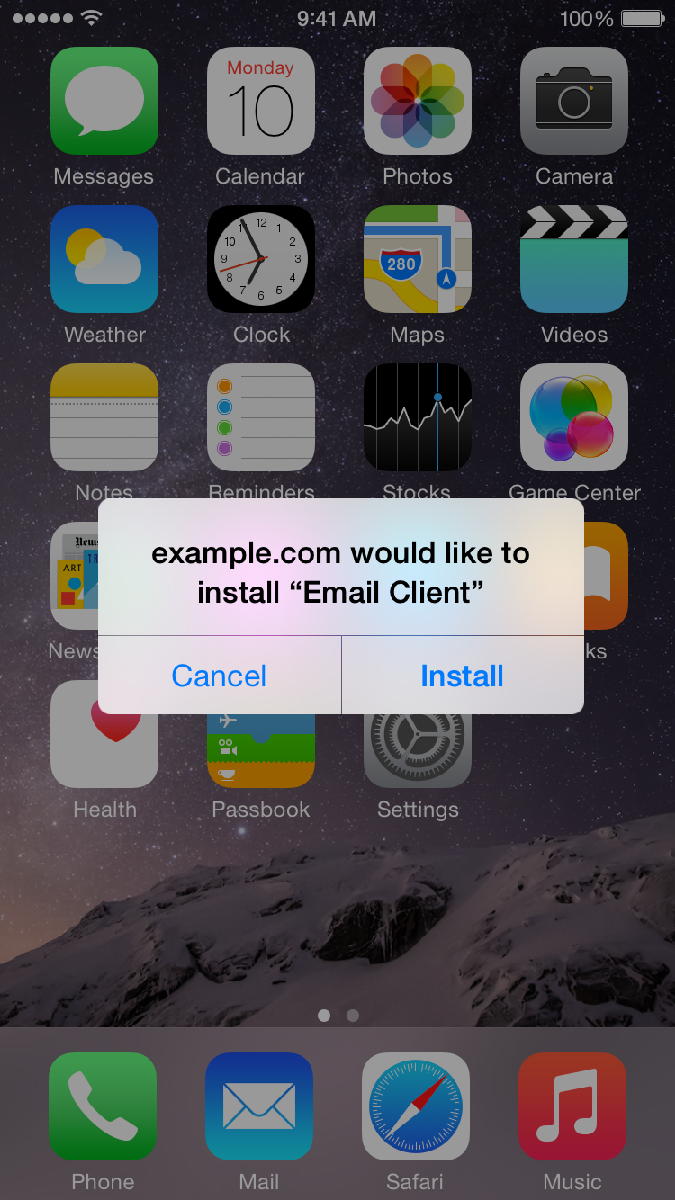
To protect yourself in this example you click CANCEL
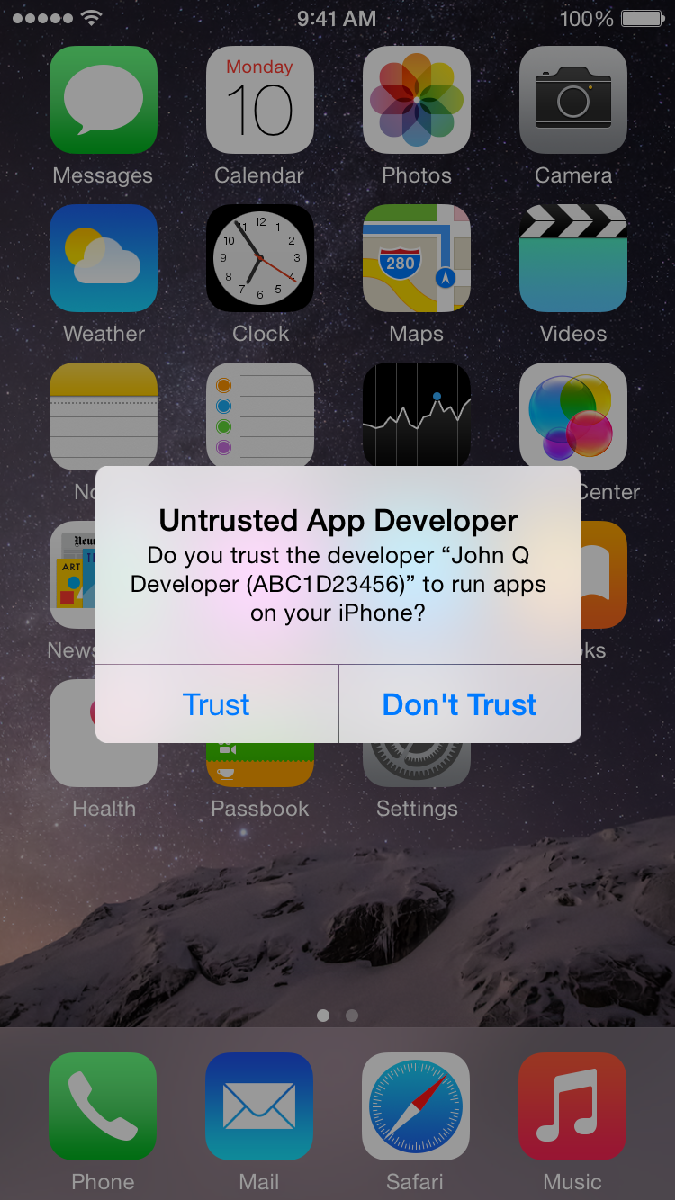
To protect yourself in this example you click DON’T TRUST
You might have also seen a similar Trust or Don’t Trust option available when connecting your iPhone or iPad to a friends computer – and again the safer option is always Don’t Trust.
Until next time, stay safe out there.