As with so many of today’s technological tools, while many people use them to make their lives easier, or to keep in touch with friends and family, there are some that take advantage of them simply to annoy others.
So while most of us use social networks to chat with friends, meet new people and keep abreast of what’s happening in the world, there are those that saturate our accounts with messages that are not just of no interest, they are downright annoying: the infamous ‘spam’.
Now, tired of users having to endure this continuous bombardment of unwanted advertising, those responsible for several social networks have decided to go on the offensive. One of these is Twitter, which has taken action as spammers have been increasing their unhindered presence on users’ timelines and direct message inboxes. Finally, those in charge of the social network have said enough is enough.

As the company has revealed on its blog, over the last six months its developers have been working on the design of a system that can detect and block the actions of these annoying spammers. They have called it ‘BotMaker’ and its objective is to counter the actions of those who, whether for commercial reasons or otherwise, are dedicated to annoying other users of the social network.
The plan that Twitter has come up with to prevent these unwelcome users from doing whatever they please has three objectives.
- Firstly, it aims to reduce the options for spammers to create content.
- Secondly, it wants to restrict the visibility of spam messages launched on the social network.
- Finally, the most difficult objective is to reduce reaction times between spam attacks and the system’s ability to detect and stop them.
To achieve its aims, BotMaker has been designed to apply a series of rules that allow it to determine who is annoying other users with spam. When there is a suspicion that a tweet breaks the rules on spam, Twitter’s new platform will activate a protocol to ensure that either the message is deleted immediately or the user that sent it is vetoed to prevent them from further annoying users.

Moreover, to prevent any unwanted messages from bothering other tweeters by trying to sell something, Twitter’s newly devised anti-spam system includes different bots that act at different stages of the hunt for spammers. The first to come into play is Scarecrow, which intervenes immediately in real time. Sniper comes next, eliminating any spam messages that have slipped past the previous filter. It also carries out a second appraisal and makes a record of suspicious users. If this weren’t enough, BotMaker also sets certain controls on users over long periods of time to prevent them from getting around the rules.
Nevertheless, the main advantage of Twitter’s new system is that it can detect spam even before the account in question can send junk mail to other users. This was the biggest challenge that the team at the social network faced because, whereas with email the delivery is delayed for a few seconds while Google or Microsoft robots check it to ensure it is not spam, with tweets this isn’t the case. These messages are sent and, theoretically, should arrive on your timeline immediately.
Users are also involved in the successful operation of BotMaker as they have the chance to identify those accounts that are flooding their timelines with spam. In this regard, the cookies that users have to accept to use Twitter also play an important role, by analyzing the traces left by tweeters. Despite this, BotMaker has no negative effects on users whatsoever. In fact, the system has been configured not to interfere with the bots that users install to automatically tweet on those topics that they have previously selected.

Trails carried out by the company with BotMaker have shown it to work efficiently. In the six months that Twitter tested its own invention, it managed to reduce by 40 percent the billions of unwanted messages aimed at selling or promoting products to other users of the social network.
Yet although these results may seem encouraging for those who regularly use Twitter, the truth is that all is not what it seems. Beyond its firm desire to counter the intentions of spammers, the social network is also striving to improve its own targeting of advertising.
As the epicenter of thousands upon thousands of comments about all types of events taking place around the world, the filters that BotMaker uses can also be used to select users who may be interested in advertising of one product or another.
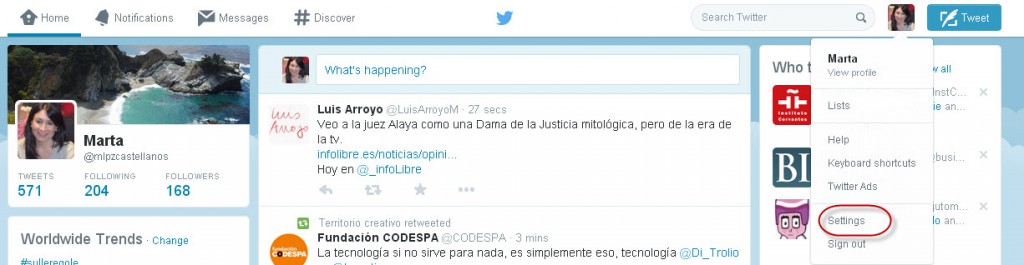
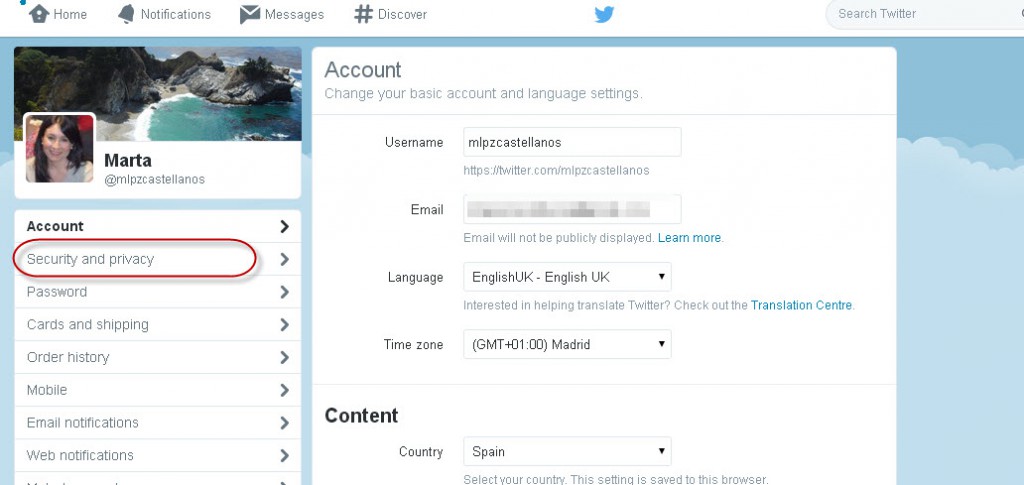
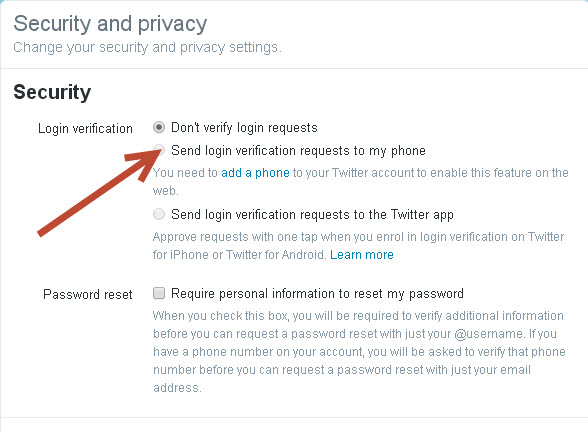
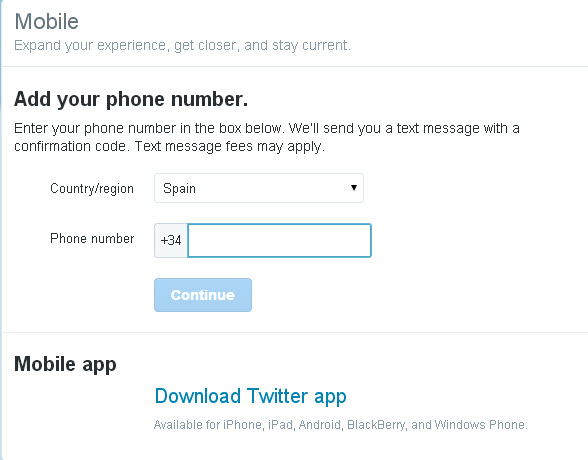
More | How to protect your Twitter account
The post How Twitter aims to prevent your timeline from filling up with spam appeared first on MediaCenter Panda Security.