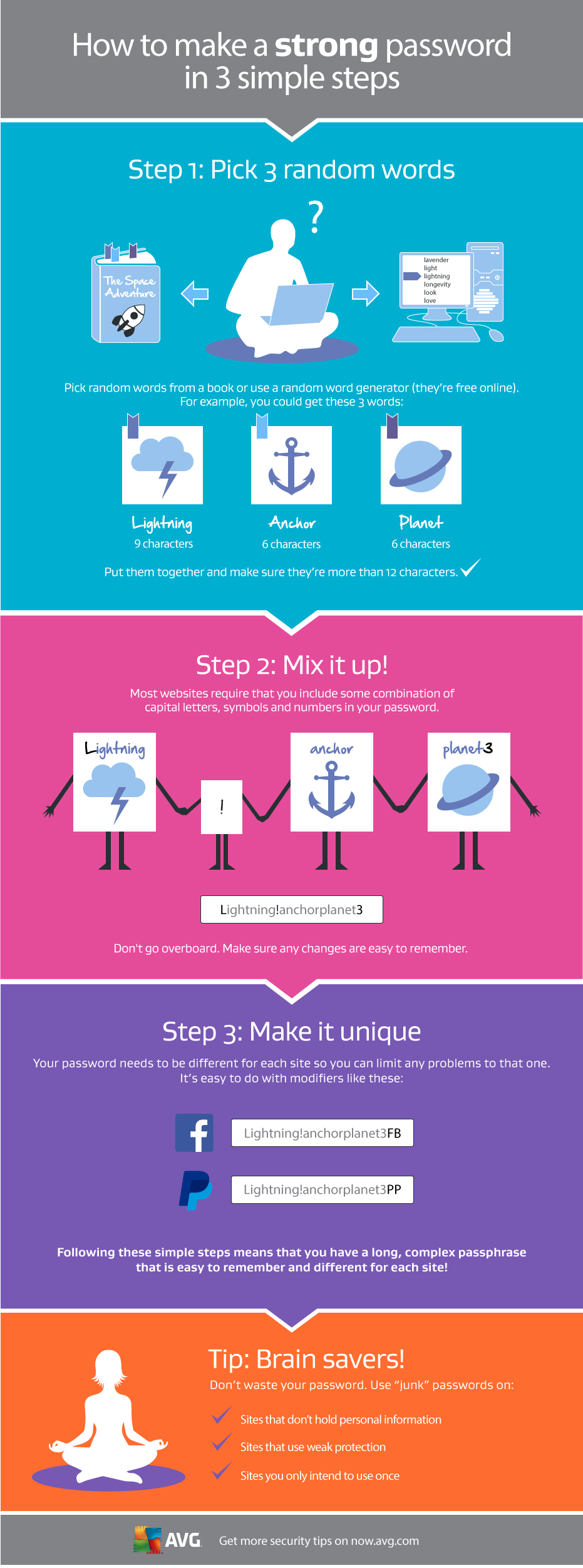
Most people have dozens of passwords, for dozens of online accounts. At times it can be tricky to remember them all, as best practice says they should all be slightly different.
If you’re one of these many people, Yahoo’s recent announcement may get you excited. Earlier in March, Yahoo revealed an innovative idea that would mean we never have to remember a password again.
The concept is very simple. By selecting to use one-time passwords in your account settings, the next time you login it will send a password to your phone that you can use to login in with via a SMS.
While this seems very convenient, is it secure?
Generally speaking, there are three types of authentication in use today
- ID and Password
- ID, Password, Verification Code (using SMS)
- Two Factor authentication using ID, Password and another device providing a unique password
The Yahoo solution seems to be half way between the least secure option A and Option B.
Sending a password on demand to a device is a step in the right direction, but there may be other security risks involved when transmitting data over SMS and to a potentially unprotected device.
The phone may not have a passcode and could be infected with malware that reads the SMS. This could mean the email account and all the data inside gets compromised.
If you do want to enable one-time passwords, I would recommend you have both of these: a passcode and AVG AntiVirus for Android on the phone to keep yourself protected.
What would I do differently?
Using the mobile device to add another layer of security is a smart idea as most people have one. Most of us also use apps regularly and if you’re a Yahoo user then you probably have the Yahoo app.
I would change the delivery method of the password from SMS and instead deliver it, in an encrypted format, via their own app.
On top of this, the Yahoo app with this one-time passwords enabled should require the device to have PIN security.
This would mean that an attacker would need the ID, the phone and the PIN in order to access the account. The app could even go further and check for the presence of an Anti-Virus product to ensure that it’s being scanned regularly.
It could be that there are currently technical limitations with one-time passwords, and that in the future we’ll see a lot more secure and comprehensive process.
My top advice right now though is if you’re going to use this service then be sure to have a security app and a PIN on your phone so you can help ensure that the password is being sent to a secure device.
Follow me on Twitter @tonyatavg