There is a huge shortage of skilled professionals in cybersecurity. We take a look at six young geniuses who may be the future of the industry.
The post 6 child geniuses destined for a career in cybersecurity appeared first on We Live Security.
![]()
There is a huge shortage of skilled professionals in cybersecurity. We take a look at six young geniuses who may be the future of the industry.
The post 6 child geniuses destined for a career in cybersecurity appeared first on We Live Security.
![]()
Earlier in August, the world’s largest social networking site, Facebook, unveiled their new Security Checkup feature.
The aim is to create a series of simple tools that help users control which devices are logged into Facebook, receive alerts when new devices log in and tips on creating a strong password.
Let’s take a look in more detail:
If you have multiple devices linked to your Facebook account, you may be surprised to see just how many apps have access to your account. Closely monitoring which apps have access to your account is a great way to help protect your account security and the privacy of your personal information.
It’s worth remembering that apps that have access to your Facebook account also have access to a lot of your personal information. Be selective about which apps you allow.
Setting up login alerts is a great way to help you manage access to your Facebook account. Used in conjunction with other security features such as Two-Factor Authentication, login alerts make it very difficult for any unauthorized party to gain access to your account. I’d highly recommend implementing both this and Facebook’s Login Approvals.
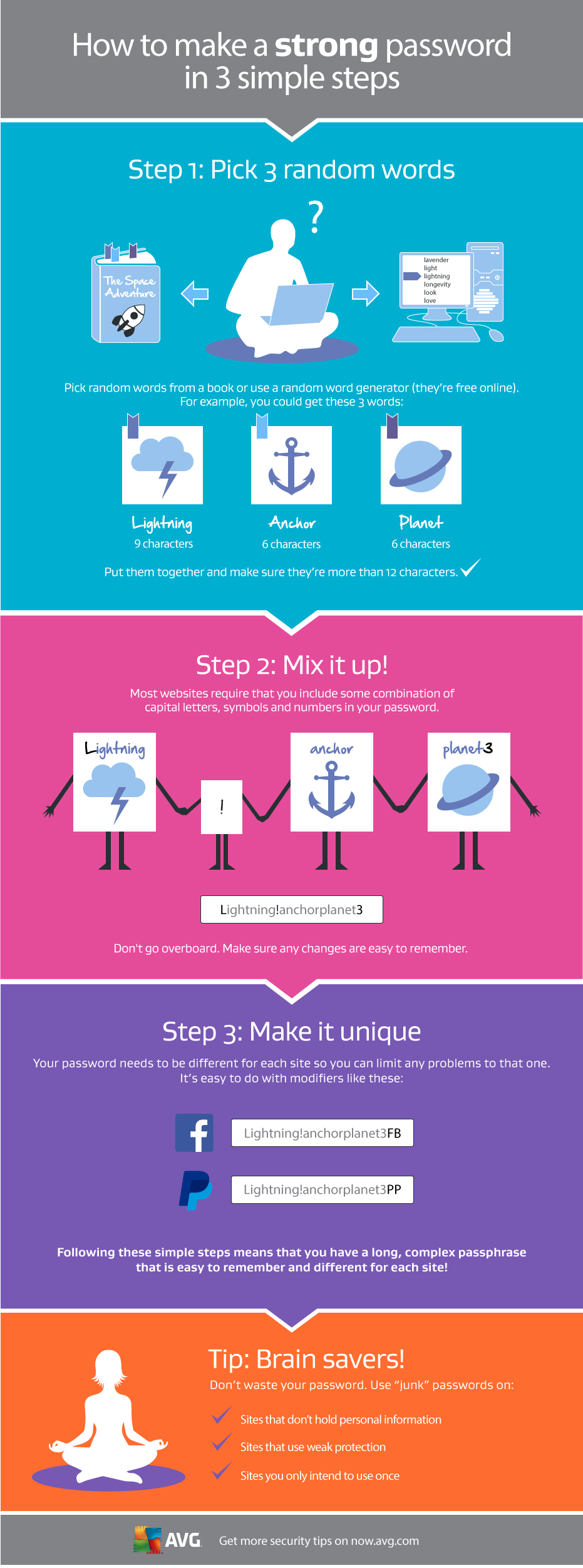
The final tool in the Security Checkup is some advice both for creating a strong password and also password safety advice.
The advice recommends using a password unique to Facebook, never sharing your password and avoiding dictionary or identifying words.
Your password is one of the most important parts of keeping all your online accounts safe, for more information on creating a strong, unique password that’s easy to remember, check out this infographic below.
Moonpig, the online personalised card company, has blocked the accounts of an unspecified number of customers after users’ details were published online.
The post Moonpig warns of password breach – but it may be more than their users who are at risk appeared first on We Live Security.
![]()
Security experts and non security experts take very different attitudes to staying safe online, according to new research.
The post New report explains gulf between security experts and non-experts appeared first on We Live Security.
![]()
Wow, that sentence sounds rather boring, right? Well, let’s elaborate a bit. If you are an avid PC gamer you most like know Steam, and if you are into playing (or watching) gamers compete in Multiplayer Online Battle Arenas (MOBAs), you also might have noticed that some of the more famous DotA 2 players got their accounts stolen. Of course their accounts were not the only ones affected, but definitely the most noticeable ones.
What happened is that Steam apparently had a rather big loophole in its system: One could access another account with only the username – and it was as simple as eating pie. Just take a look at the video below and be amazed:
The issue is now fixed, after Valve learned of it on July 25th – so if you are a gamer with a lot of games in your steam library (or a professional DotA/CS:GO player) you can relax.
According to Kotaku, Valve release a statement to those affected:
“To protect users, we are resetting passwords on accounts with suspicious password changes during that period or may have otherwise been affected. Relevant users will receive an email with a new password. Once that email is received, it is recommended that users login to their account via the Steam client and set a new password.
Please note that while an account password was potentially modified during this period the password itself was not revealed. Also, if Steam Guard was enabled, the account was protected from unauthorized logins even if the password was modified.
We apologize for any inconvenience.”
The post Steam Account Security Issue Got Fixed appeared first on Avira Blog.
A new app could see Mastercard accepting selfies instead of passwords to make purchases online.
The post Mastercard trials selfies as password replacement appeared first on We Live Security.
![]()
Now the favorite past time of some (namely taking selfies!) might actually become a legit payment method for MasterCard users. The company is experimenting with a feature called ID Check, which would scan your face (or your fingerprint, depending on what you choose) in order to approve an online purchase. Basically they are trying to go full blown biometric.
Ajay Bhalla, the MasterCard executive who’s in charge of the new payment methods told CNN: “The new generation, which is into selfies … I think they’ll find it cool. They’ll embrace it.“
Why MasterCard would do something like that? Definitely not only to please us youngster, but also to cut down fraud, it seems. The US trial is supposed to start very soon with a limited customer base of 500. The launch will follow sometime after that.
If you’re afraid that you’ll need a selfie stick in order to make payments with your MasterCard in the future, don’t worry too much: The way the system is described you’ll just install the MasterCard app, purchase something, and once you want to pay a pop up appears. Now you can choose to complete the payment with a fingerprint scan or via said selfie. According to CNN “you stare at the phone — blink once — and you’re done. MasterCard’s security researchers decided blinking is the best way to prevent a thief from just holding up a picture of you and fooling the system.” Easy peasy, right?
Well, let’s see how it will work out and what’s next: Bhalla also said that MasterCard is experimenting with voice recognition and approving transactions by recognizing your heartbeat …
The post Shopping via Selfie is the next thing … appeared first on Avira Blog.
Emoji’s such as smiley faces and others pictographs used commonly by many people nowadays have been put forward as a possible replacement to the humble password or PIN by a British start-up called Intelligent Environments.
As reported in The Guardian recently, the concept lends itself to our natural ability to remember pictures much more vividly than standard characters like letters and numbers.
Add to that research that shows 64% of millennials are using Emoji’s almost exclusively in their communication, and one wonders if this trend just might have some merit in the future.
The method proposed is that instead of entering your password or PIN, instead you would select a sequence of 4 Emoji pictures from a possible set of 44. The math behind this says that an Emoji “password” would therefore be one out of a possible 3,748,096 combinations.
However, the question of whether this would be more secure over the standard password, and in particular a 4-digit PIN is open for debate.
While technically your 4-digit PIN is only one from a combination of 10,000 choices, the implementation on your mobile device tends to be much more secure, by the fact that incorrect attempts will result in gradually increasing timeouts – making it much more difficult and impractical to crack easily.
And consider that, just as with passwords, it is possible that people will select Emoji sequences that are quite predictable. For example, selecting Emoji’s that tell a common story, like a Man, a love heart, a Woman, and a bunch of flowers; it’s quite possible people will end up selecting popular Emoji versions of the 1234 PIN equivalent.
On the positive side, think of how hard writing down your Emjoi “password” is going to be for those of us who aren’t artistically gifted.
If you are concerned about only using a 4-digit PIN on your mobile device, however, there are options you can change:
For more information keeping your mobile device safe, check out the video below 6 Tips to Secure your Android Phone video.
Until next time, stay safe out there.
![]()
![]()
Few people’s idea of a relaxing Father’s Day involves getting to grips with IT security, but scammers typically target the holidays to catch out consumers.
The post Must-know security tips for non-technical fathers appeared first on We Live Security.
![]()
Six university researchers discovered high-impact “zero-day” security weaknesses in iOS and Mac, which can be abused by getting a malicious app approved by the Apple app store – something they managed to do without any issues. Through this app they were able to access sensitive data from other apps – with dire consequences. The researchers state that “our sandboxed app successfully retrieved from the system’s keychain the passwords and secret tokens of iCloud, email and all kinds of social networks stored there by the system app Internet Accounts, and bank and Gmail passwords from Google Chrome […]”
It does sound unbelievable, doesn’t it? Just take a look at the below video to see a malicious sandboxes app on OS X steal all private notes in the Evernote app:
Or how about a look at how it is able to steal any websites’ passwords:
According to their research 88.6% of the apps they tested were found to be completely exposed to the XARA attacks. This includes popular apps like Evernote, WeChat, and 1Password: “In our study, we downloaded 1,612 free apps from the MAC App Store. These apps cover all 21 categories of the store, including social networking, finance, business, and others. In each category, we picked up all the free apps when less than 100 of them are there, and top 100 otherwise. Also from the iOS App Store, we collected 200 most popular apps, 40 each from “All Categories”, “Finance”, “Business”, “Social Networking” and “Productivity”, after removing duplications.”
The researcher informed Apple about the issues in October 2014, a fix seems to be still outstanding.
Take a look at the research paper to read all about the issue.
The post XARA – With This Exploit Hackers Can Steal Your Passwords appeared first on Avira Blog.